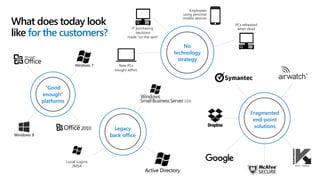
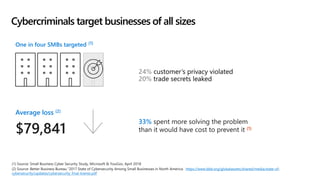
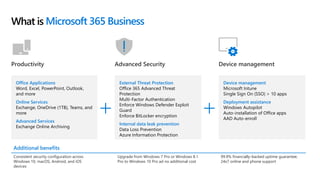
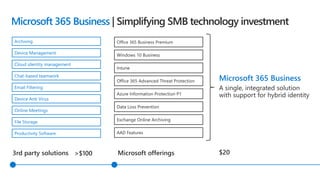
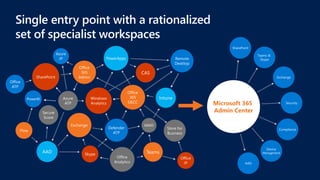
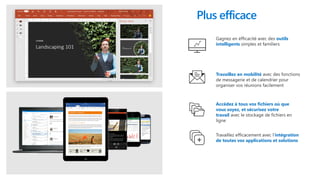
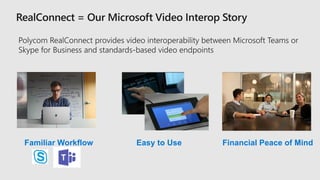
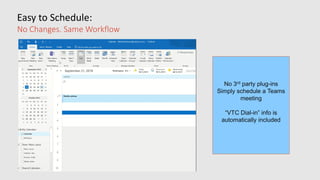
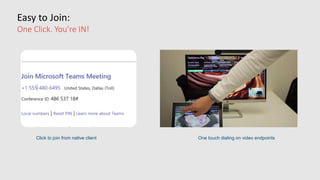
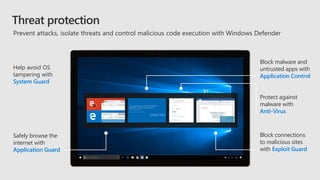
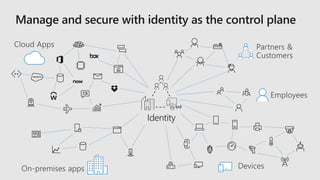
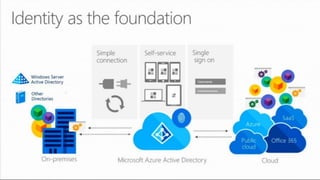
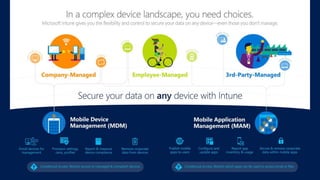
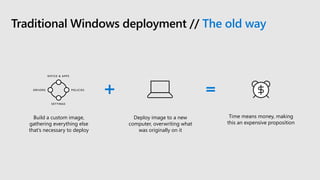
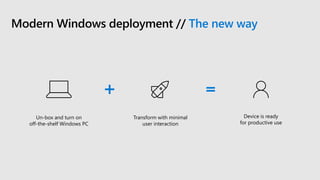
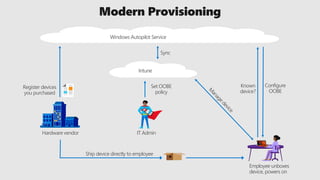
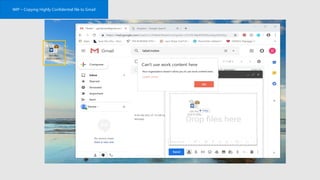
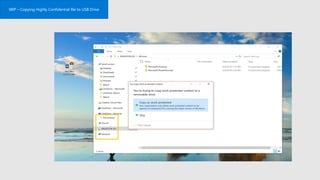
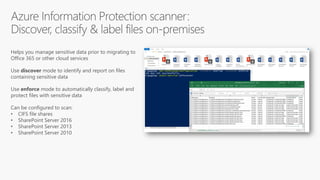
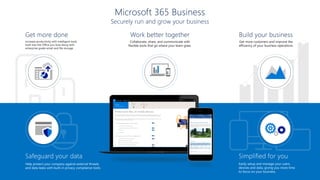
This document profiles Siddick ELAHEEBOCUS, the director of SPILOG Partner Consulting Services (SPCS). It provides details on his background, areas of expertise including Microsoft technologies, and the territories he serves. It also lists some of the organizations and professional networks he is involved with. The document highlights some of the key challenges small and medium businesses face with technology today such as outdated systems, lack of mobility, security issues, and cyber threats. It promotes Microsoft 365 as an integrated solution to address these challenges through features for productivity, collaboration, and security.