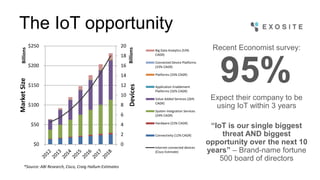
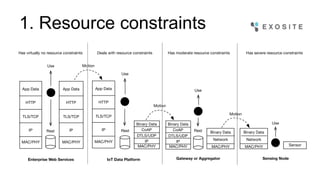
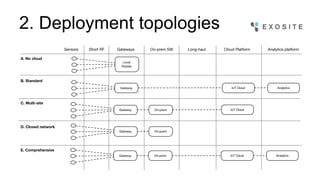
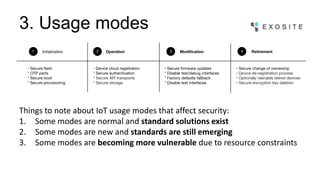
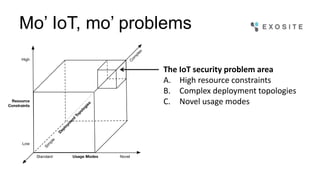
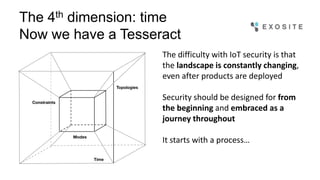
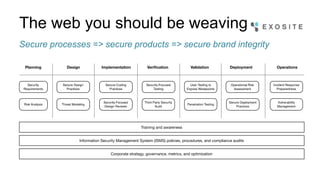
Mark Benson discusses the significant growth and risks associated with the Internet of Things (IoT), emphasizing that it presents both major opportunities and threats. The challenges in IoT security arise from resource constraints, complex deployment topologies, and evolving usage modes, requiring a proactive and adaptive security approach. Key recommendations include establishing a security architecture early, continuously evolving technology, and preparing operational responses to potential security incidents.