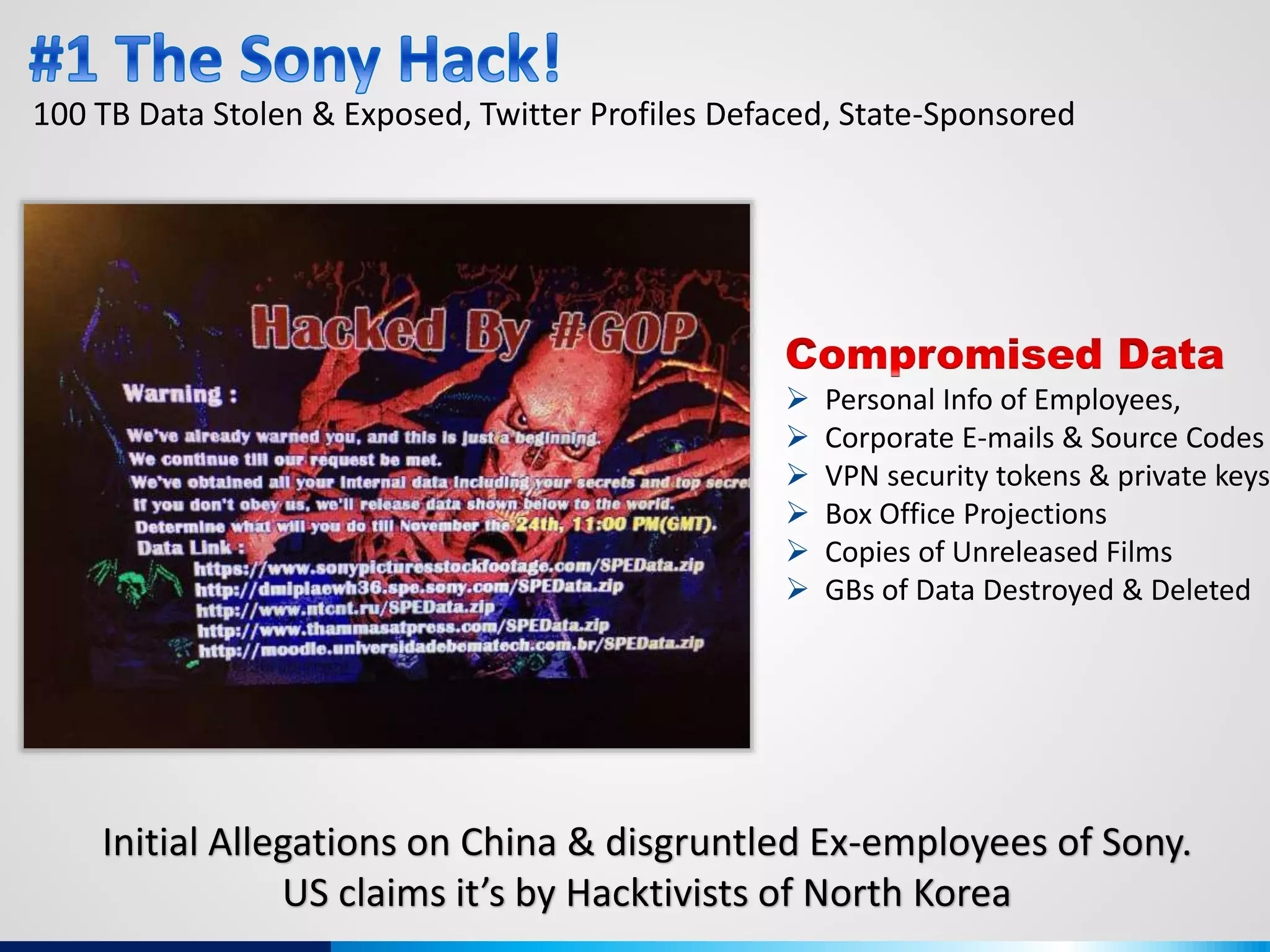
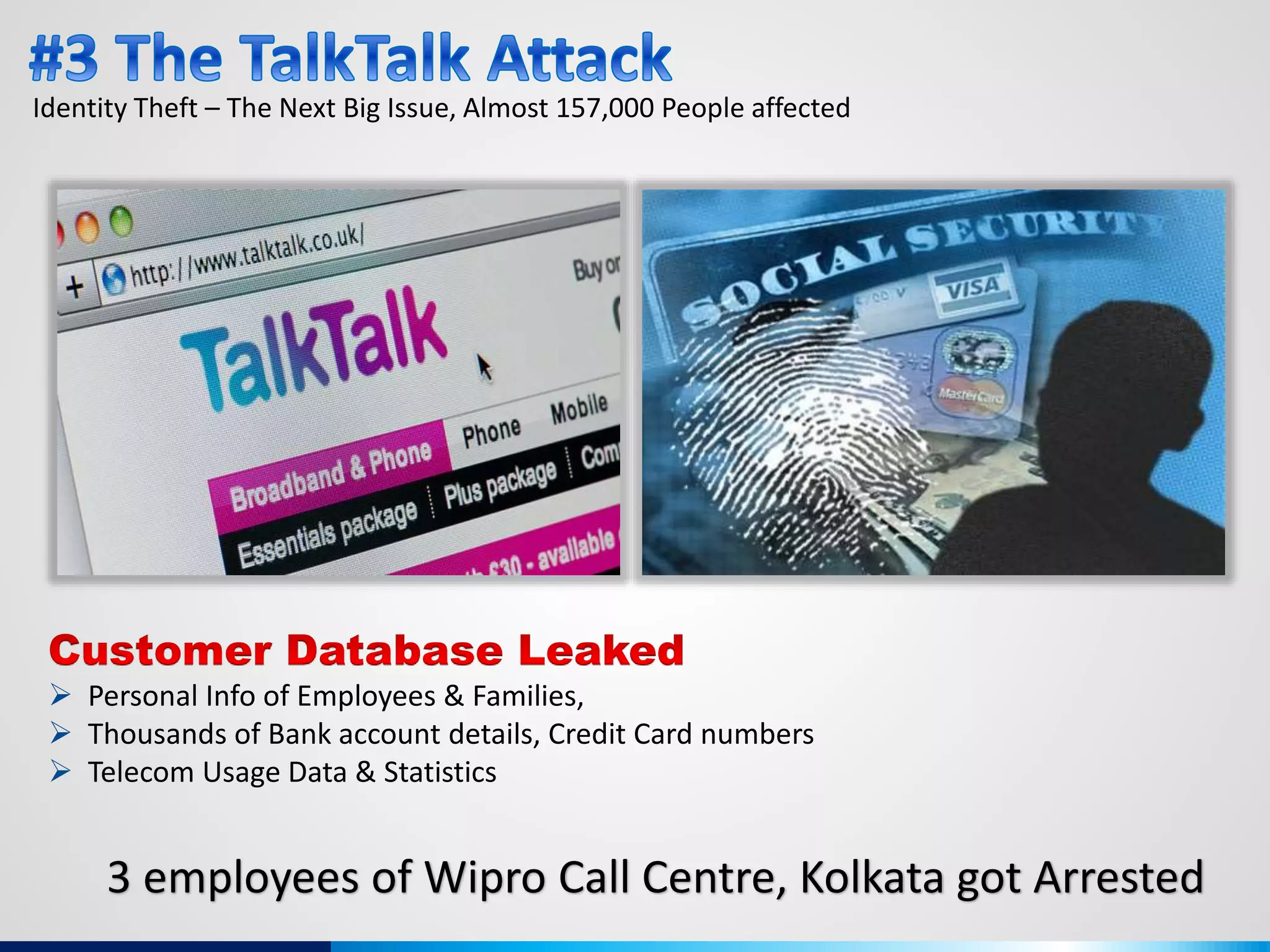
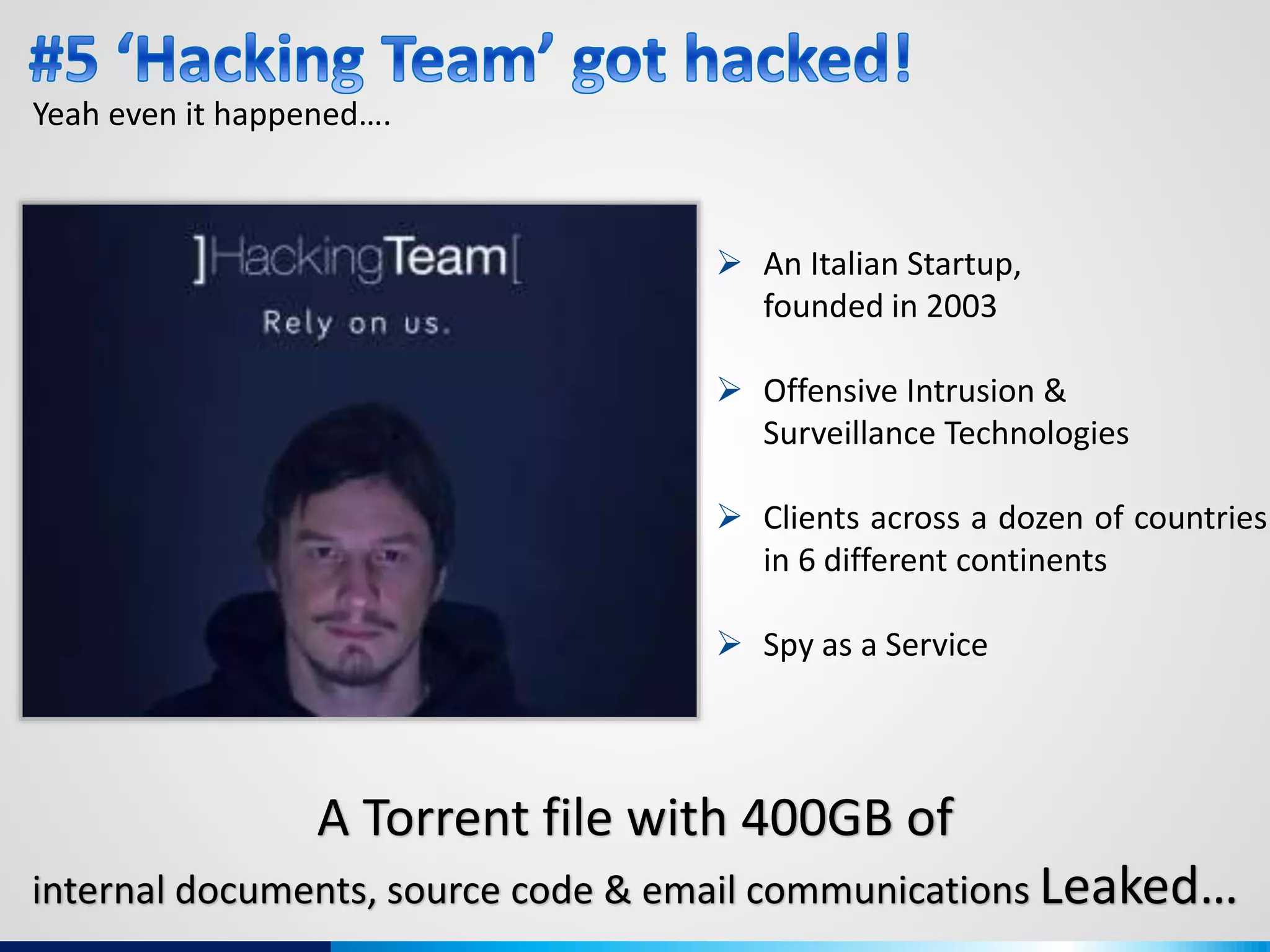
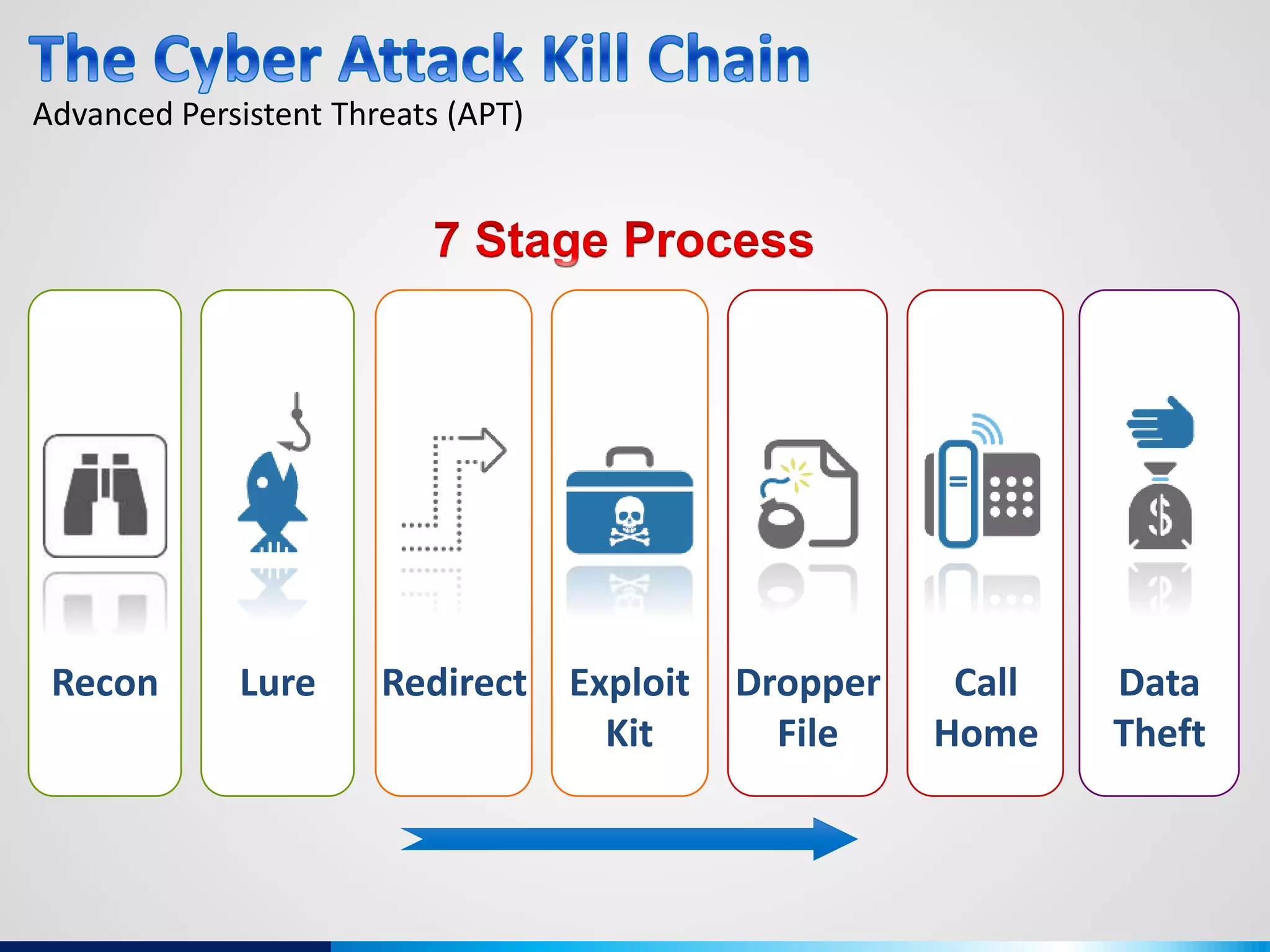
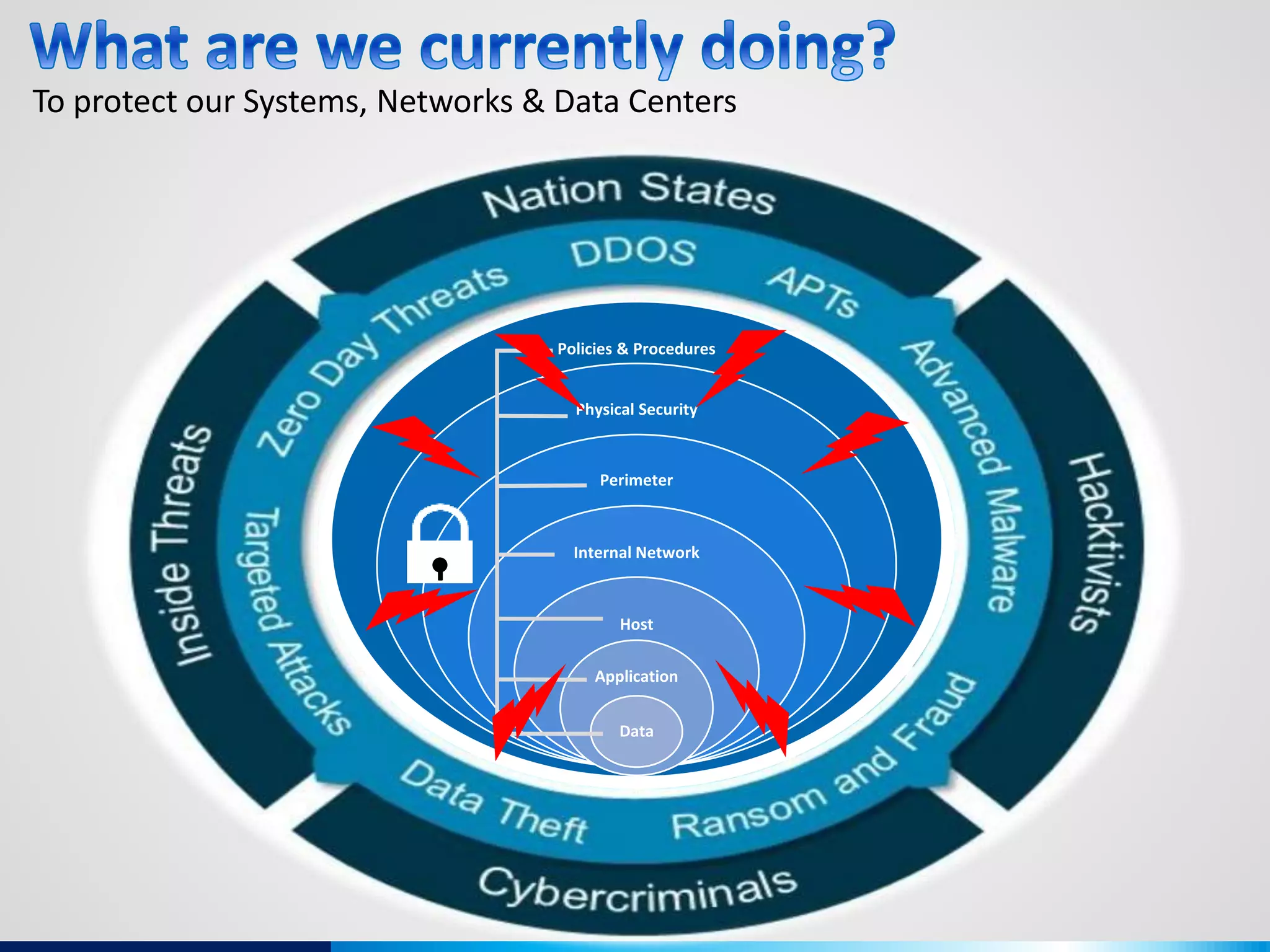
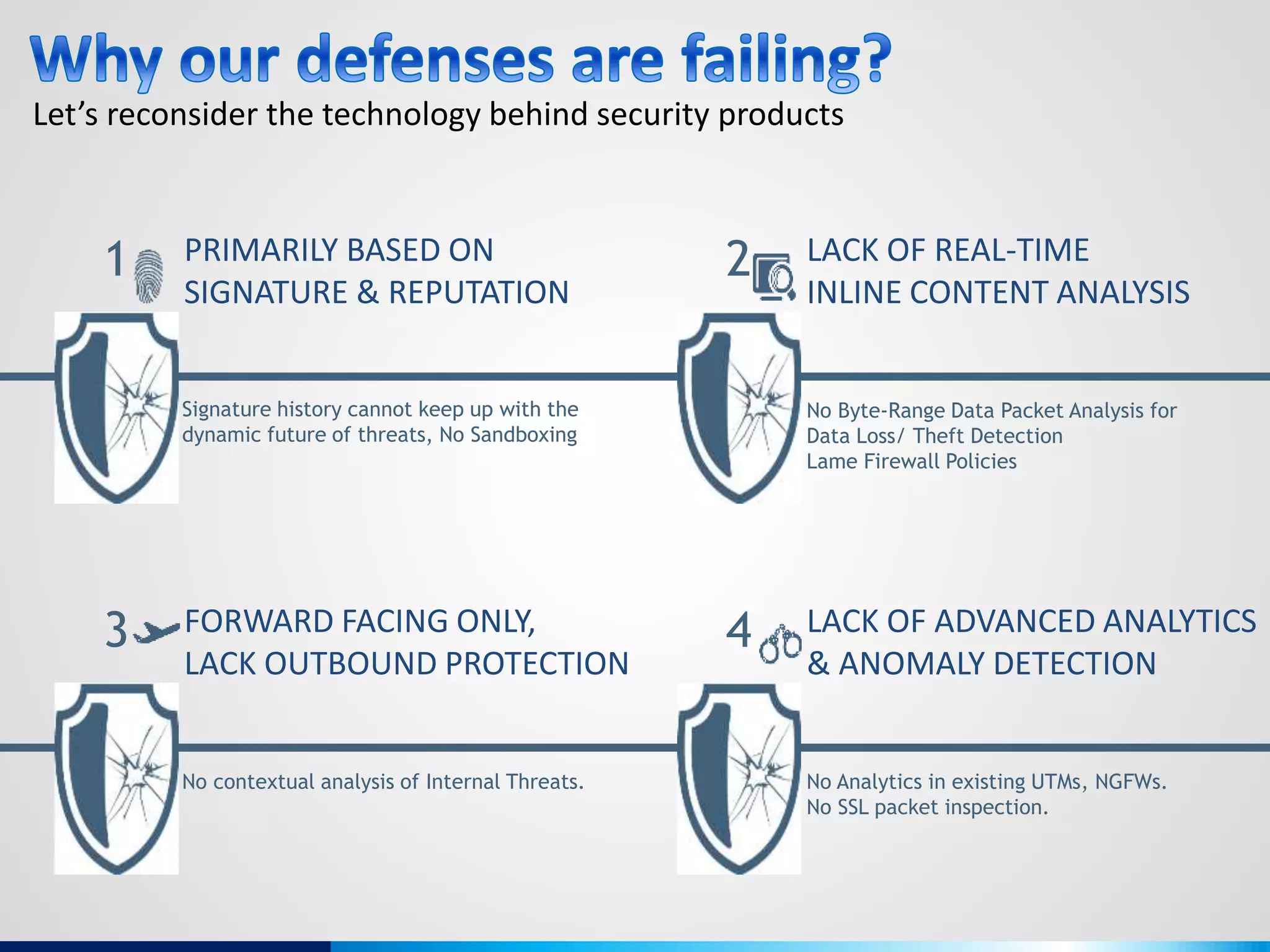
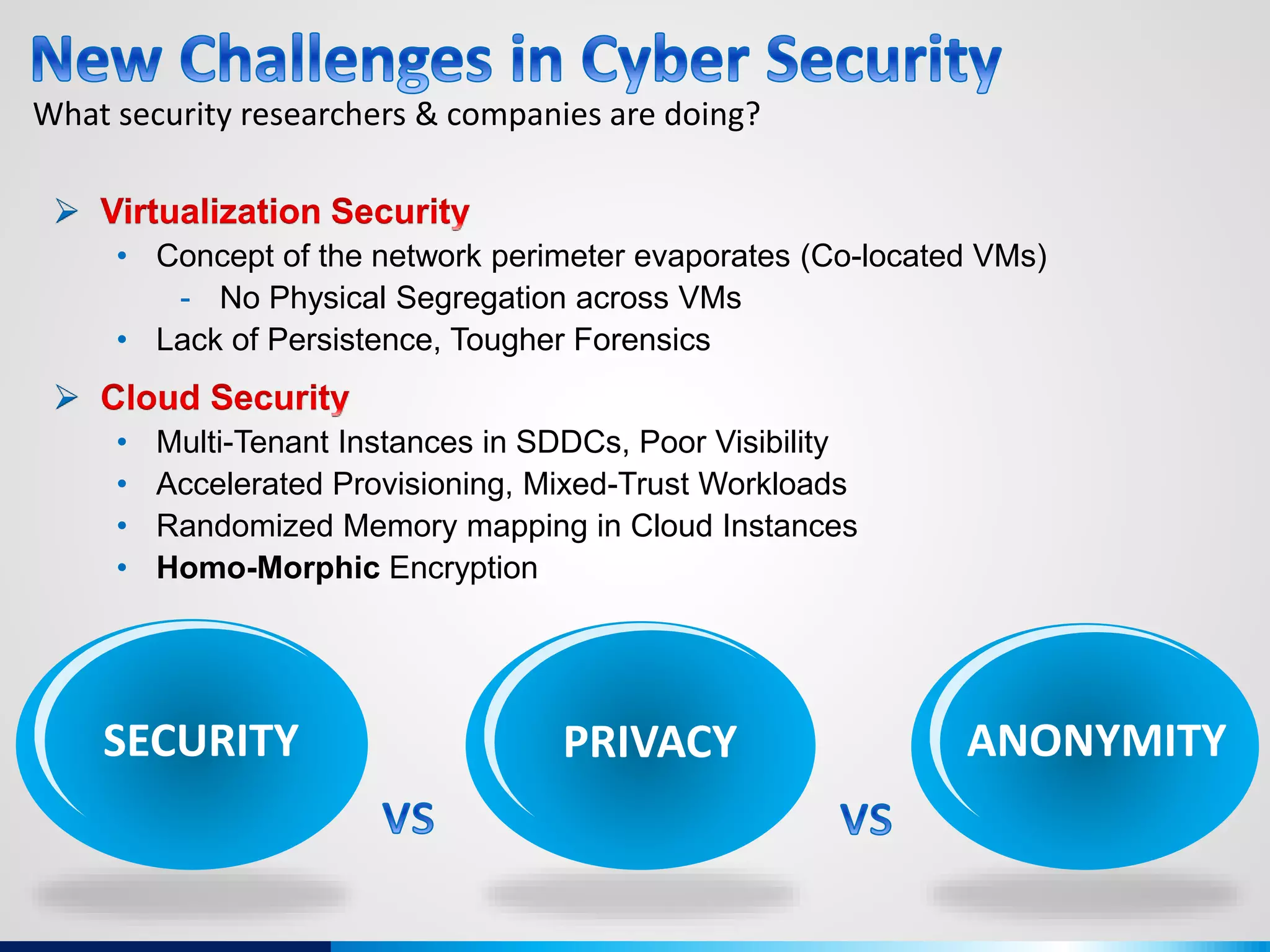
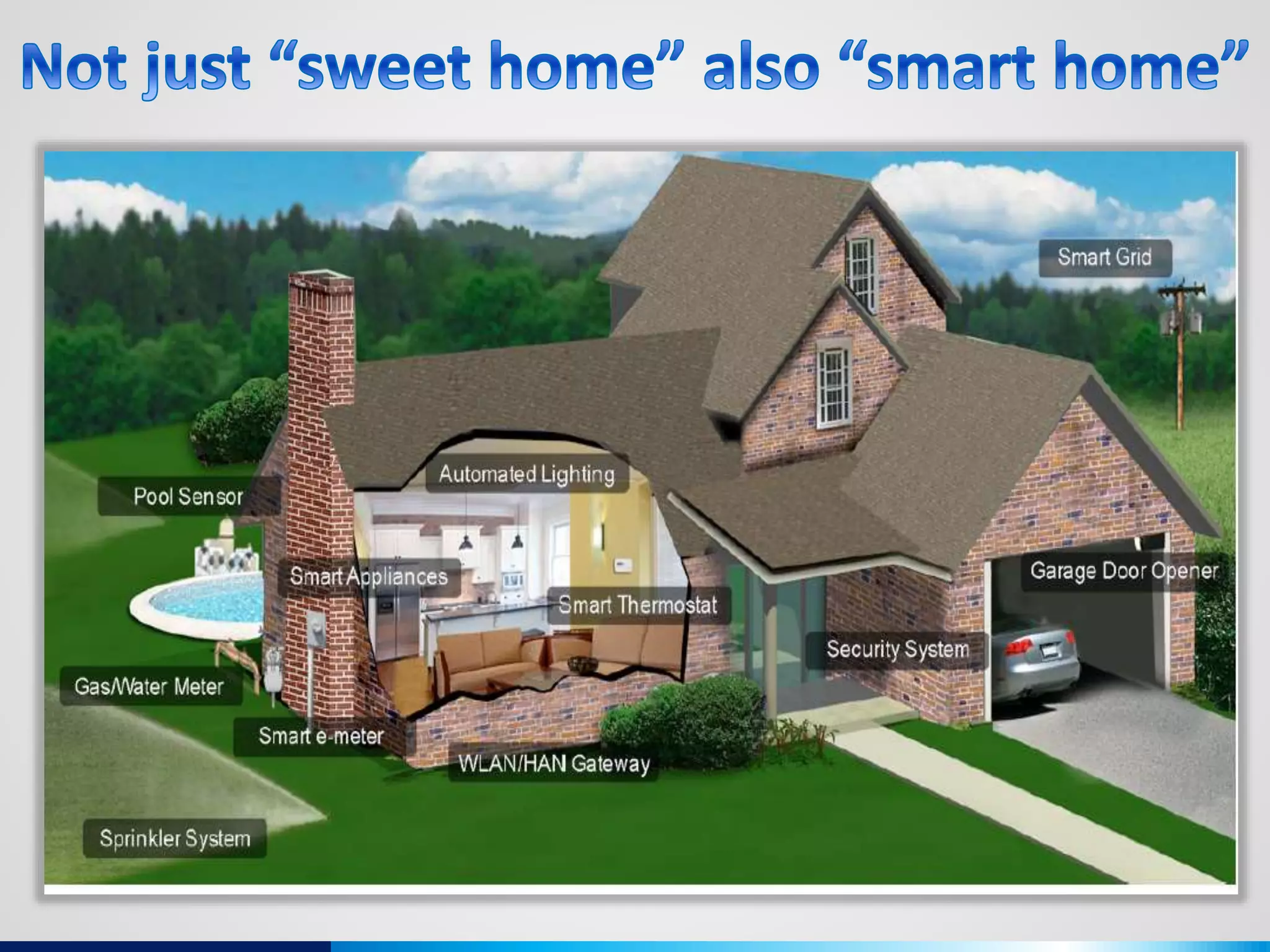
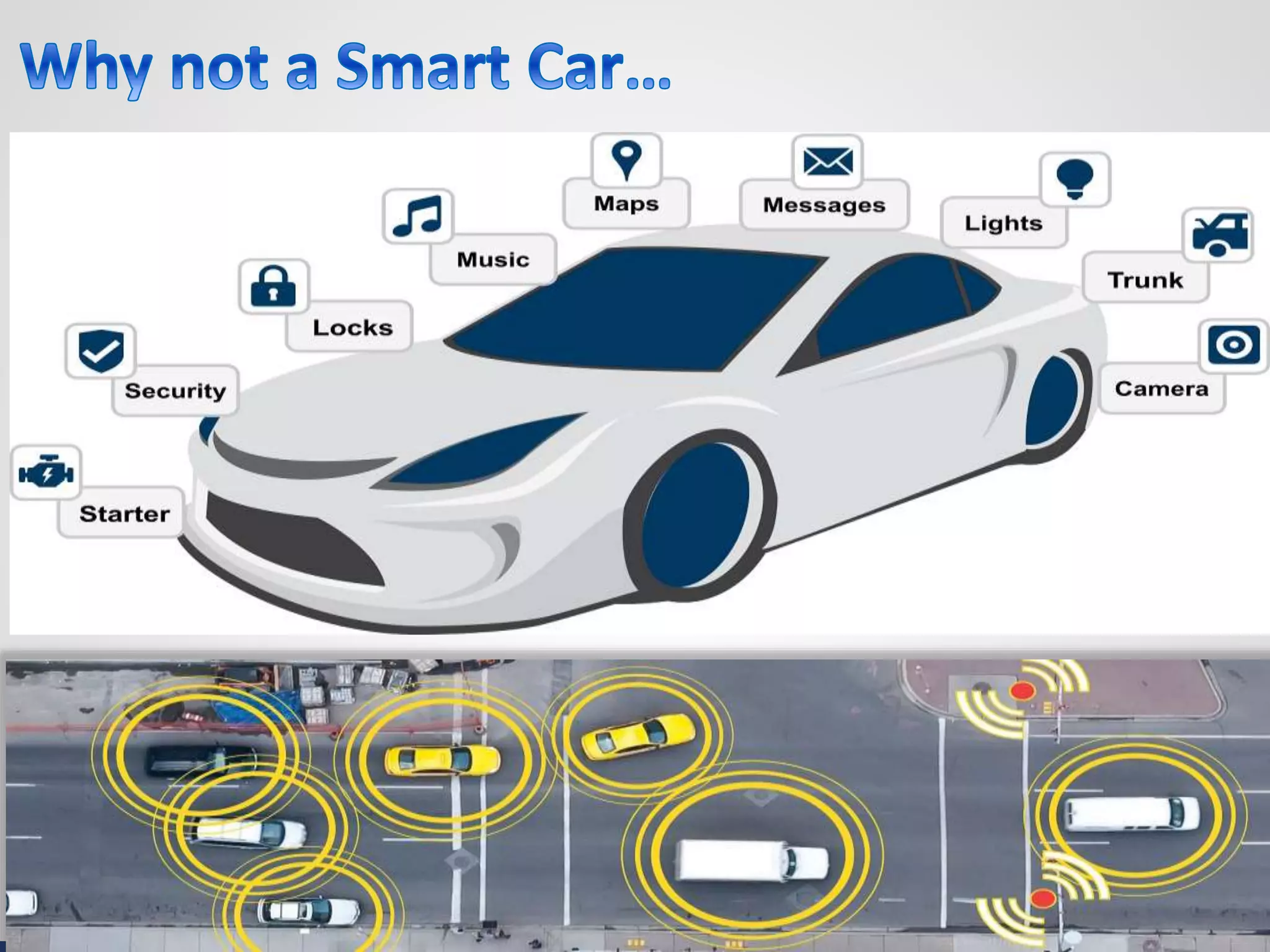
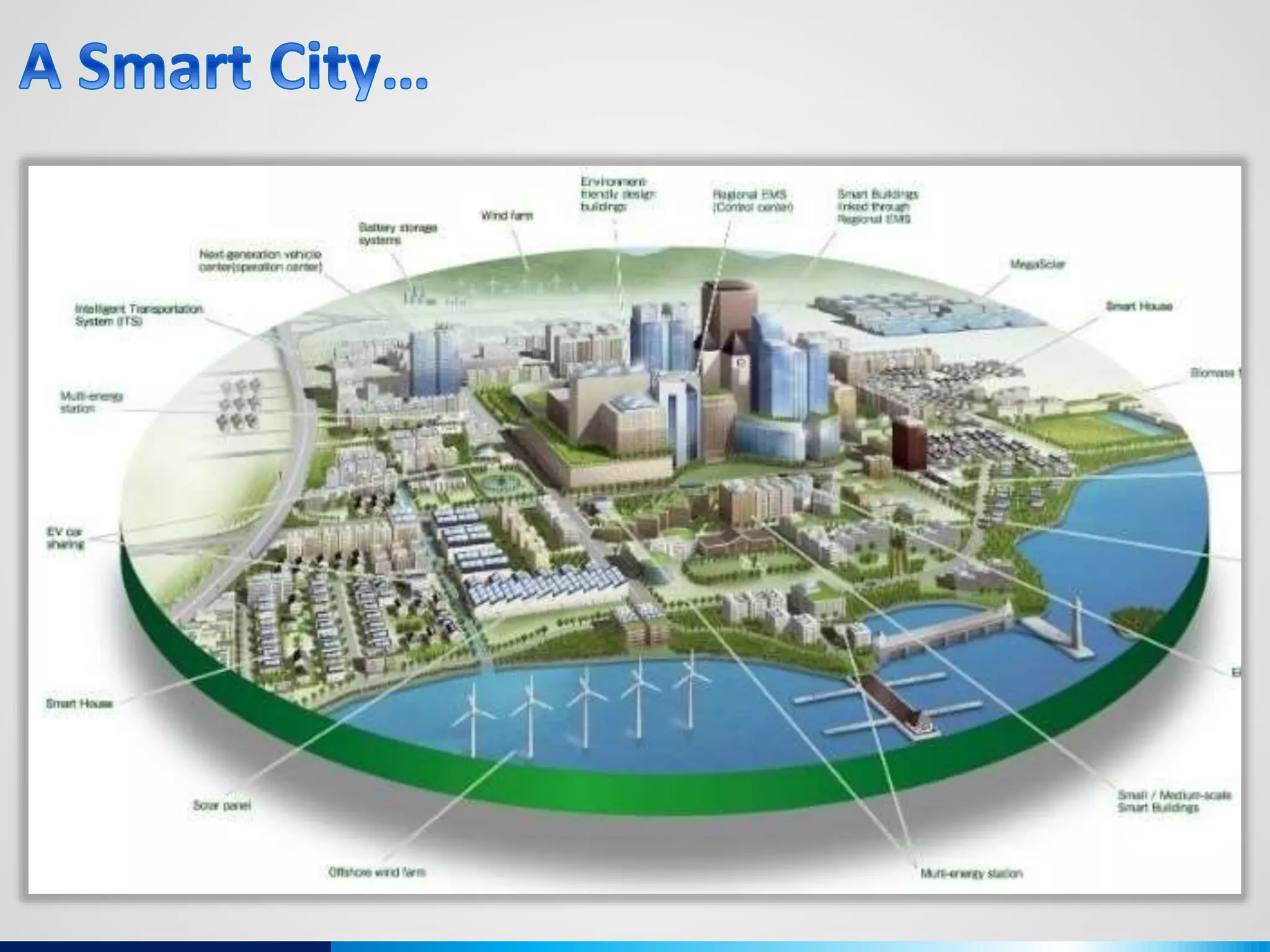
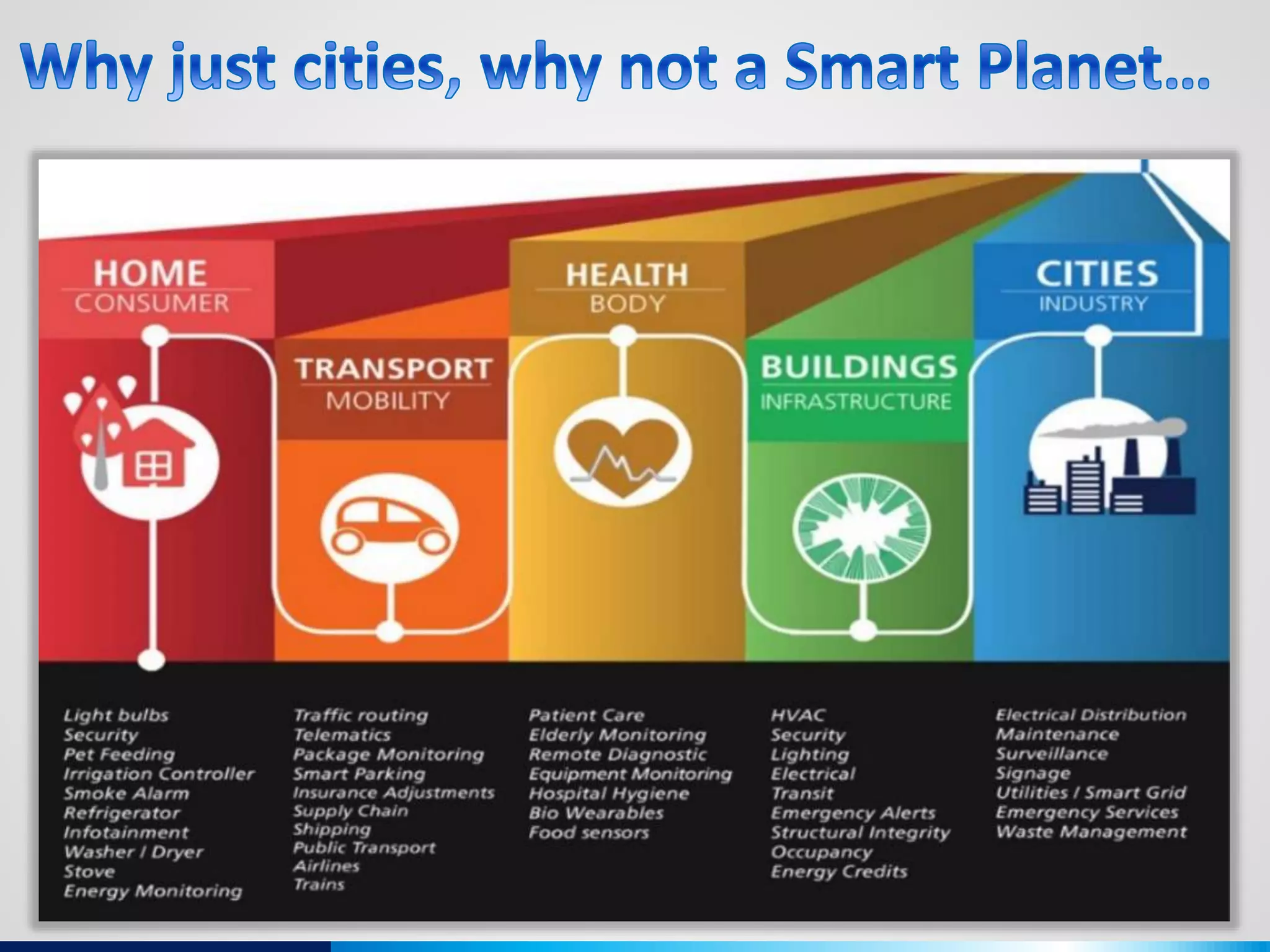
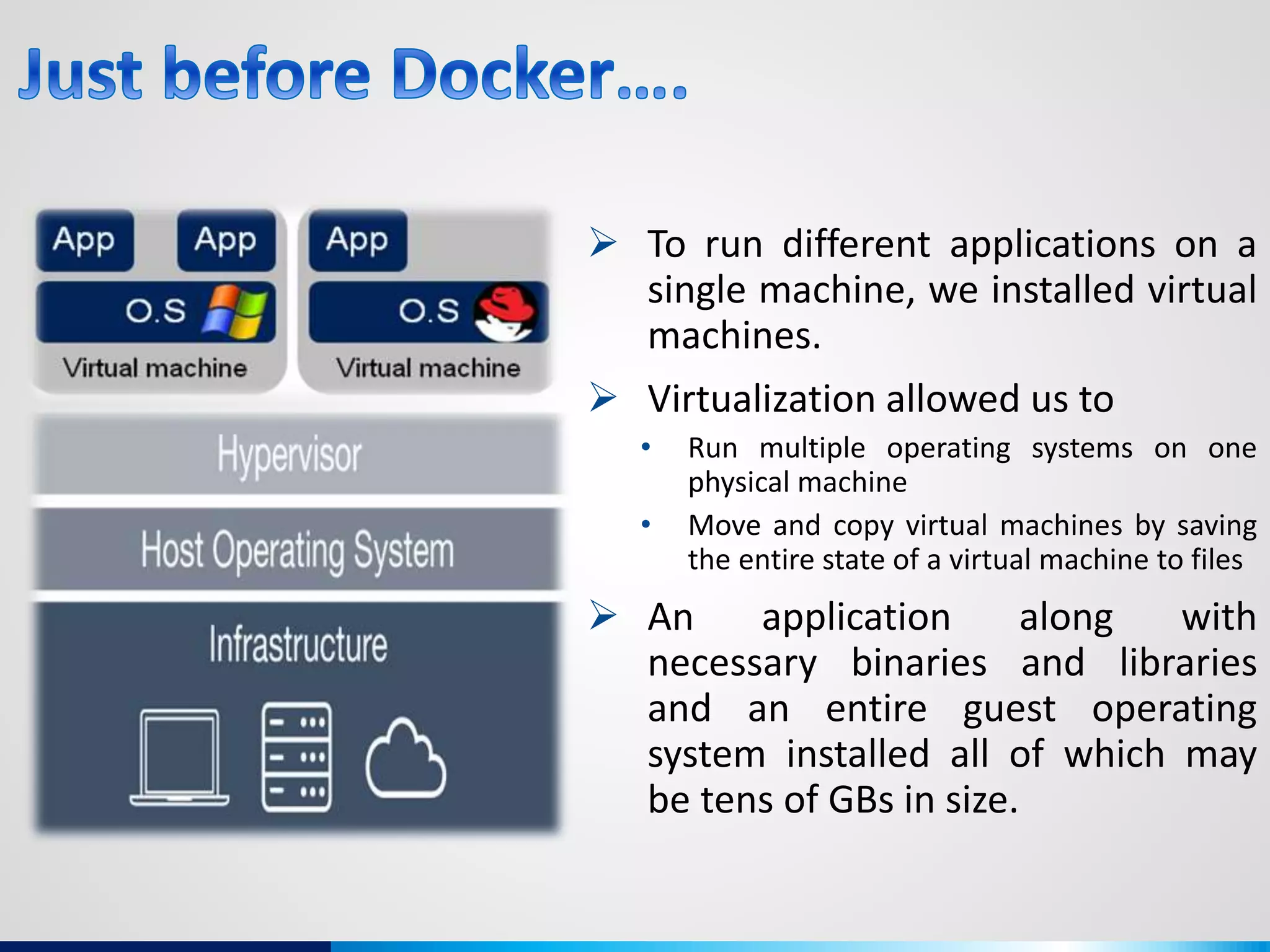
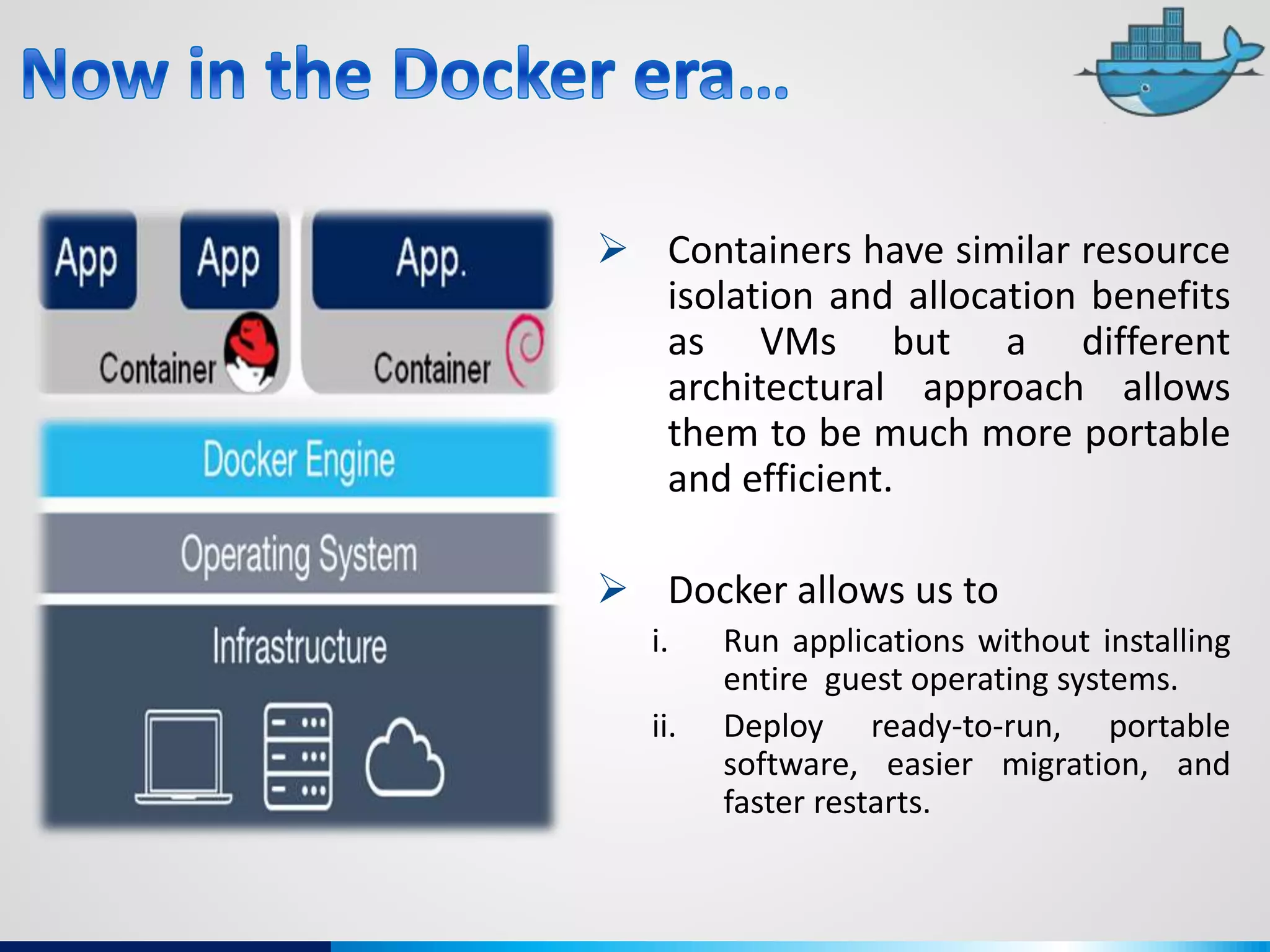
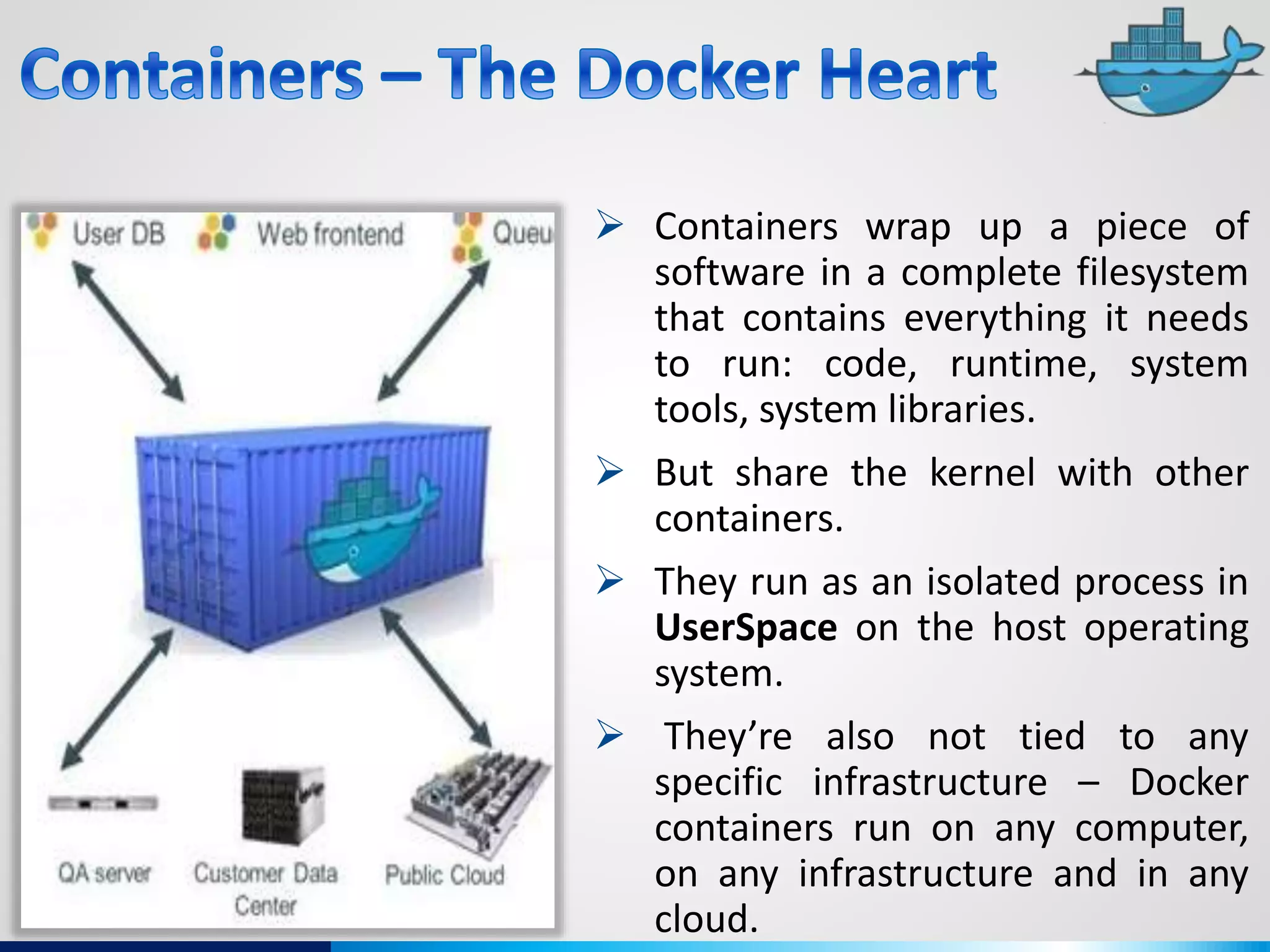
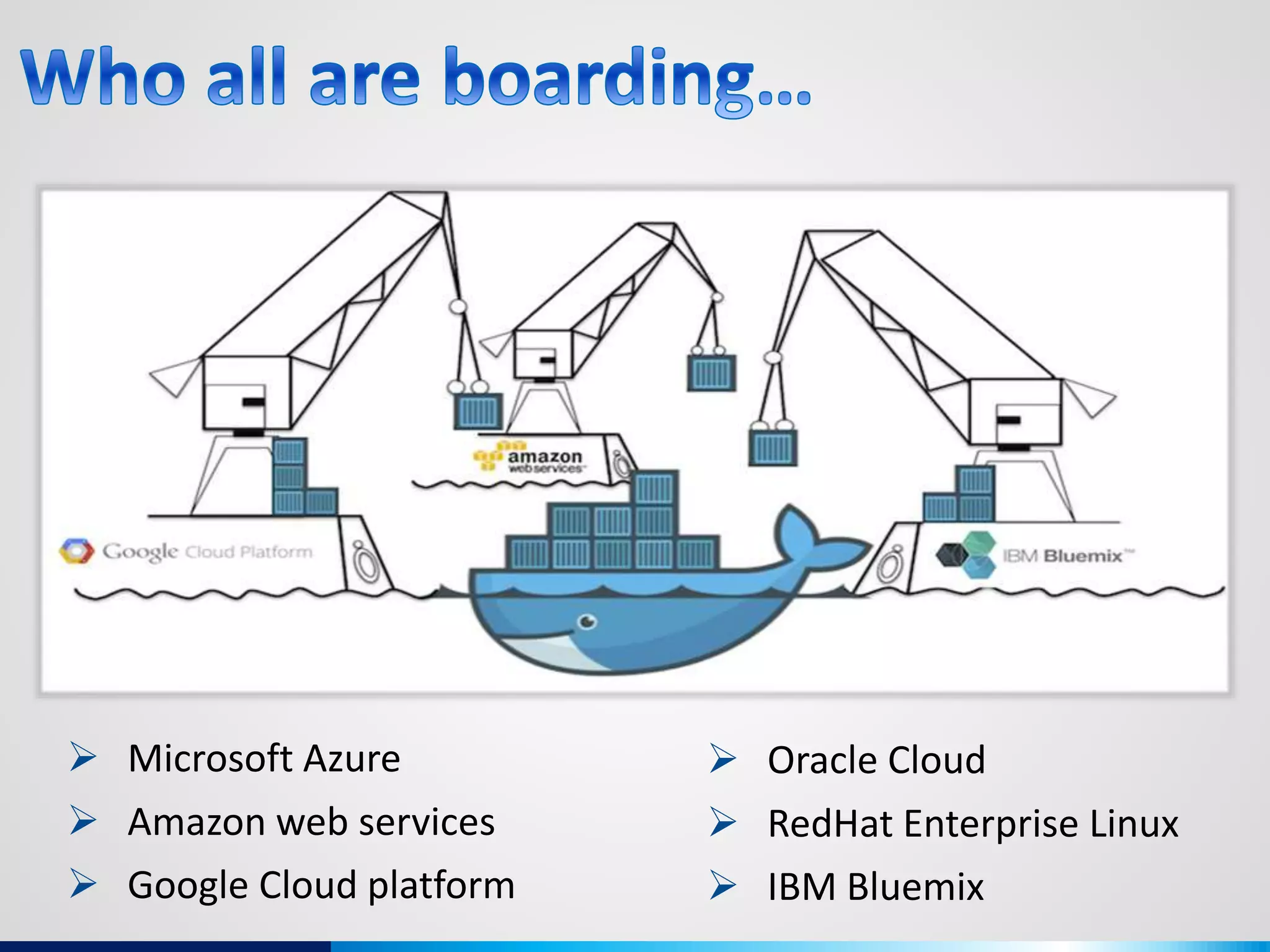
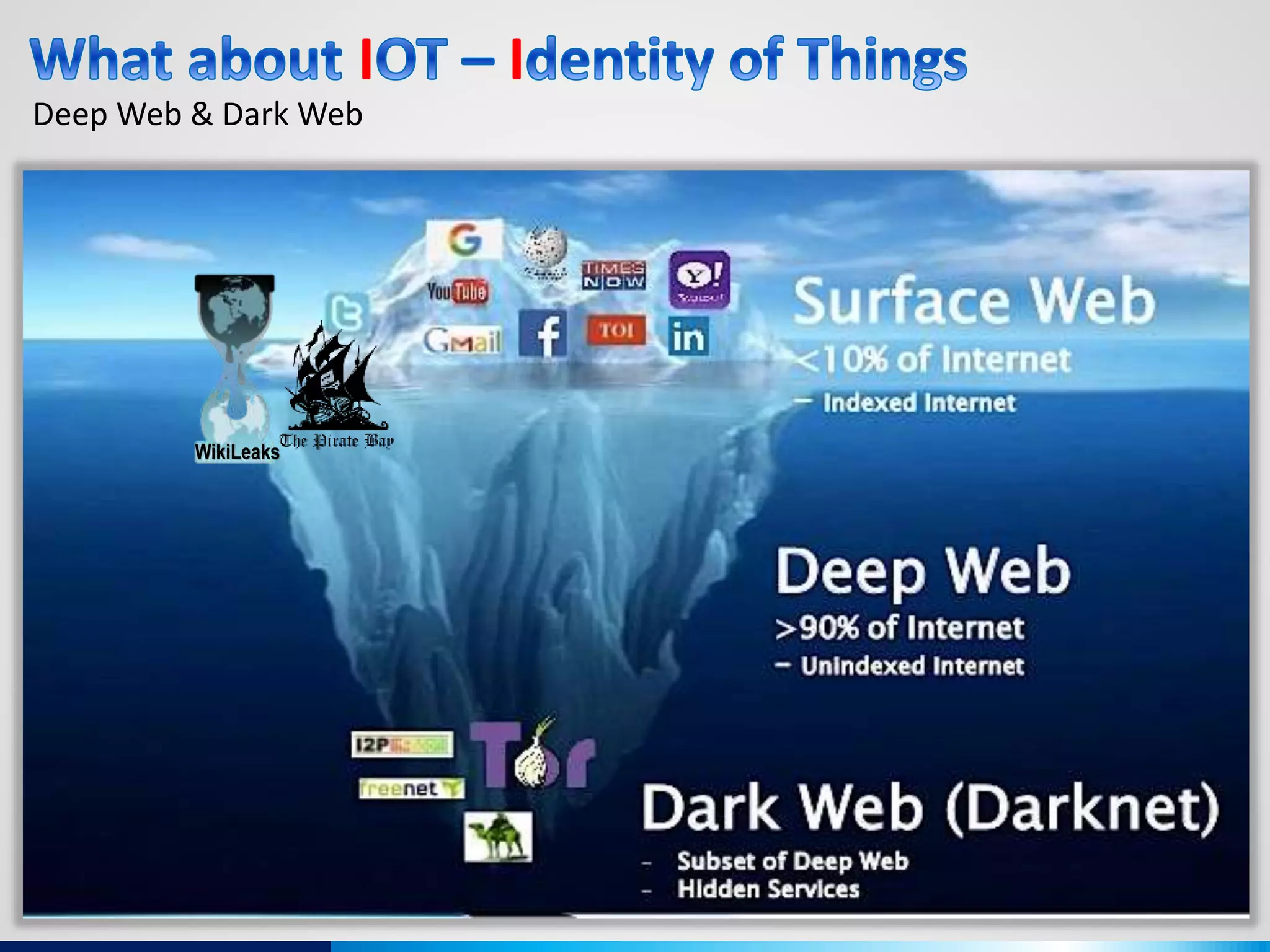
The document discusses various aspects of cybersecurity, including advanced persistent threats, virtualization, cloud security, and the implications of the Internet of Things (IoT) on privacy and anonymity. It highlights significant incidents of data breaches, the evolution of security technologies, and the use of containers in application deployment. Furthermore, it addresses the challenges posed by identity theft, surveillance, and the use of technologies like Tor for anonymous internet browsing.