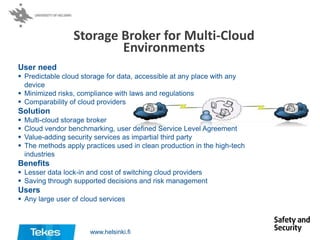
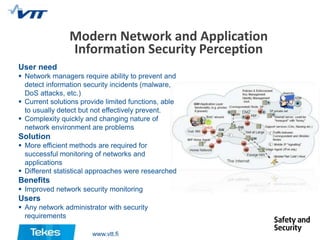
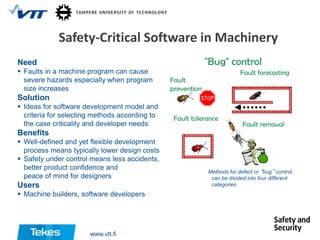
The document describes several cyber security solutions from Tekes Safety and Security Programme. The first solution discussed is a total IT asset data erasure solution that can completely erase digital data from all IT assets such that the data cannot be recovered with any existing technology. The solution has the most comprehensive certification in the industry. The second solution discussed is a flexible and secure authentication solution that aims to improve authentication for internet services. The third solution is a testing-as-a-service called Fuzz-o-Matic that can test applications for vulnerabilities and ensure their safety.