Embed presentation
Download to read offline

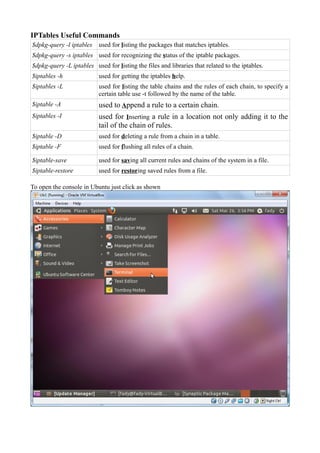

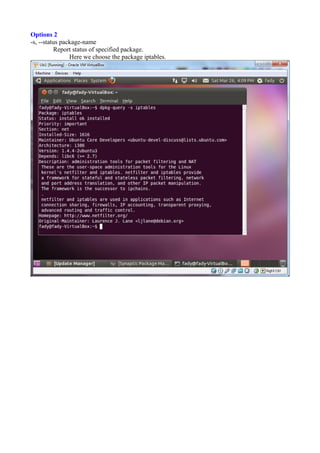
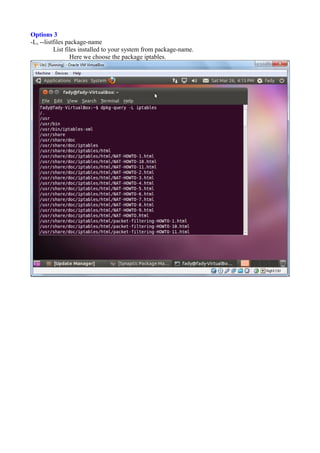
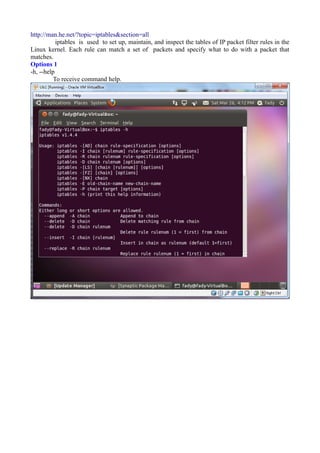
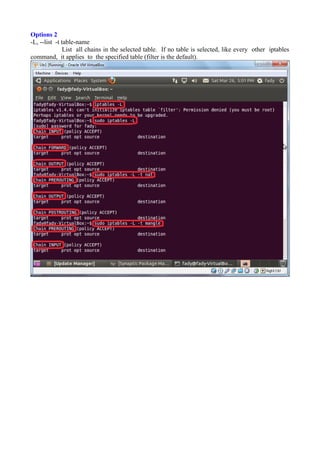
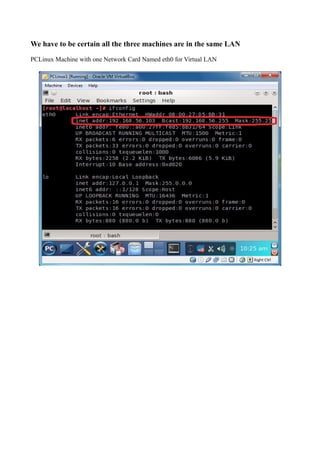
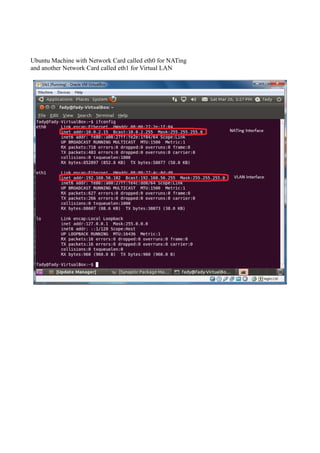
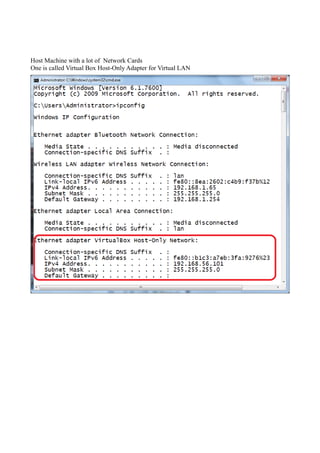
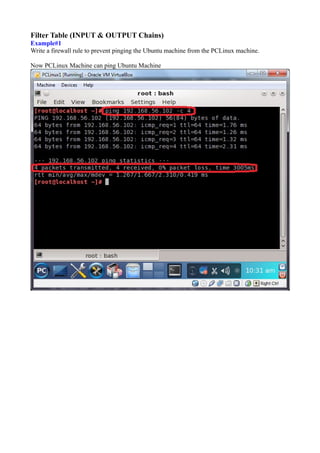
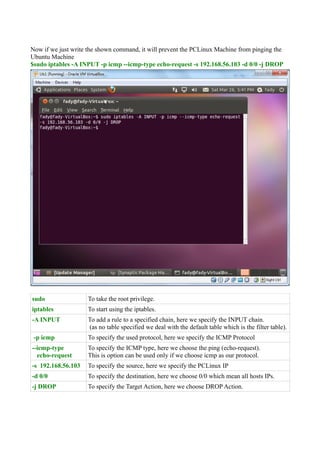
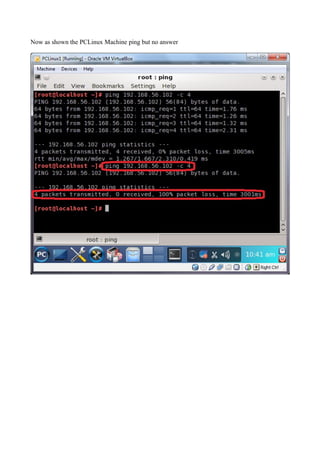
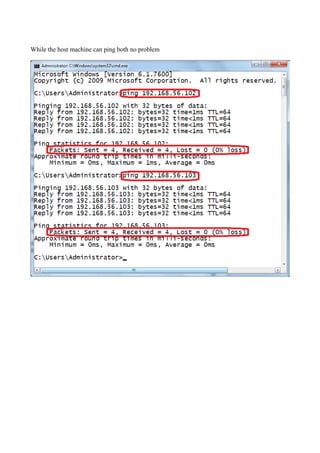
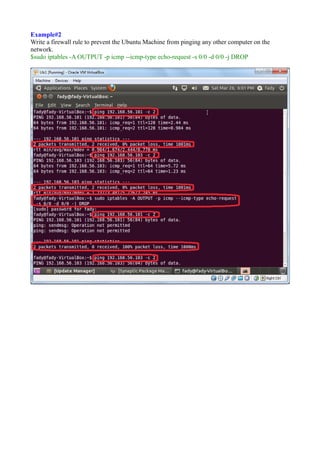
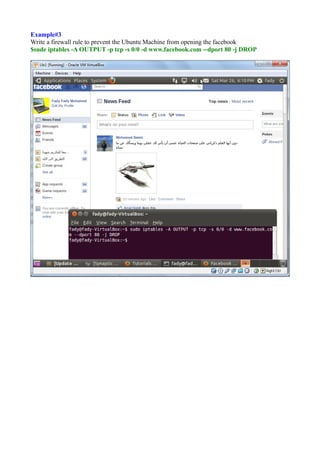
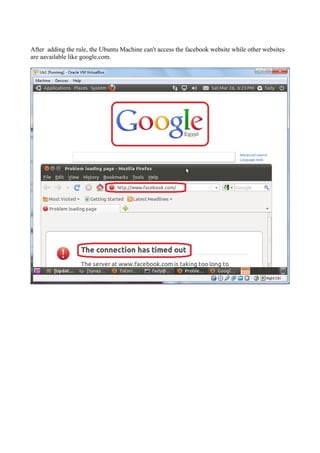
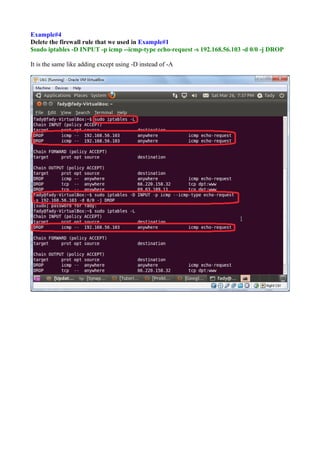


The document discusses Linux firewalls and the iptables software. It provides information on how iptables organizes rules into tables and chains and describes some common iptables commands. The key points are: - Iptables is a net filter software that controls inbound and outbound traffic through rules organized in tables (filter, nat, mangle) and chains. - Common commands include iptables -L to list rules, iptables -A to append rules, and iptables -F to flush/delete all rules. - Examples are given of iptables rules to block ping requests between machines and restrict the Ubuntu machine's access to Facebook.




















