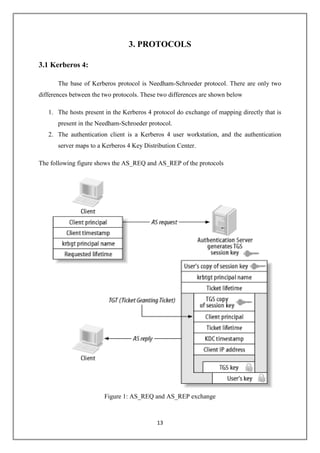
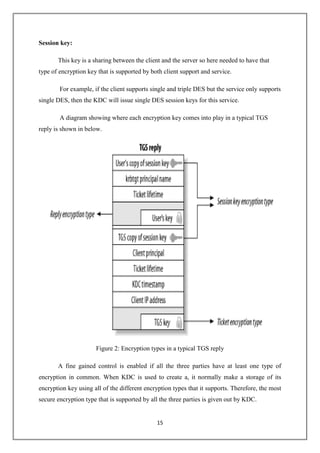
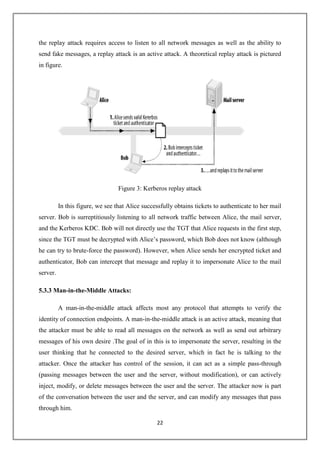
Kerberos is an authentication system that allows clients to securely request services from servers across an insecure network. It was developed at MIT to prevent passwords from being sent in unencrypted form. This document provides an overview of Kerberos, including its goals of providing secure authentication, a history of its development from versions 1-5, and concepts like tickets, encryption, and cross-realm authentication. It also discusses Kerberos applications, security issues and solutions, and potential future developments like smart cards and better encryption standards.