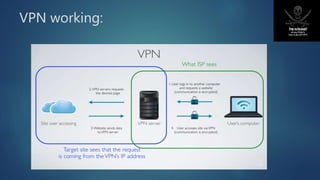
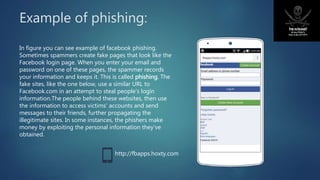
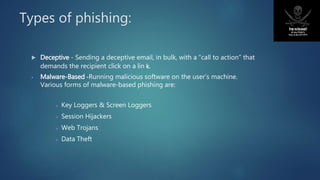
Proxy servers act as intermediaries between internal network clients and the internet. They screen requests, cache content to improve performance, and can anonymize users' IP addresses. Anonymizers like VPNs also anonymize users by routing their traffic through encrypted tunnels to hide their real IP addresses and locations. Phishing scams try to steal users' sensitive information like login credentials by tricking them into entering information on fake websites masquerading as legitimate ones. Educating users and technical measures can help combat phishing.