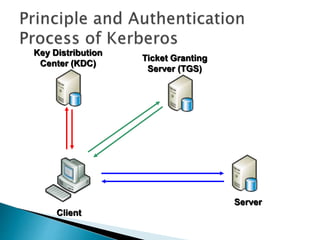
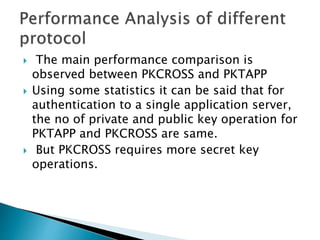
This document discusses adding public key cryptography to Kerberos to address limitations. It introduces three extensions: PKINIT for initial authentication using public keys; PKCROSS for cross-realm authentication using public keys between KDCs; and PKTAPP for authenticating to application servers using public keys. It analyzes performance and security issues when using these extensions and concludes they can improve Kerberos scalability in large networks.