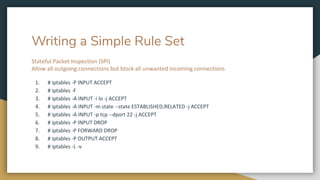
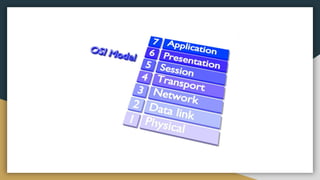
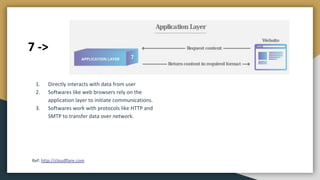
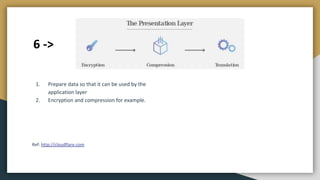
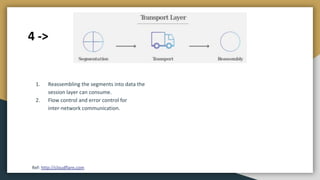
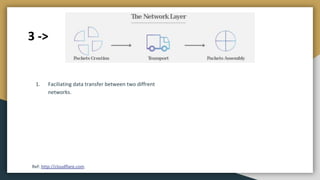
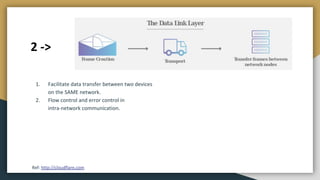
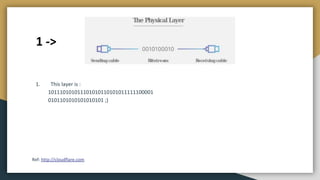
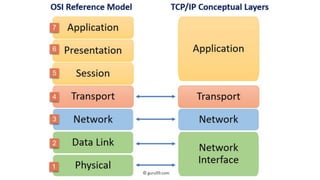
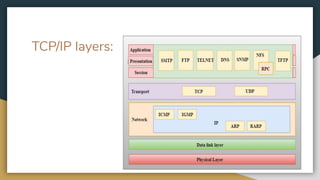
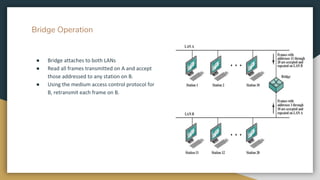
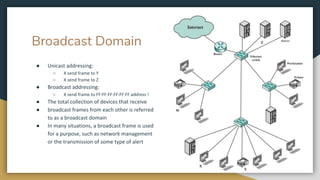
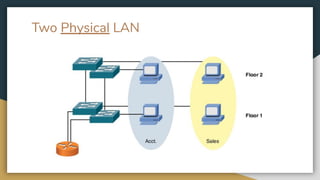
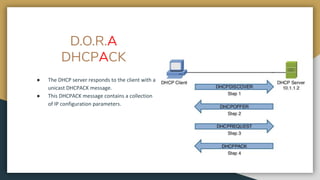
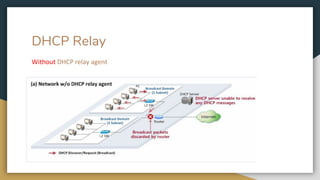
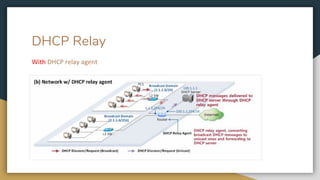
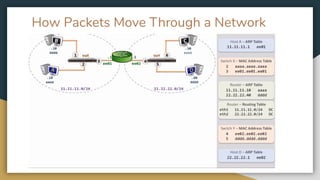
The document outlines key networking concepts, including the OSI model and the roles of the application, network, and data link layers. It details how data packets navigate through various network layers, the significance of IP addressing (both public and private), and the DHCP process for dynamic IP assignment. Additionally, it provides an overview of Linux command-line tools for network configuration and management.









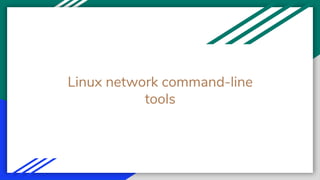
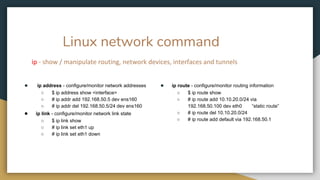




![Linux network command
arp - manipulate the system ARP cache
● $ arp -a
○ ? (172.16.10.44) at 08:01:27:62:9a:8f [ether] on enp0s25
○ ? (172.16.10.40) at 1c:1b:0d:49:e6:4 [ether] on enp0s25
● $ arp -d 192.168.10.11 “delete a ARP table entry”
● ip -s -s neigh flush all “clear the arp cache”
○ 172.16.10.44 dev enp0s25 lladdr 08:00:23:62:9a:8f used 460/456/412 probes 1 STALE
○ 172.16.10.40 dev enp0s25 lladdr 10:8b:0d:39:e6:a4 used 44420/44418/44378 probes 1 STALE](https://image.slidesharecdn.com/precloud-01-200531194431/85/packet-traveling-pre-cloud-49-320.jpg)








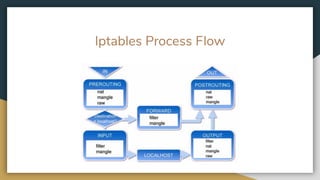


![Iptables -t[table] -OPTIONS[CHAIN] [matching component] [Action component]
Filter
NAT
Mangle
INPUT, FORWARD,
OUTPUT
Pre-routing,
post-routing, output
Pre-routing,
post-routing, forward,
output, input
Options:
A:append, I:insert,
D:delete, L:list, F:
flush, -P: policy
p - Protocol
s - Source IP
d - Dest IP
i - IN Interface
o - OUT Interface
ACCEPT
DROP
REJECT
LOG](https://image.slidesharecdn.com/precloud-01-200531194431/85/packet-traveling-pre-cloud-61-320.jpg)