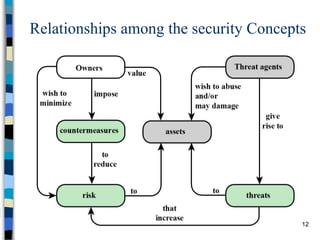
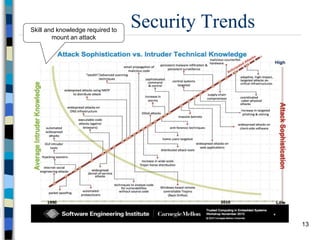
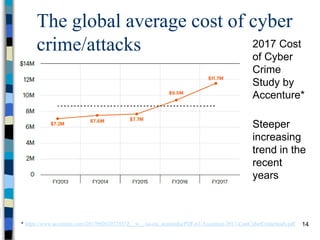
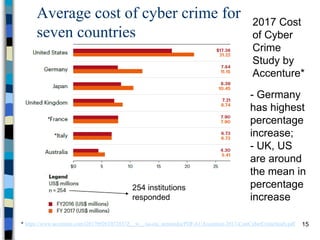
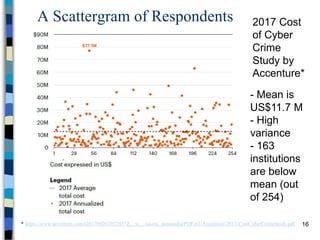
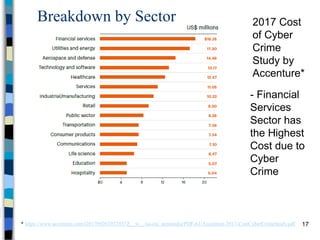
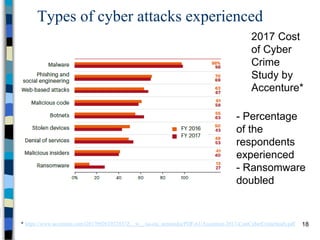
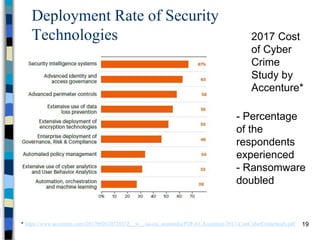
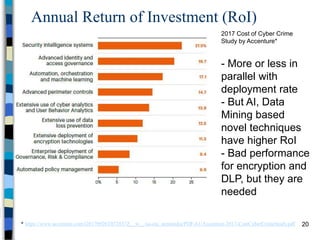
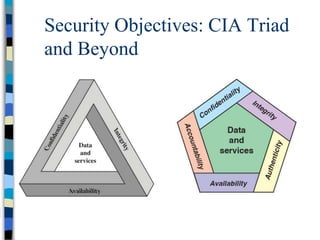
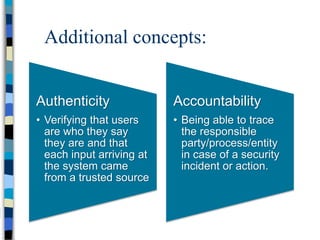
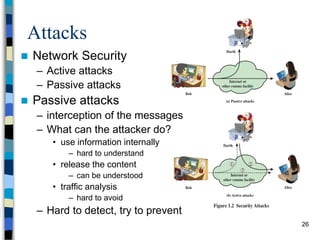
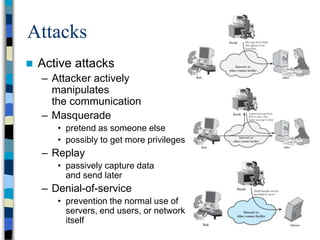
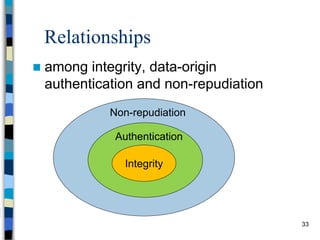
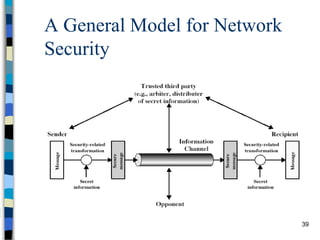
This document provides an overview of a computer and network security course. It discusses what topics will and won't be covered, including security threats, protocols, cryptography, and practical security issues but not advanced cryptography or computer networks. It also defines key security concepts like the CIA triad of confidentiality, integrity and availability. Additional topics covered include security attacks, services, and mechanisms like encryption, authentication, access control and intrusion detection.