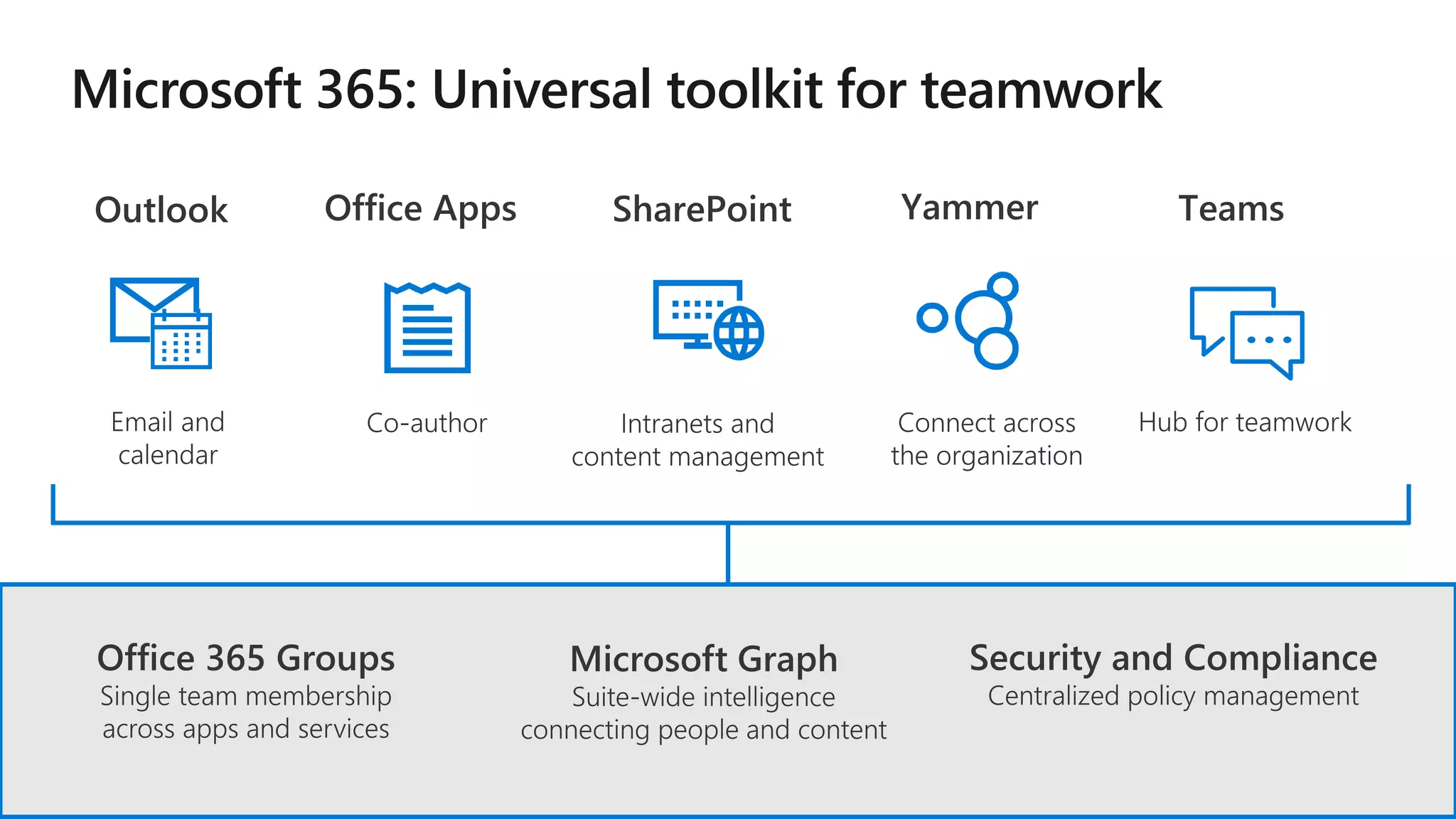
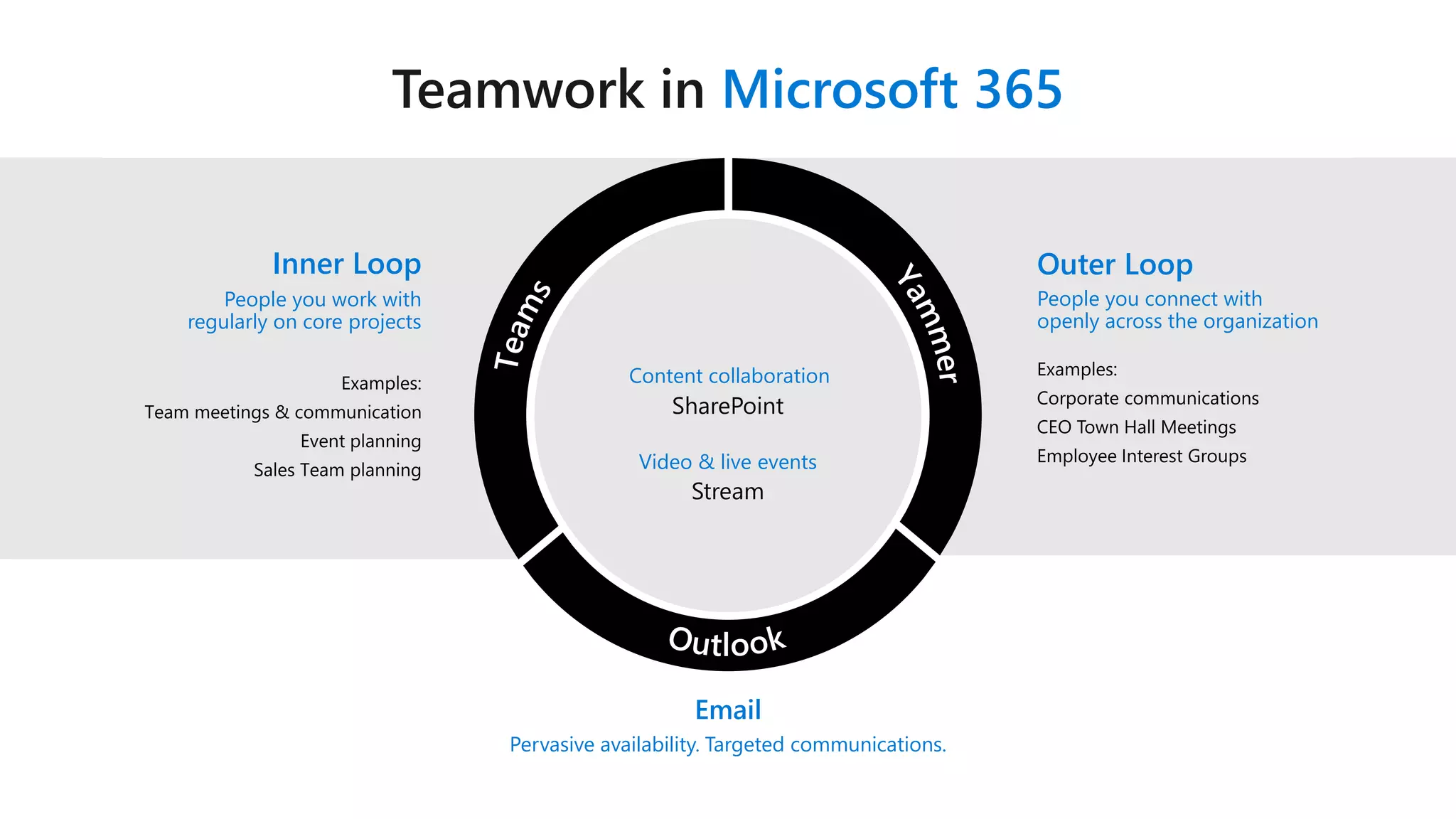
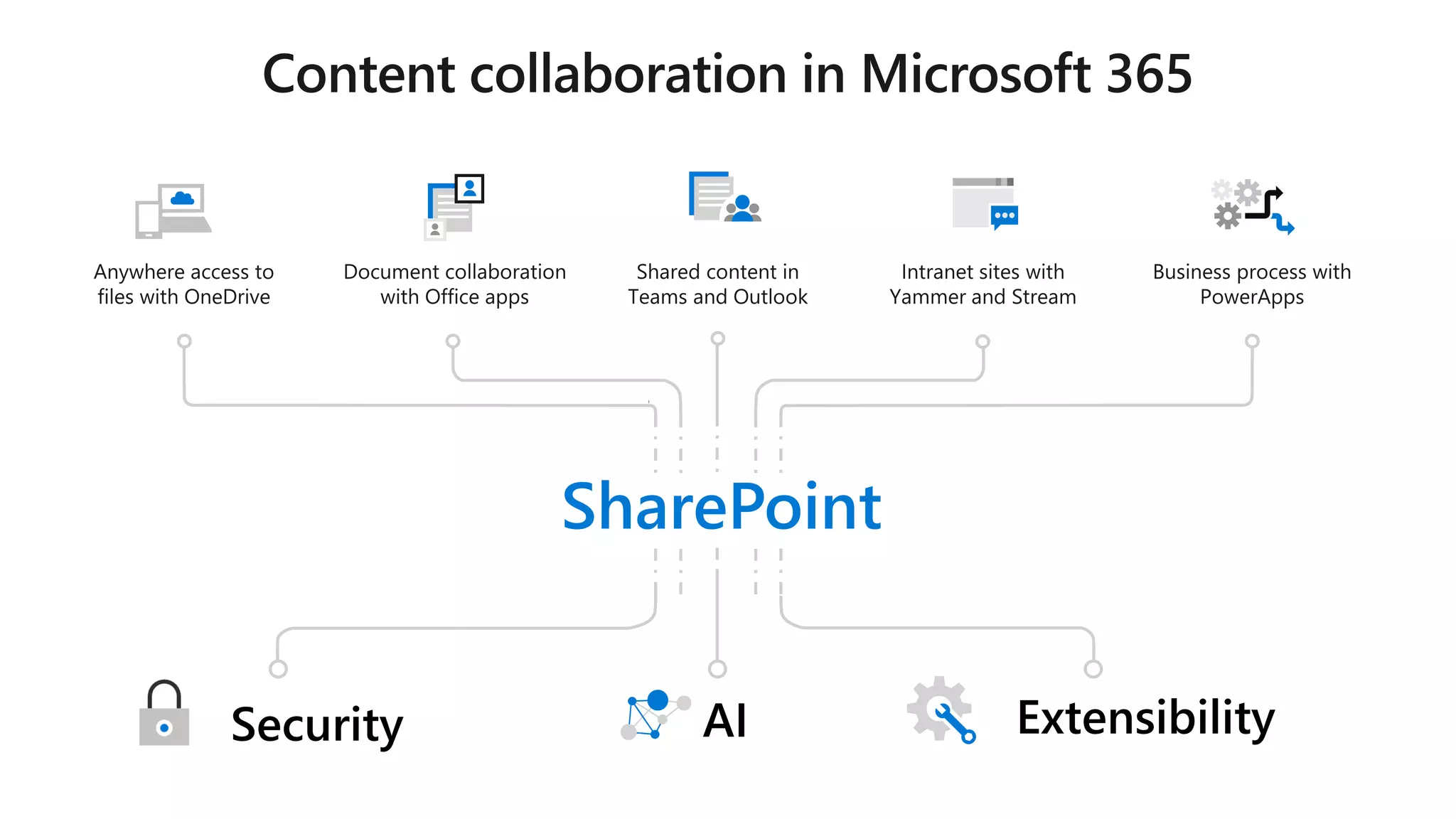
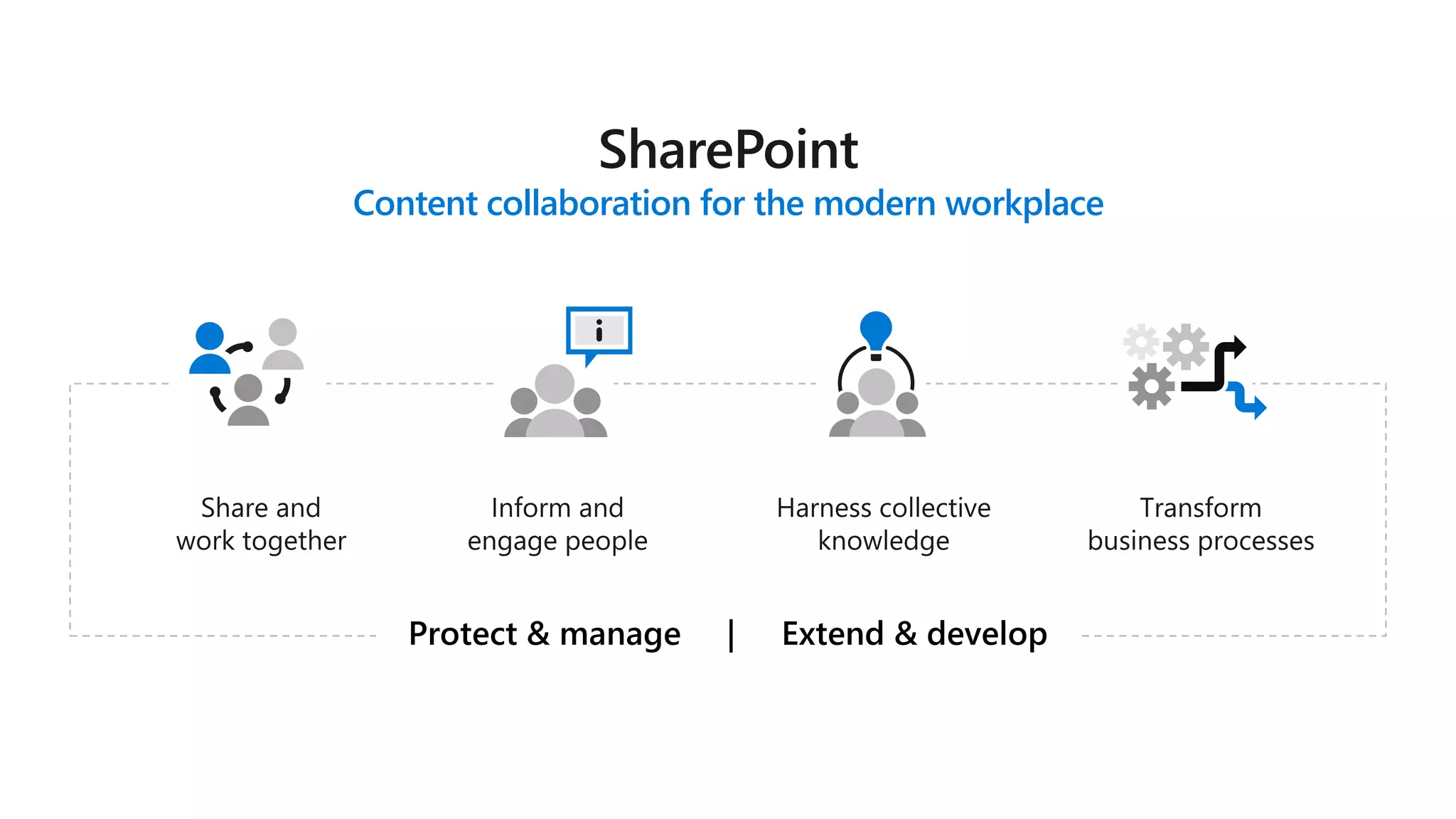
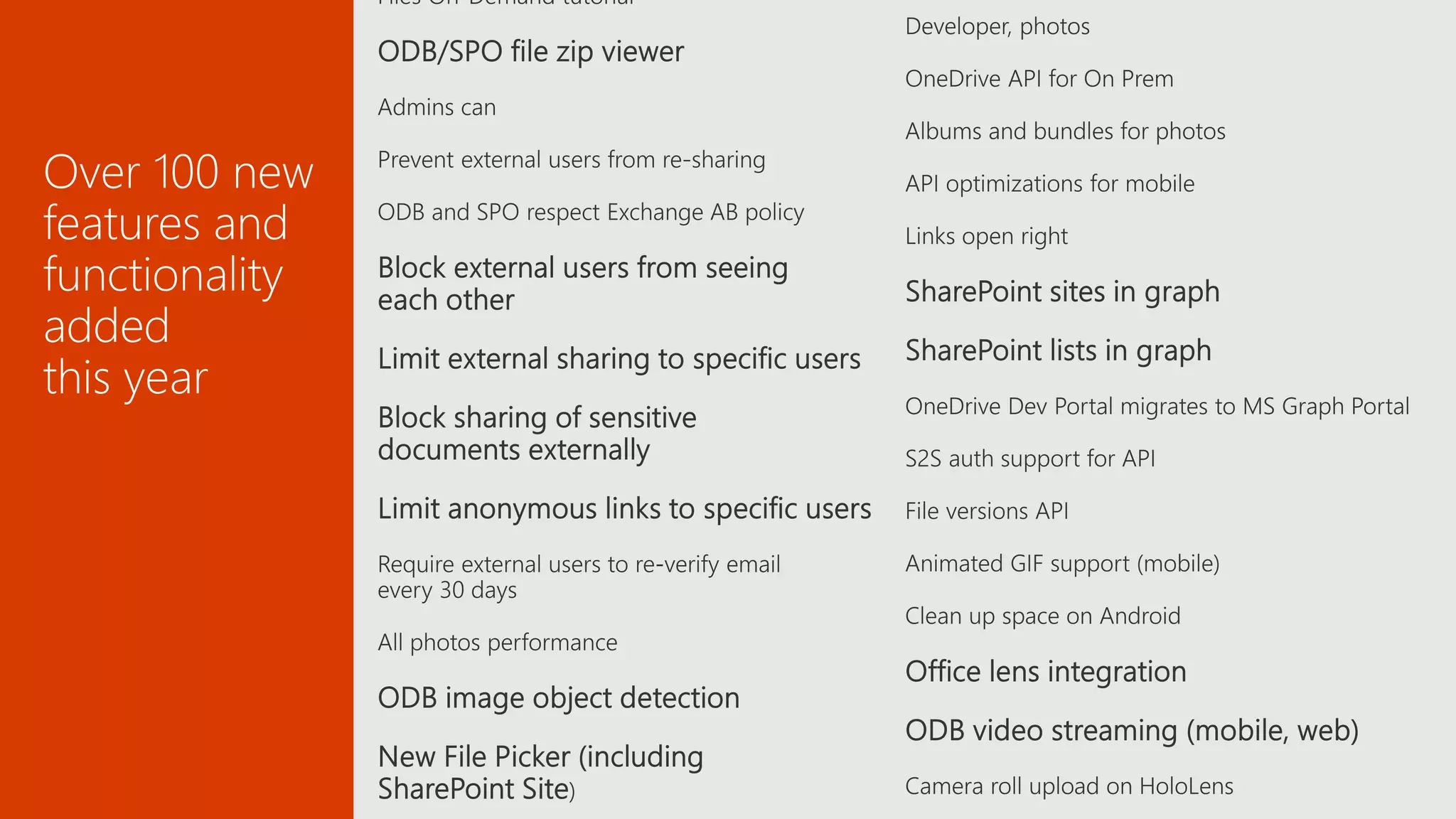
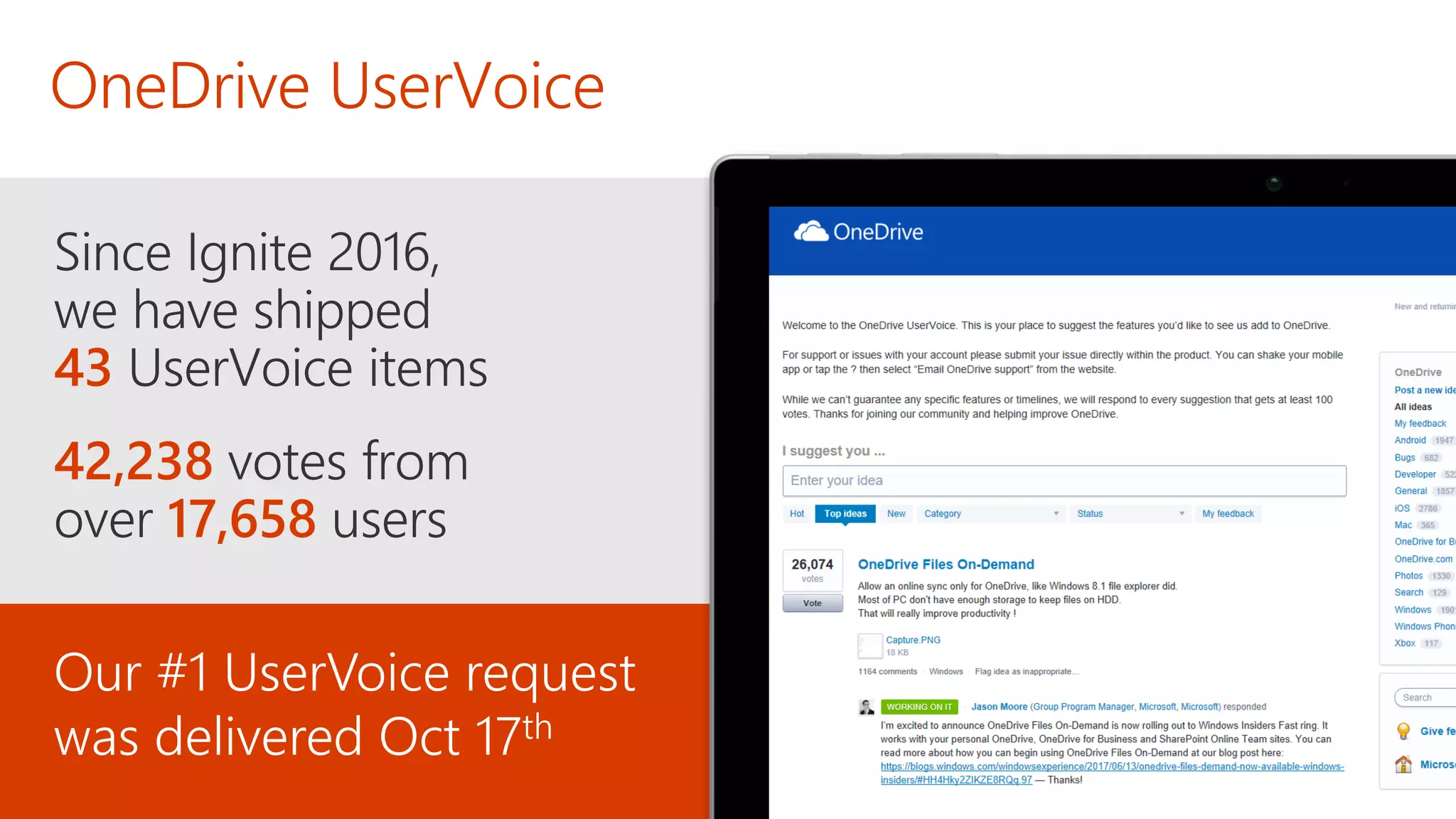
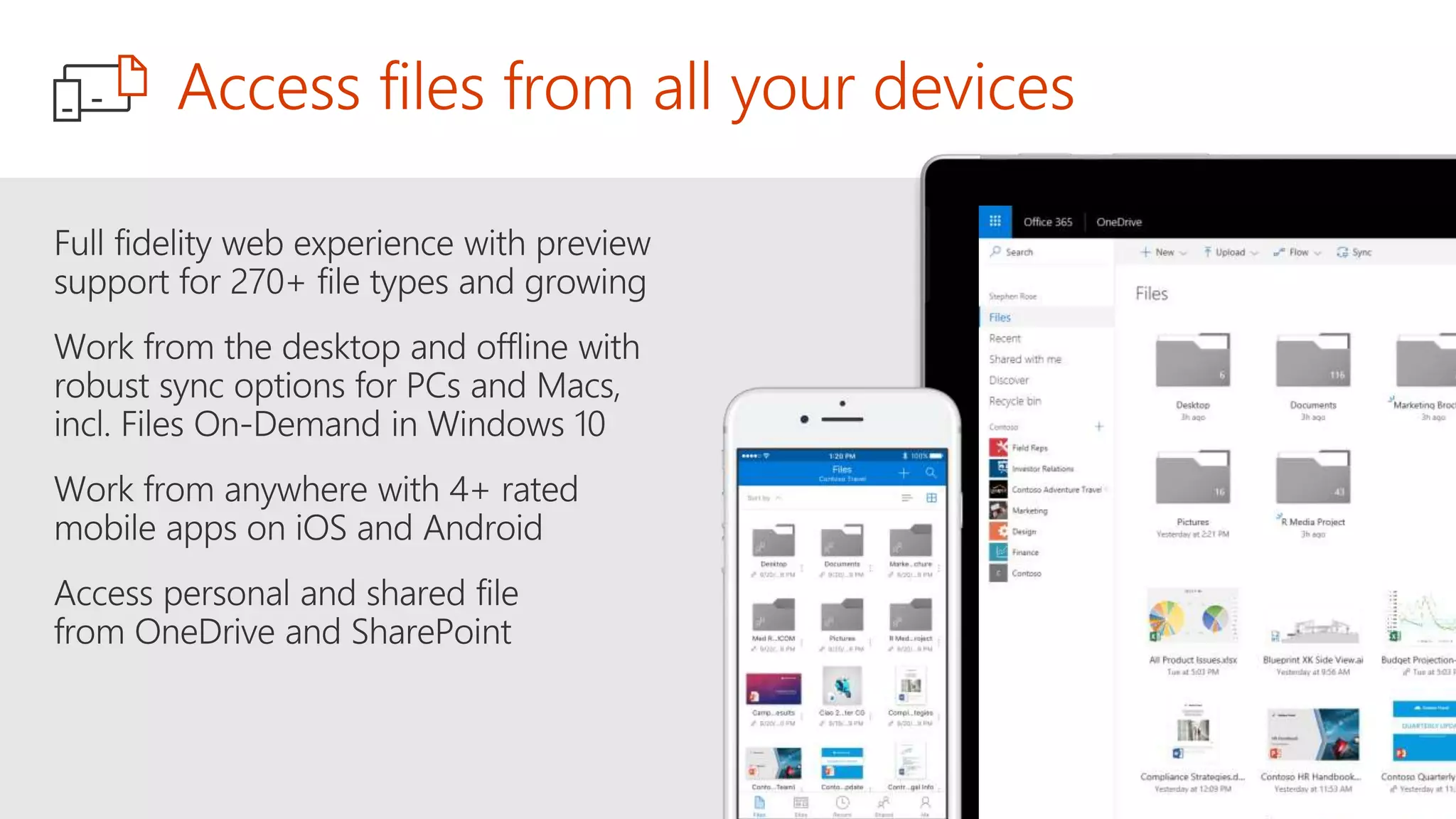
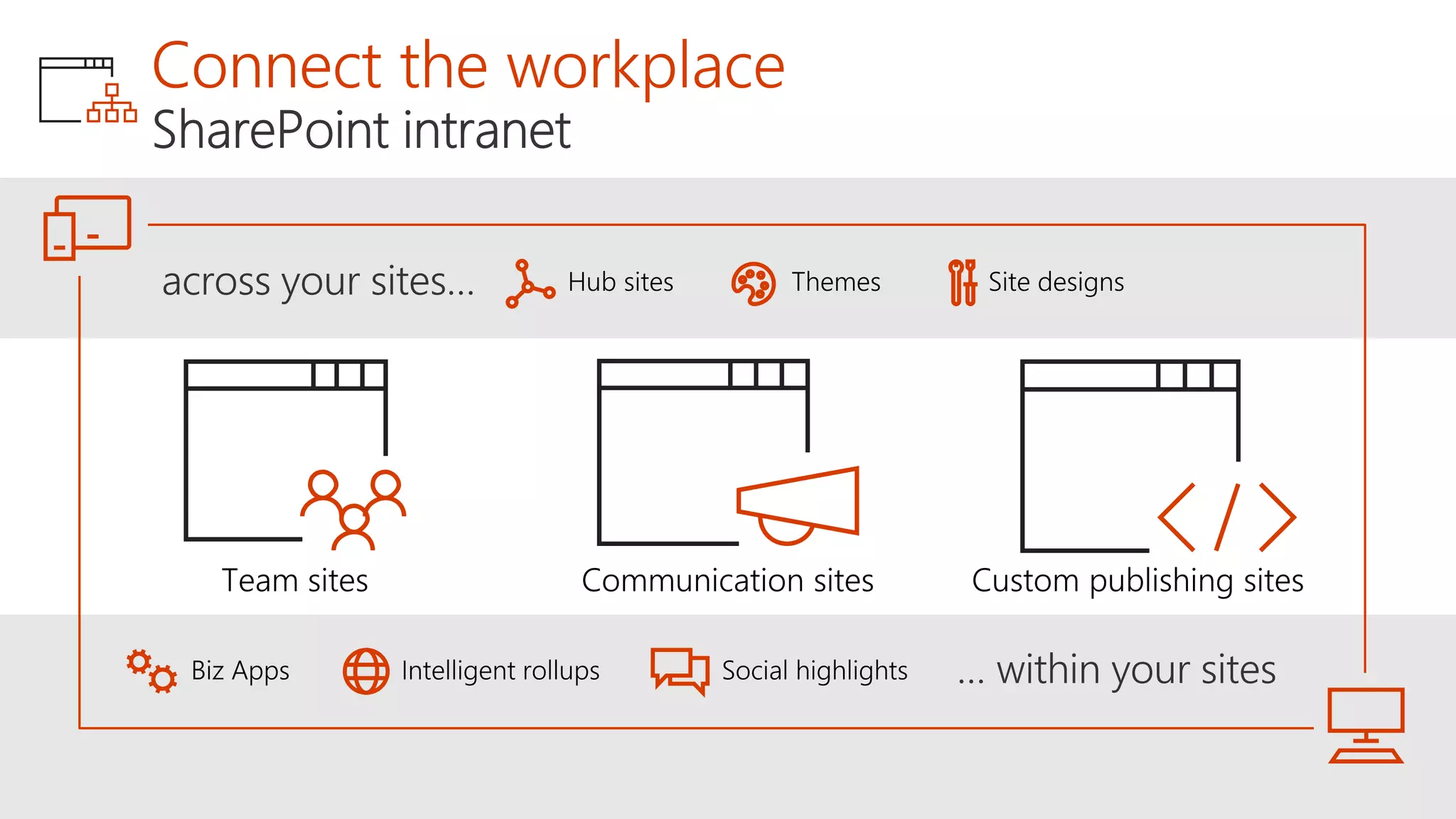
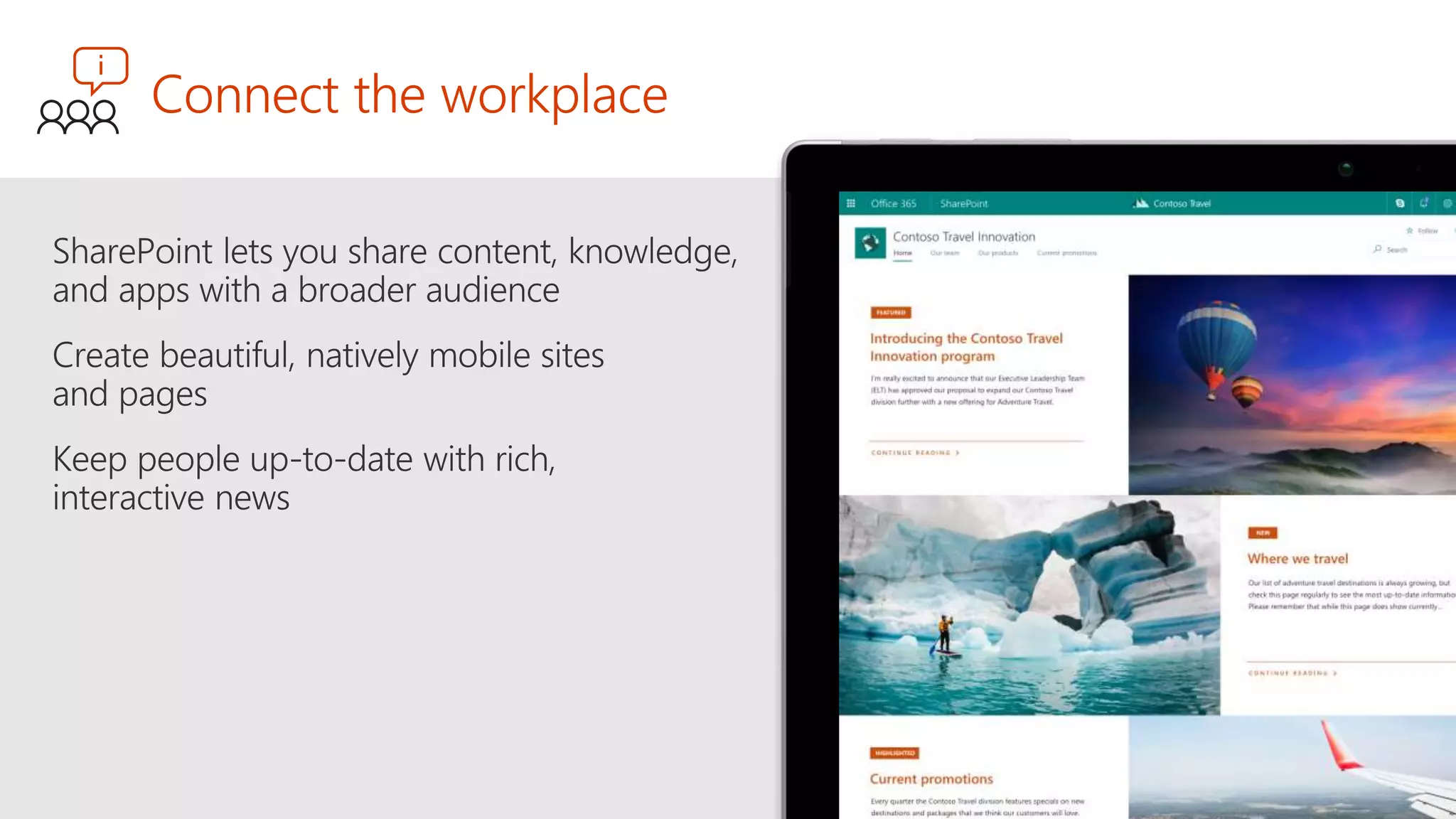
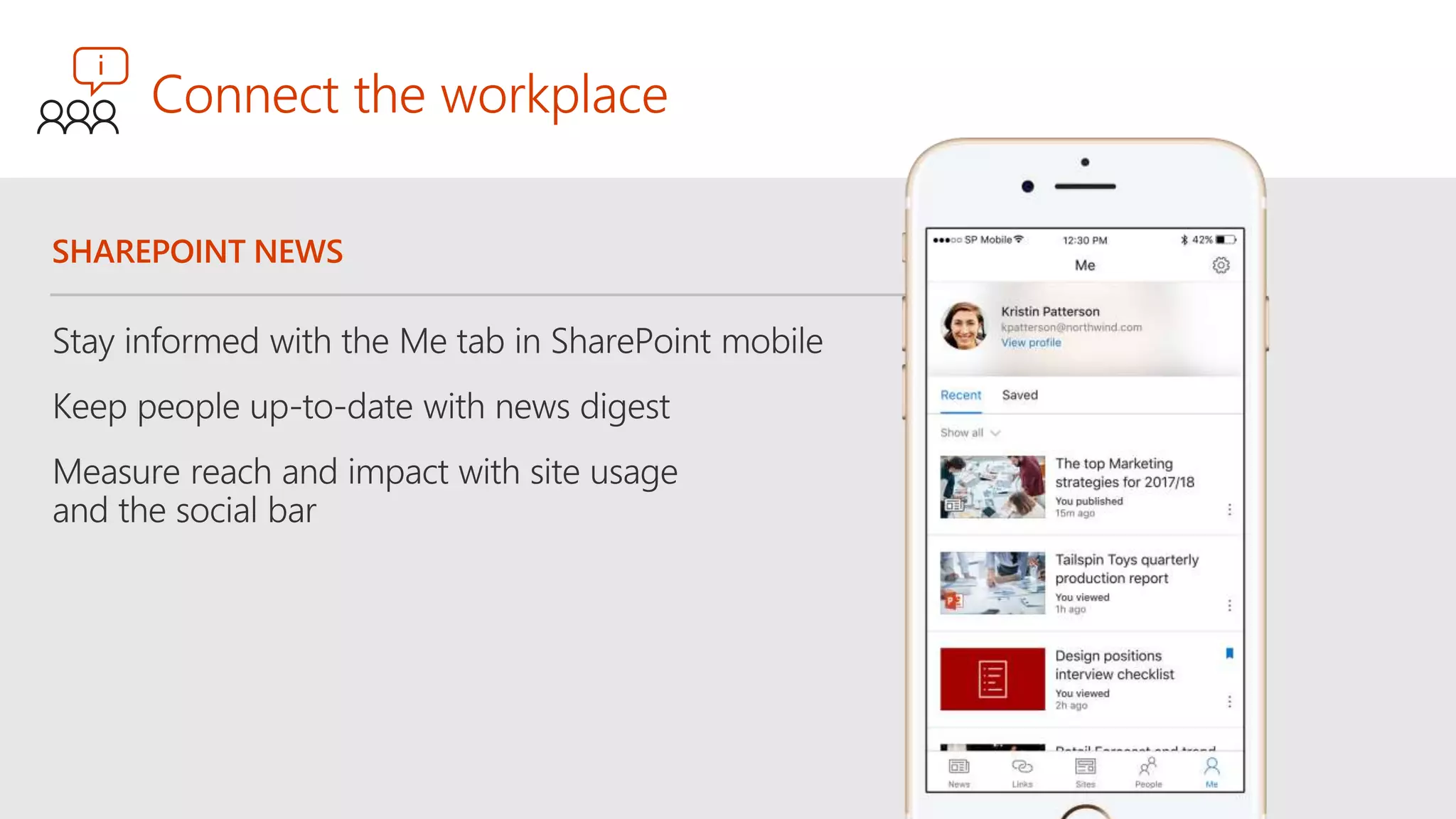
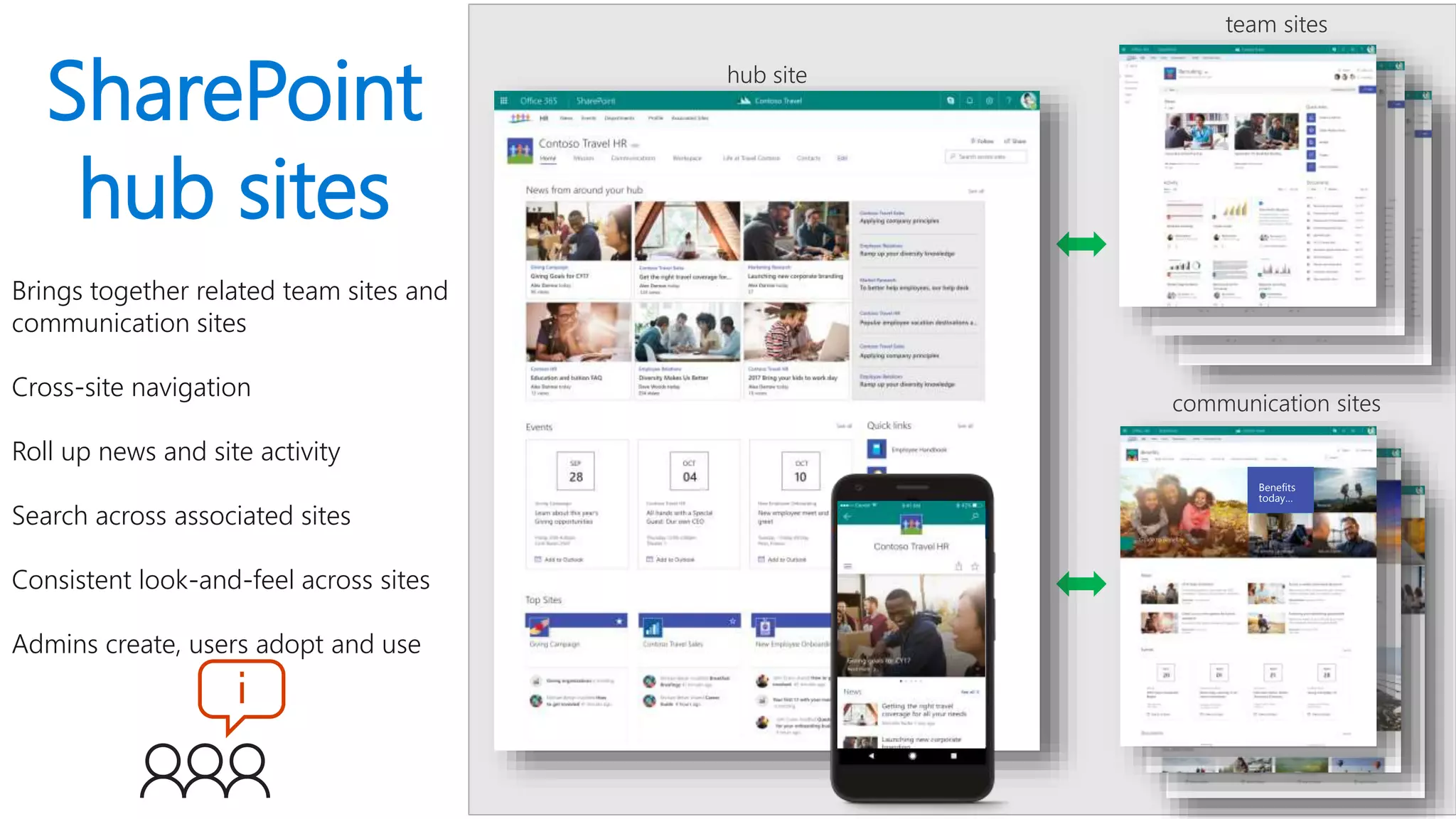
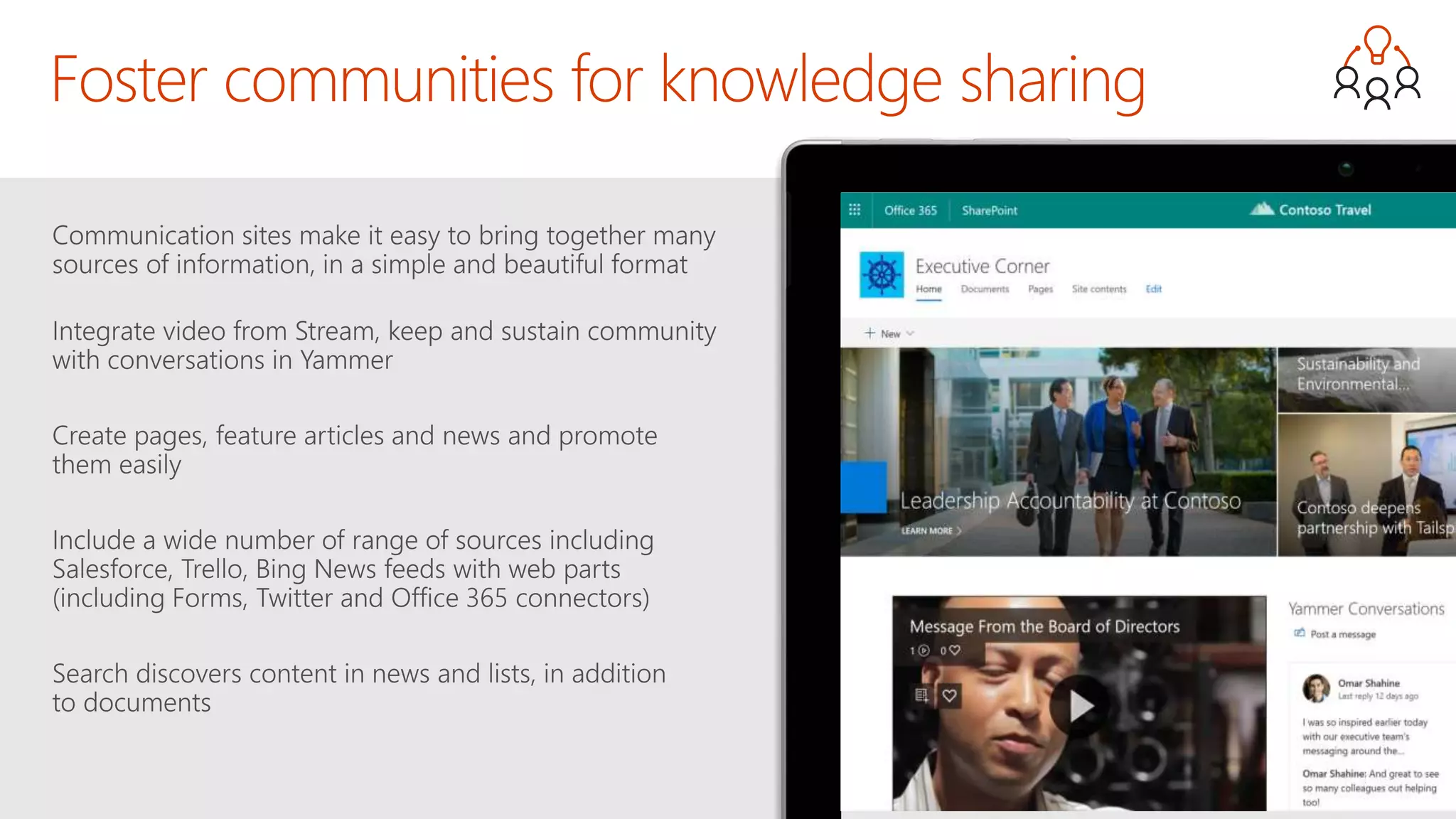
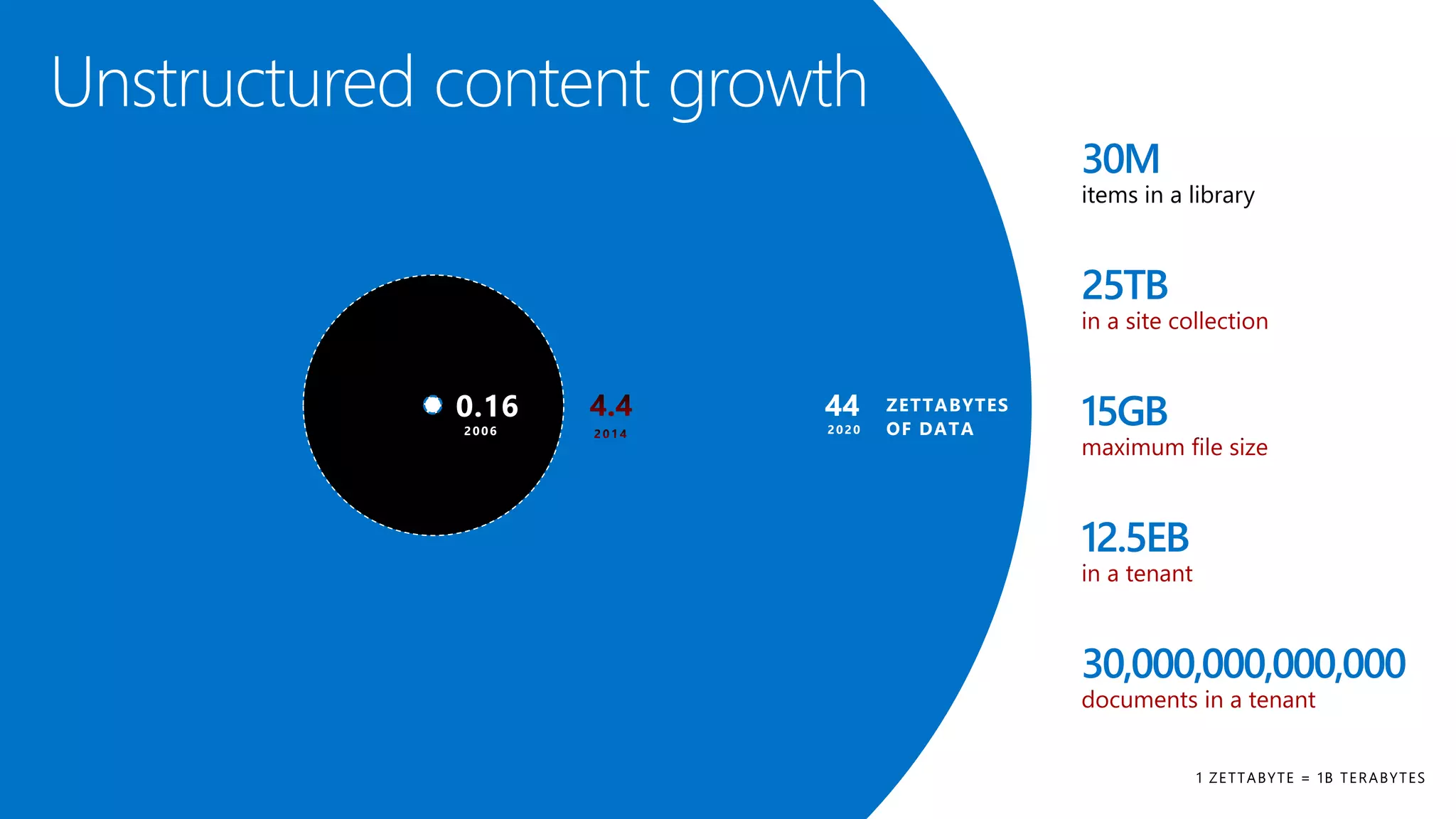
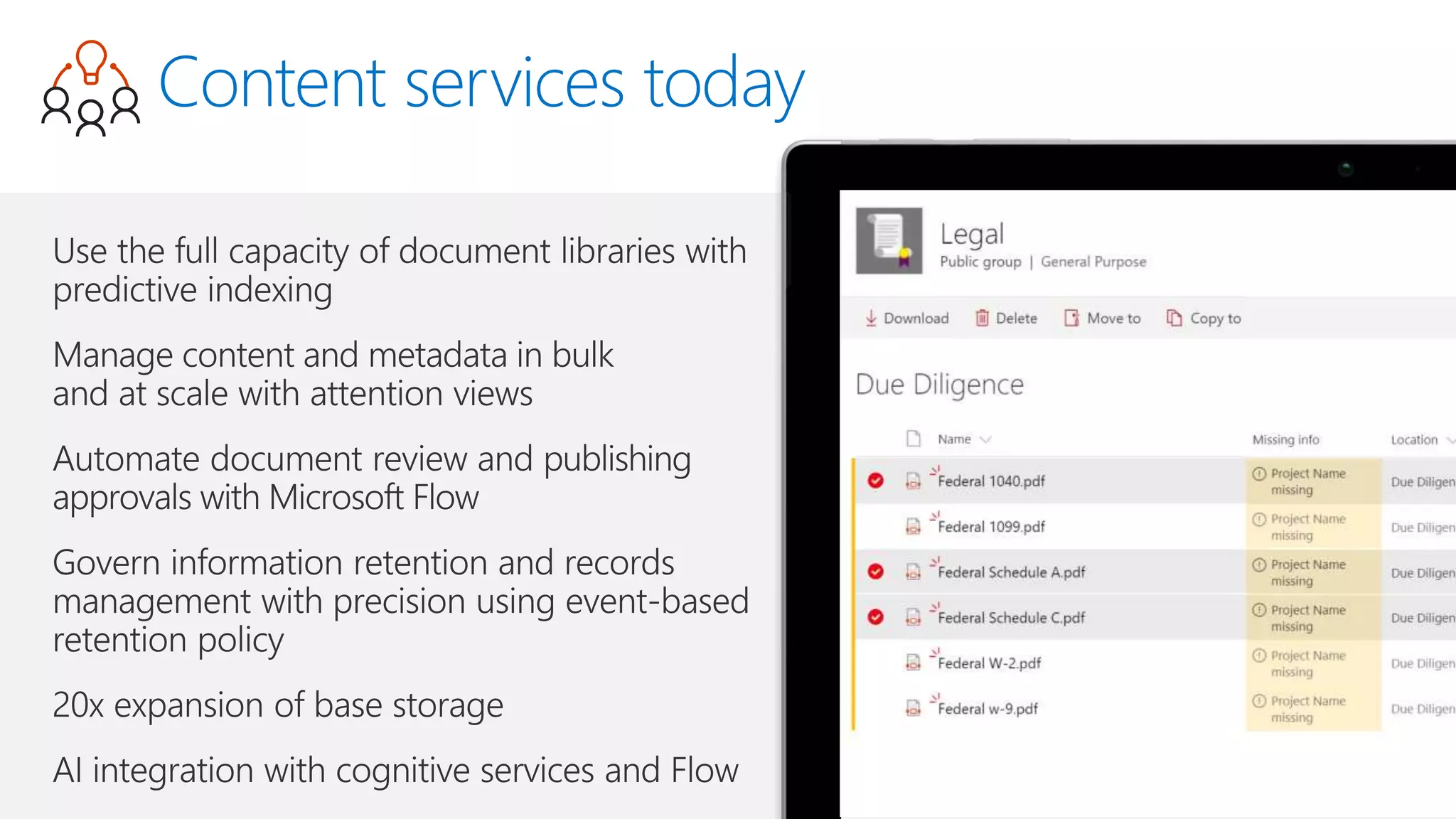
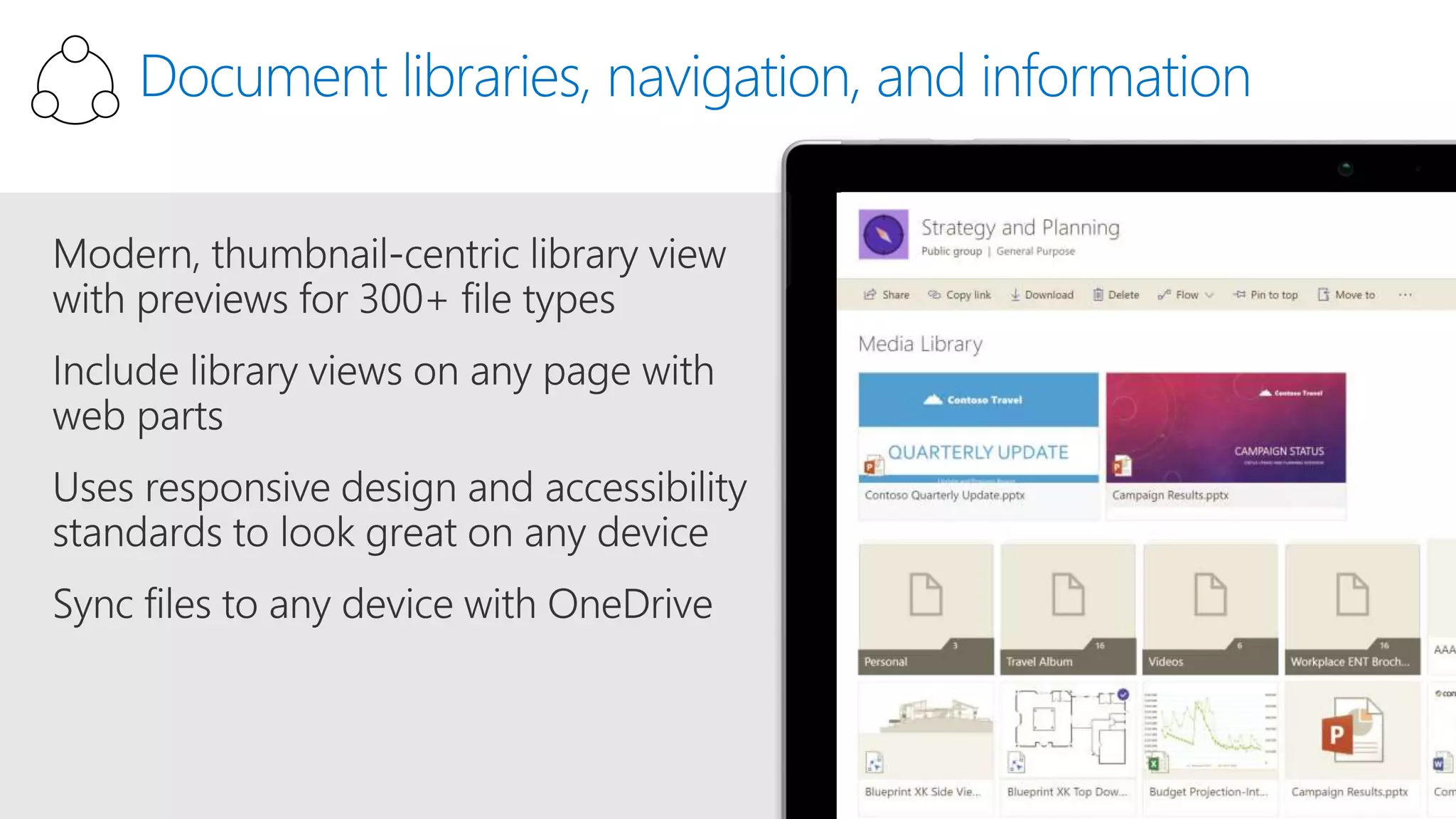
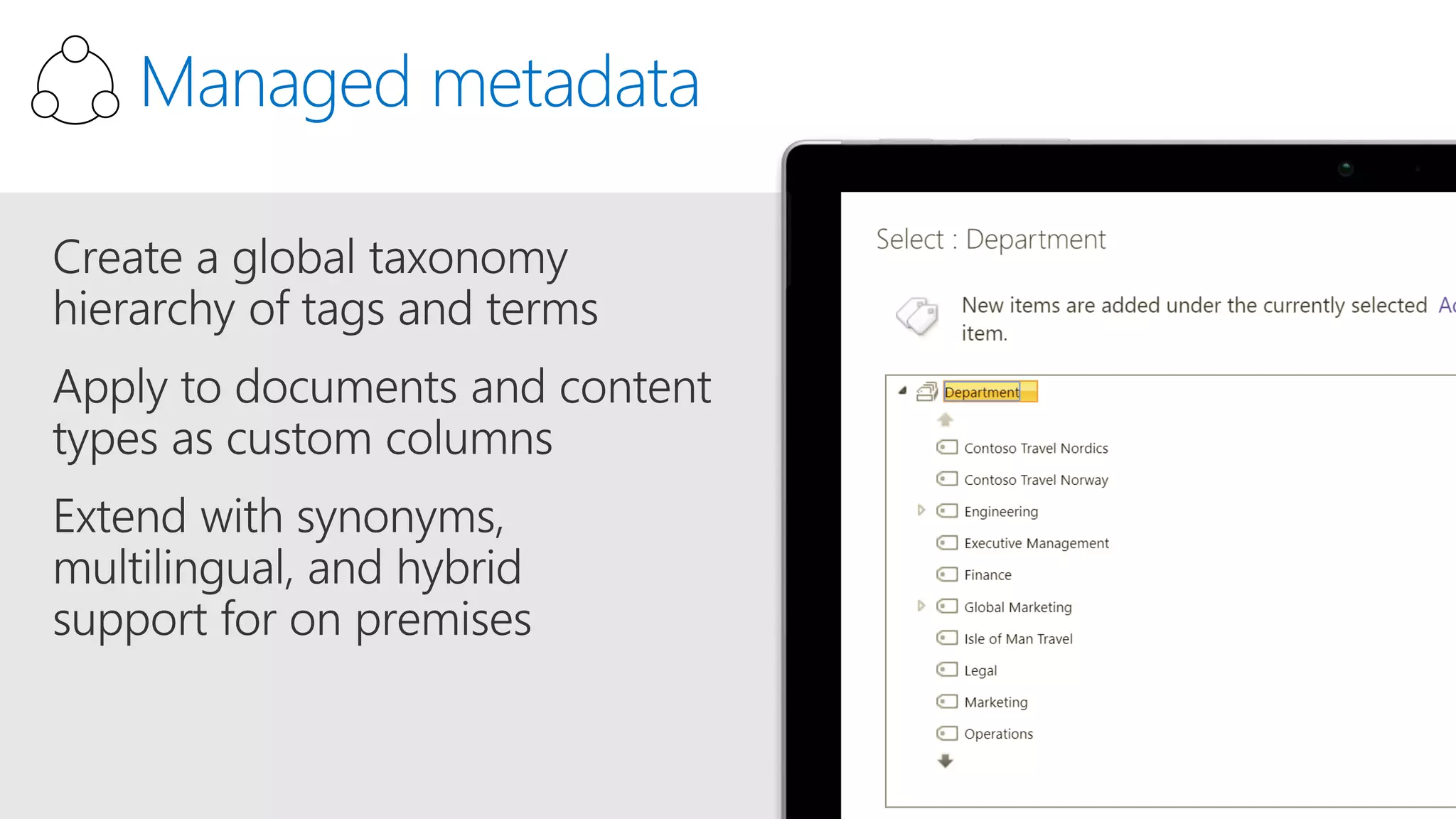
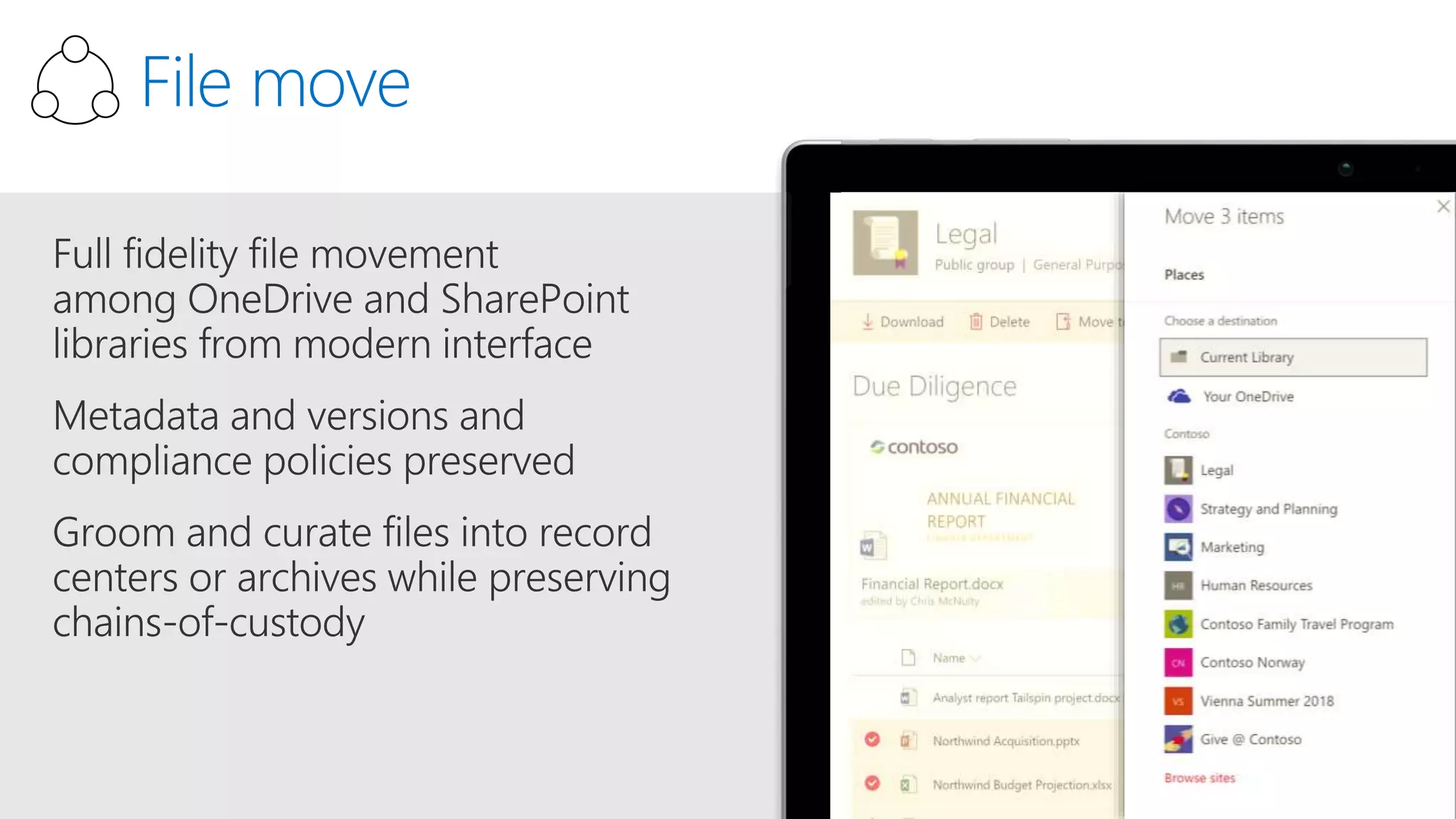
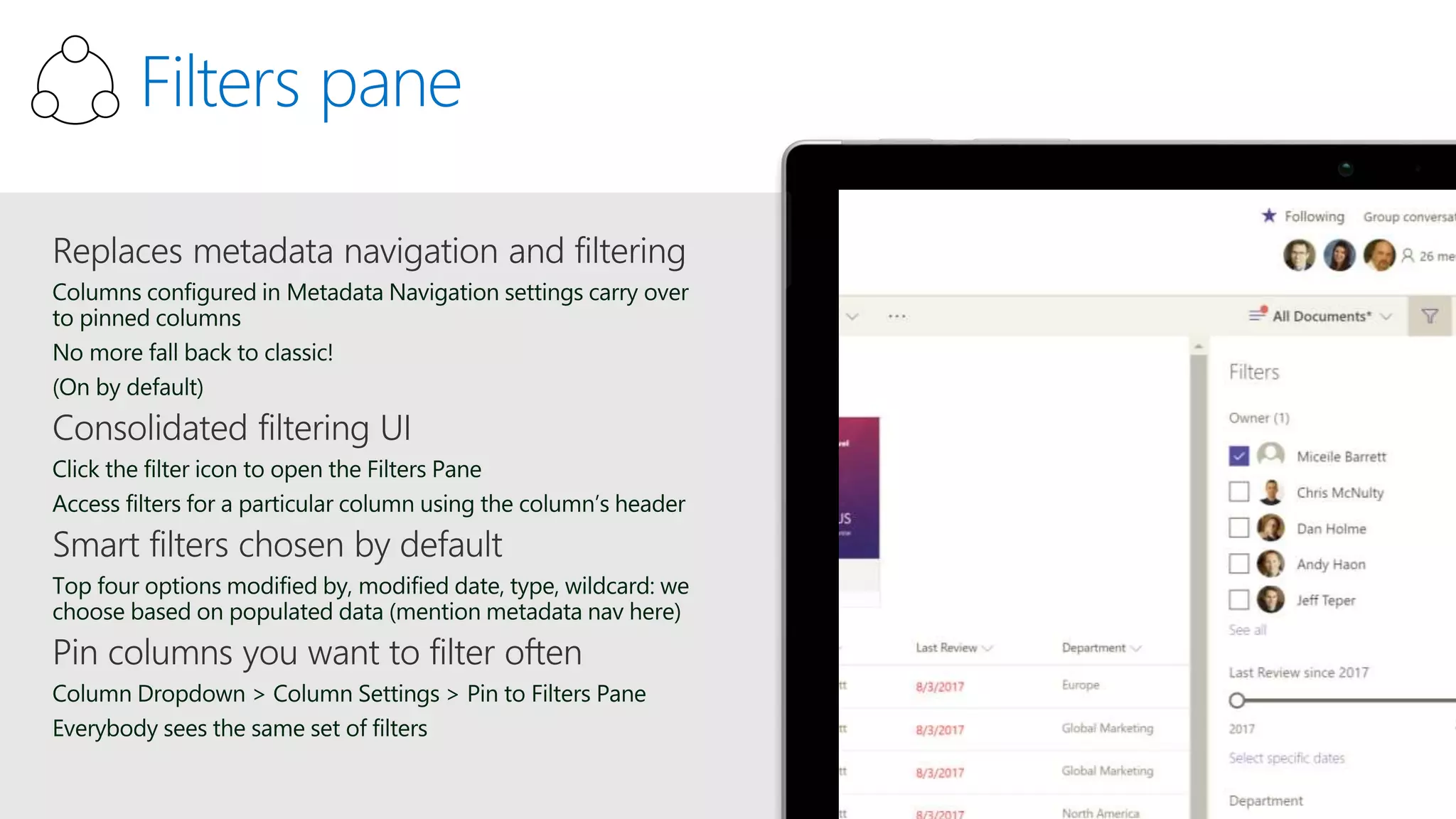
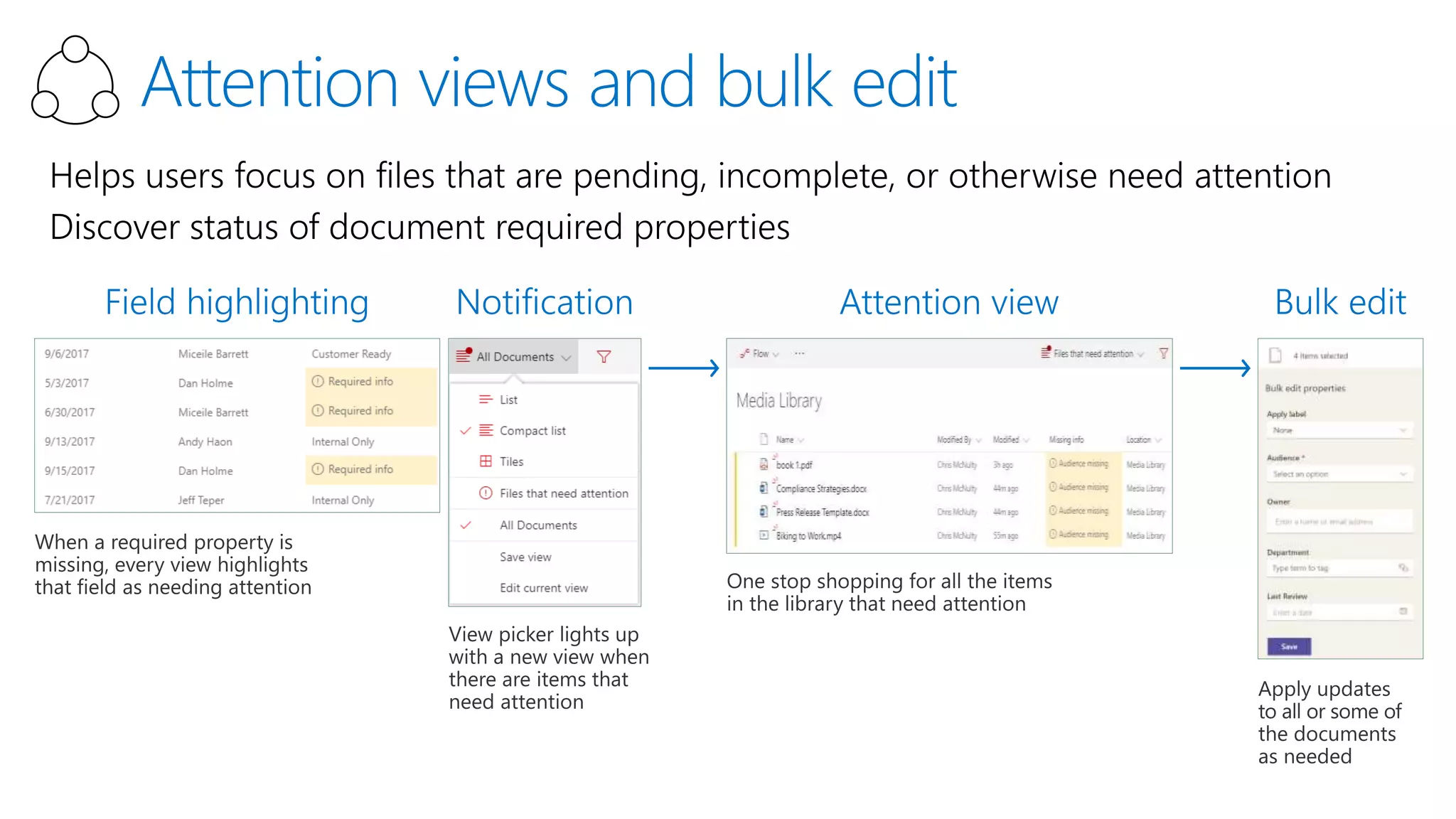
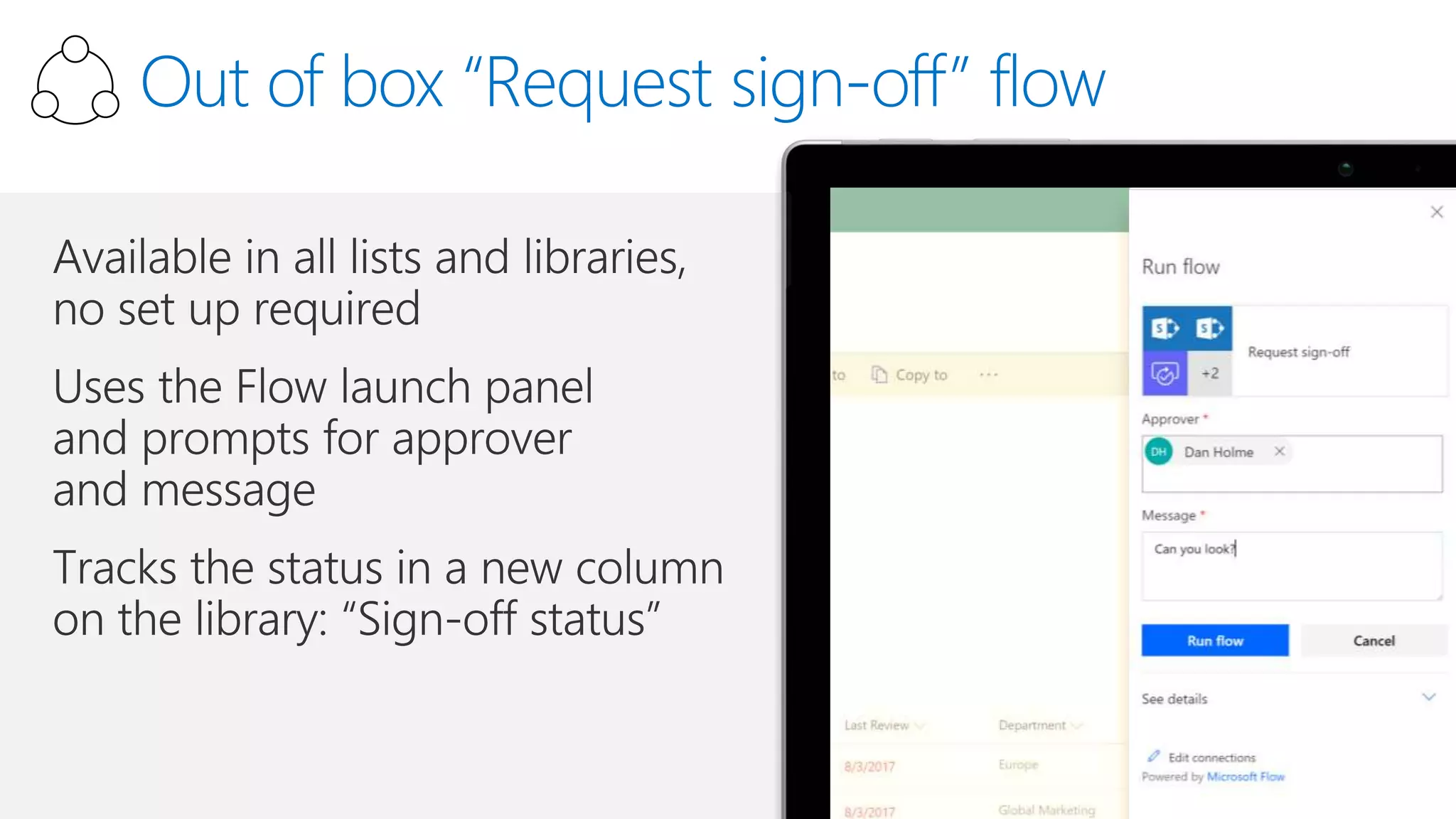
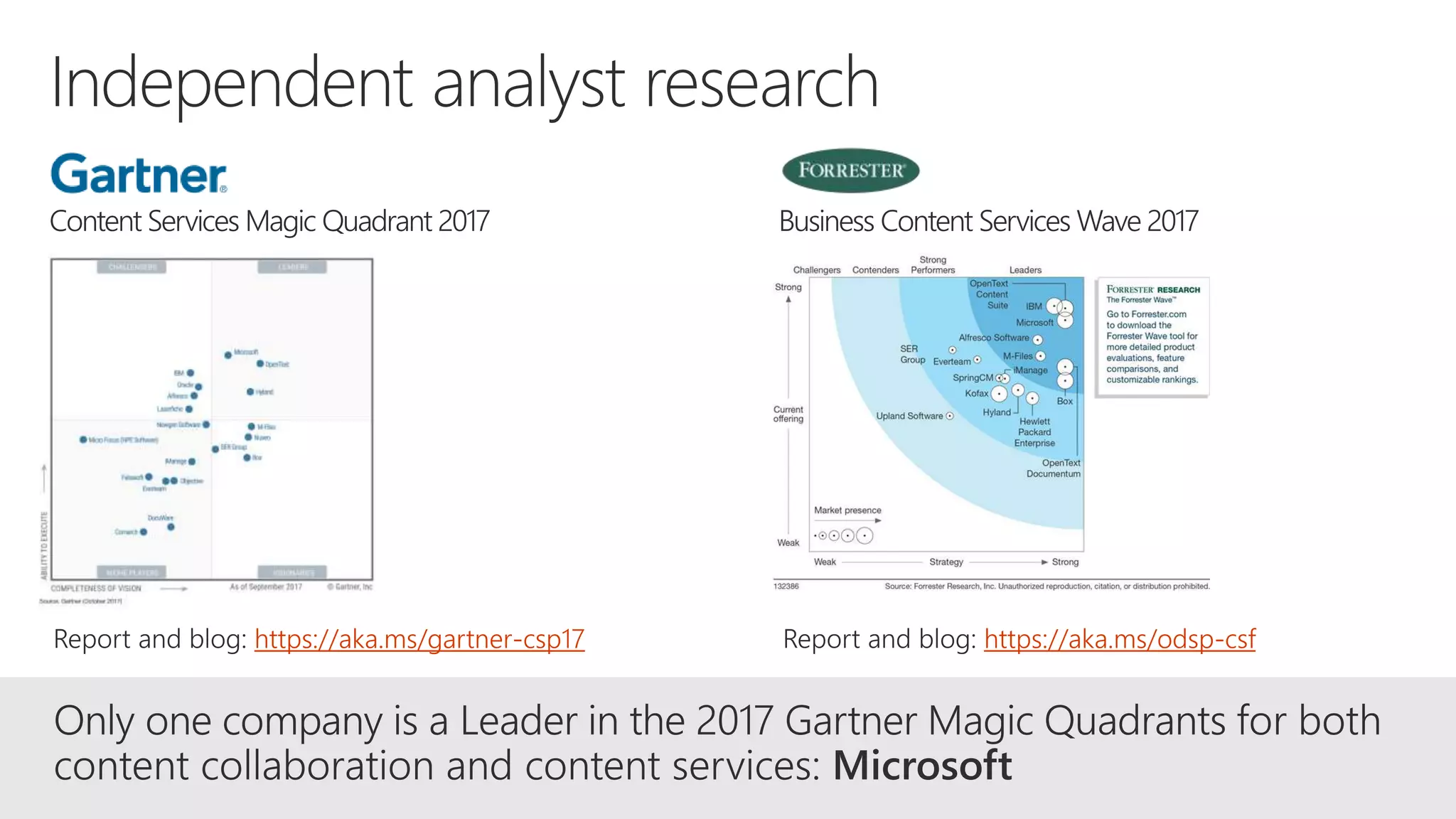
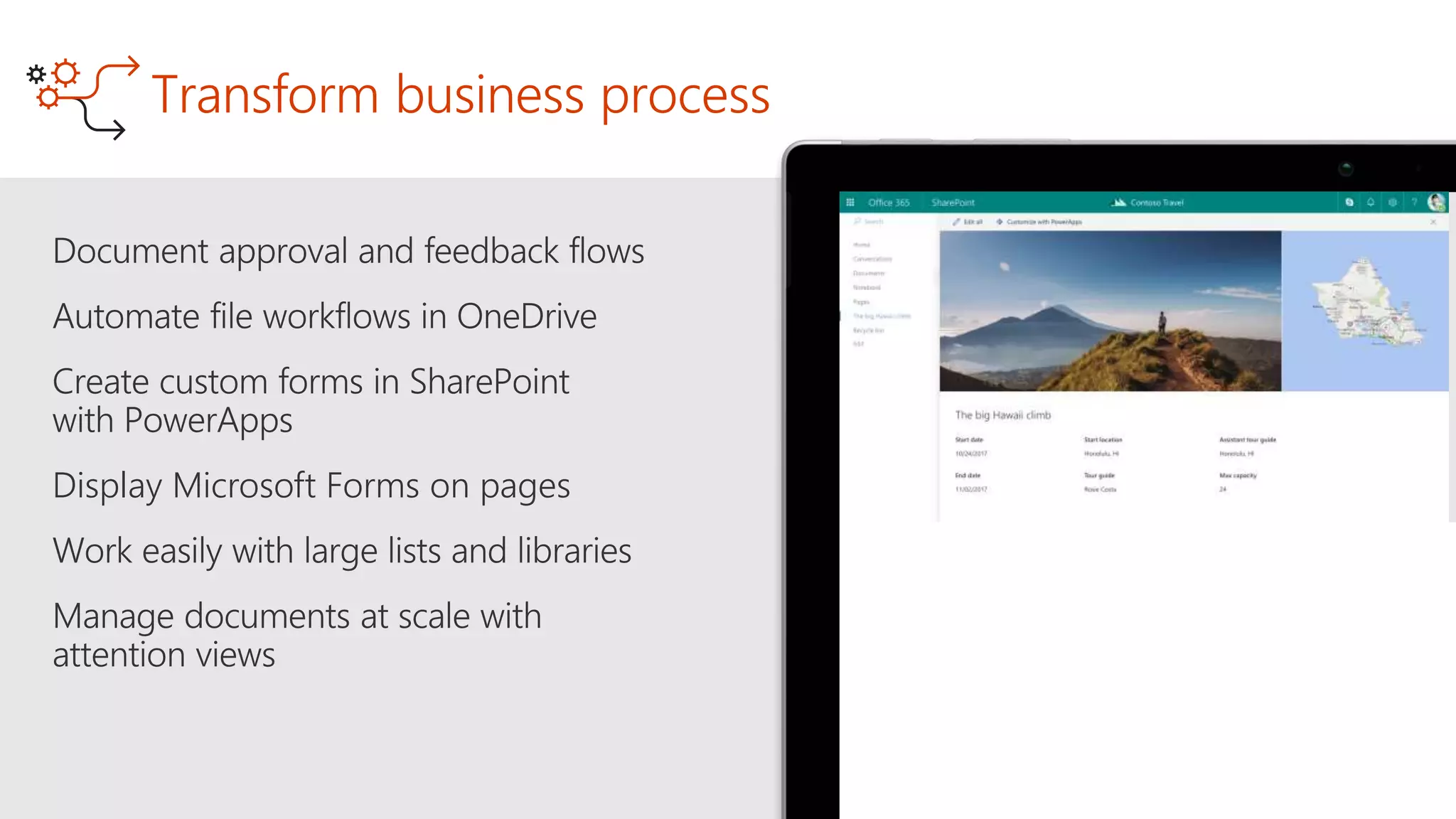
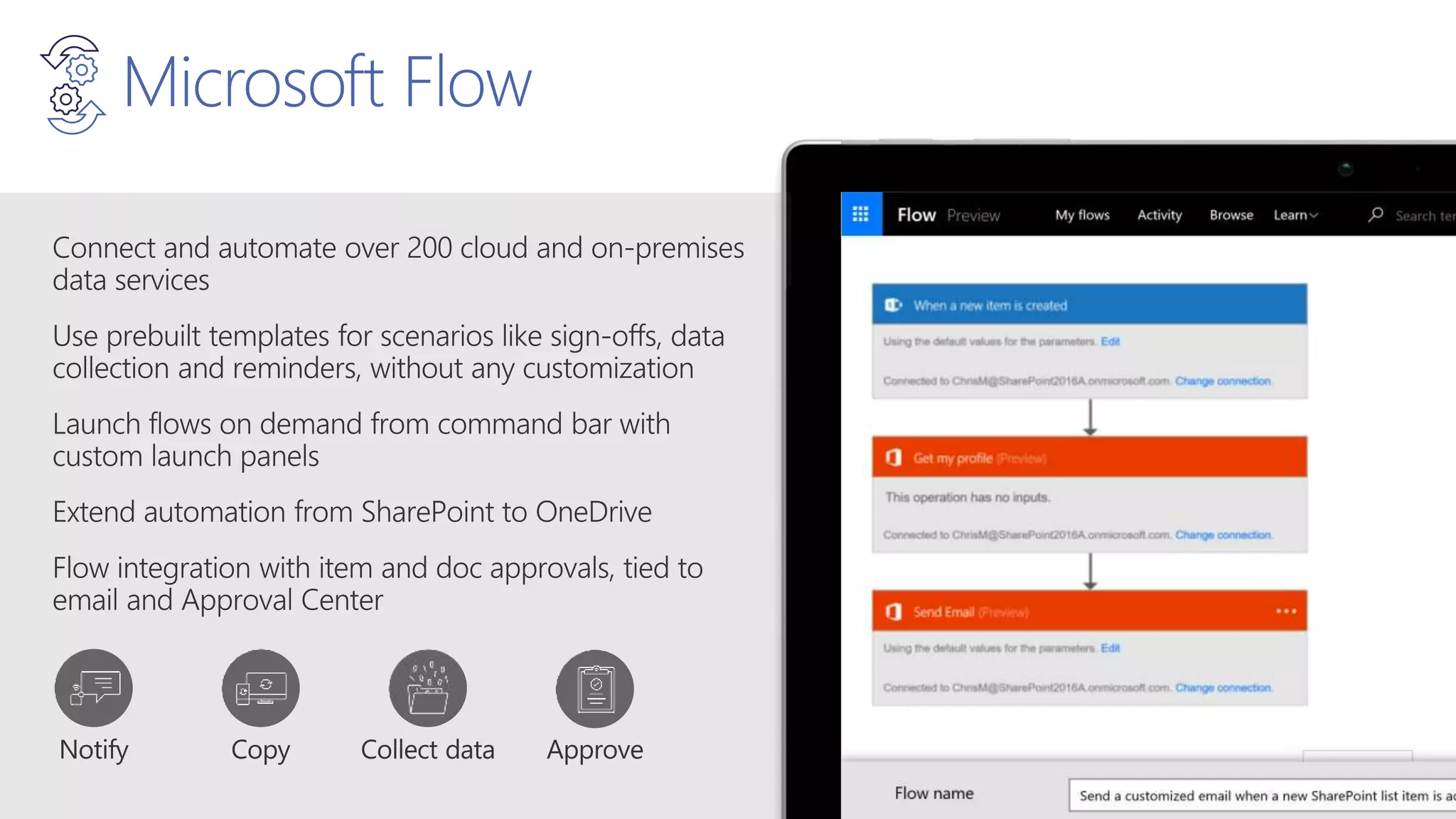
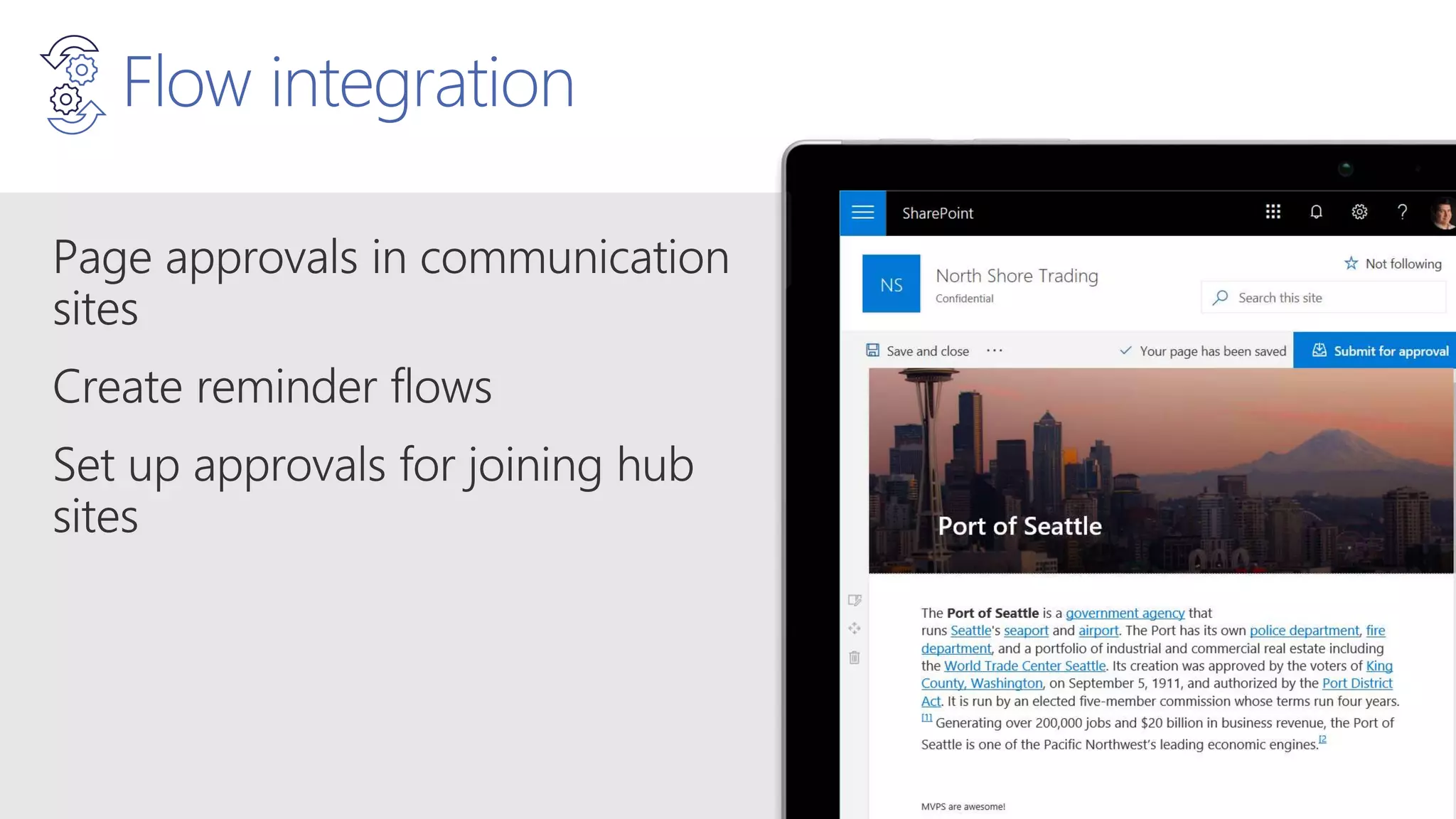
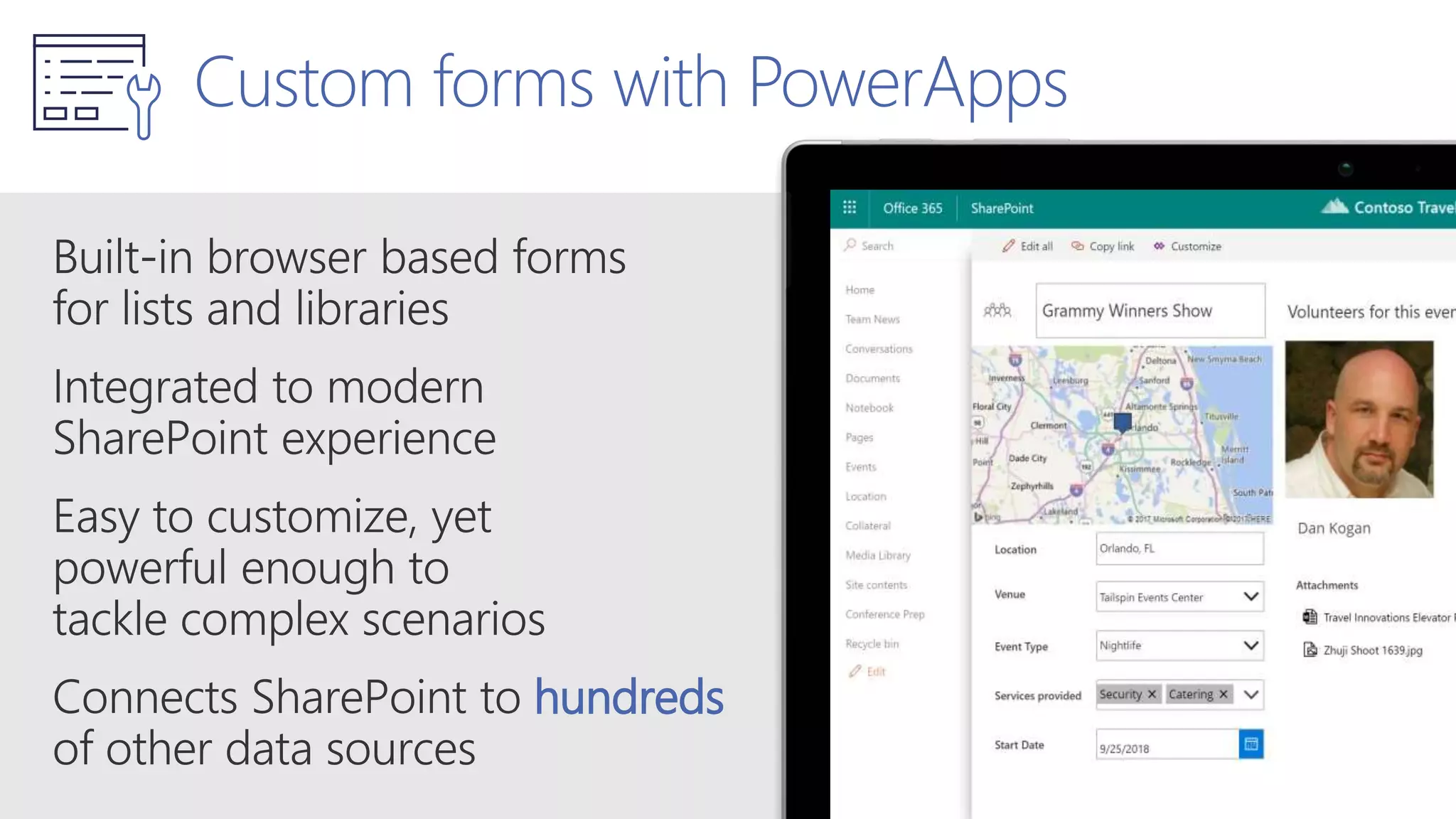
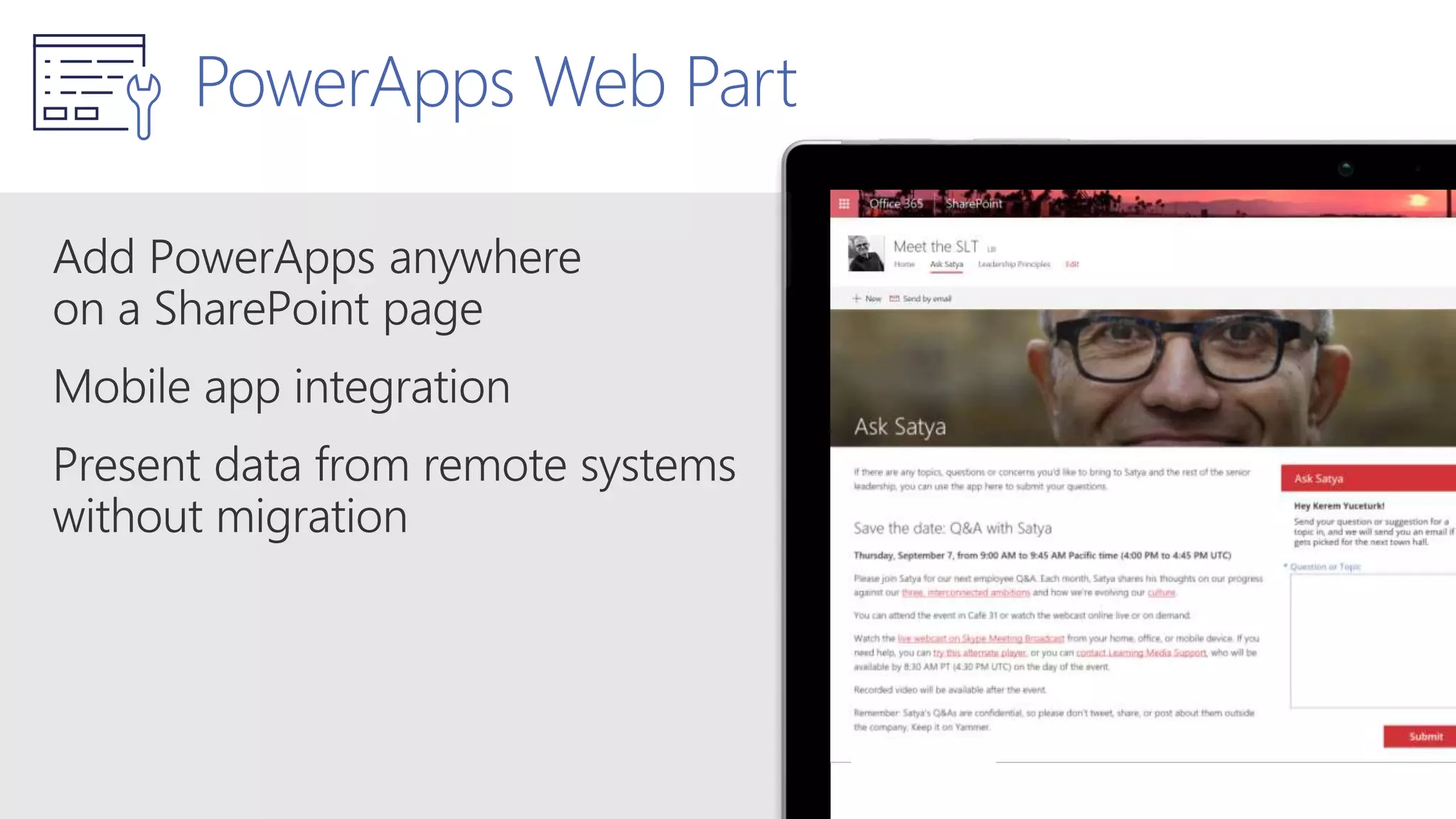
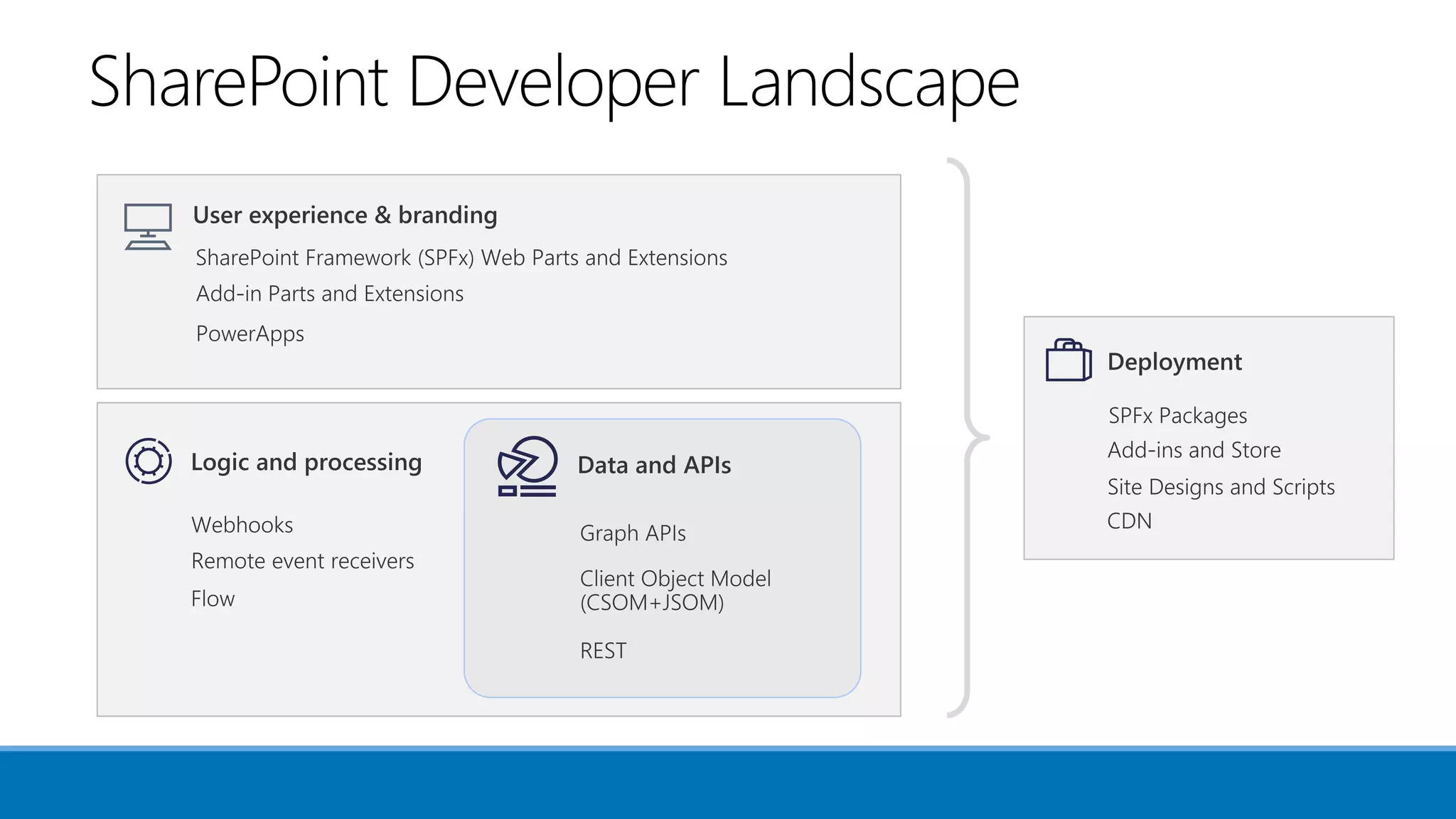
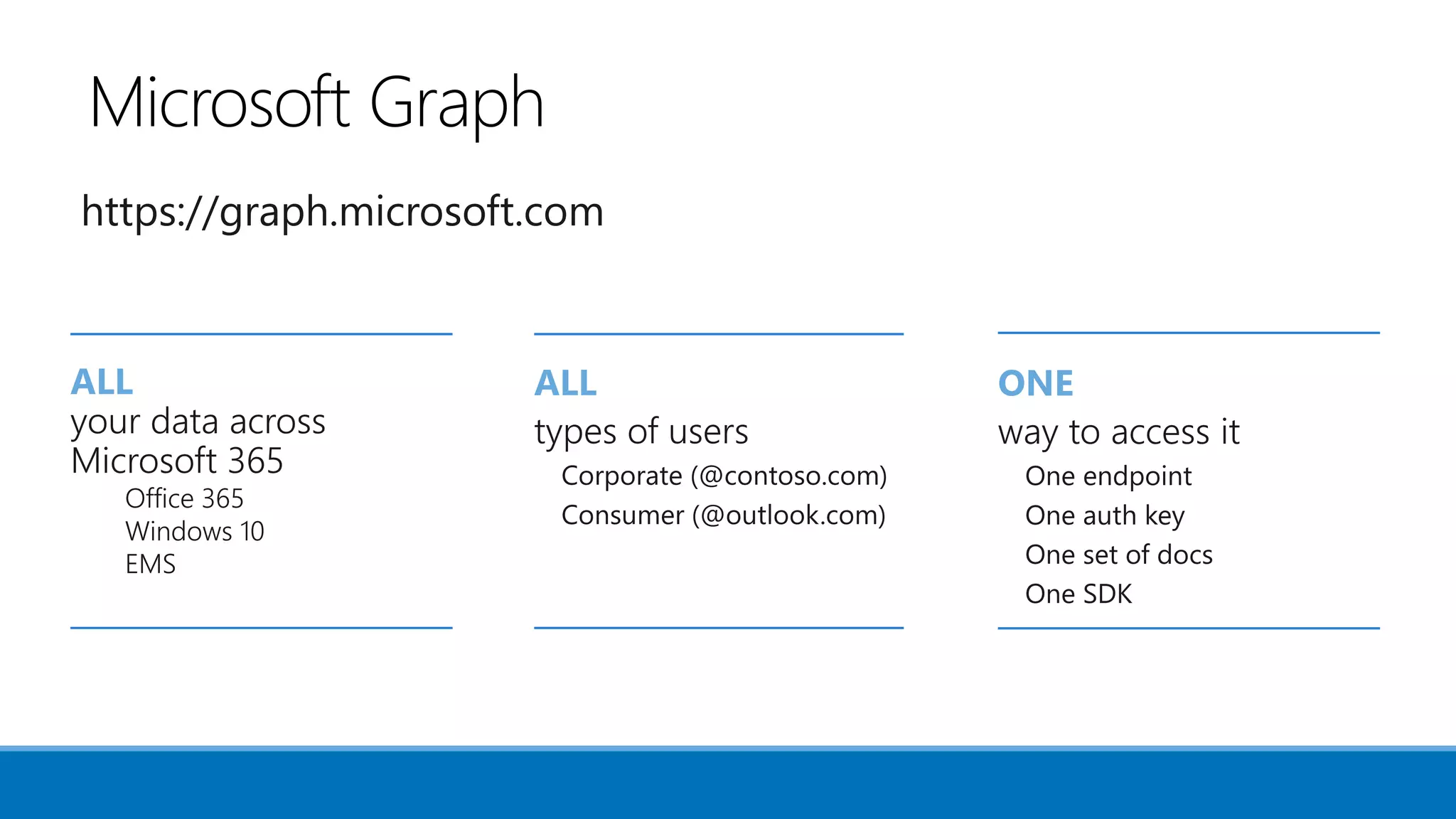
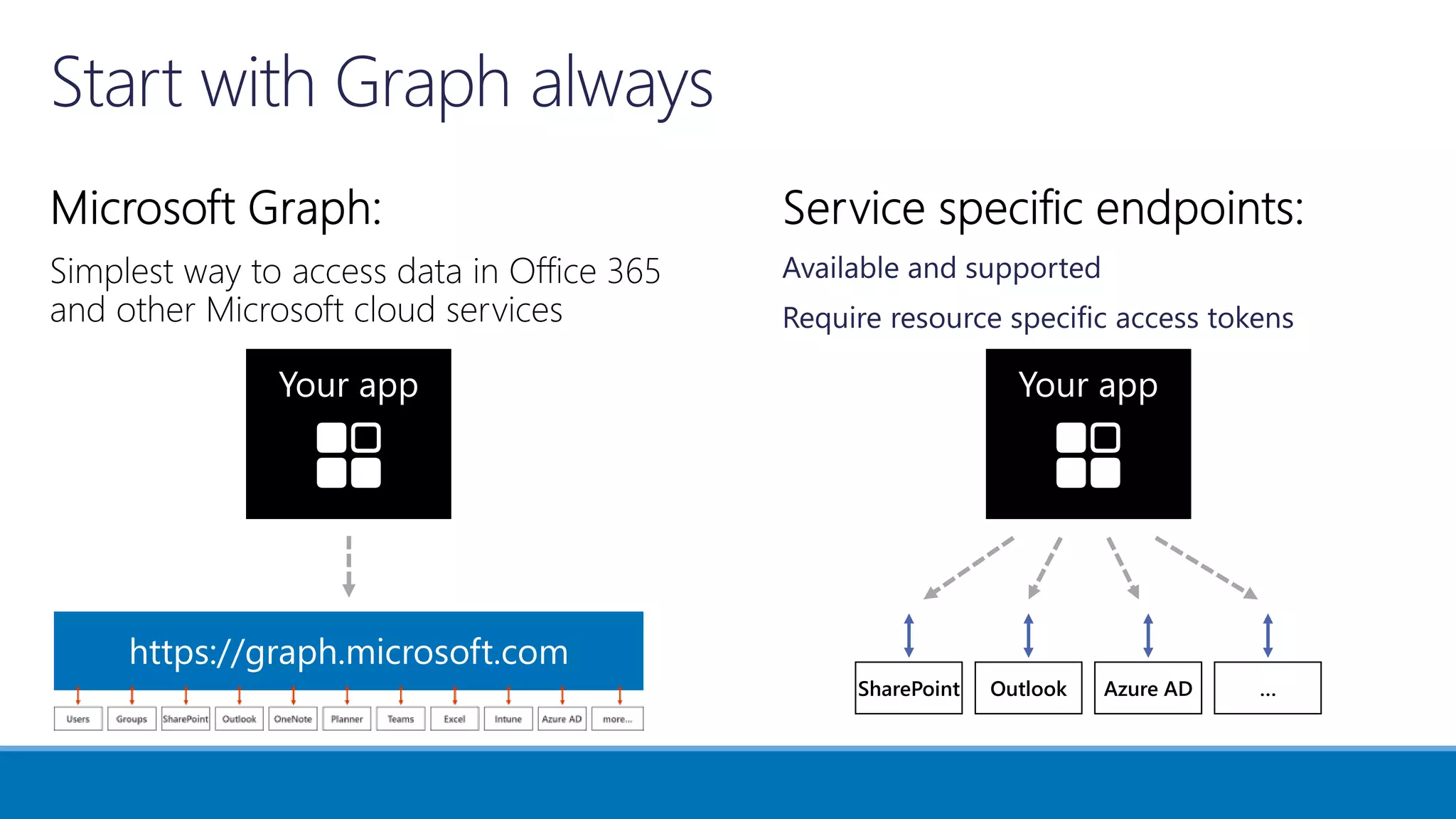
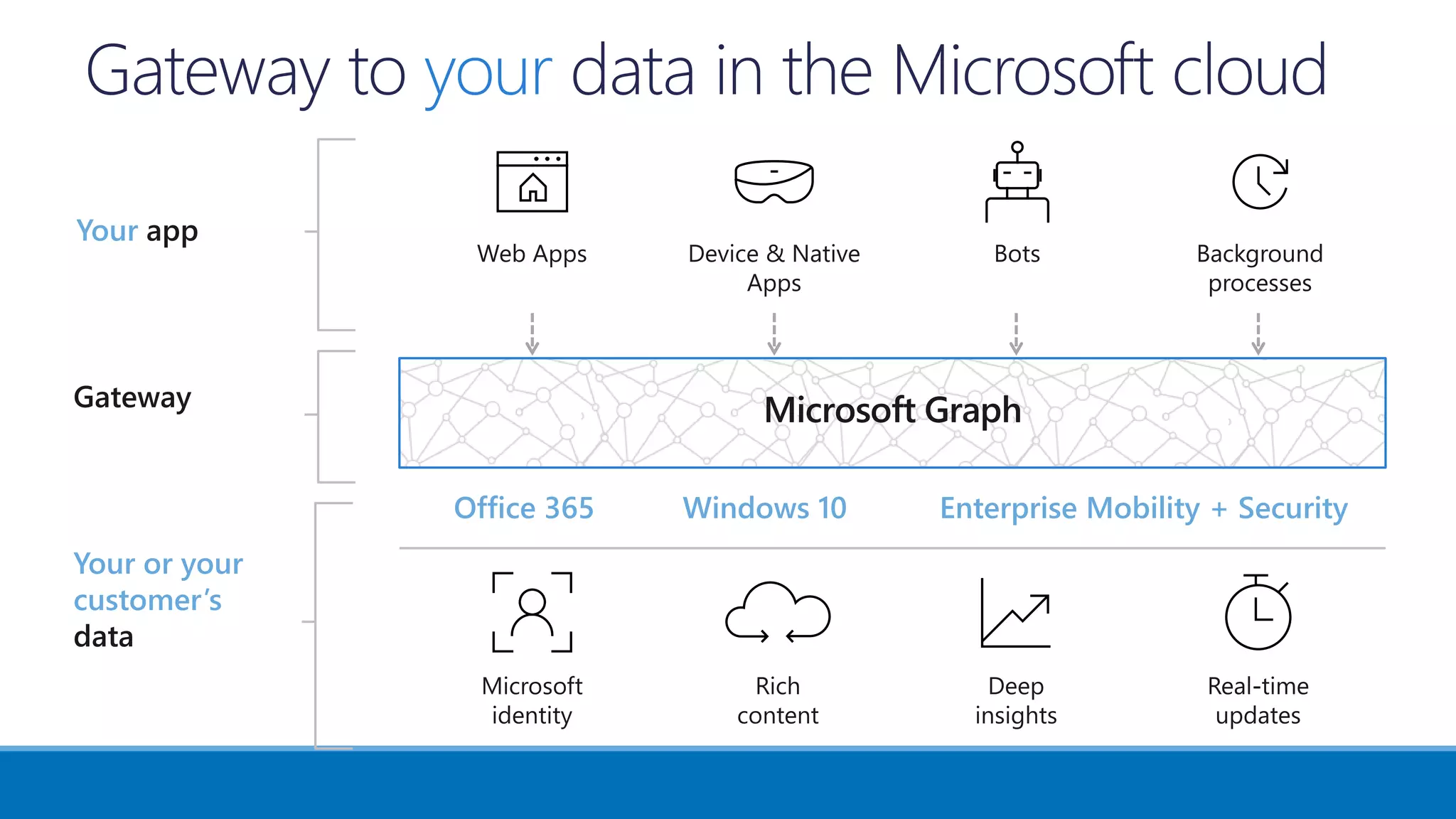
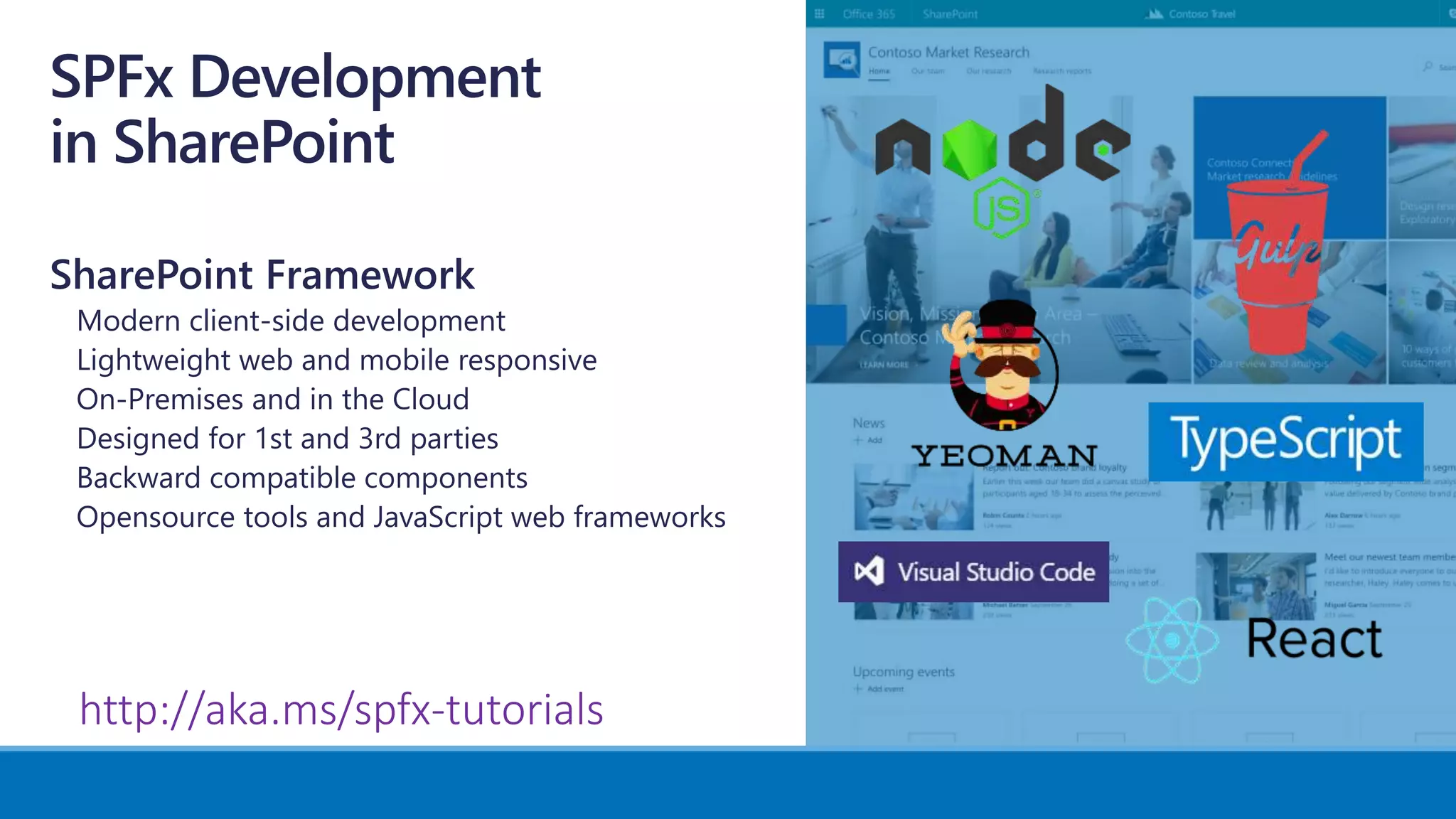
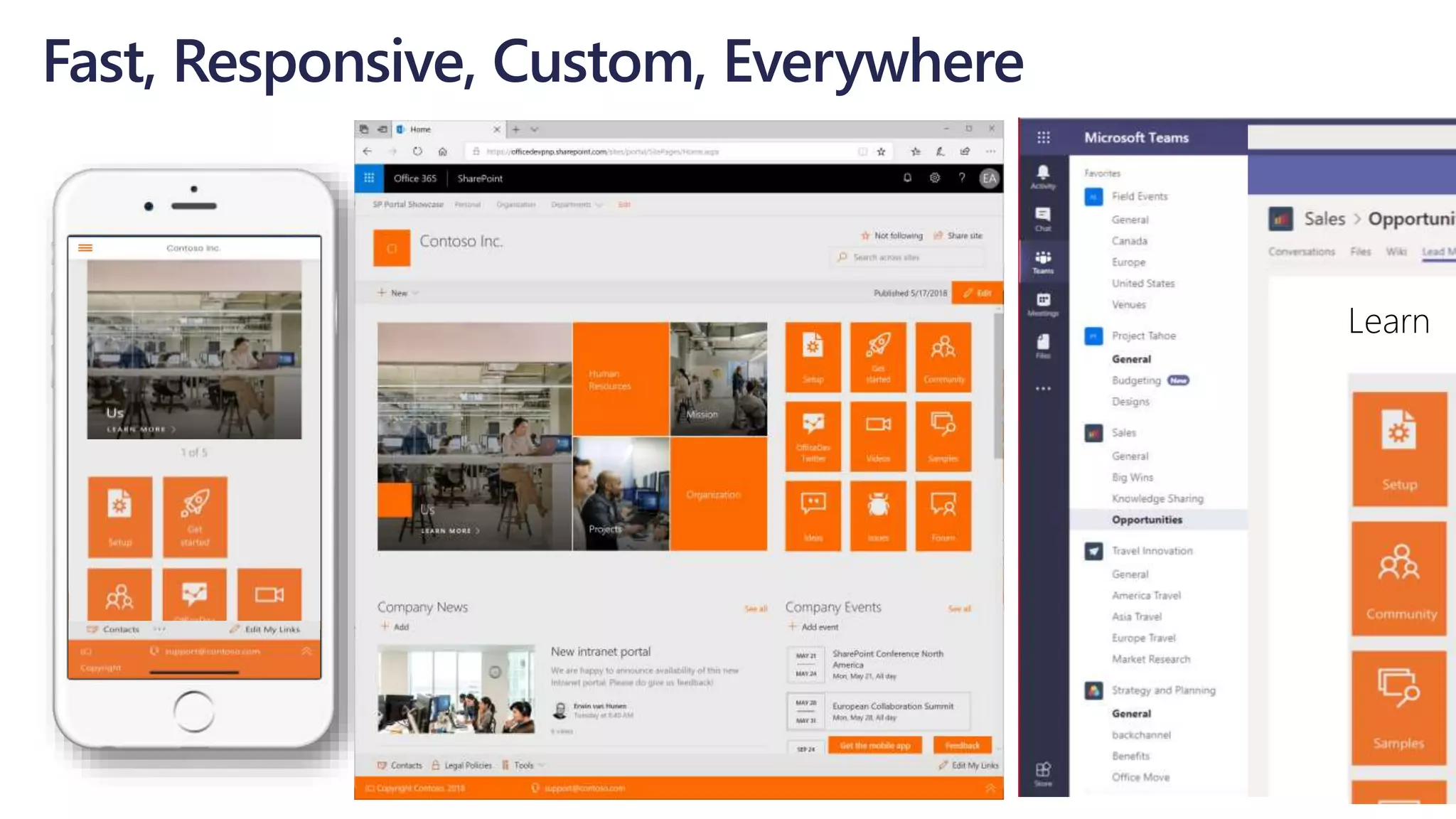
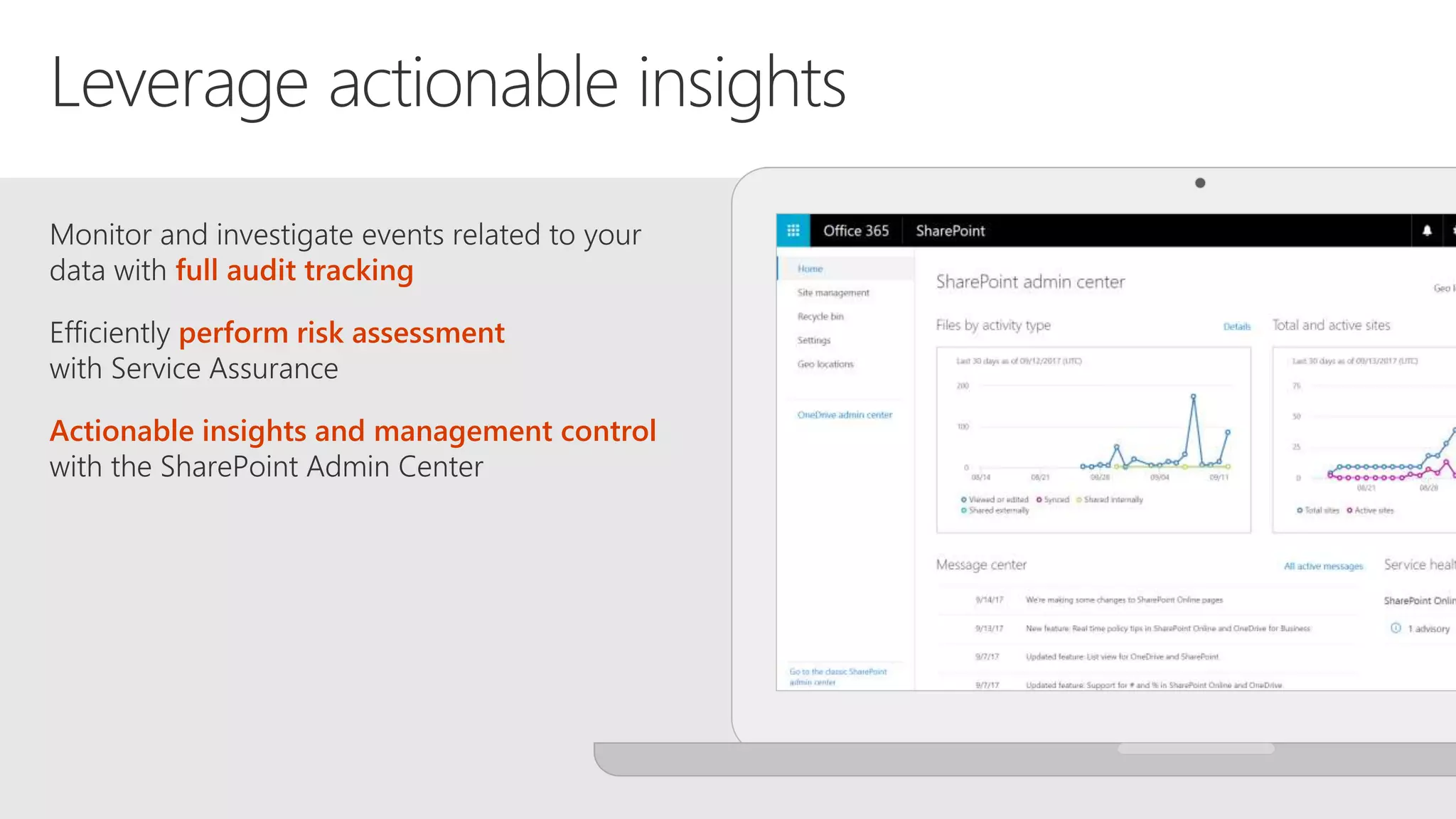
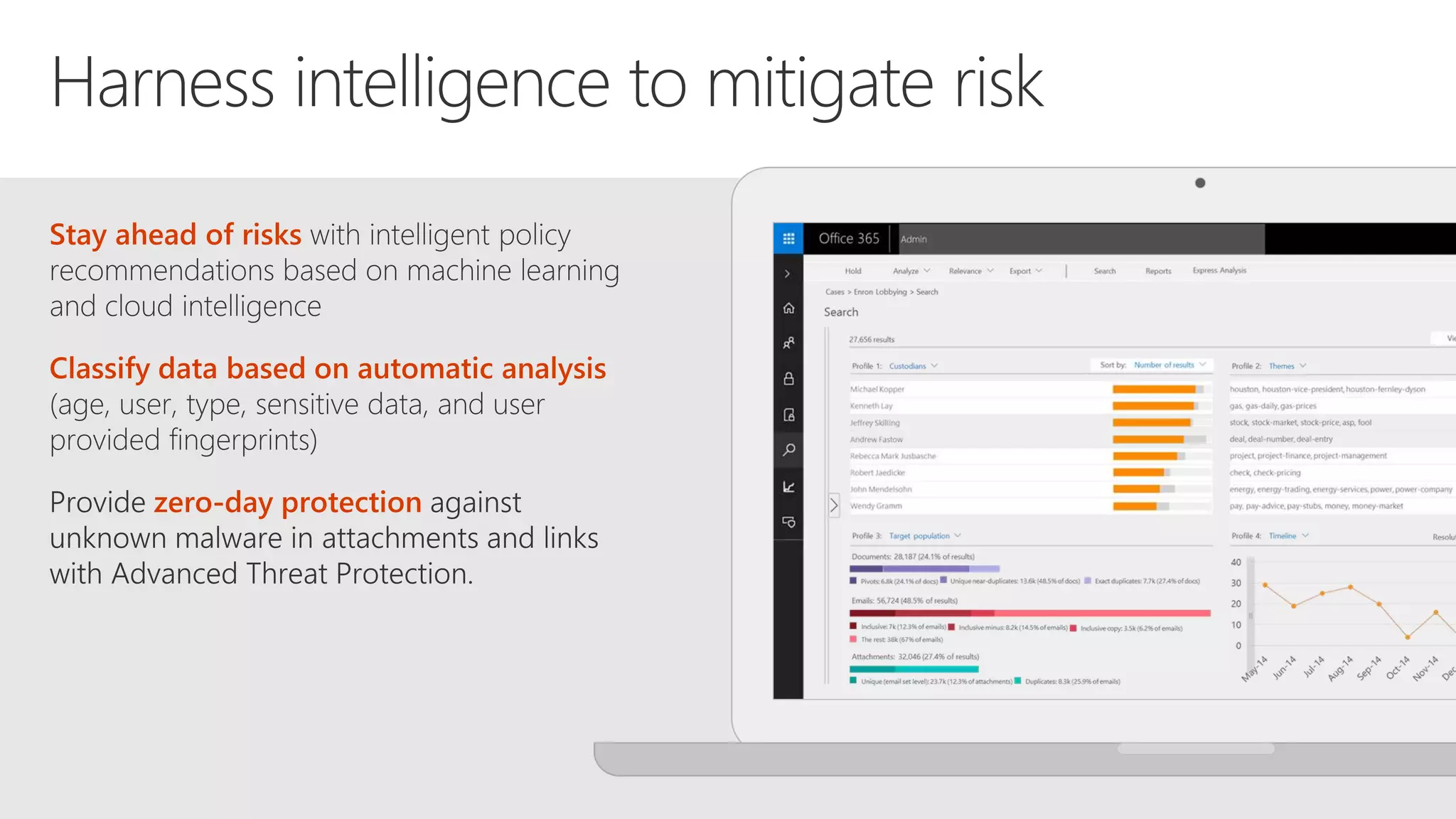
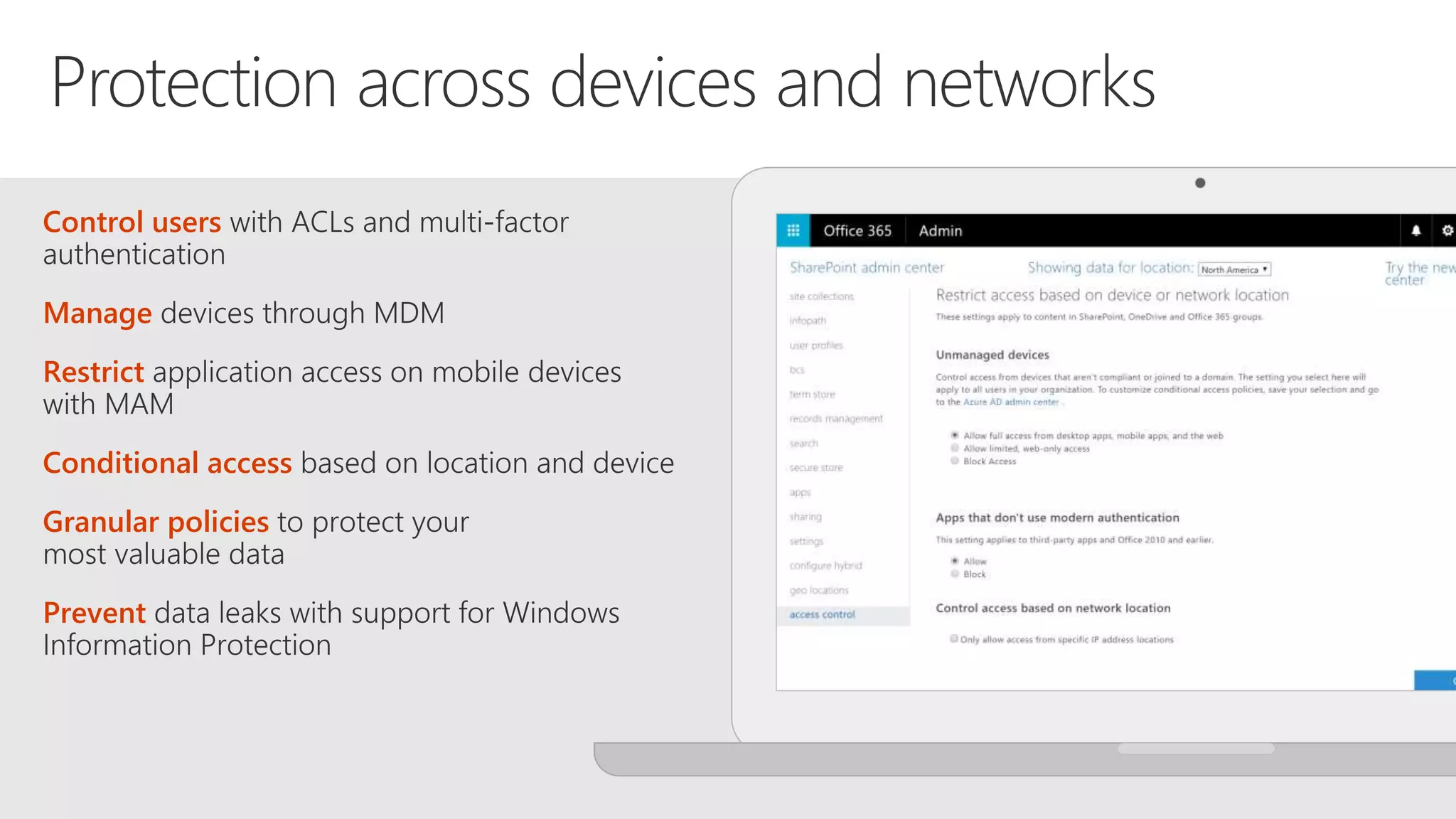
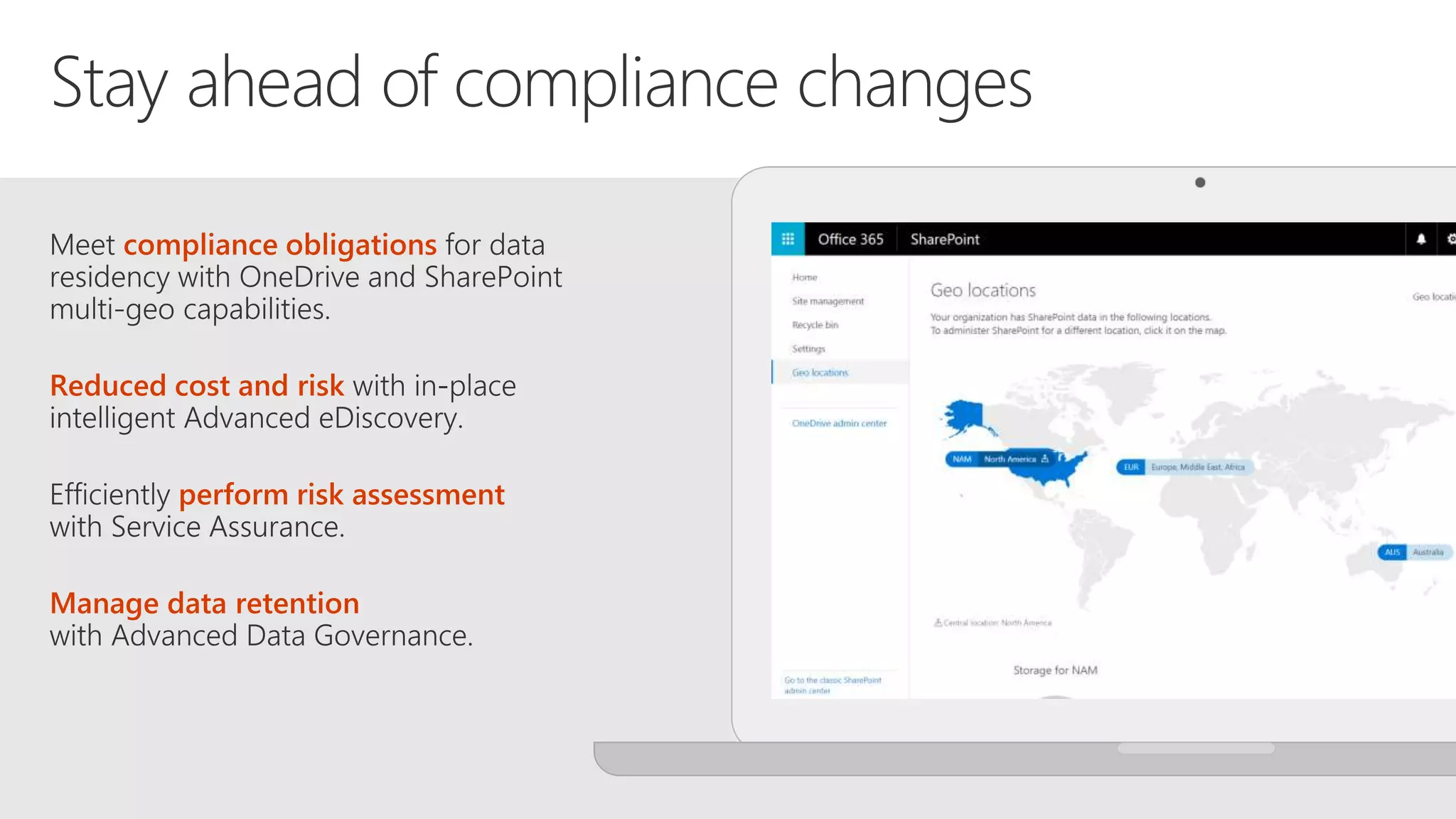
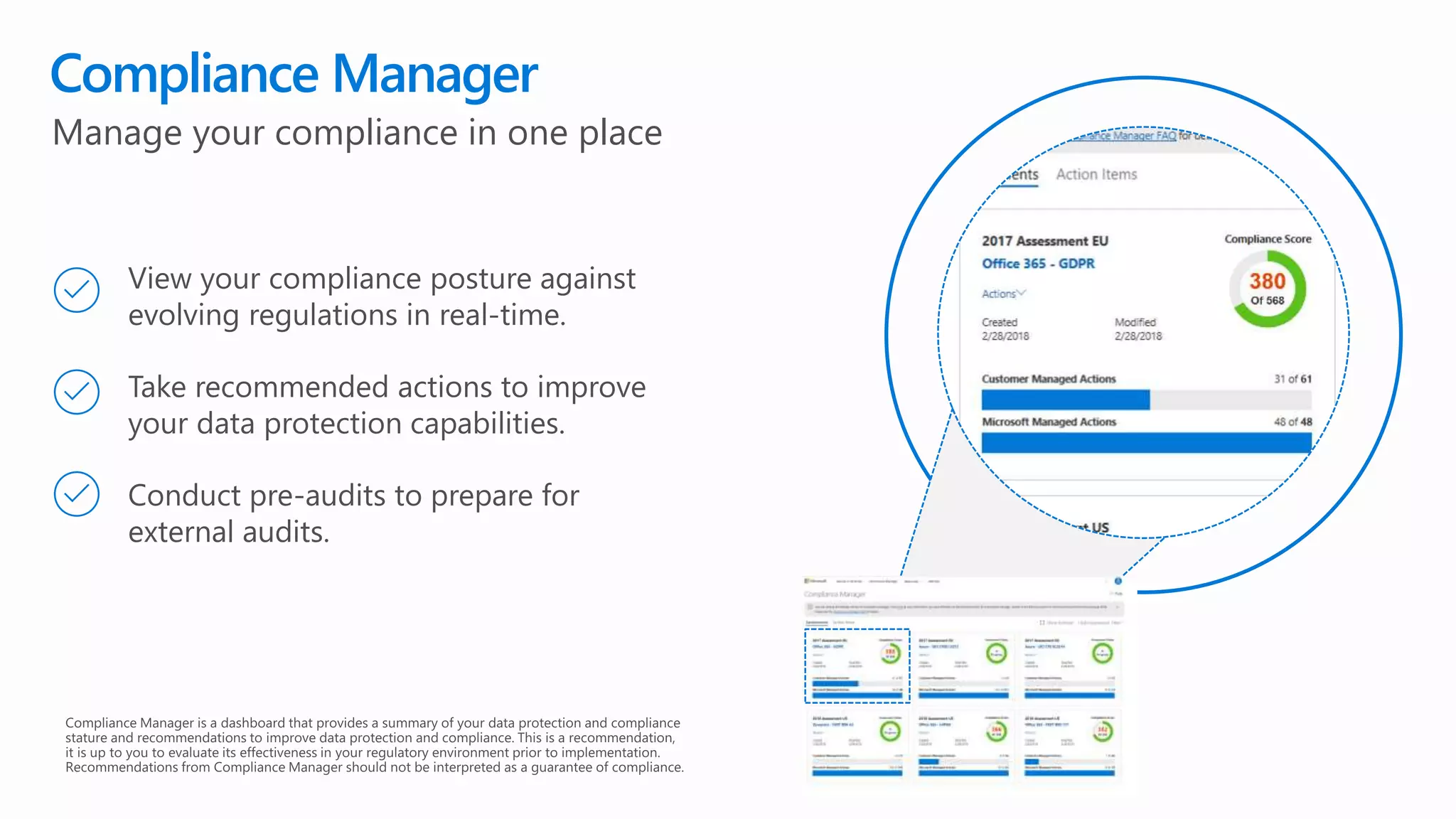
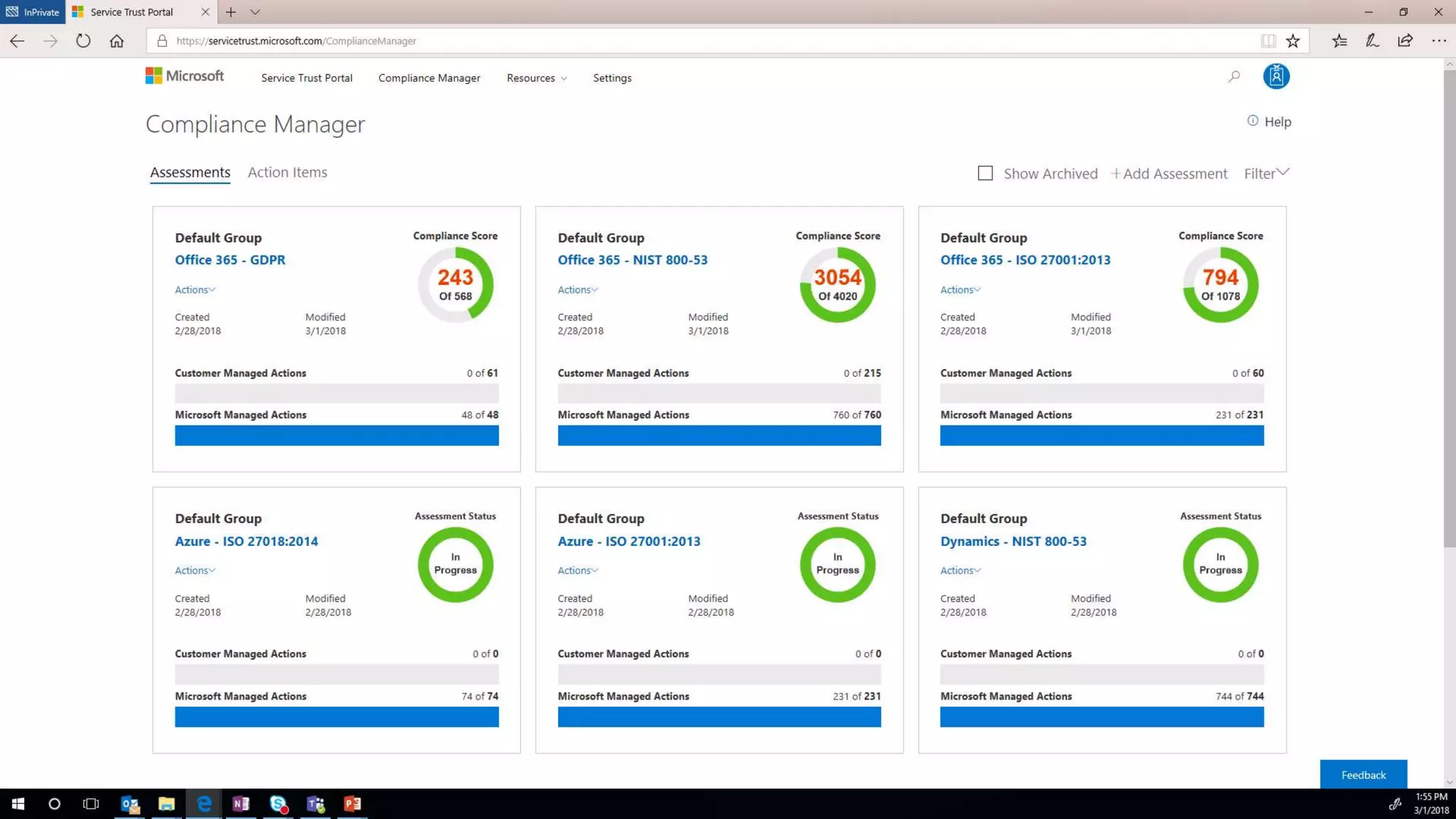
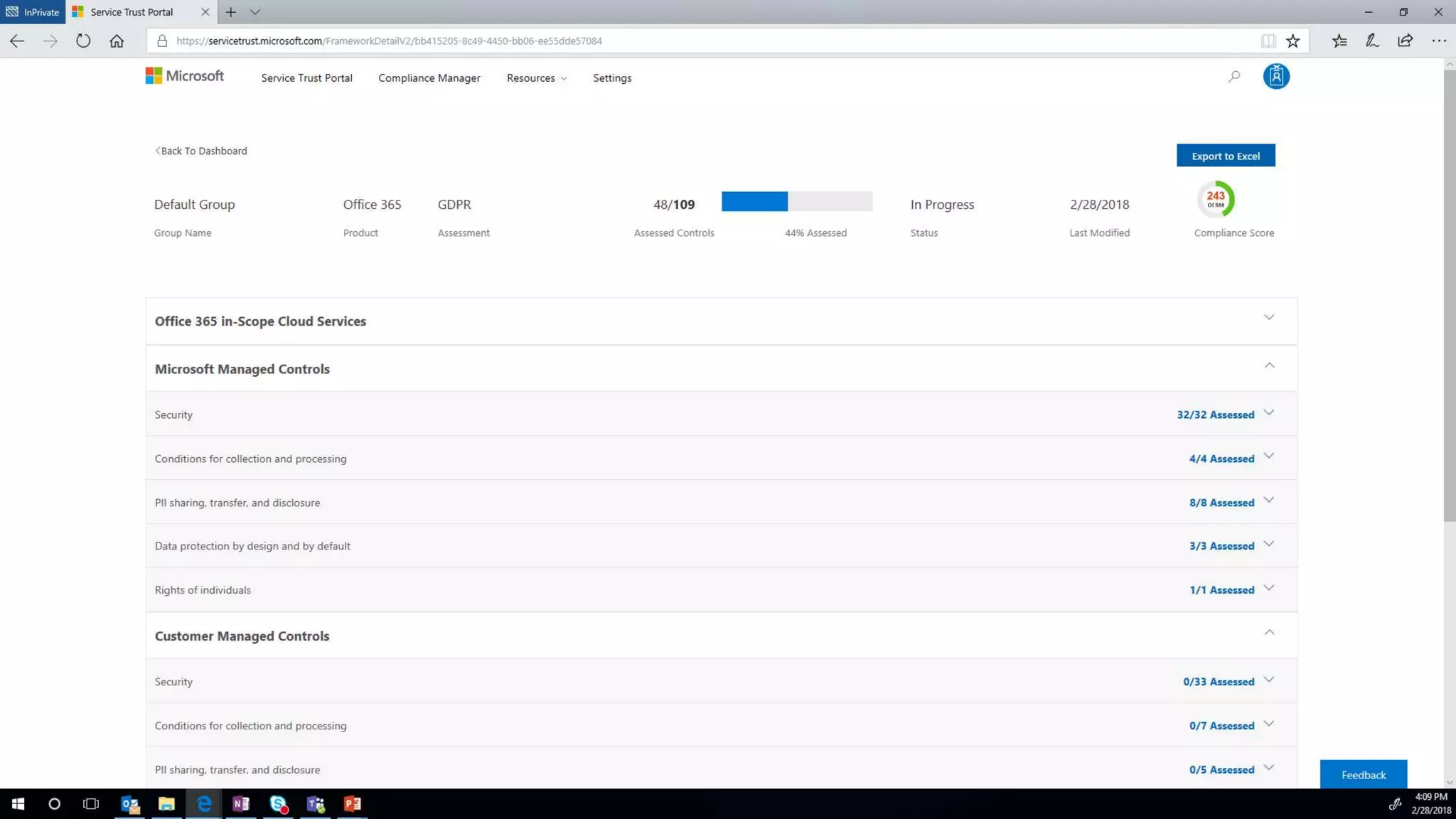
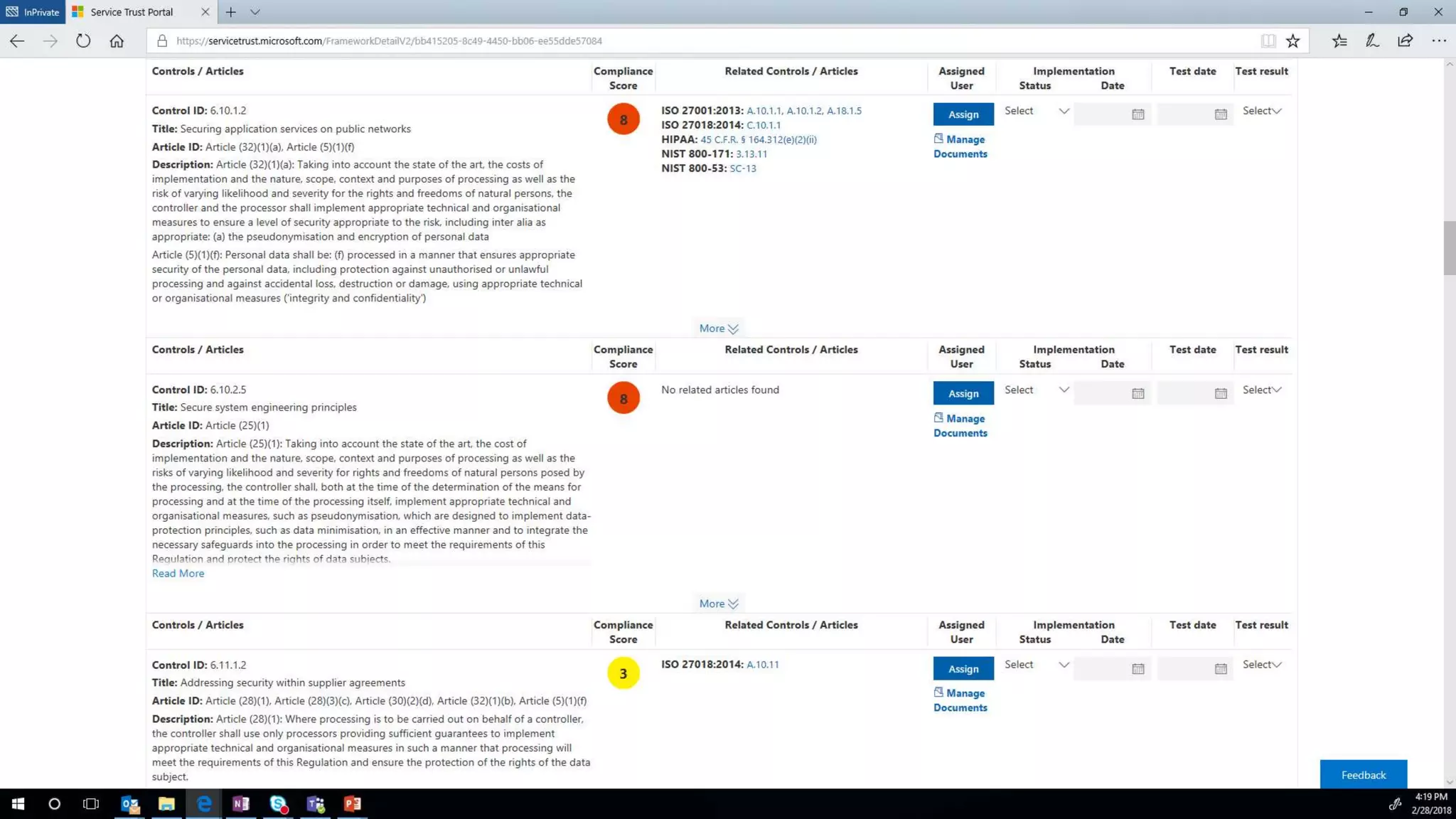
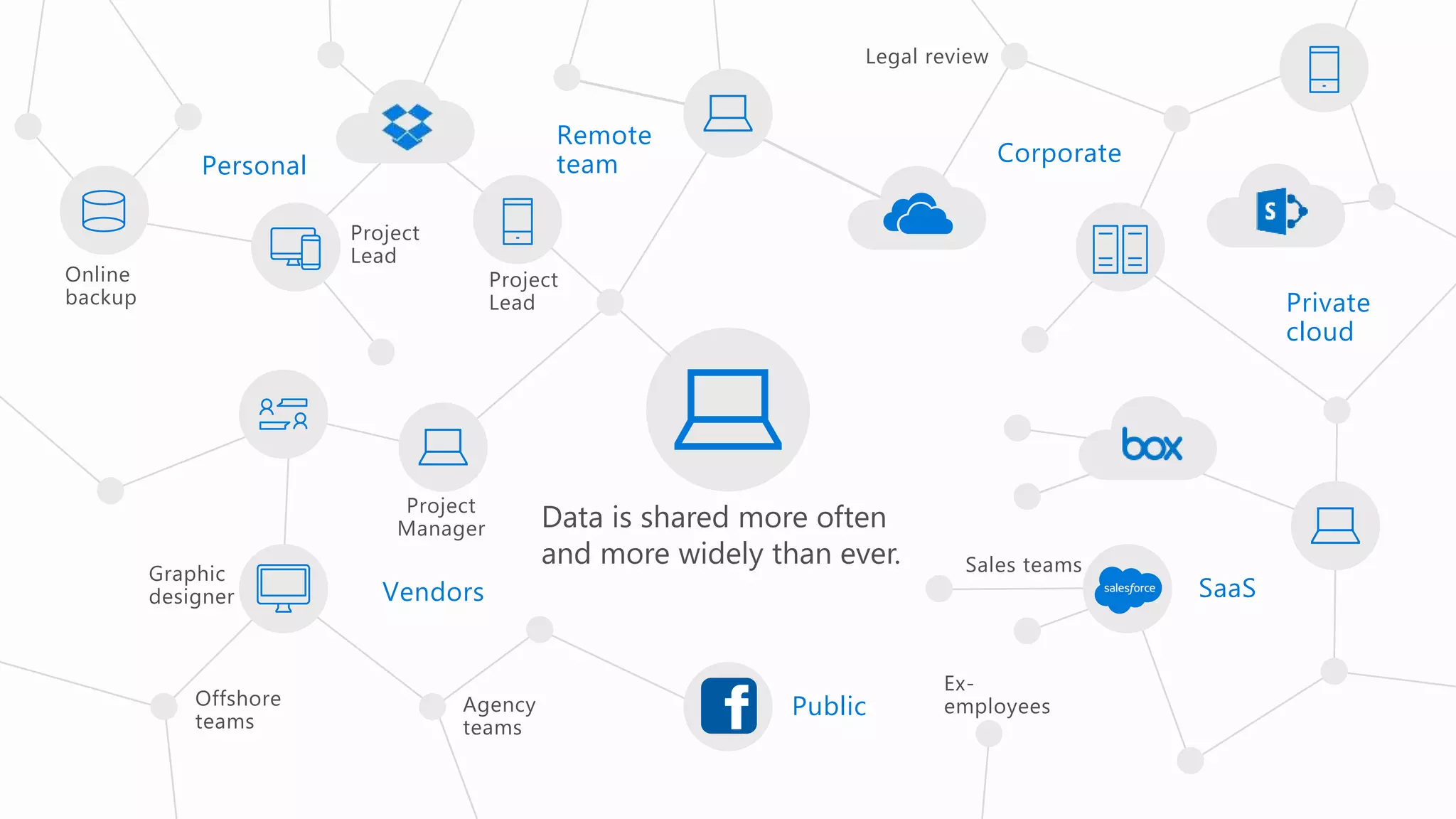
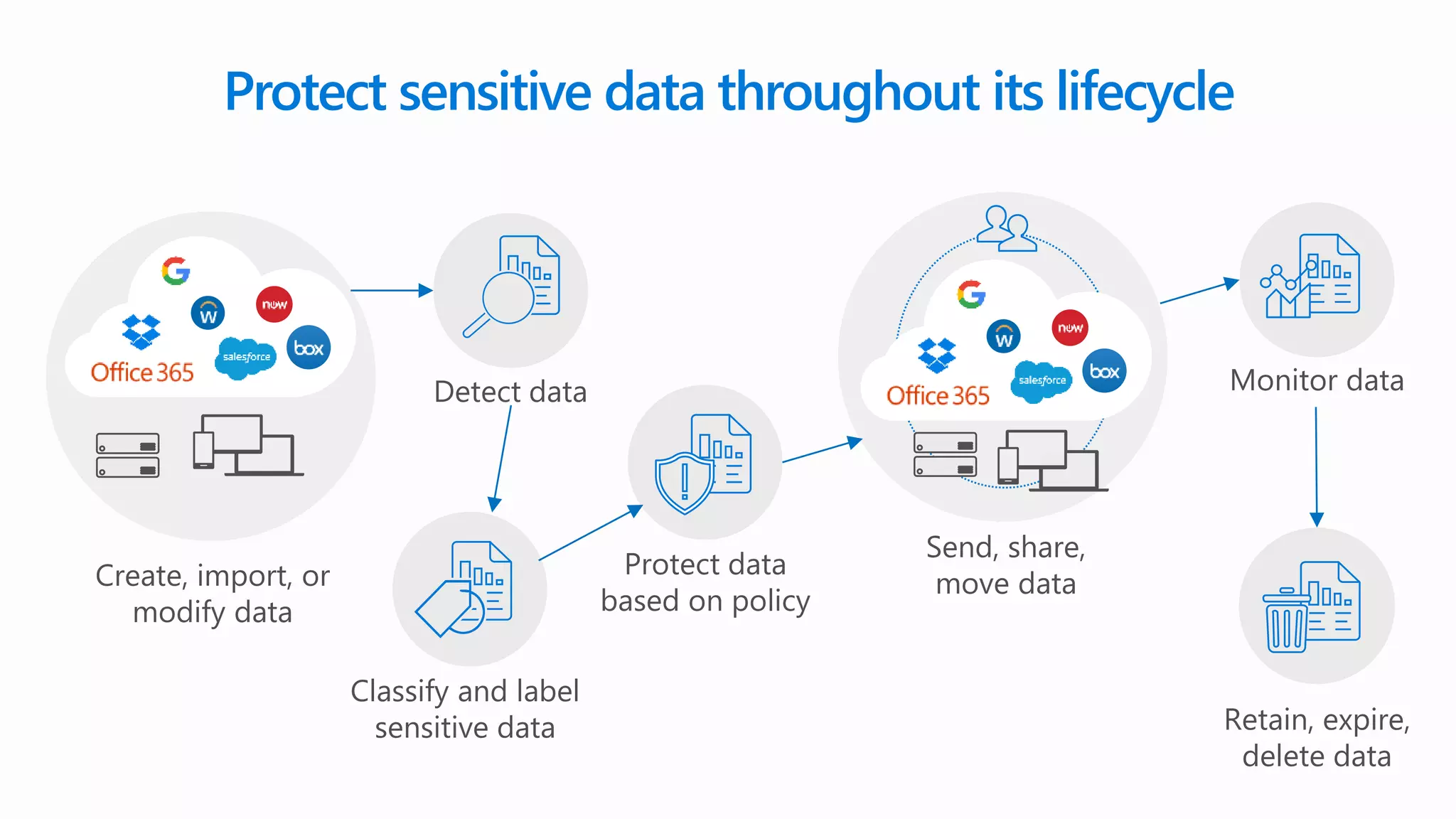
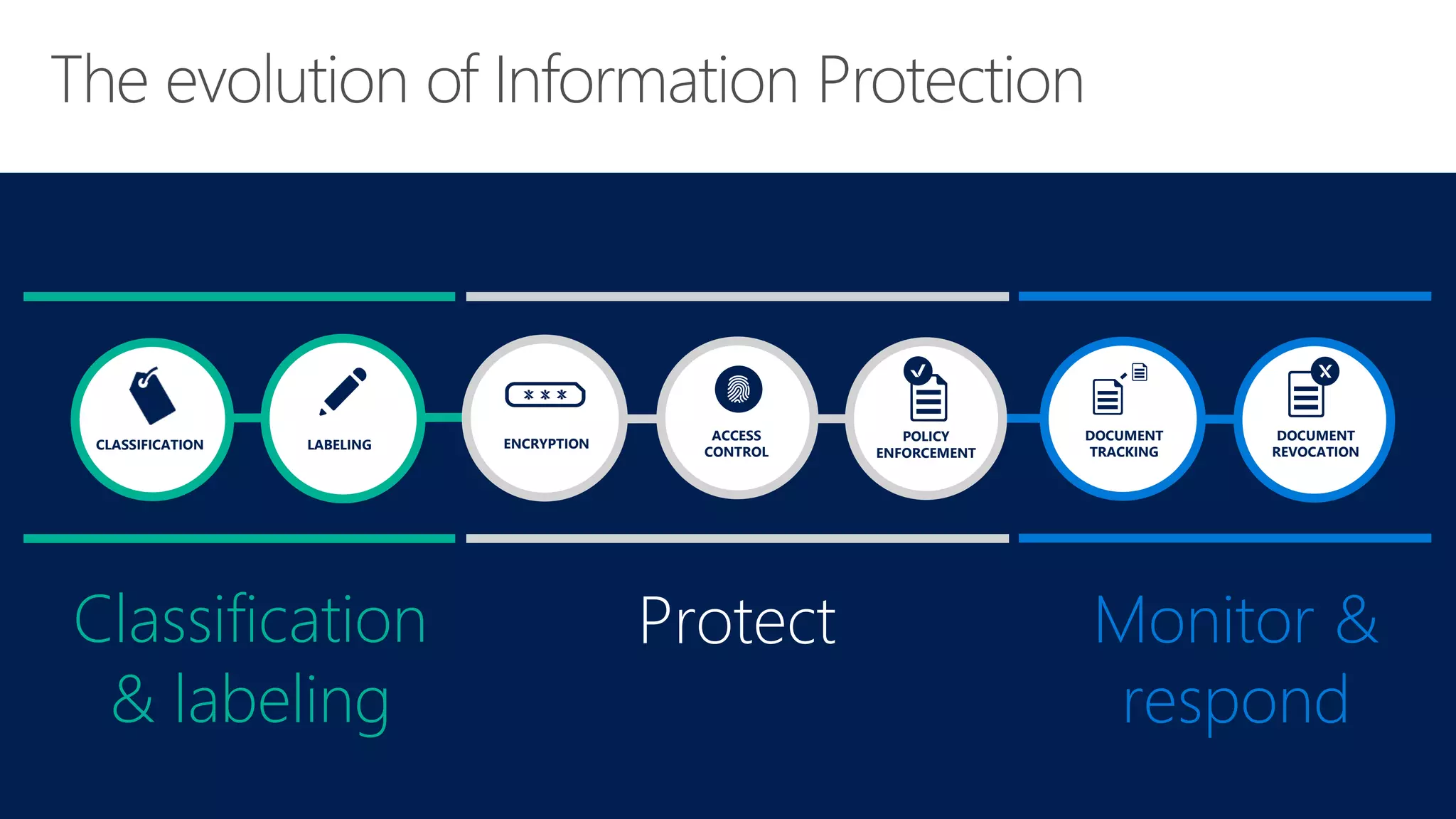
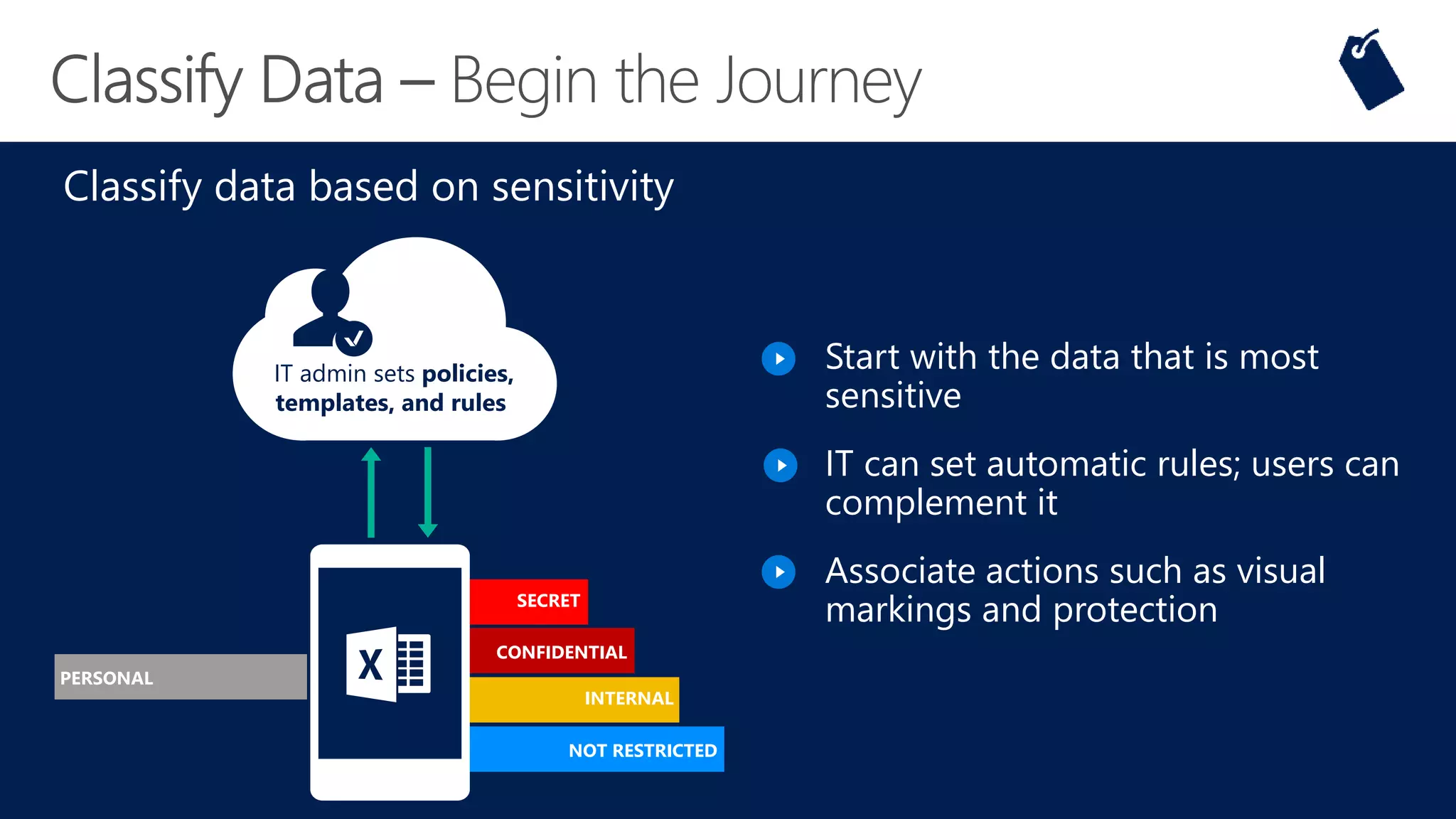
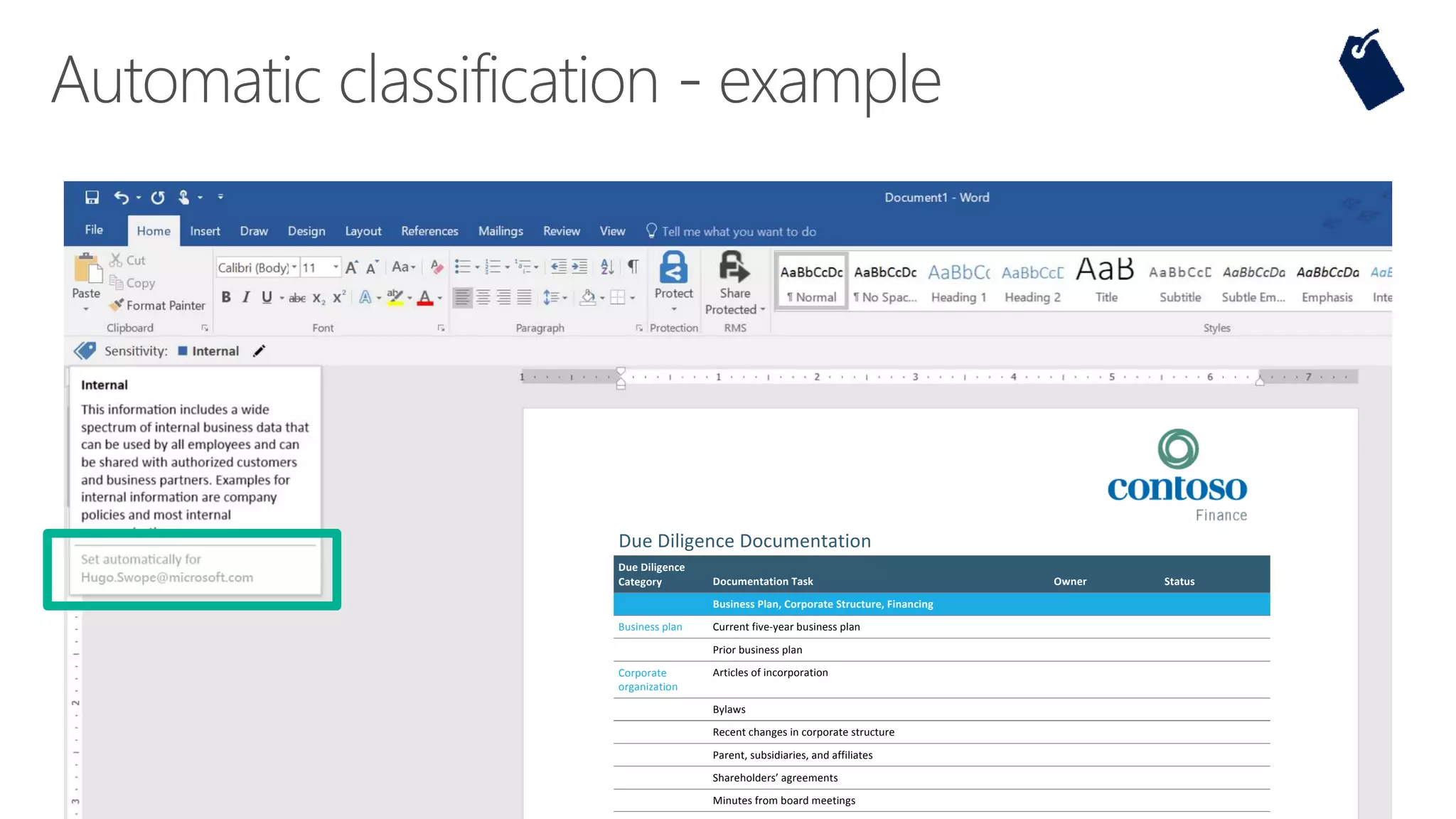
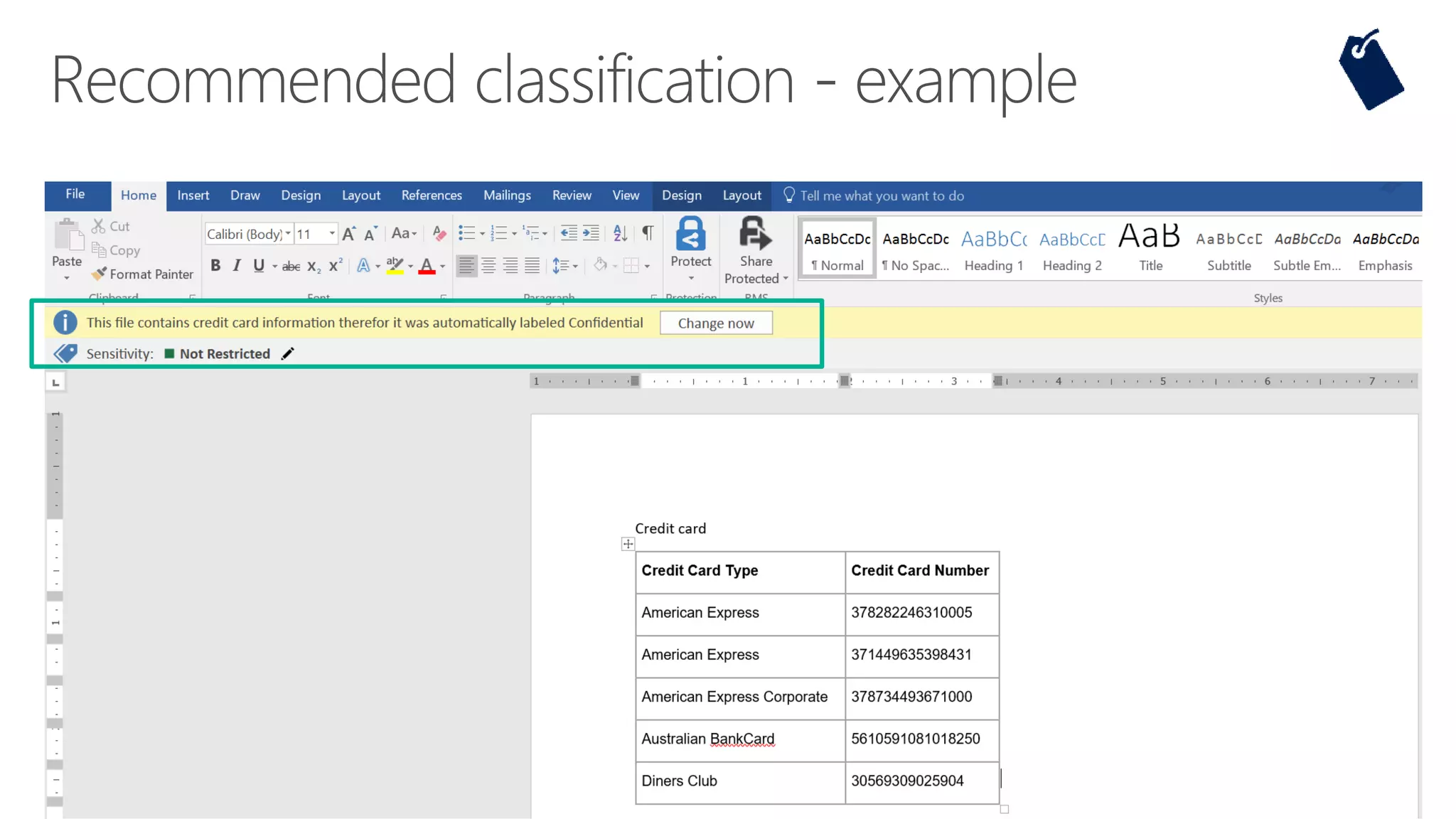
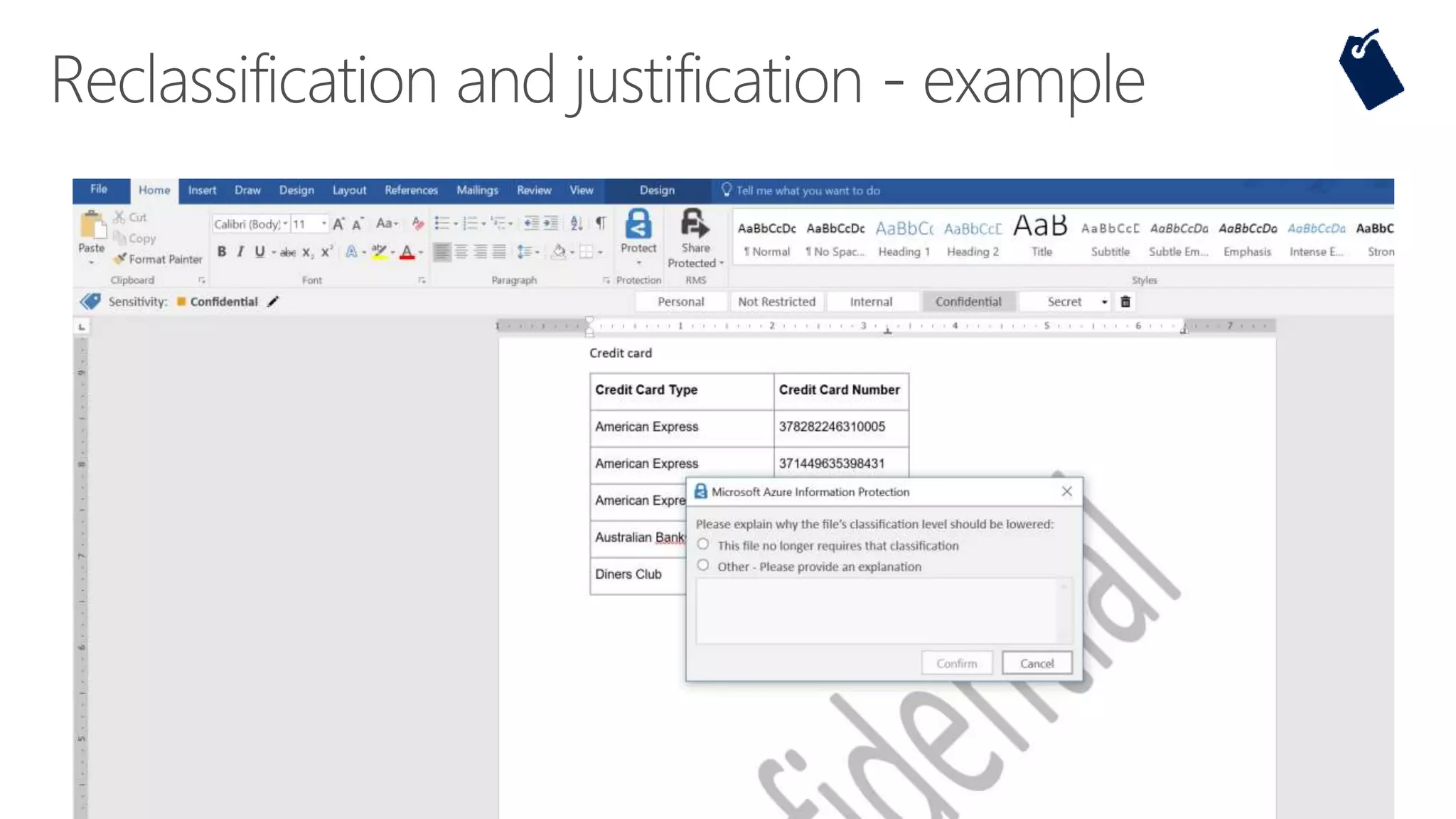
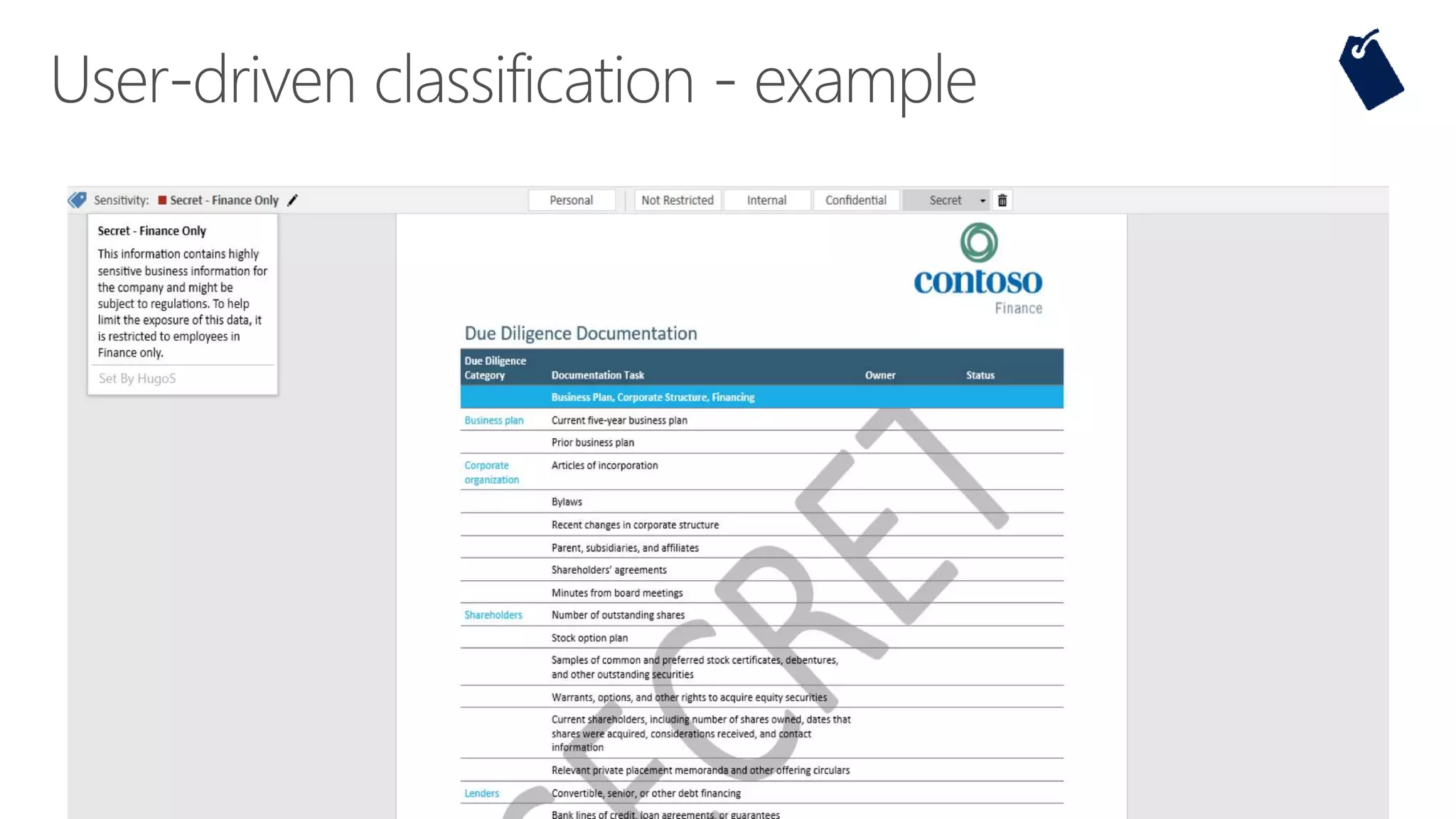
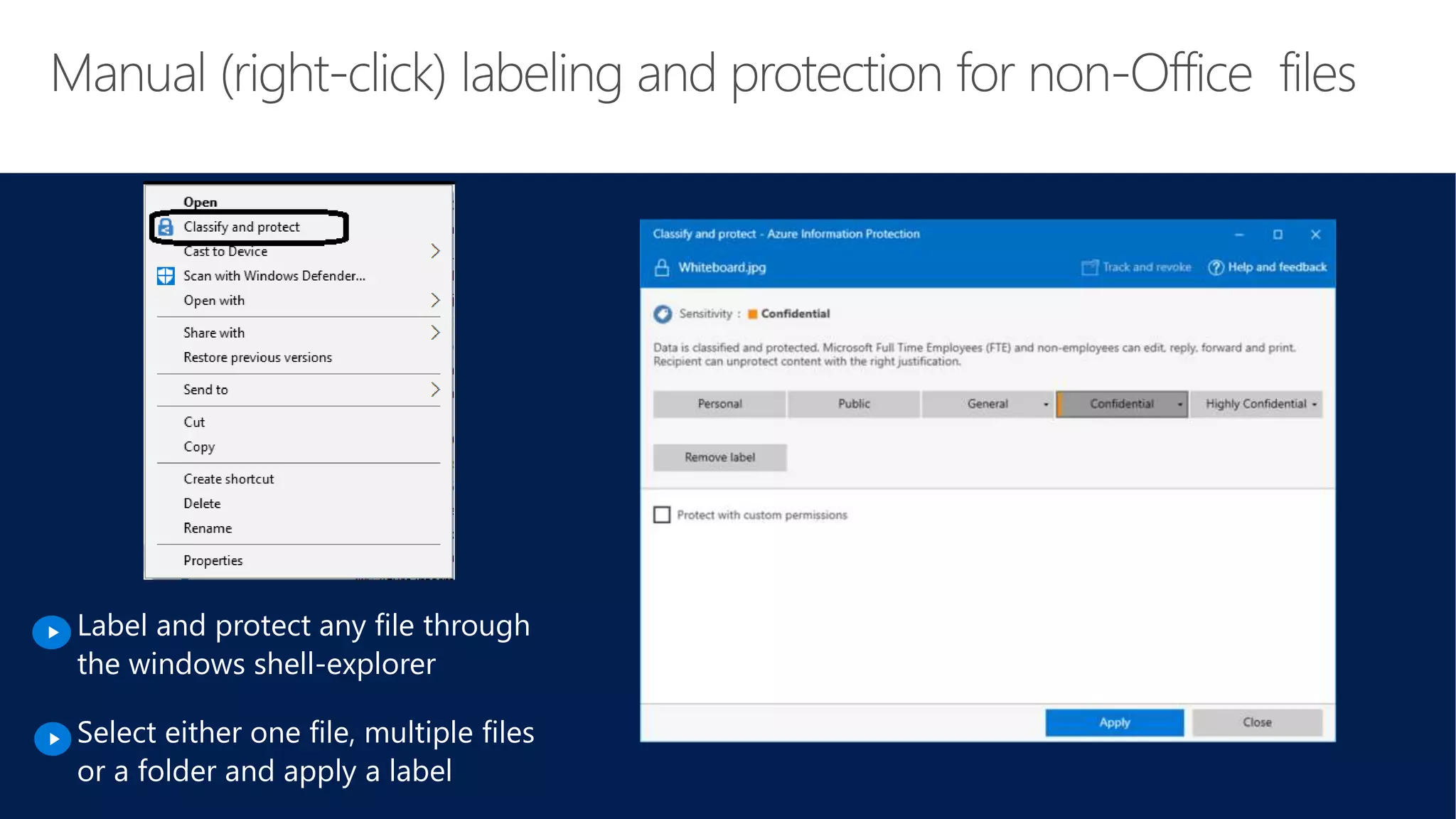
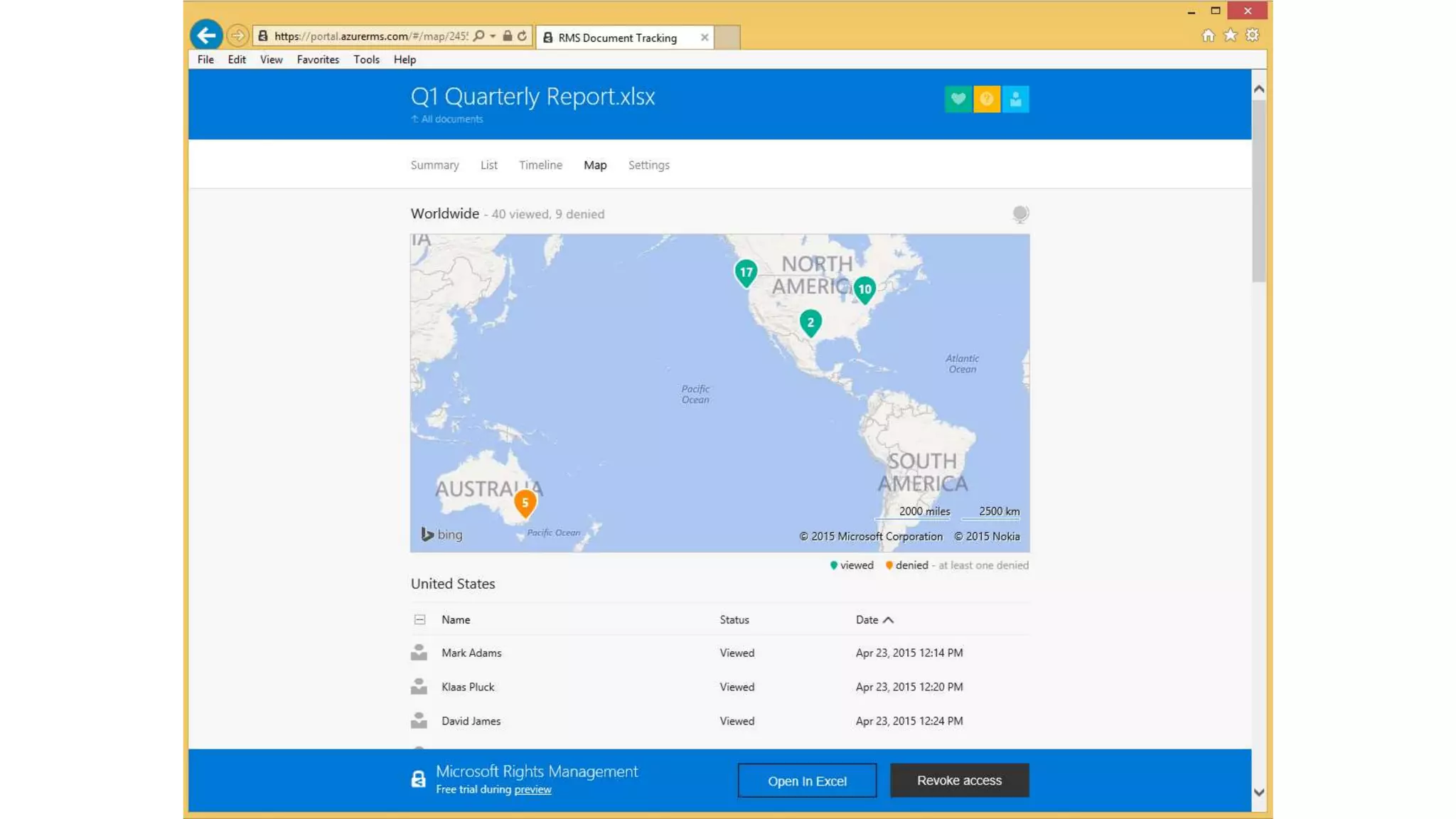
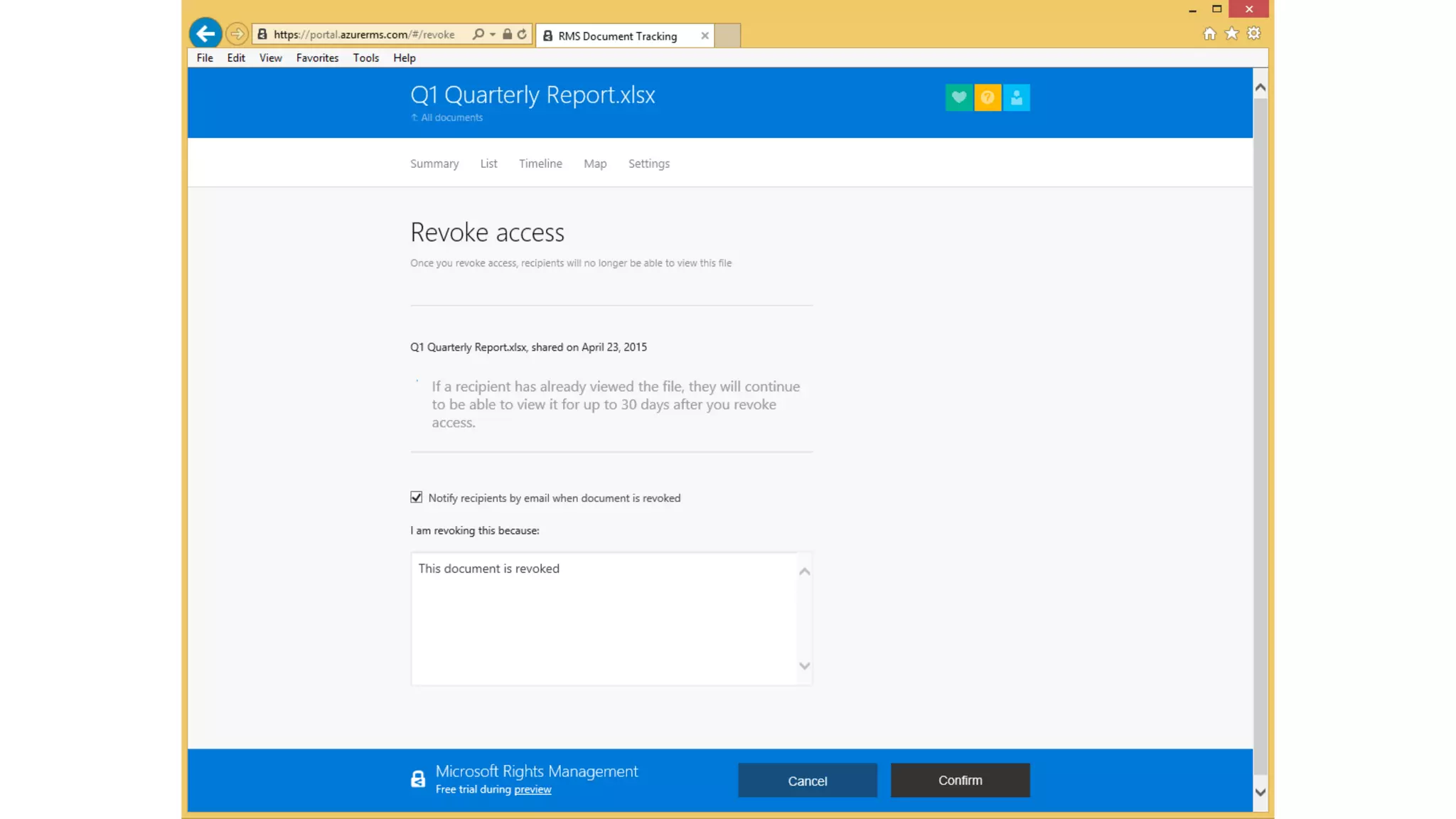
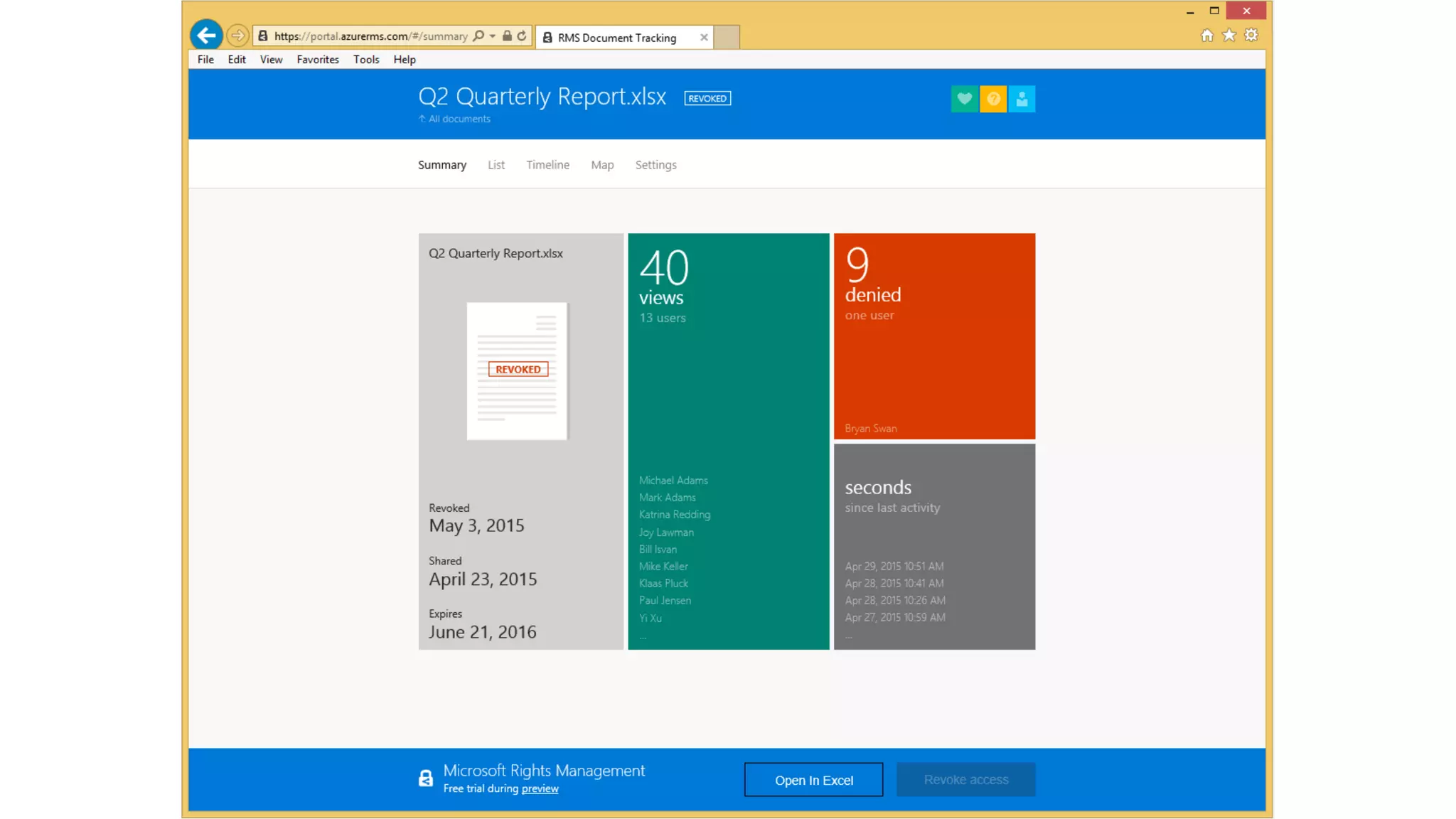
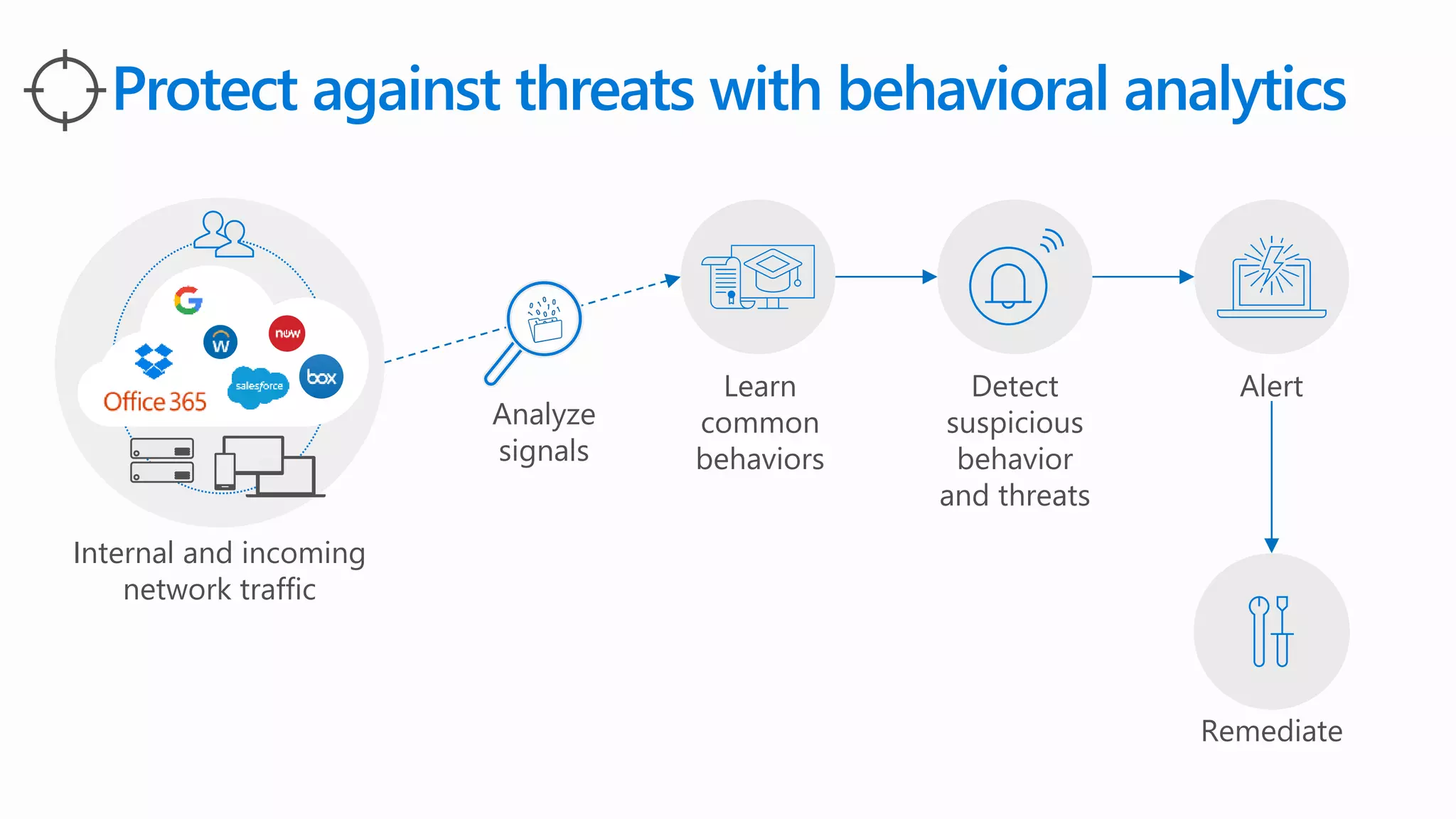
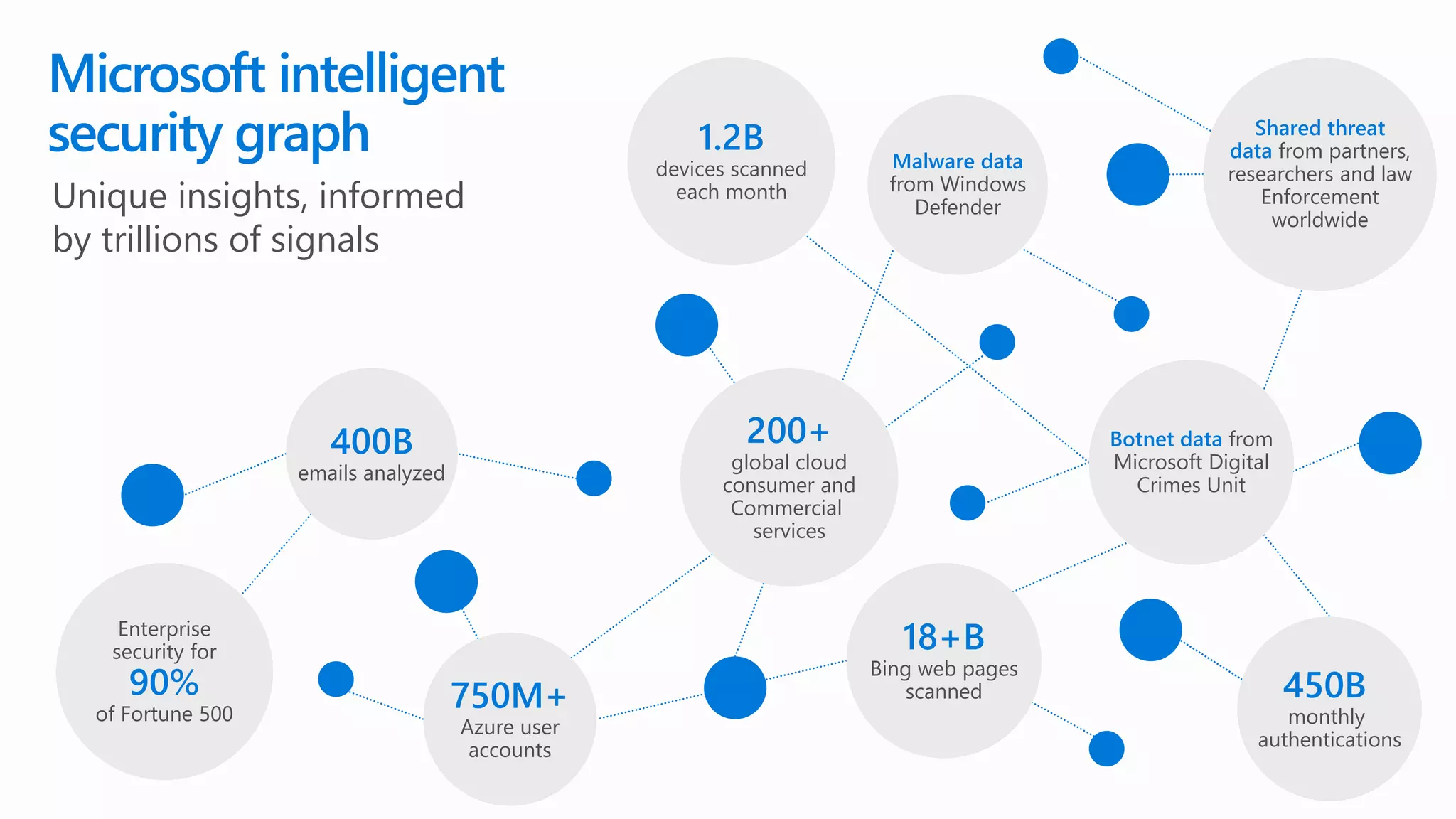
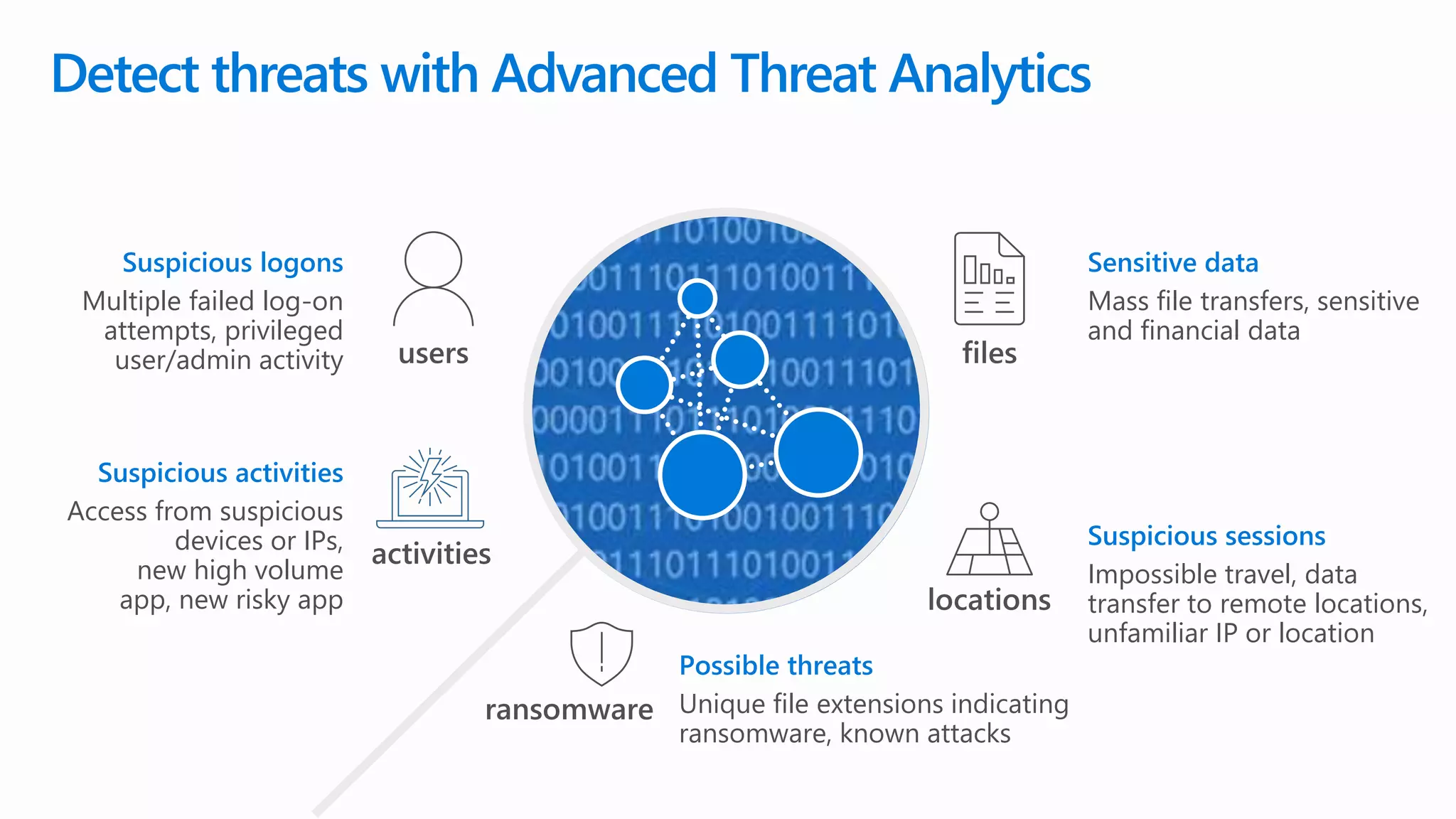
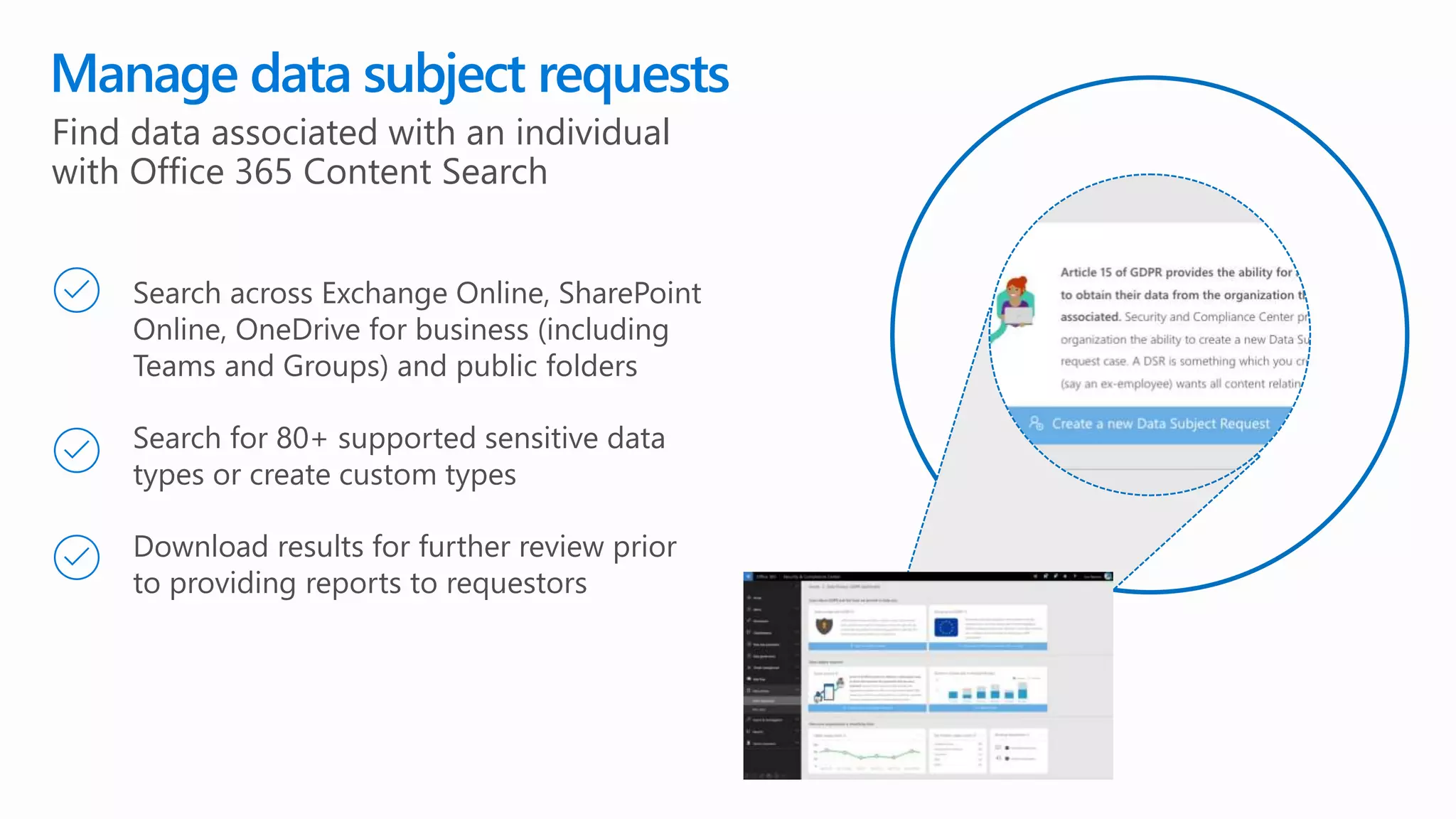
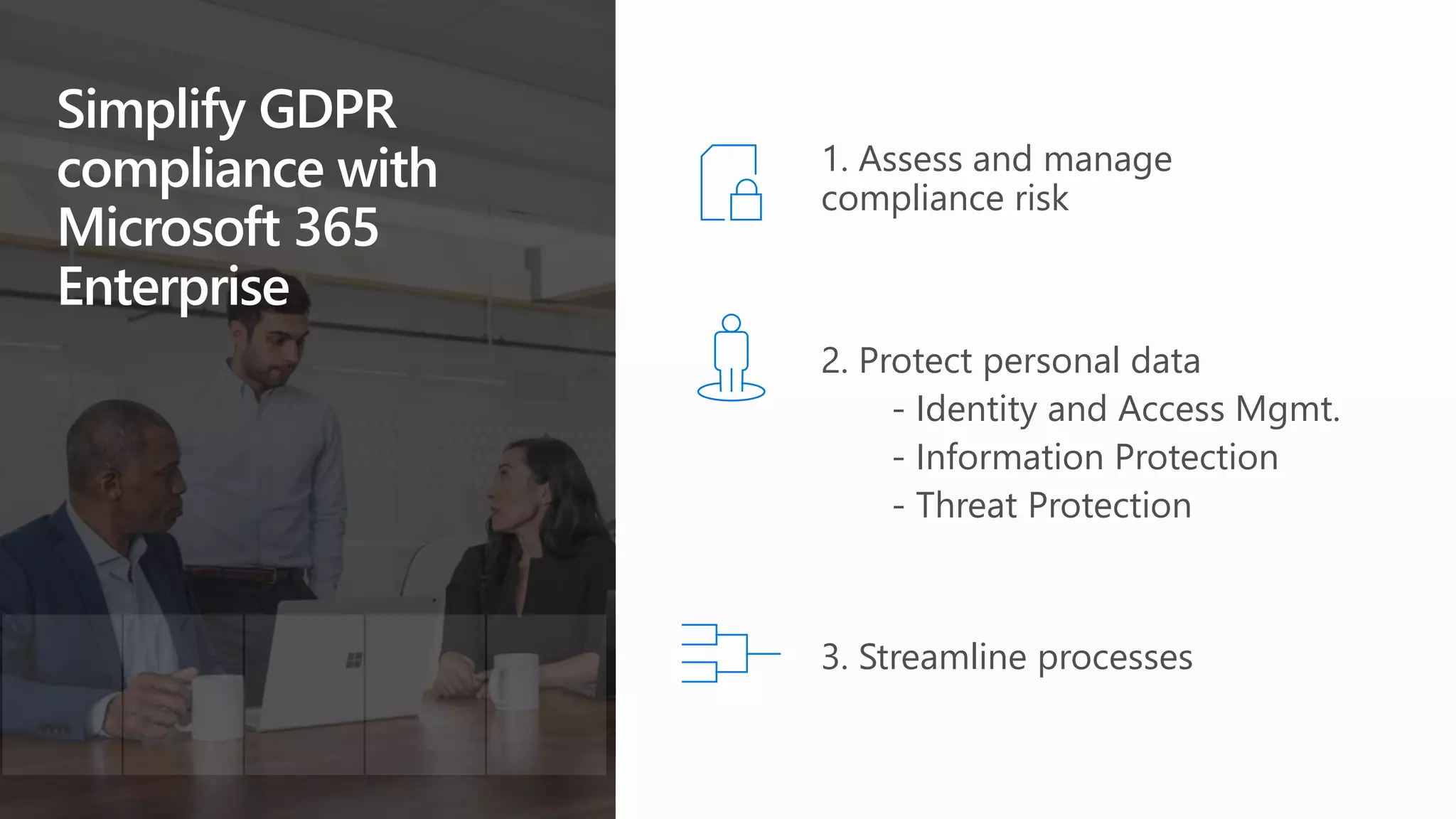
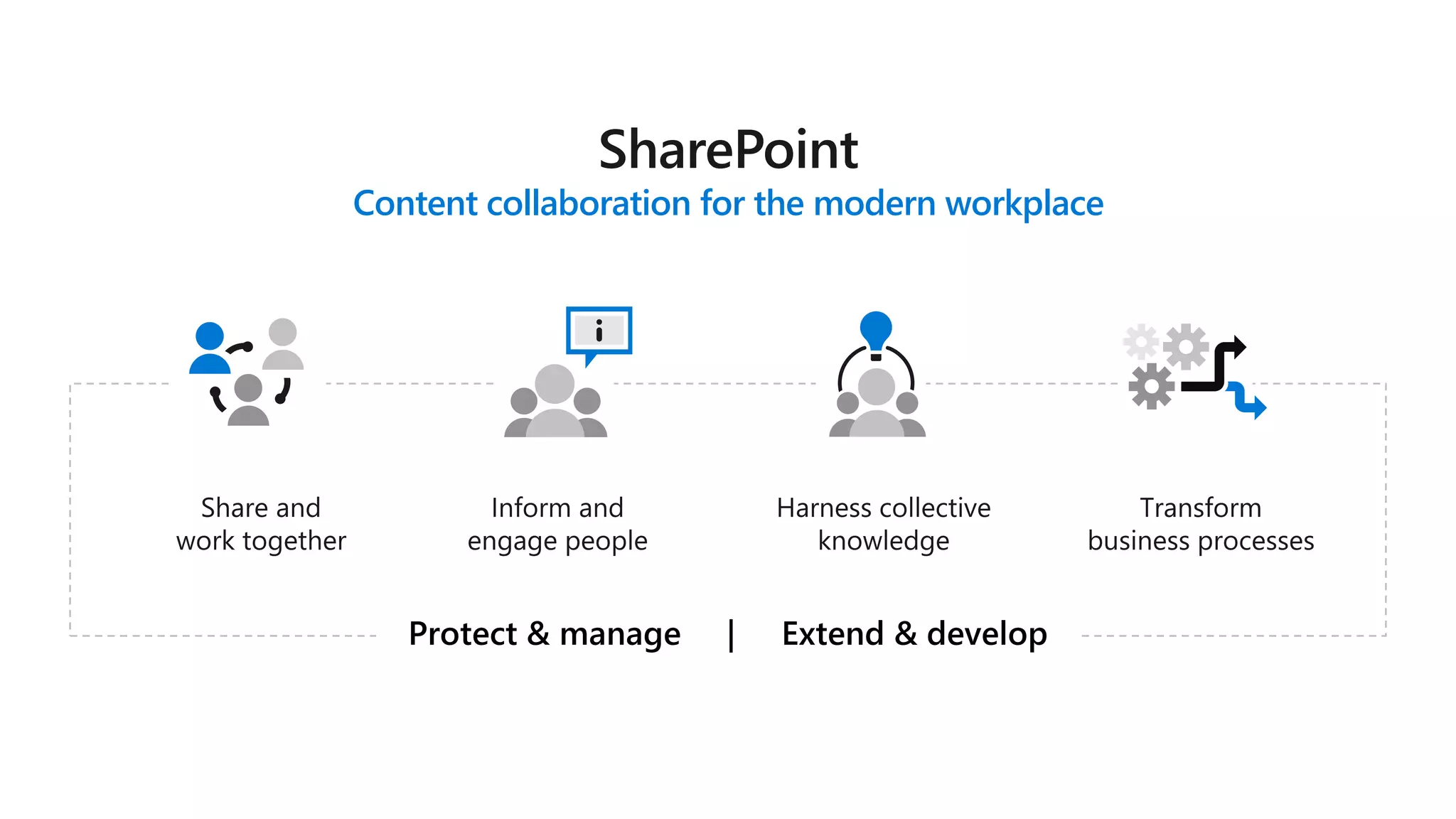
The document outlines Microsoft's solutions for a modern digital workplace, emphasizing tools for content collaboration, compliance management, and data protection using Microsoft 365. It describes features like SharePoint hub sites, sensitive data governance, and advanced security measures to enhance collaboration and protect personal data. Key compliance aspects and policies related to GDPR and data subject requests are also highlighted to ensure organizations meet regulatory requirements.