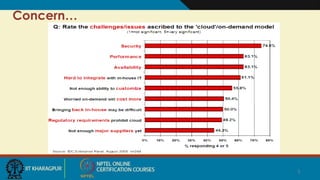
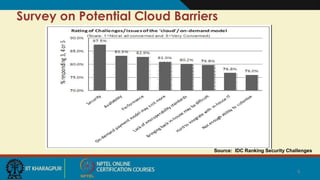
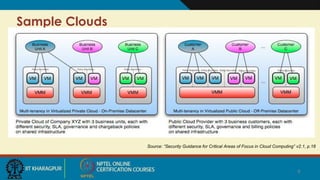
The document discusses security issues related to cloud computing. It begins by defining cloud computing and its economic advantages for consumers and providers. However, security concerns are a barrier to wider adoption of cloud computing. The document then examines seven specific security risks identified by Gartner: privileged user access, regulatory compliance and audit, data location, data segregation, recovery, investigative support, and long-term viability. Additional security issues discussed include virtualization, access control, application security, and data life cycle management. Throughout, the document emphasizes the importance of customers understanding security responsibilities and having visibility into a cloud provider's security practices.