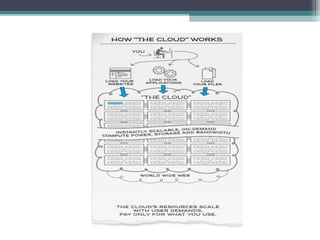
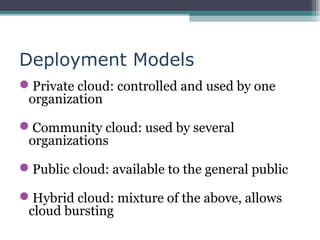
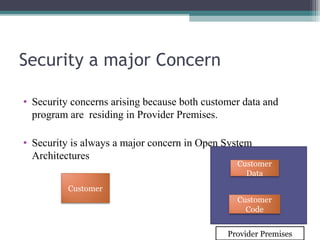
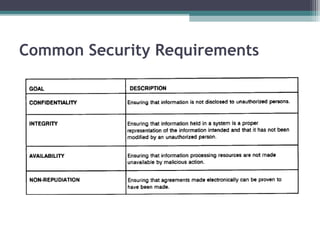
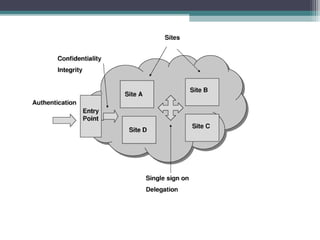
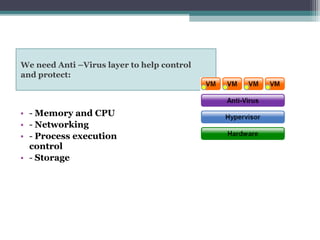
The document discusses the security concerns associated with cloud computing, emphasizing the importance of managing customer data safely in a shared environment. It outlines various cloud deployment models and highlights essential security requirements across multiple levels, including server and data access. Additionally, it addresses issues related to data redundancy, encryption, and the challenges of ensuring secure communication and operational integrity within cloud infrastructures.