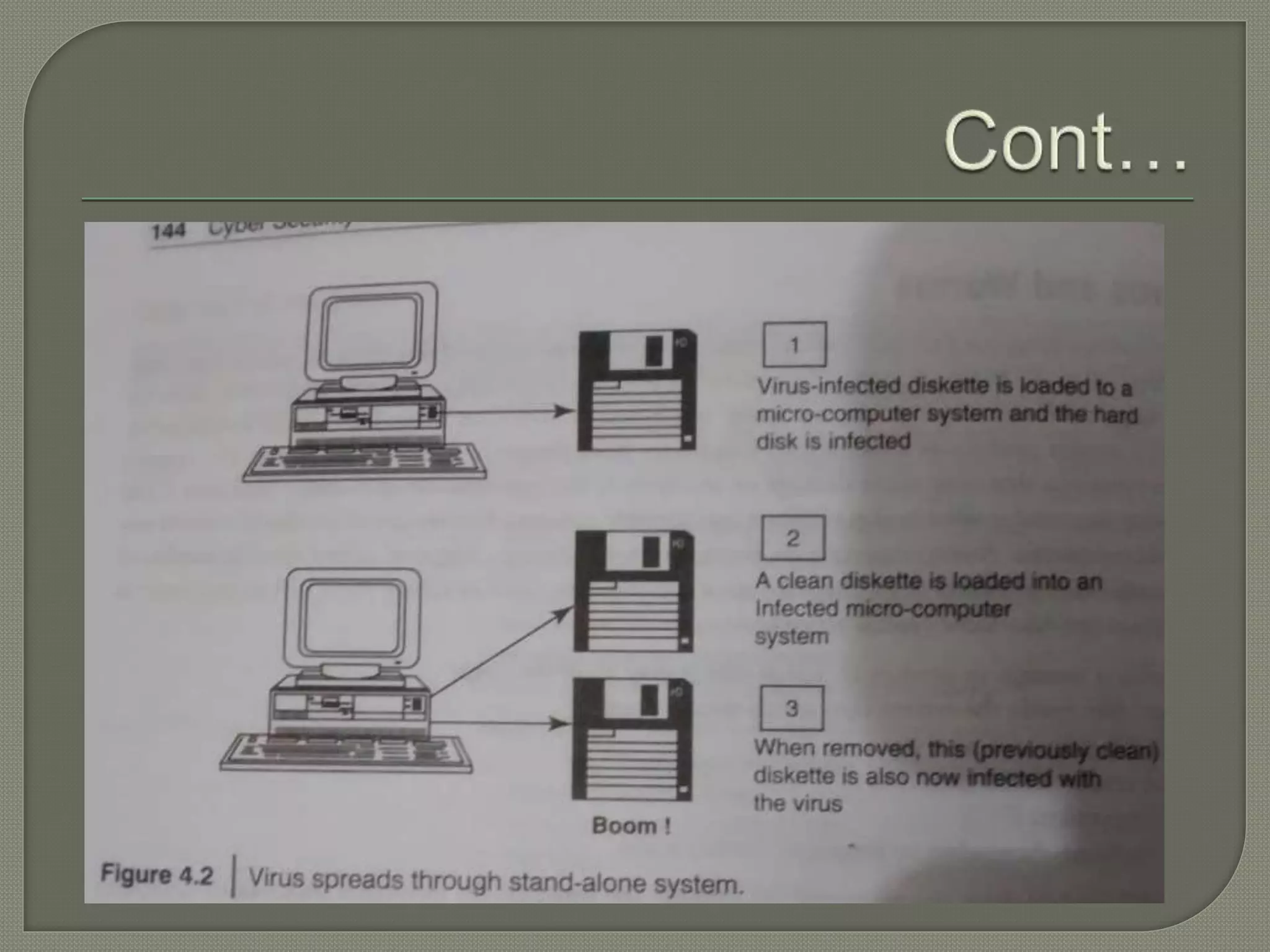
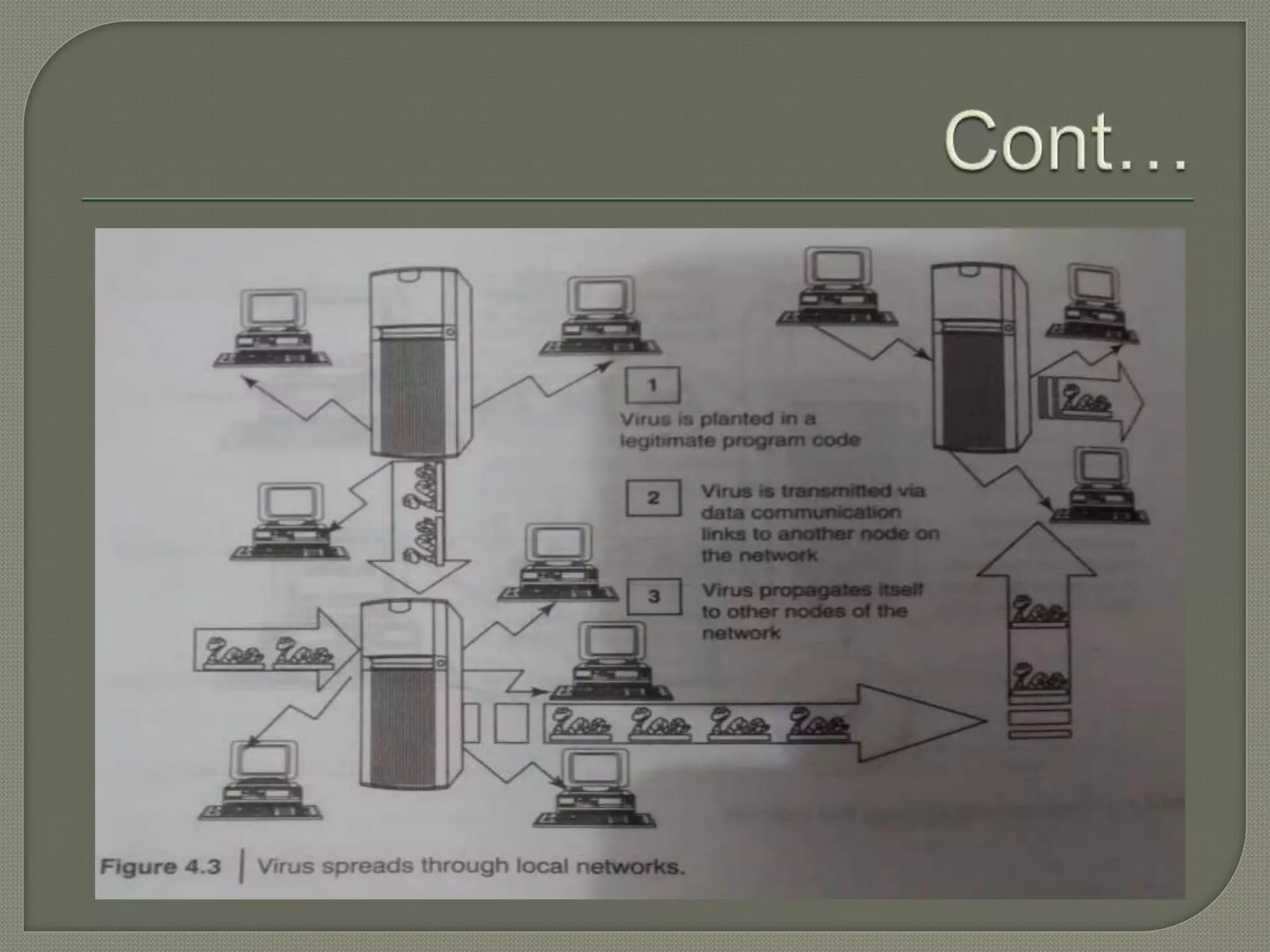
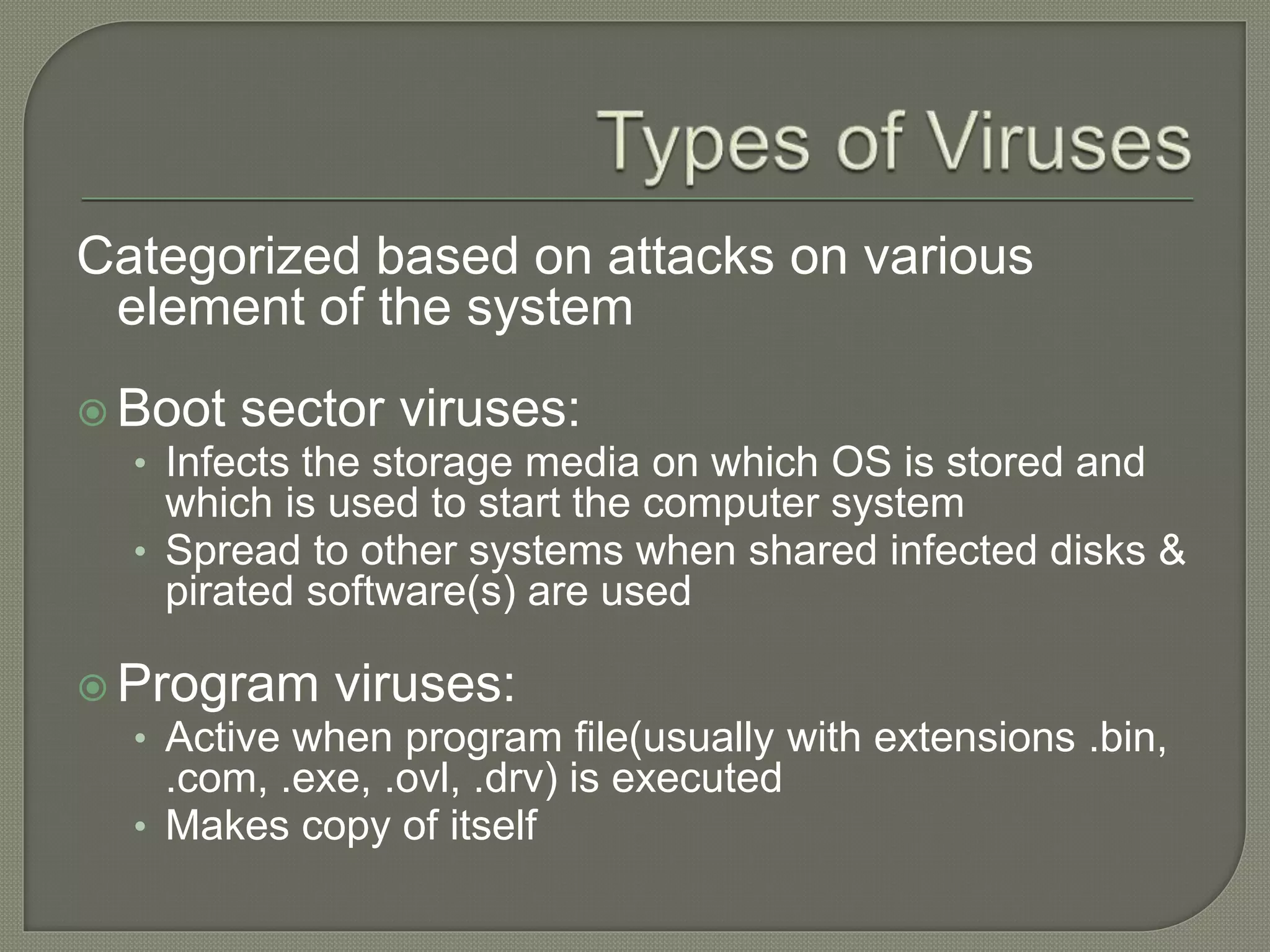
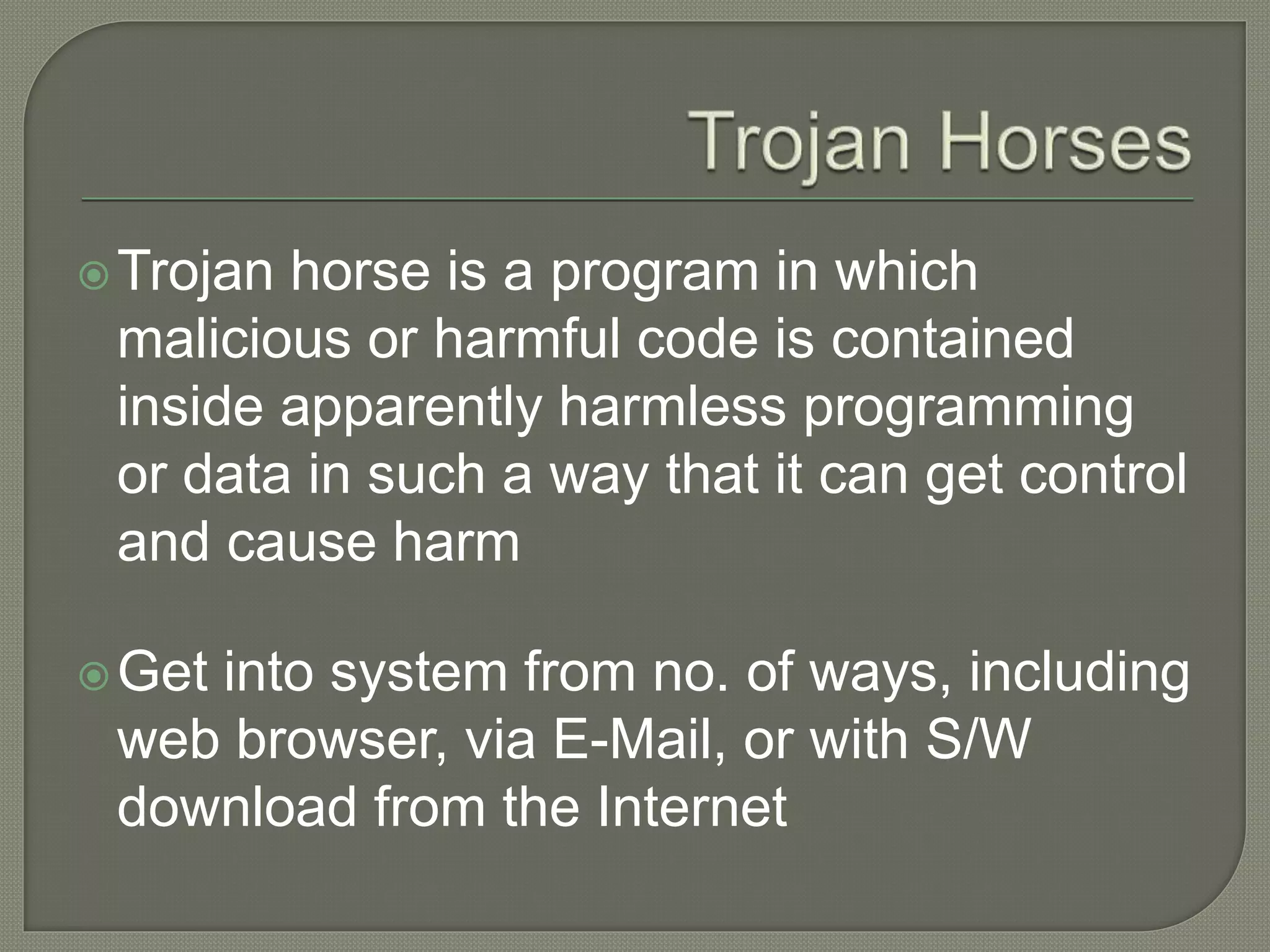
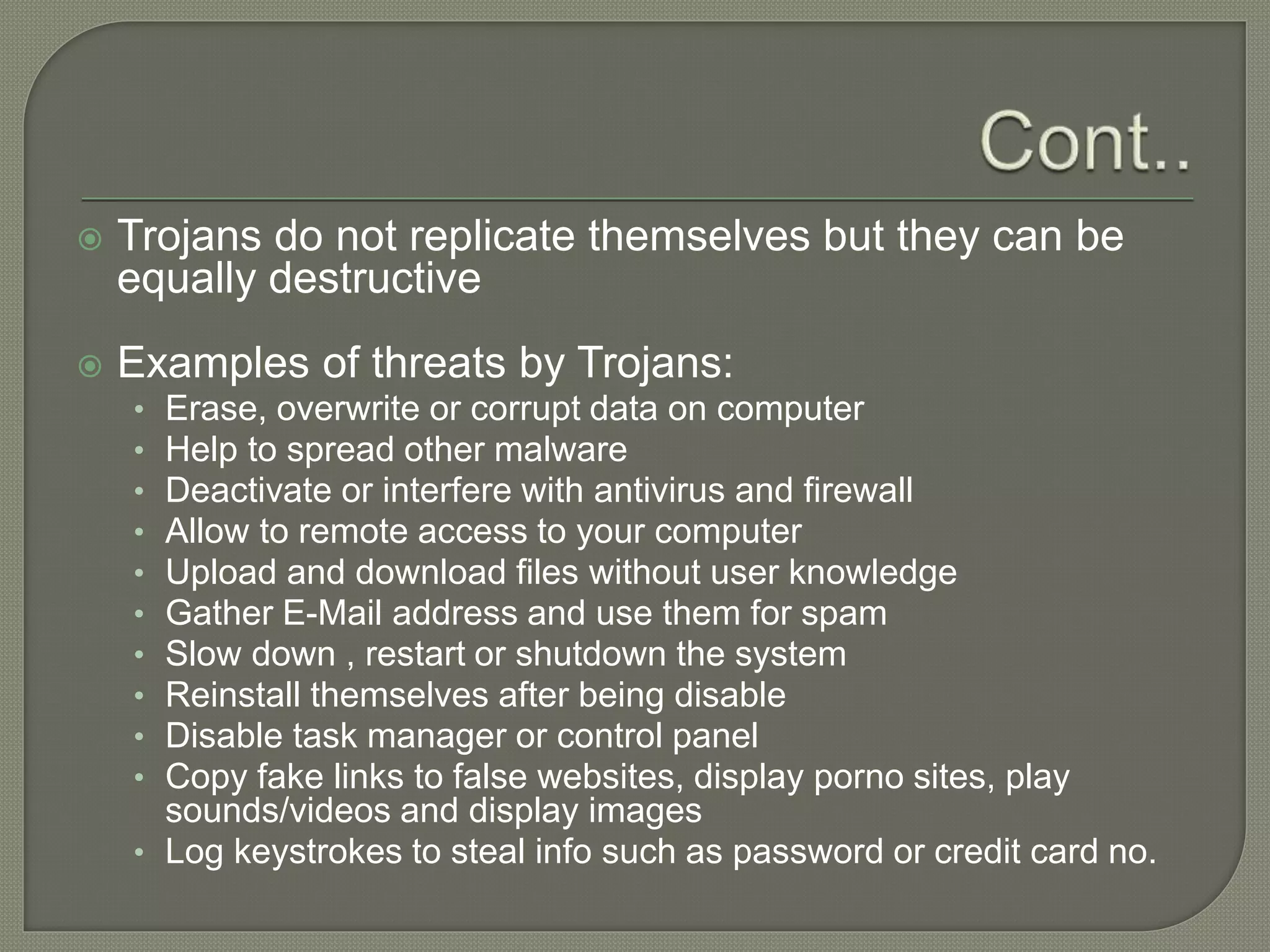
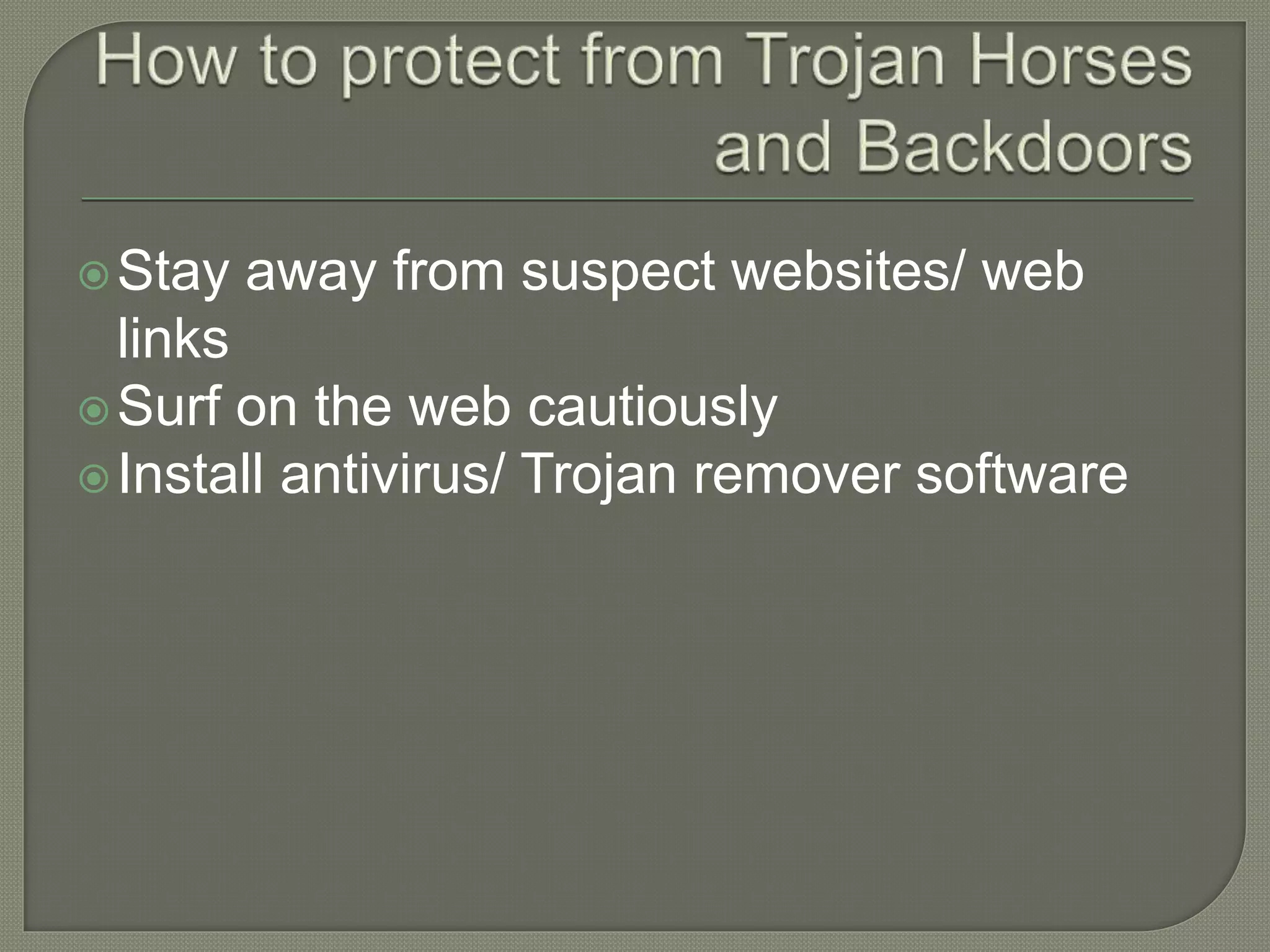
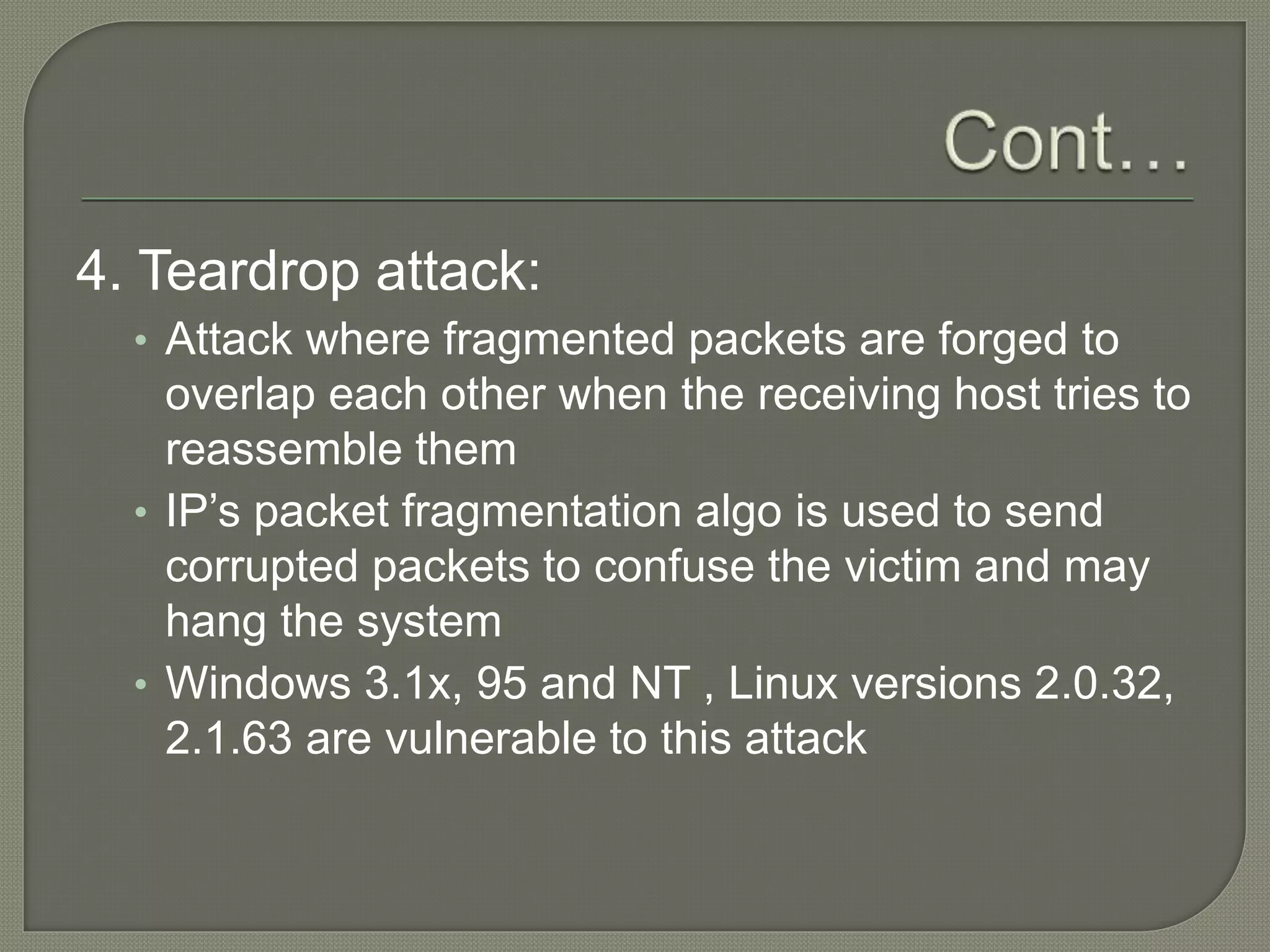
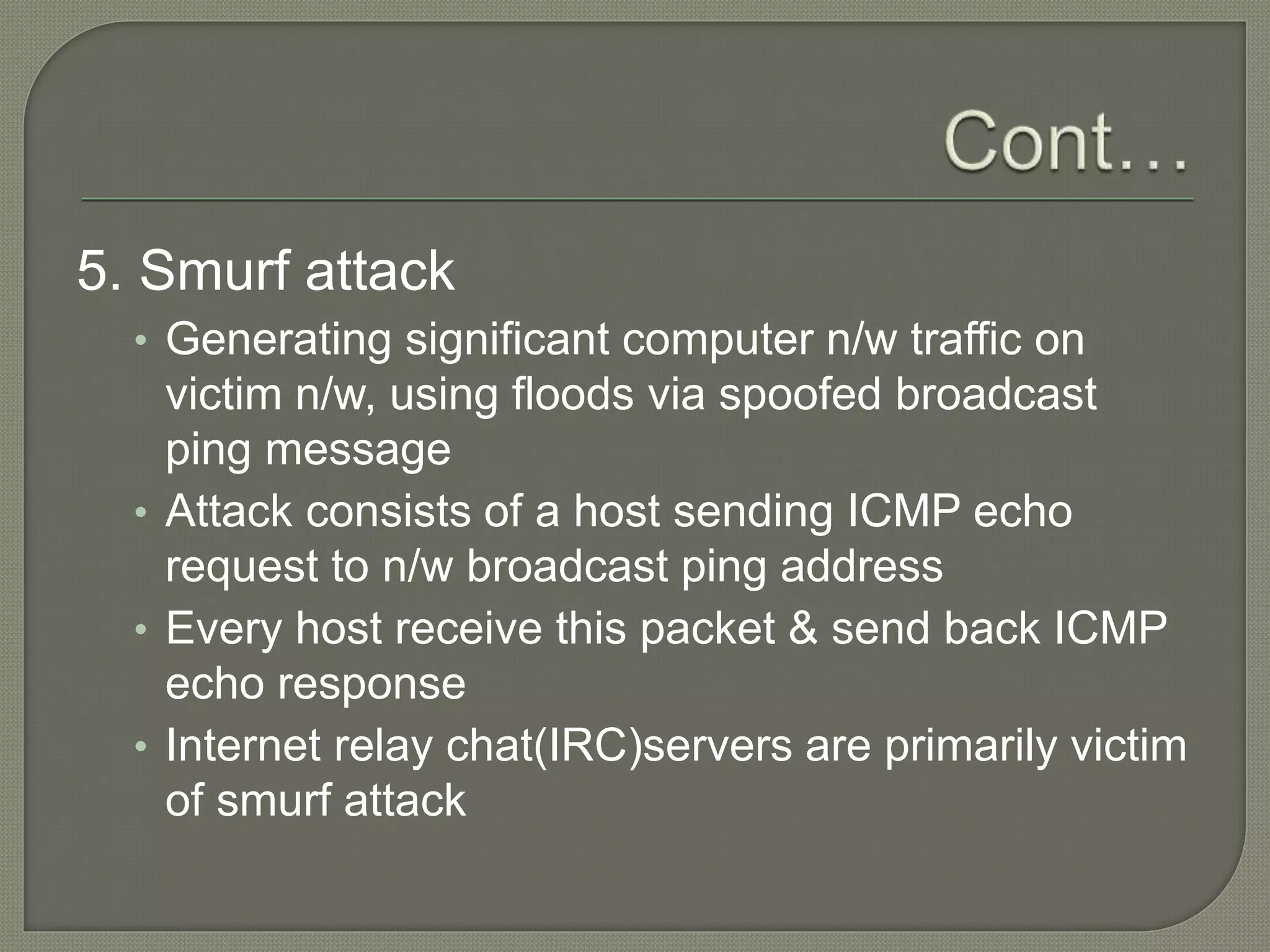
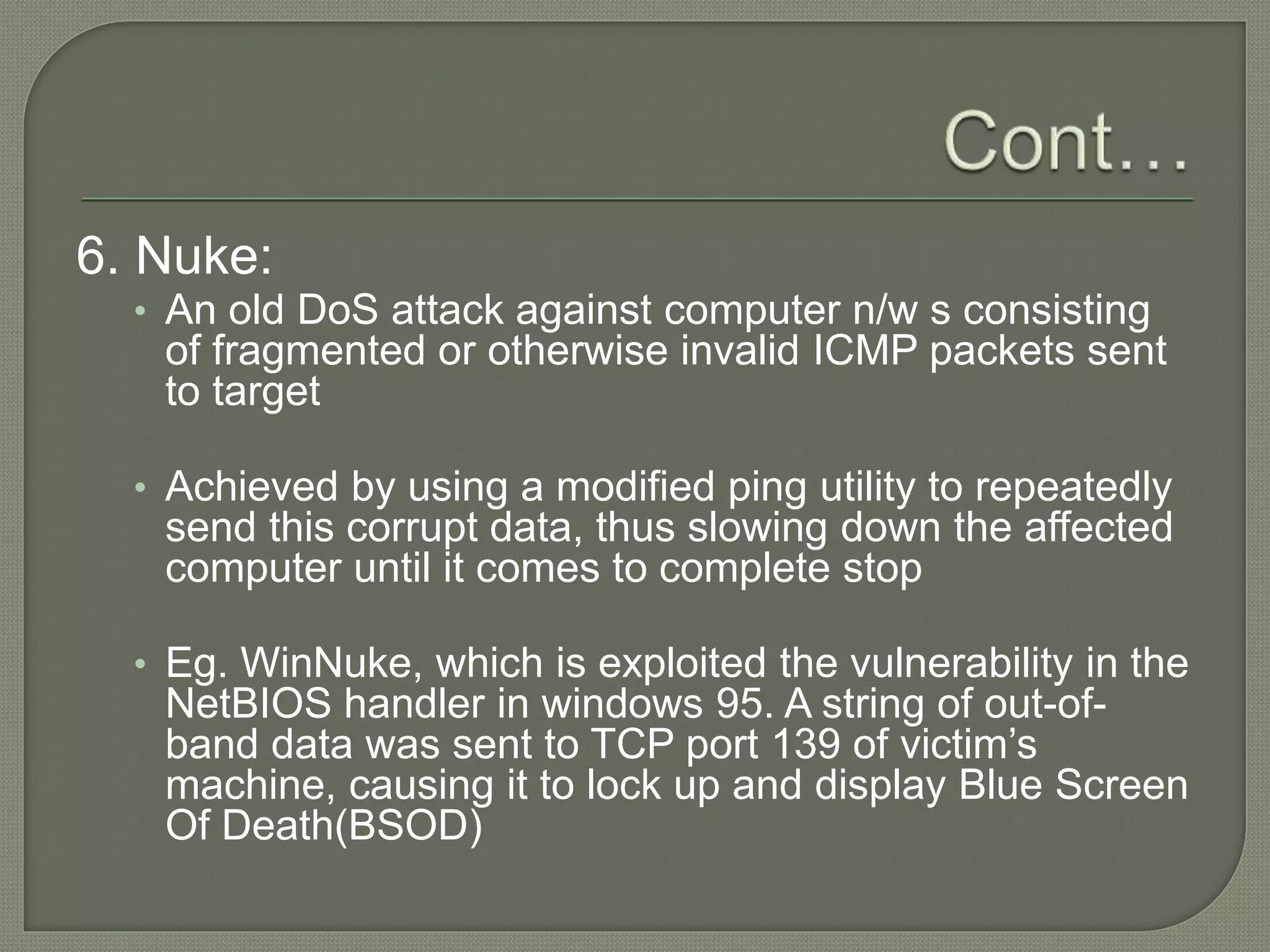
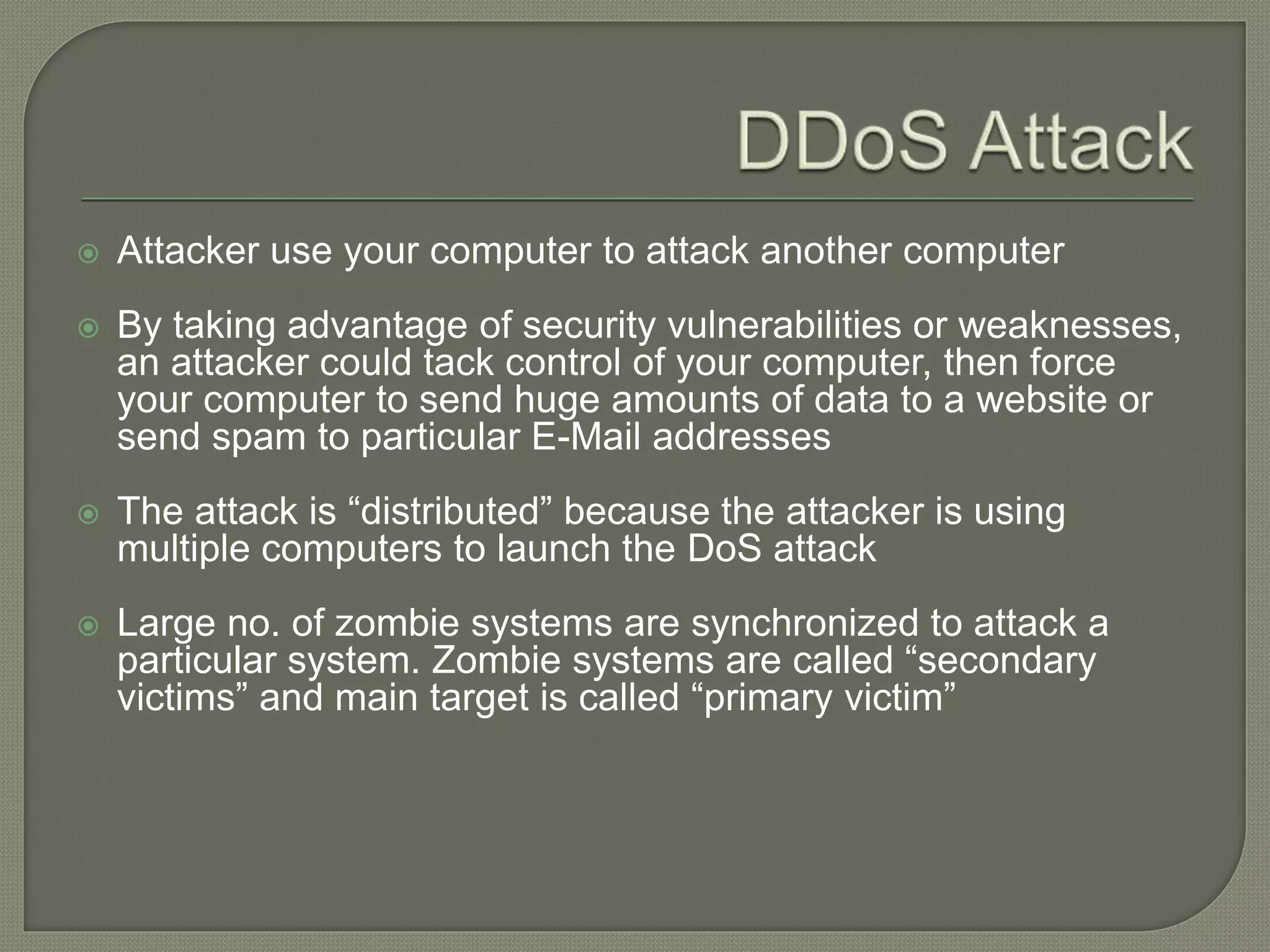
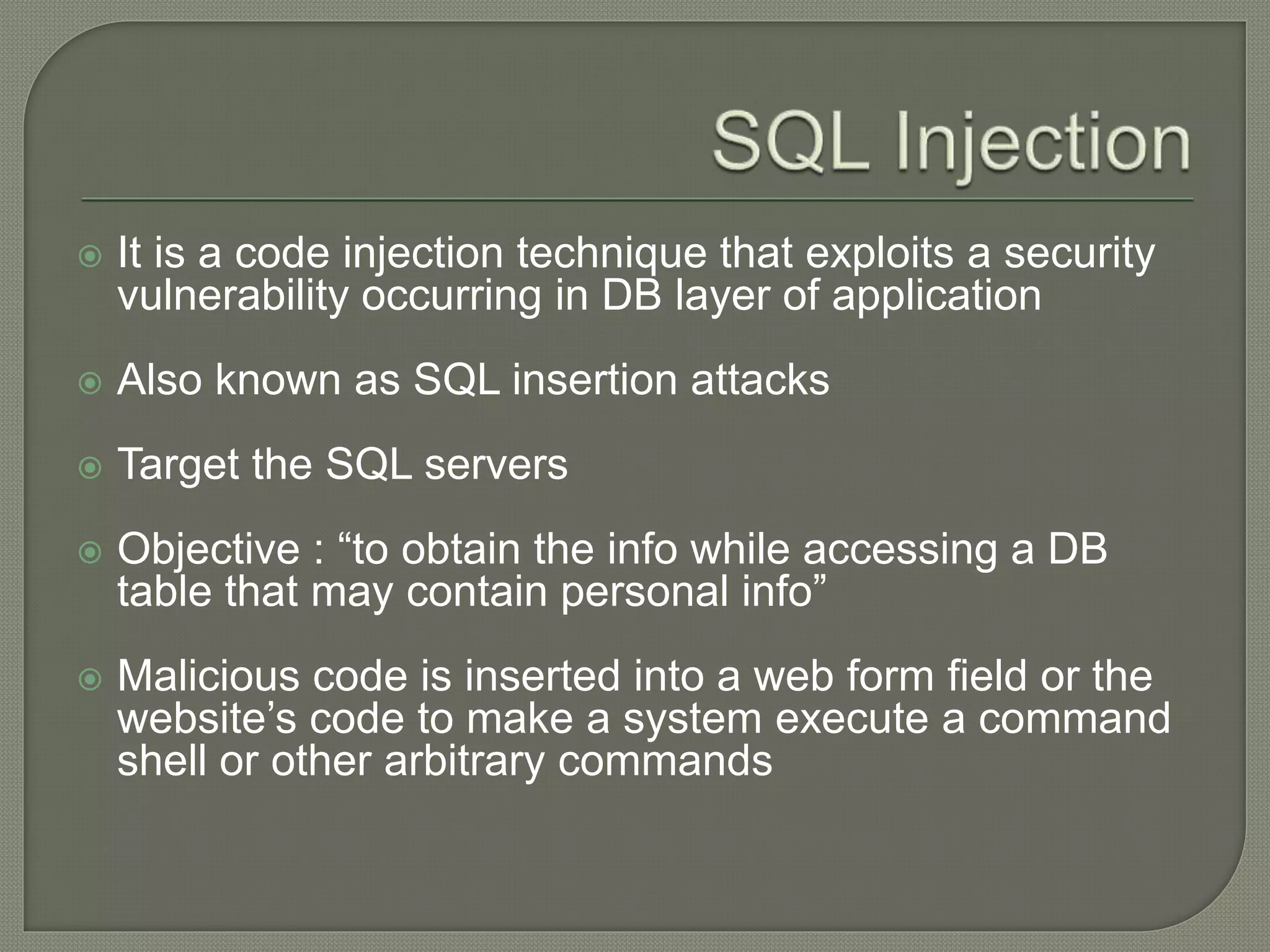
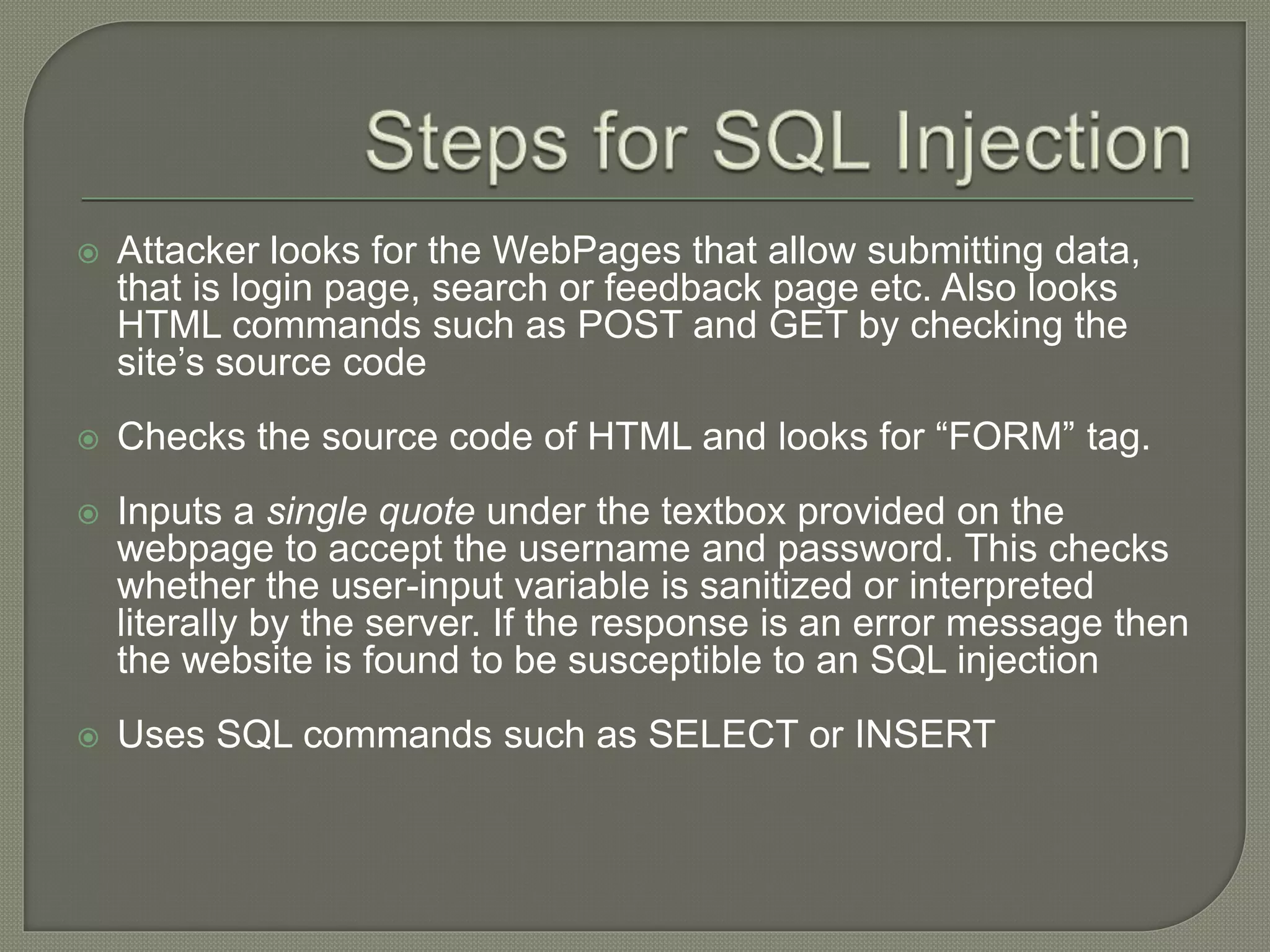
The document discusses various tools and methods used in cybercrime, including proxy servers, anonymizers, phishing, password cracking, keyloggers, viruses, worms, Trojan horses, backdoors, steganography, denial of service attacks, SQL injection, and buffer overflows. It provides details on how each method works and how attackers use them to launch cyber attacks. The document also outlines the basic stages of a cyber attack, from initial reconnaissance to covering tracks.