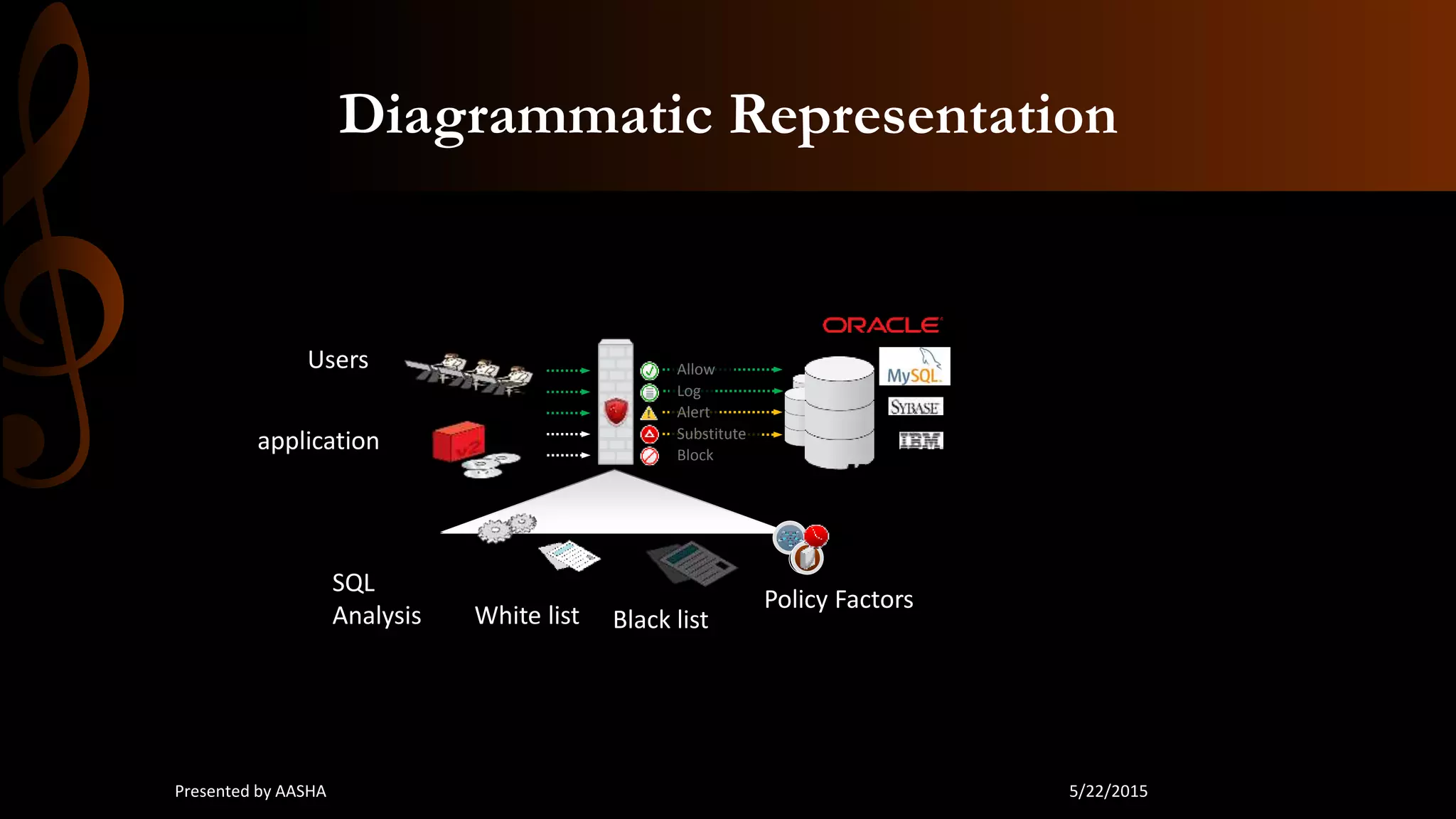
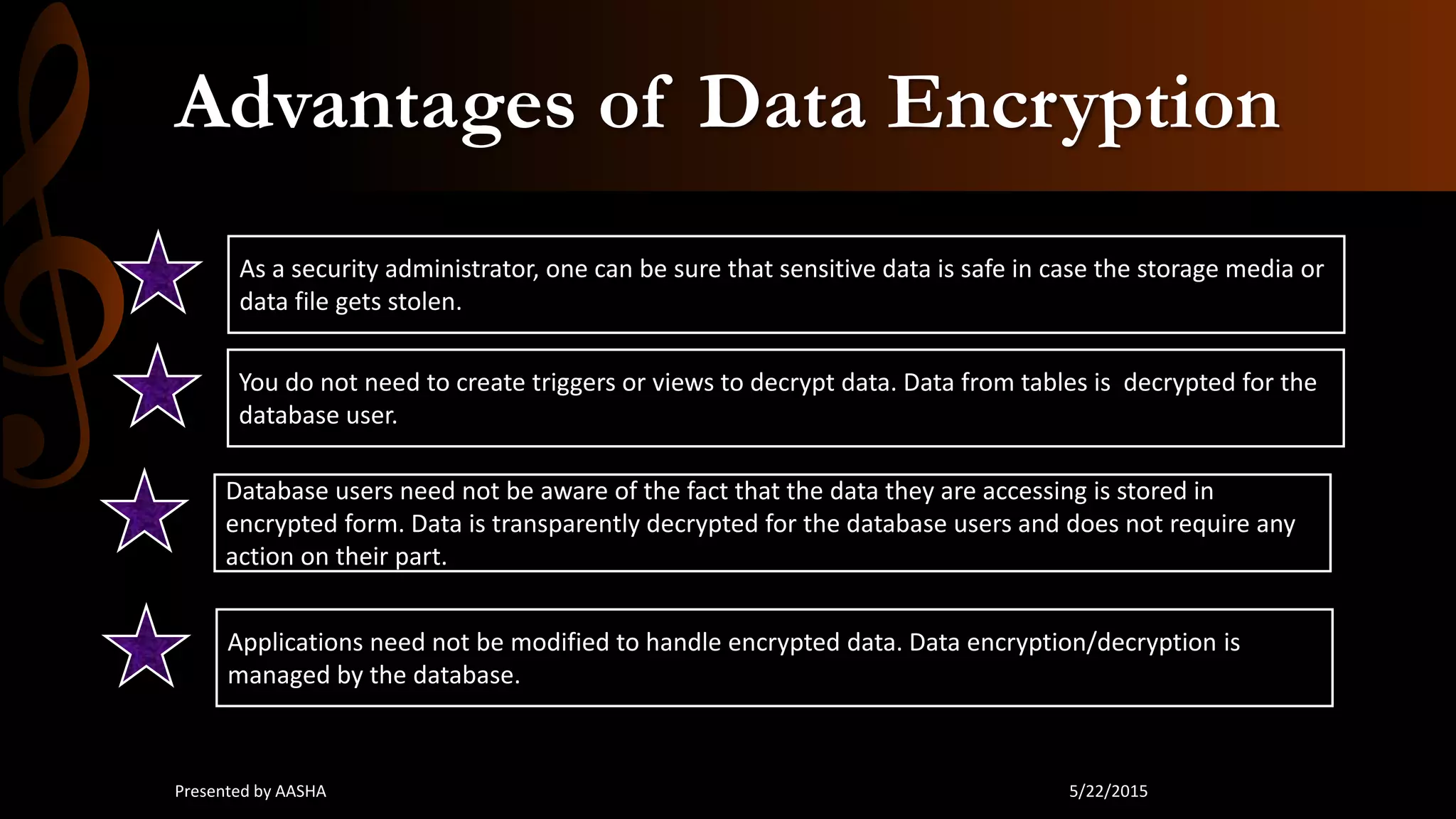
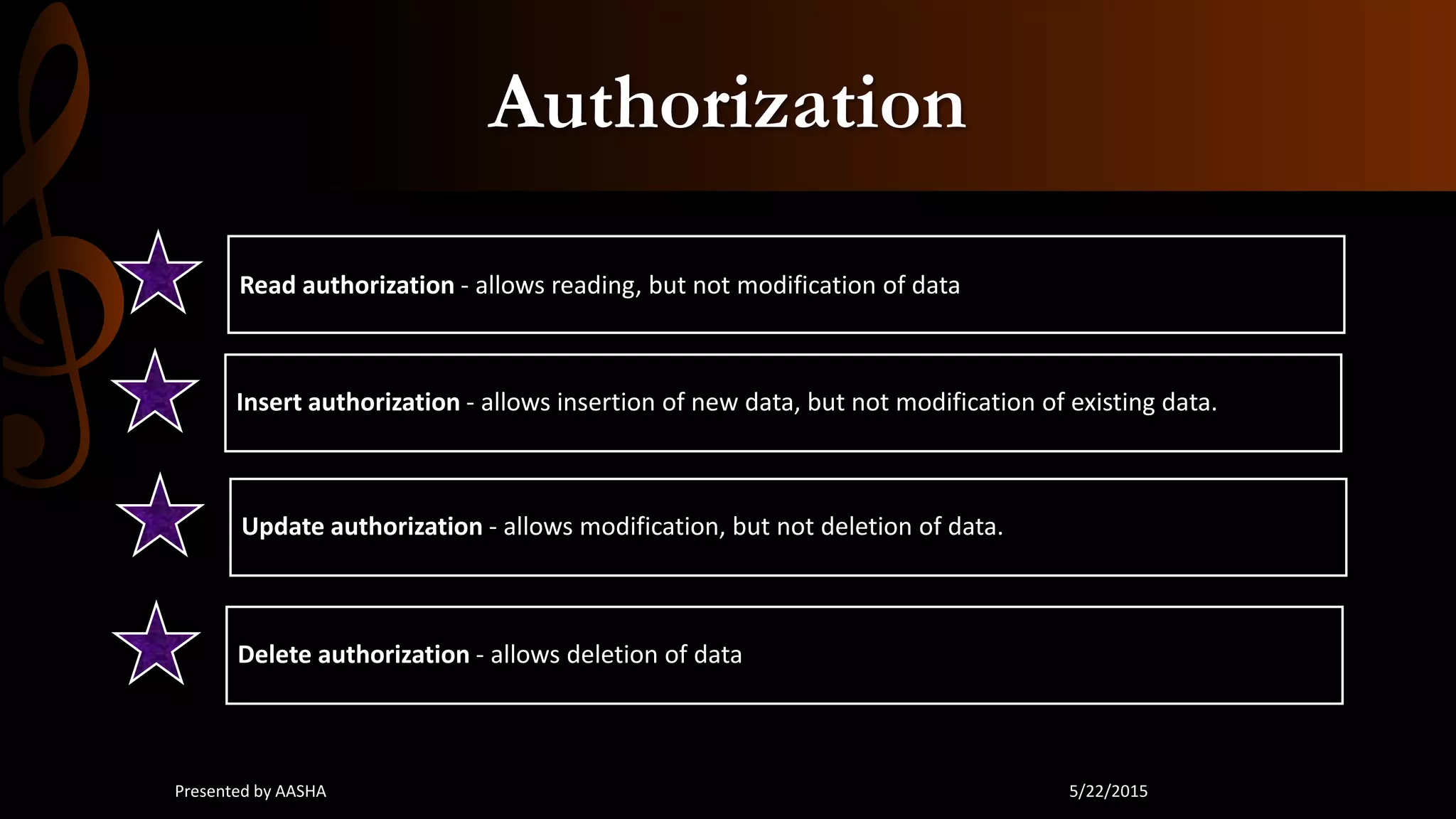
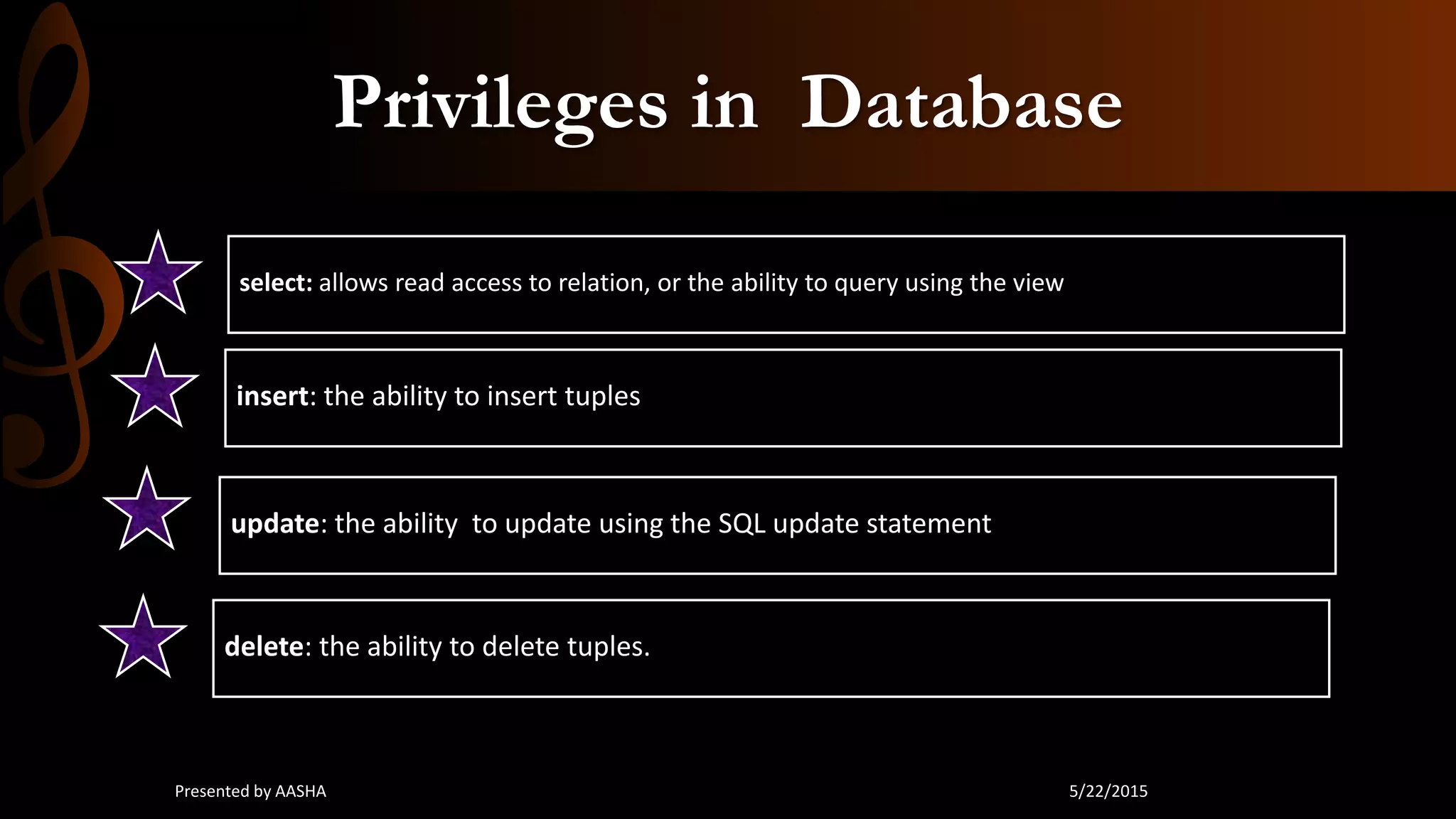
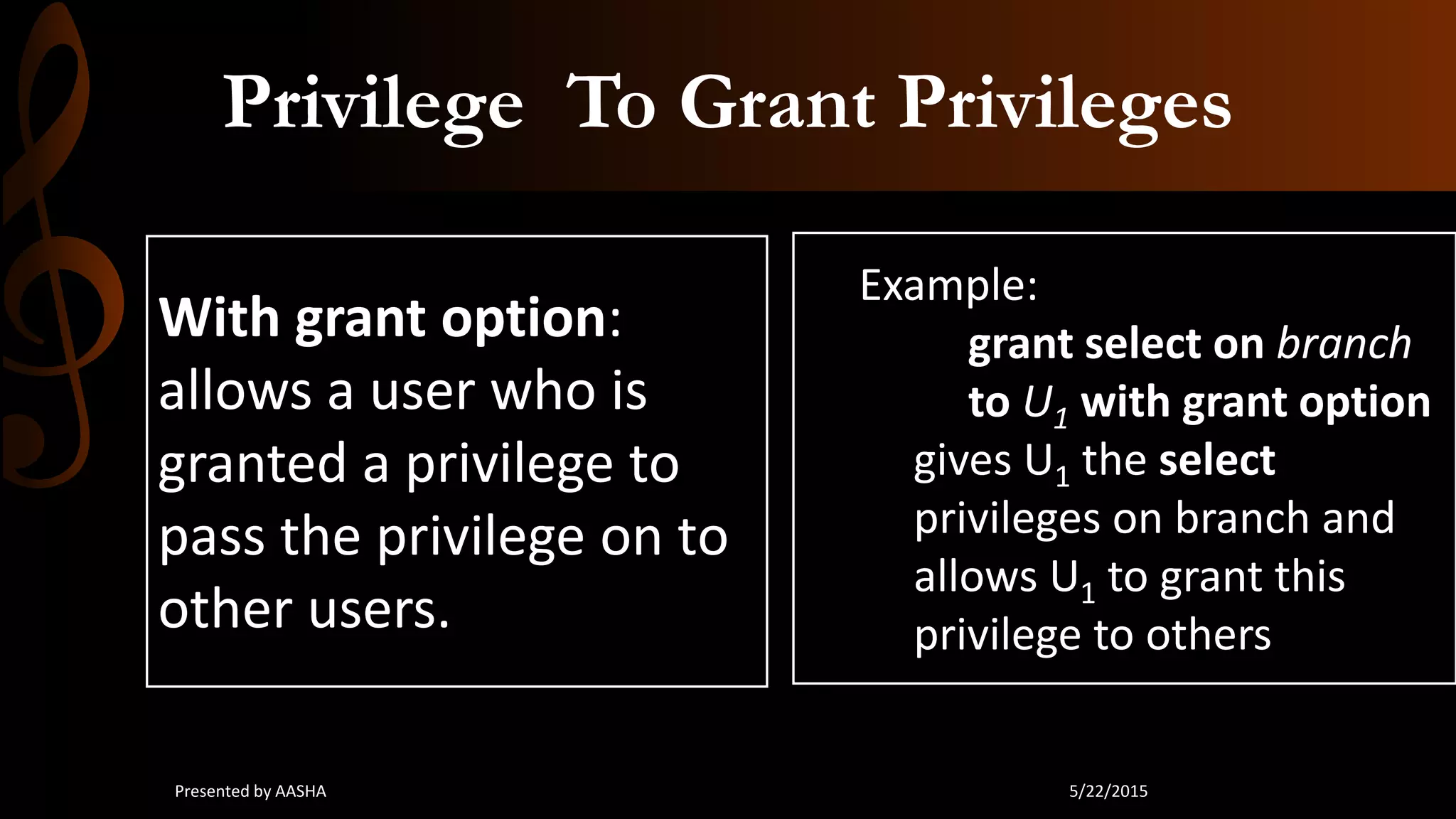
This document discusses database security, emphasizing the importance of protecting sensitive data from unauthorized access and attacks. It outlines key concepts such as confidentiality, integrity, and availability, along with methods for securing databases, including firewalls, encryption, and user privileges. The document also highlights various threats to databases, such as SQL injection and password cracking, and suggests countermeasures to mitigate these risks.