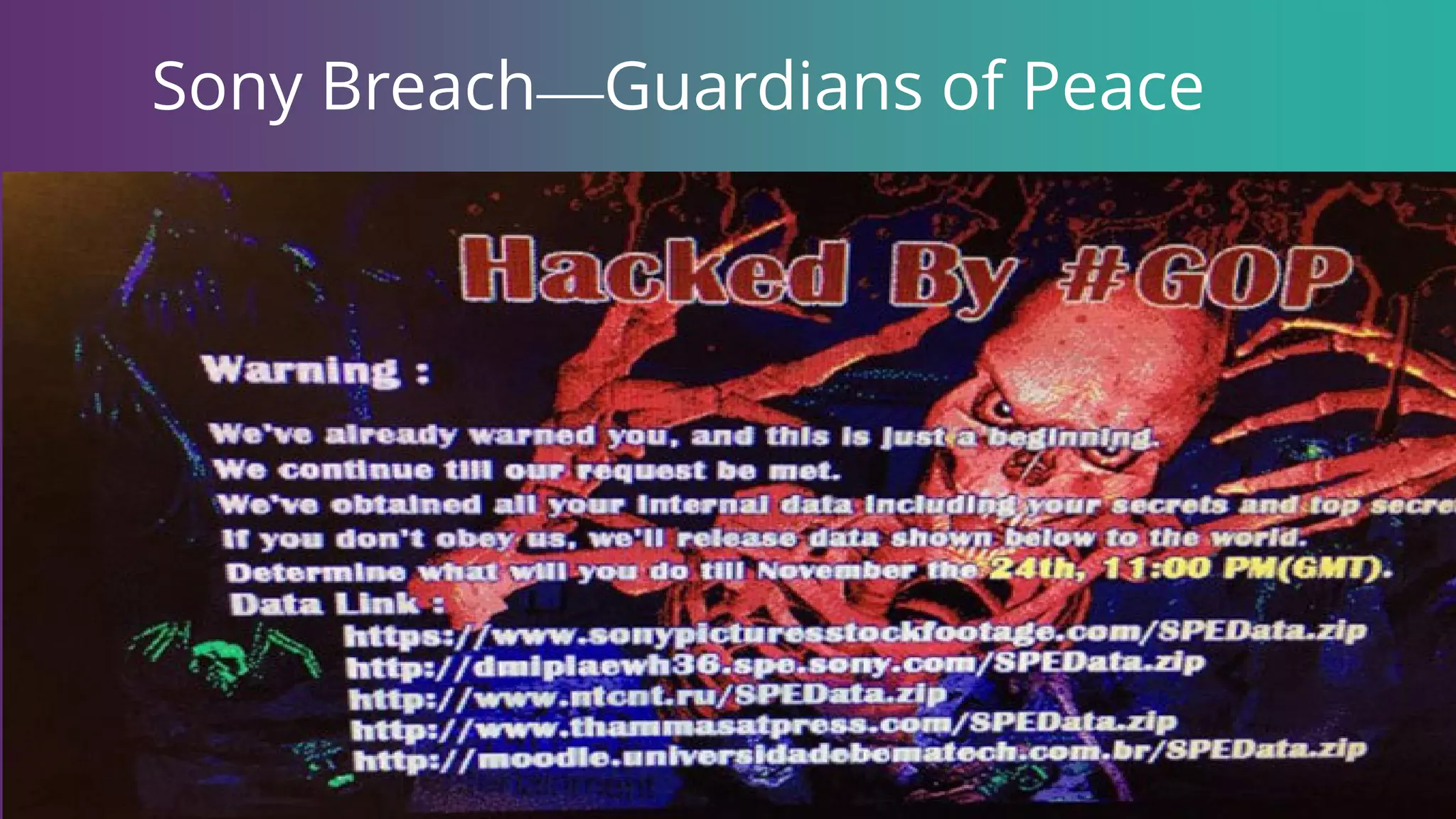
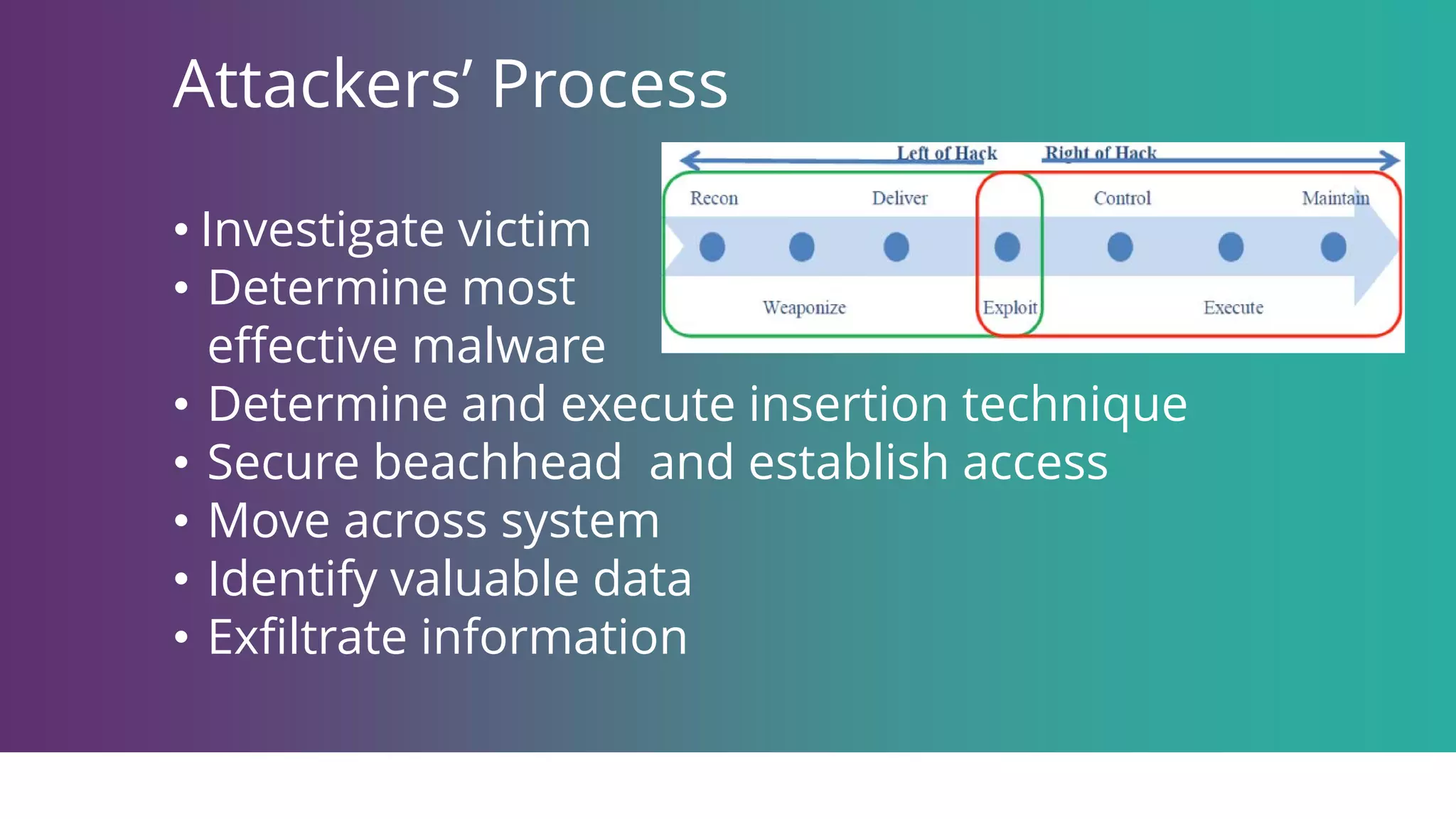
Geoff Hancock discusses significant data breaches, including those involving Sony Pictures, Target, and JP Morgan, emphasizing the methods used by attackers such as phishing and social engineering. The breaches resulted in millions of stolen records and substantial financial impacts on the organizations involved. Recommendations for enhancing cybersecurity include improved cyber hygiene, technical measures, and awareness of insider threats.