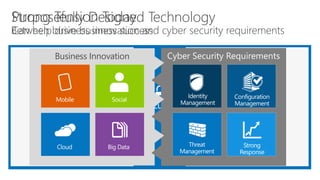
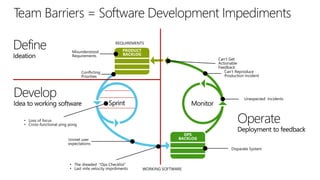
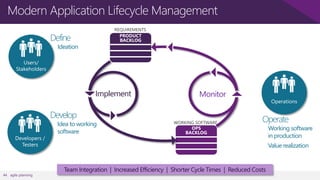
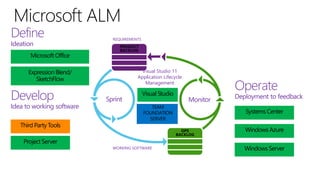
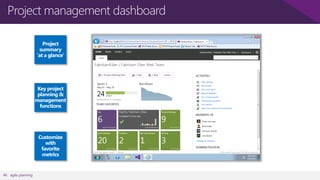
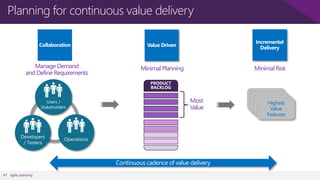
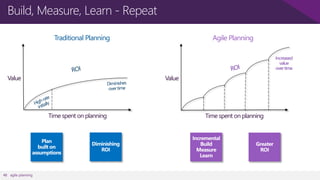
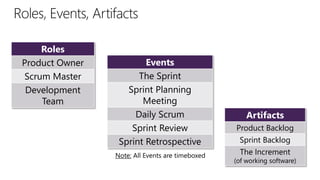
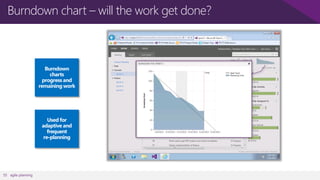
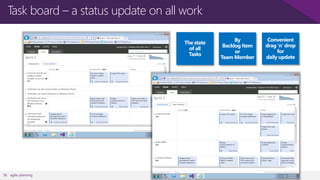
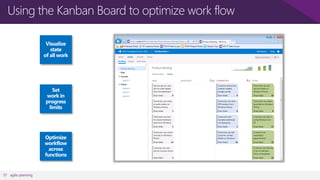
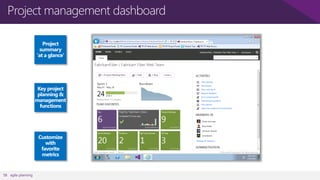
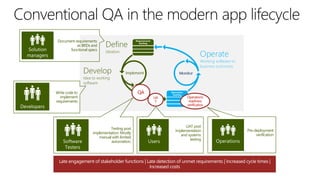
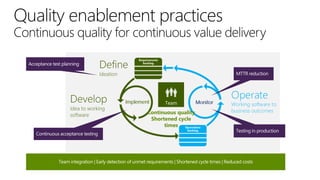
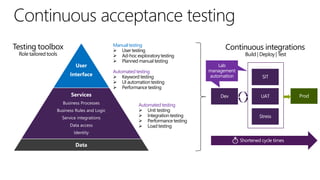
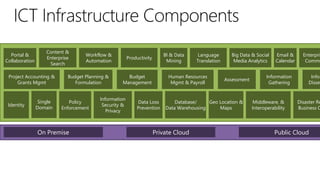
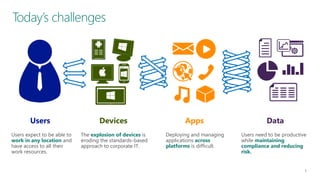
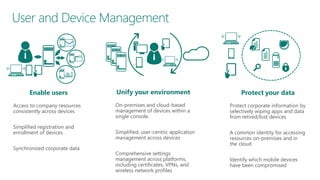
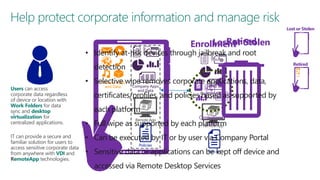
The document discusses user and device management in Microsoft. It states that users expect to access corporate resources from any location using various devices, but this creates challenges for IT departments. The document outlines how Microsoft's user and device management tools enable users by providing consistent access across devices, simplifying device enrollment, and synchronizing corporate data. It also allows IT to unify management of on-premises and cloud-based devices from a single console. Further, it discusses how these tools help protect corporate information by selectively wiping devices and identifying compromised ones.





![HEADLINES
How hackers allegedly
stole “unlimited”
amounts of cash US economy up to
Cybercrime costs from
banks in just a few hours
$140 billion annually, report says
Politics.co.uk [2013]
Ars Technica [2013]
Los Angeles Times [2013]
Malware burrows deep
into computer BIOS to
escape AV
The Register [September 2011]
Researchers have discovered one of the
first pieces ever used in the wild that
modifies the software on the motherboard
of infected computers to ensure the
infection can’t be easily eradicated…
Cyberspace changes
the fog of war
Universities face a
rising barrage of
cyberattacks
Ars Technica [2013]
Cyberattacks on the rise
against US corporations
Espionage malware
infects rafts of
governments,
industries around
the world
New York Times [2013]
Ars Technica [2013]
Forget carjacking, soon
it will be carhacking
The Sydney Morning Herald [2013]
Rising cyber security risks to drivers as
their cars become increasingly powered
by and connected to computers have
prompted the US auto-safety regulator to
start a new office focusing on the threat…](https://image.slidesharecdn.com/iso27034-tonysenomicrosoft-131115045840-phpapp02/85/Security-Development-Life-Cycle-10-320.jpg)