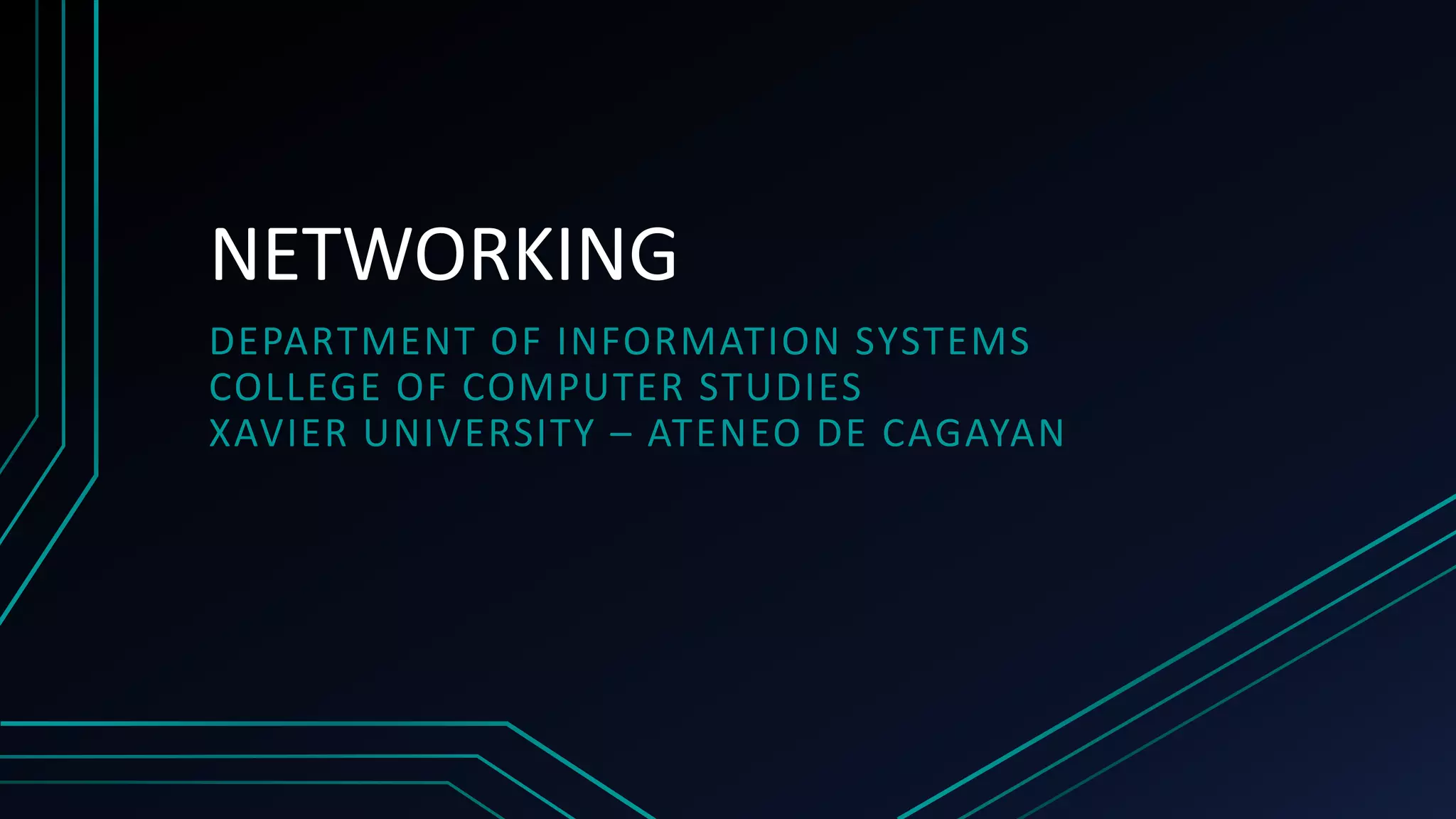
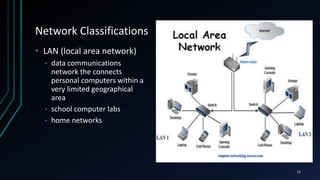
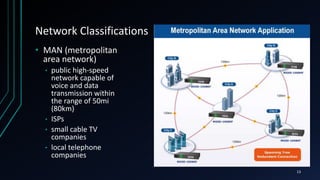
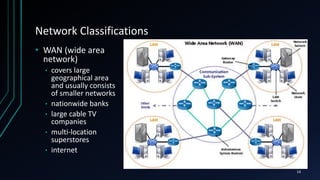
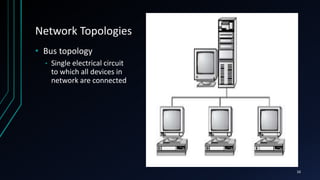
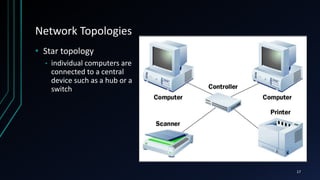
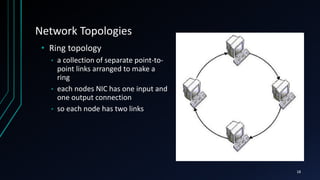
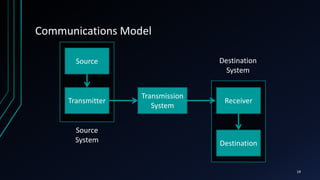
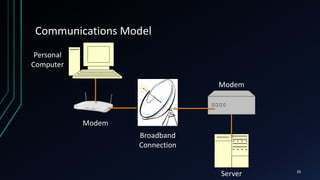
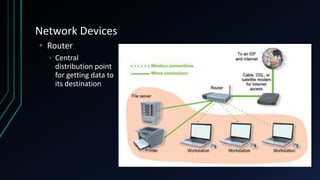
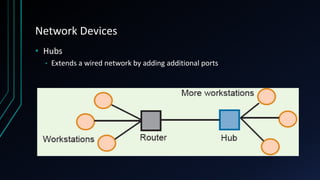
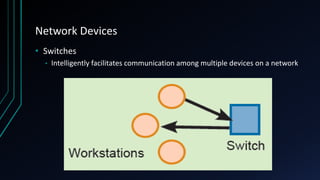
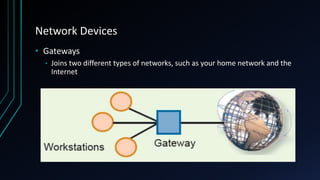
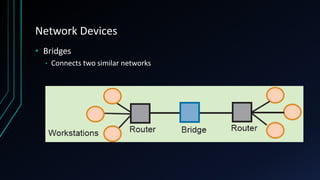
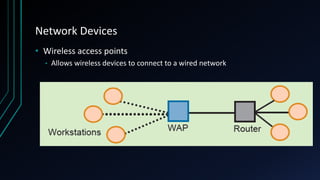
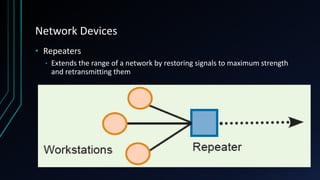
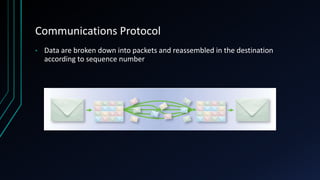
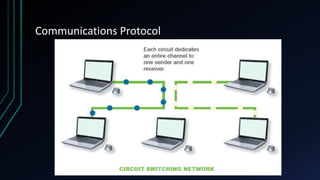
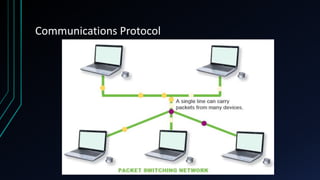
This document provides an overview of networking concepts including network components, topologies, and protocols. It defines what a network is as two or more connected computing devices that can share resources. The basic components are servers, clients, and circuits that connect them. Networks can be classified by size as personal area networks (PAN), local area networks (LAN), metropolitan area networks (MAN), or wide area networks (WAN). Common network topologies include bus, star, and ring configurations. The document also discusses network devices, links, and communications protocols like TCP/IP that regulate data transmission and packet routing.