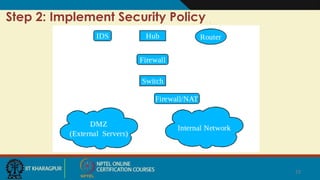
This document discusses cloud computing security and covers the following key points in 15 sentences or less:
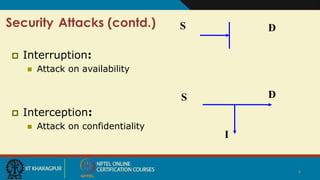
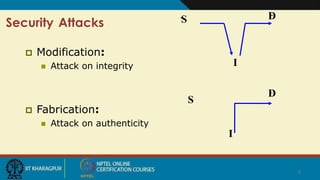
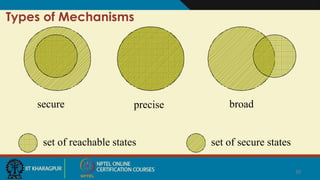
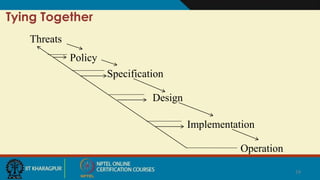
Cloud security involves ensuring confidentiality, integrity, and availability of data. There are four main types of security attacks: interruption, interception, modification, and fabrication. Security threats can be classified as disclosure, deception, disruption, or usurpation. Security policies define what is and is not allowed, while mechanisms enforce these policies. Security aims to prevent attacks, detect violations, and enable recovery from any successful attacks. Trust and assumptions underlie all aspects of security policies, mechanisms, operations, and issues.