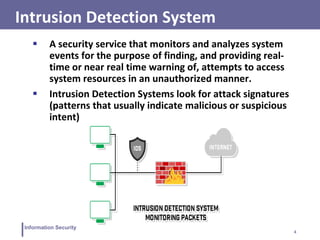
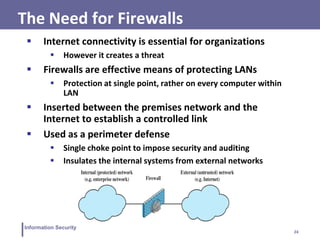
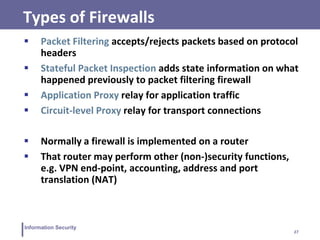
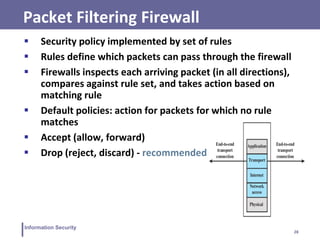
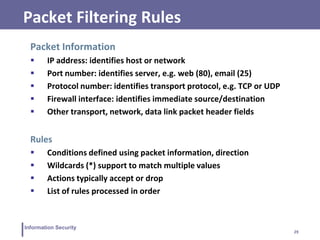
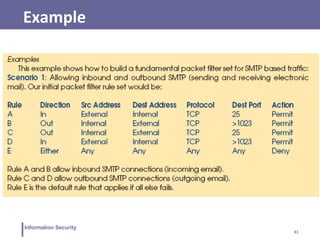
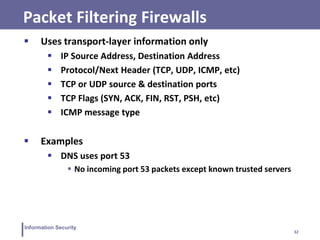
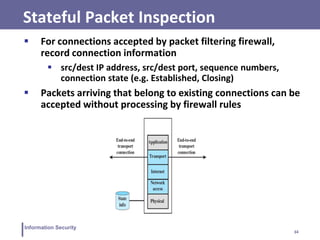
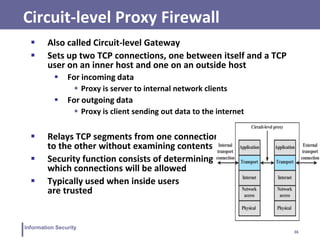
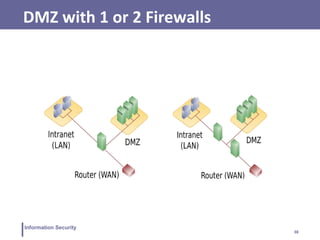
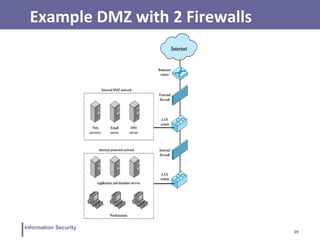
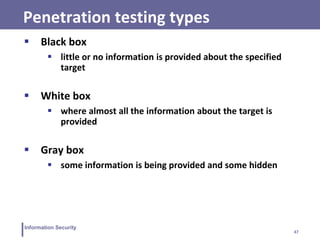
This document discusses information security and intrusion detection. It defines intrusion as an attempt to break into or misuse a system. There are three classes of intruders: masqueraders, misfeasors, and clandestine users. Intrusion detection systems (IDS) monitor systems for signs of intrusion and provide warnings. IDS use sensors to collect data, analyzers to detect intrusions, and user interfaces to view outputs. IDS can operate using anomaly detection, misuse detection, hybrid detection, or specification-based detection. The document also discusses honeypots, which are decoy systems that aim to divert attackers from critical systems.