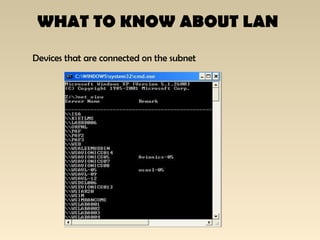
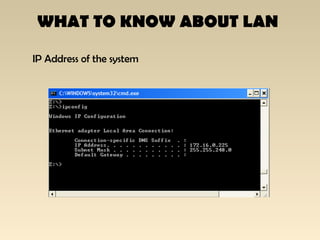
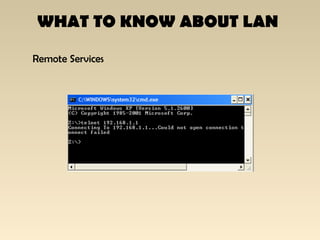
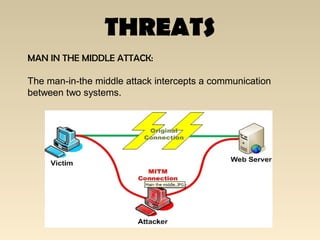
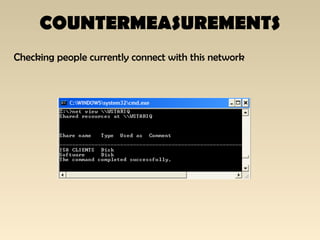
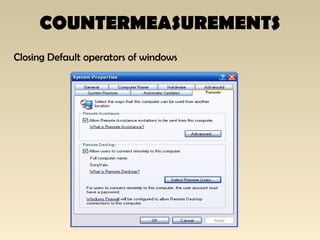
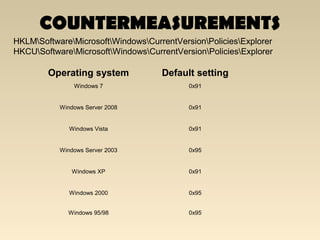
The document discusses the importance of Local Area Network (LAN) security, outlining its definition, functionalities like file sharing and messaging, and the necessity for security measures to combat various threats including man-in-the-middle attacks and denial-of-service attacks. It emphasizes countermeasures such as denying unusable services, monitoring connected devices, and modifying operating system defaults to minimize risks. Additionally, it suggests performance evaluation practices like customizing Windows services and registry settings to enhance overall system security and efficiency.