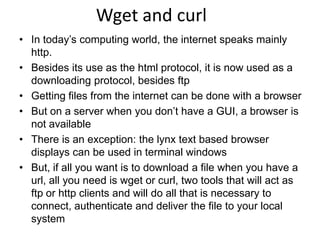
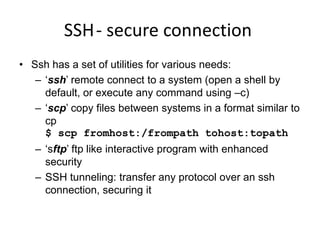
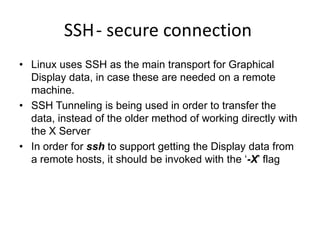
This document provides information on various networking tools and concepts in Linux. It discusses network basics like hosts, servers, clients and protocols. It then summarizes tools for remote access (Telnet), file transfer (FTP), downloading files (Wget, Curl), secure connections (SSH), network configuration (ifconfig, route), viewing connections (netstat), and network tracing (tcpdump).








![@ Copyrights InterBit LTD.
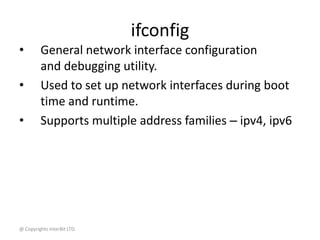
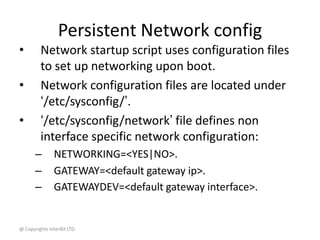
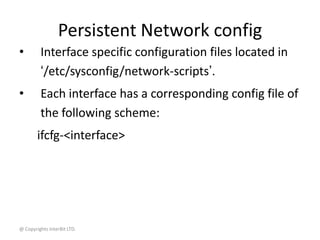
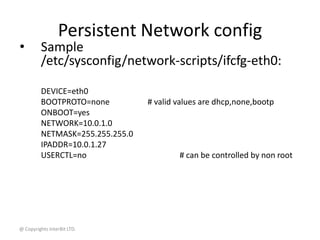
NIC link configuration
# ethtool eth0
Settings for eth0:
Supported ports: [ TP MII ]
Supported link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
Supports auto-negotiation: Yes
Advertised link modes: 10baseT/Half 10baseT/Full
100baseT/Half 100baseT/Full
Advertised auto-negotiation: Yes
Speed: 10Mb/s
Duplex: Half
Port: MII
PHYAD: 1
Transceiver: internal
Auto-negotiation: on
Supports Wake-on: g
Wake-on: g
Current message level: 0x00000007 (7)
Link detected: yes](https://image.slidesharecdn.com/14networktools-130801014829-phpapp02/85/14-network-tools-23-320.jpg)
![@ Copyrights InterBit LTD.
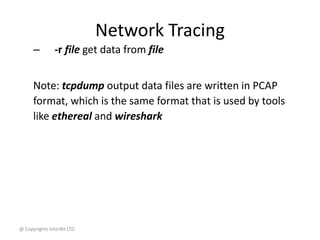
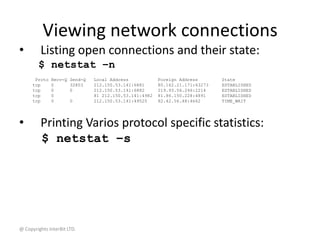
Network Tracing
• tcpdump is a network tracing tool. It connects
to a network interface, and print out
information about every packet going through
this interface
• Syntax:
tcpdump [options]
• Options:
– -i interface trace packets on interface
– -w file write data to file](https://image.slidesharecdn.com/14networktools-130801014829-phpapp02/85/14-network-tools-25-320.jpg)