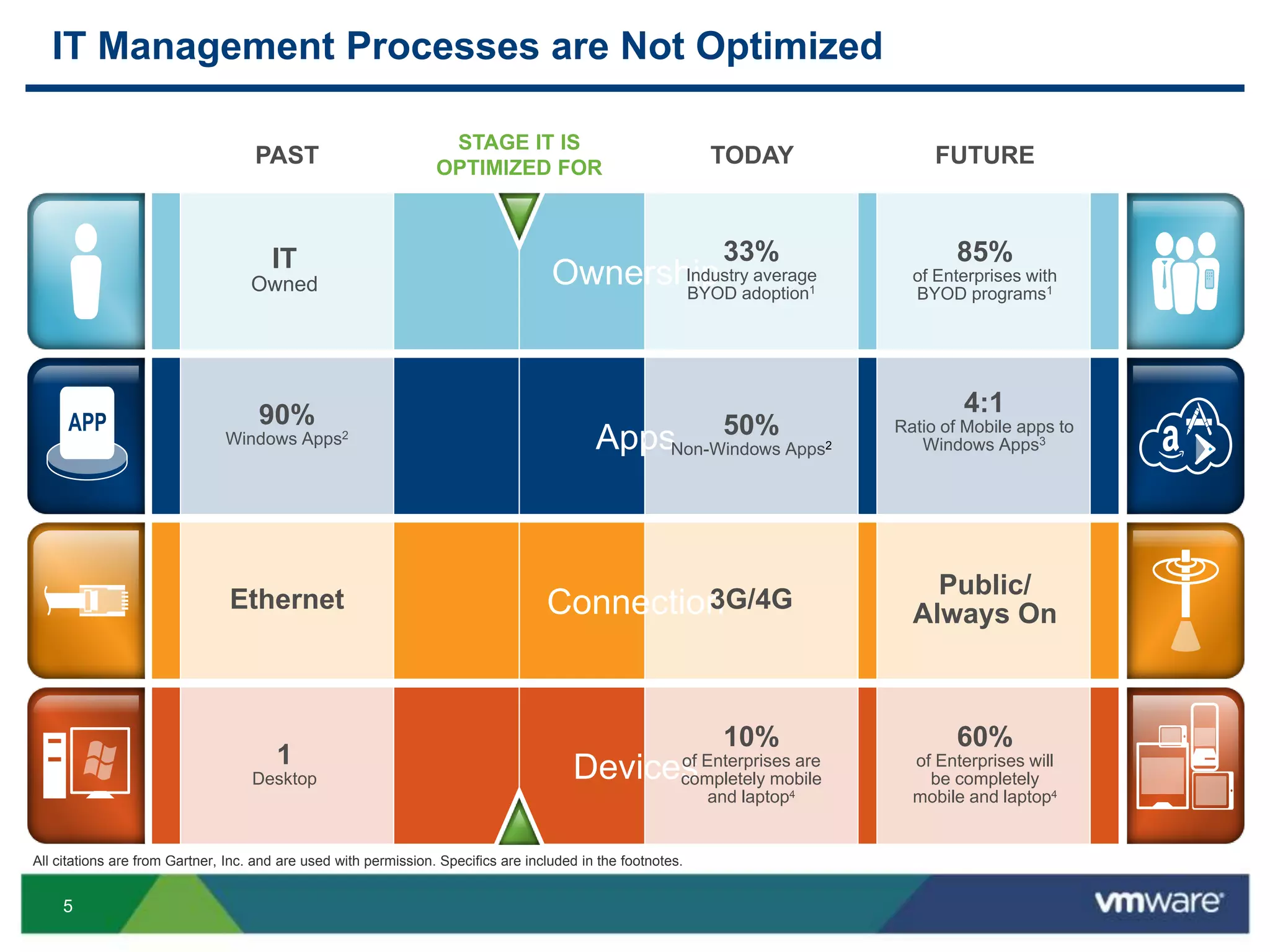
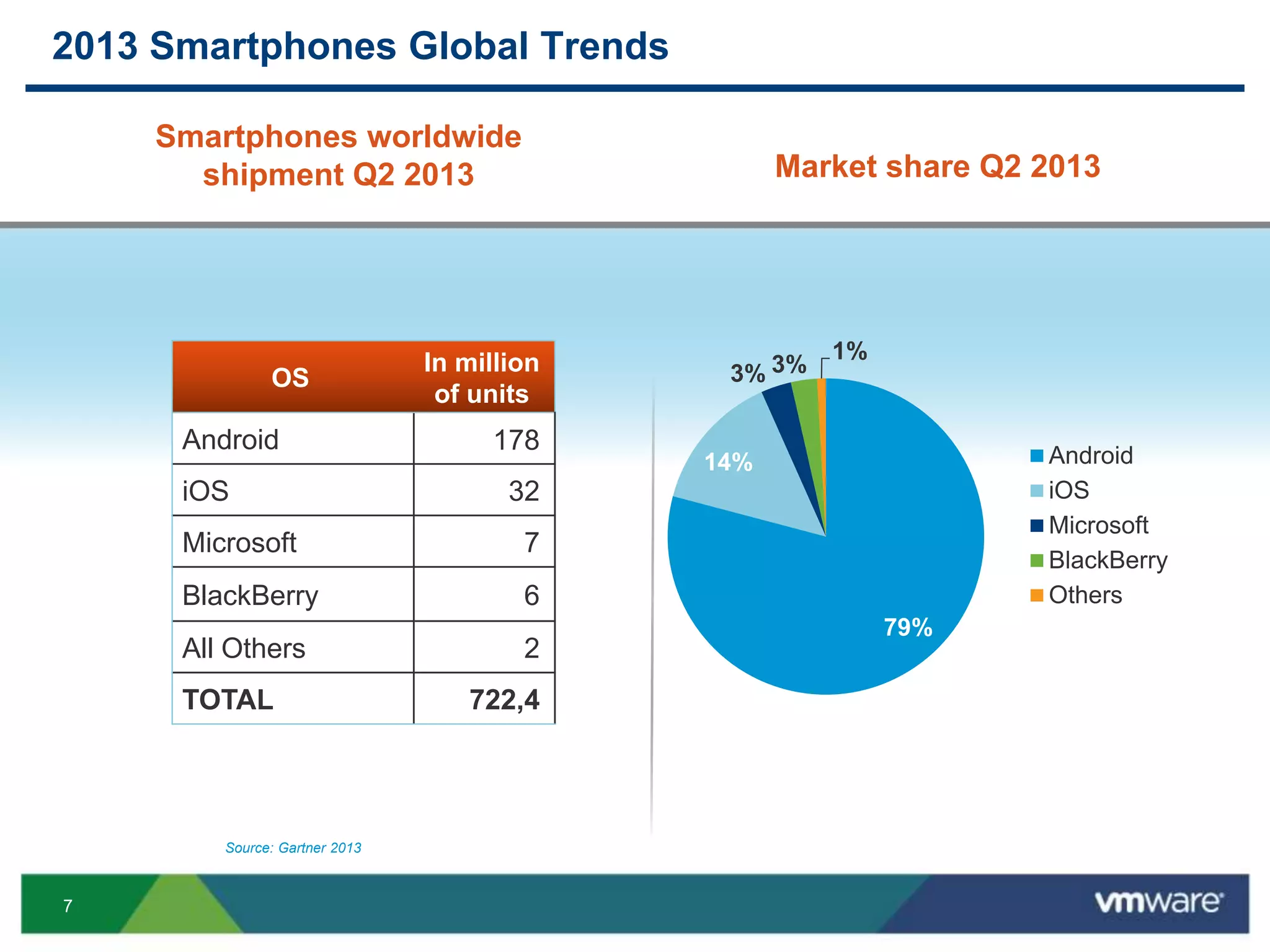
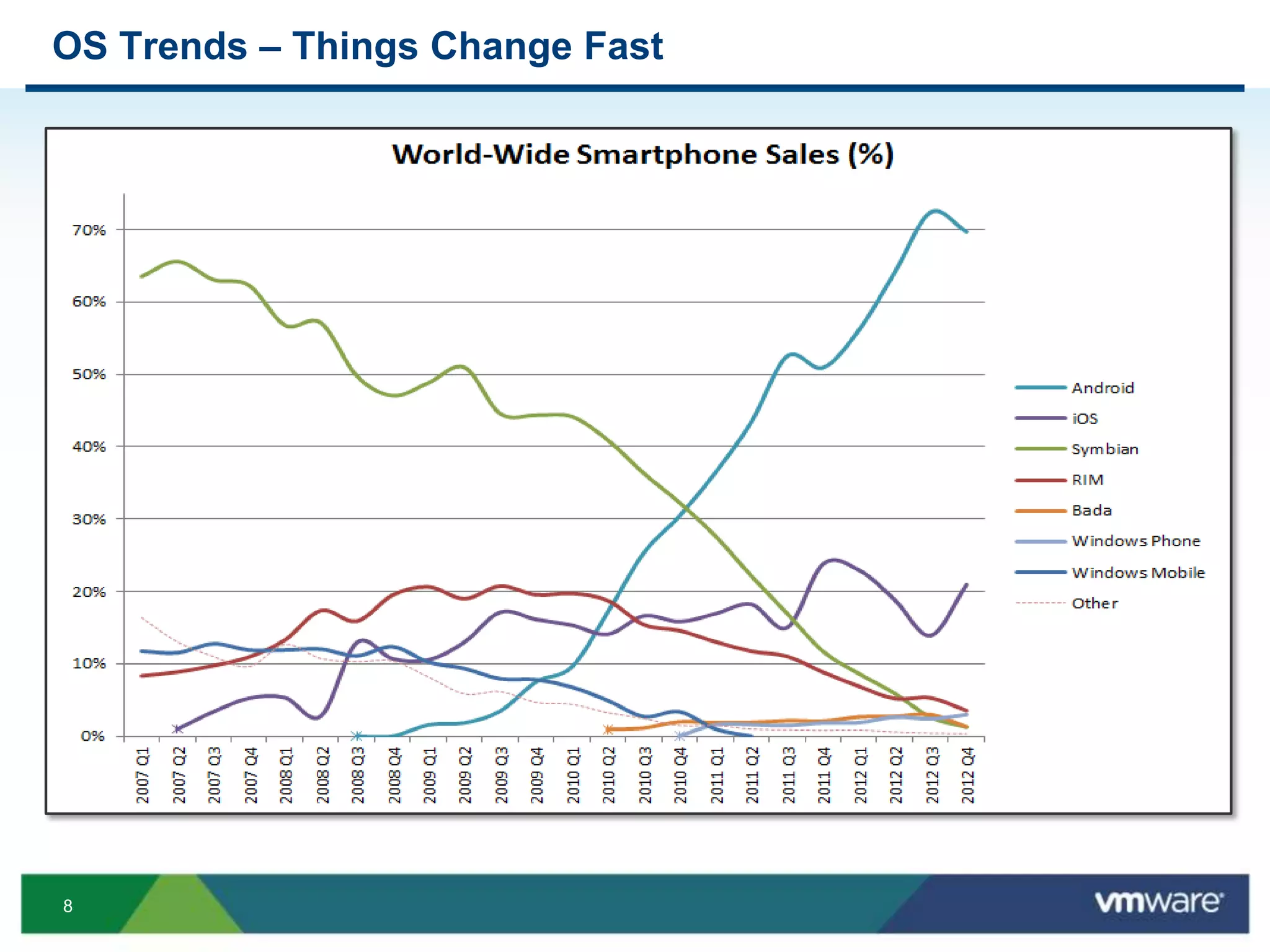
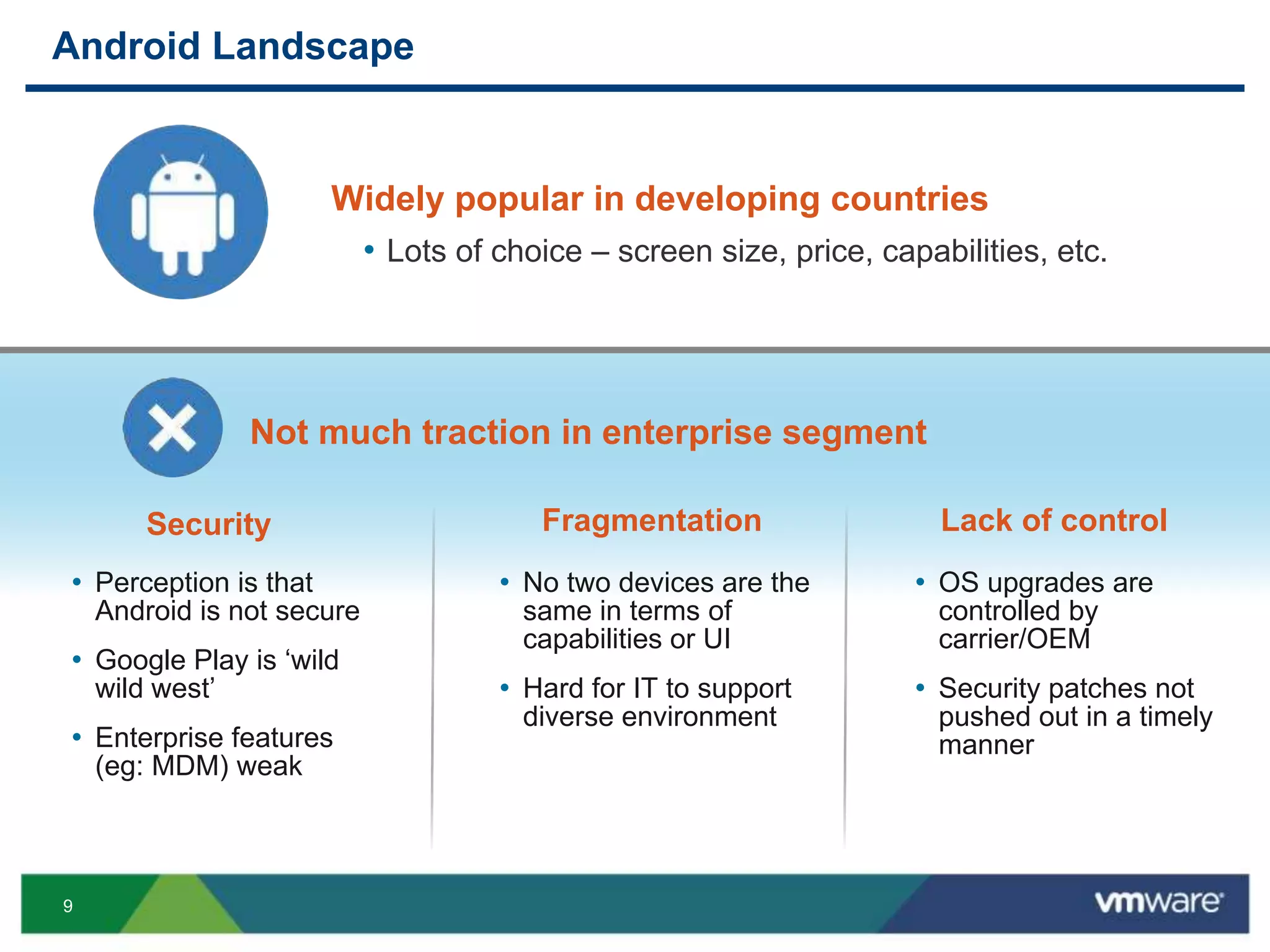
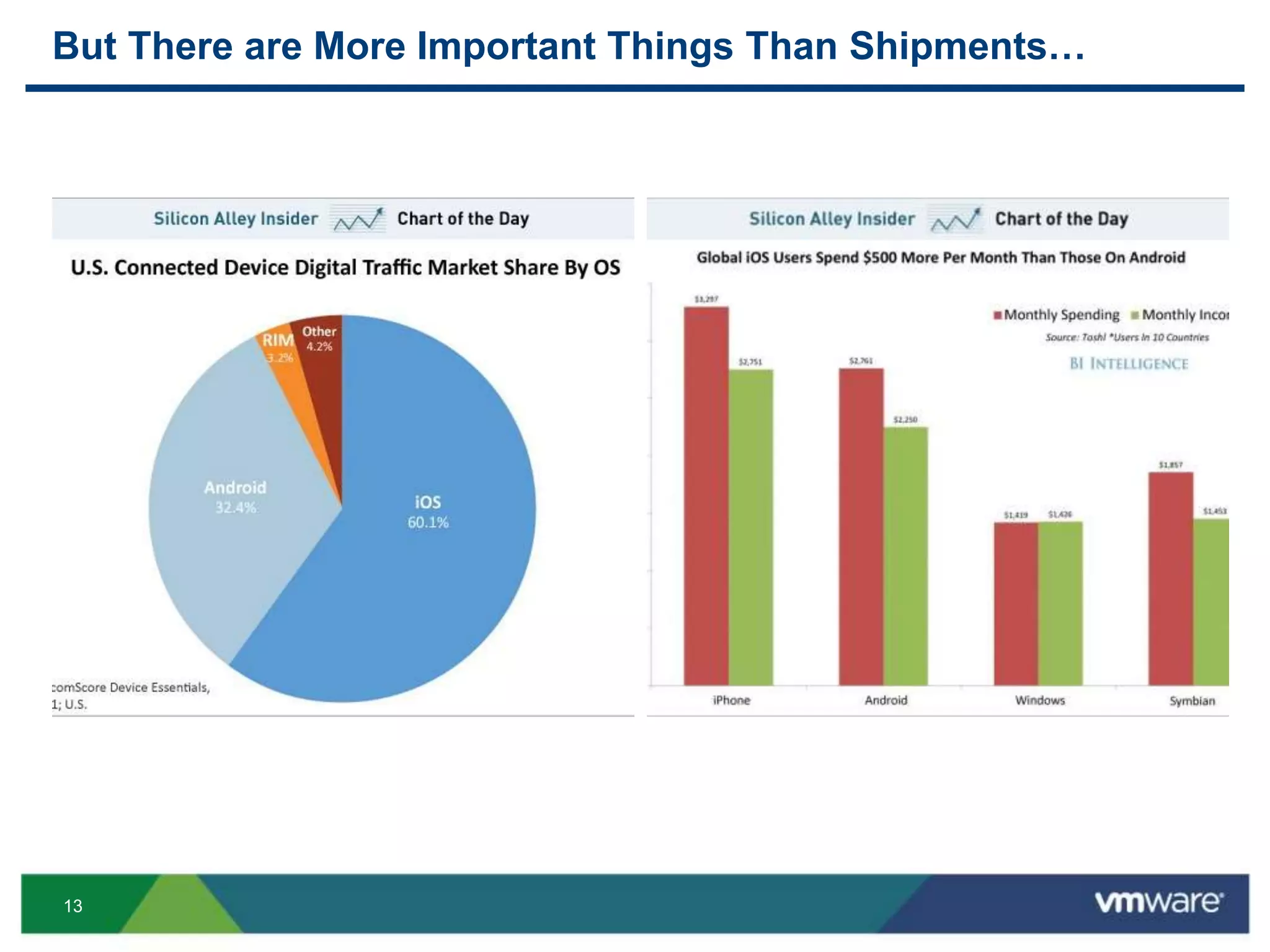
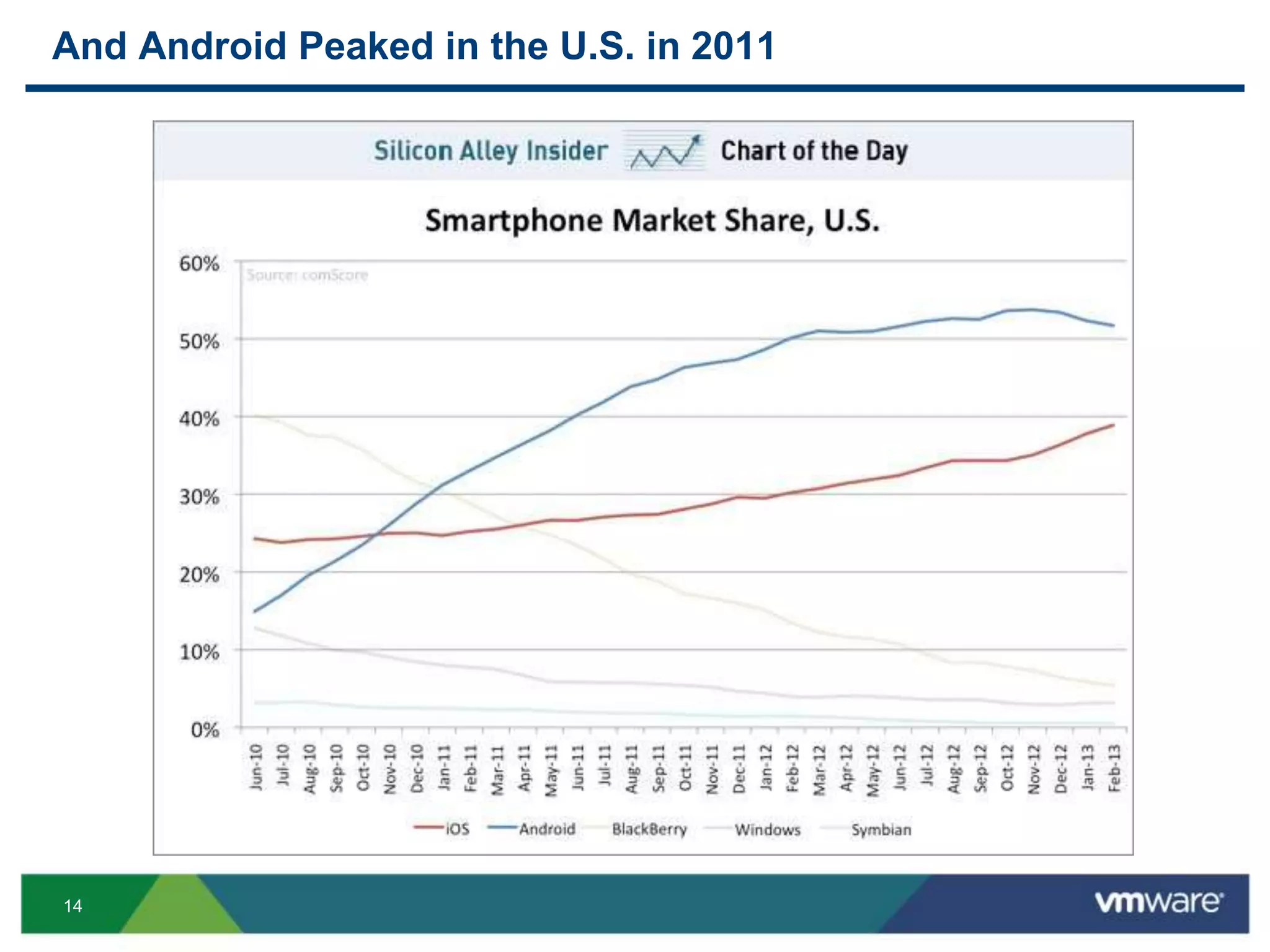
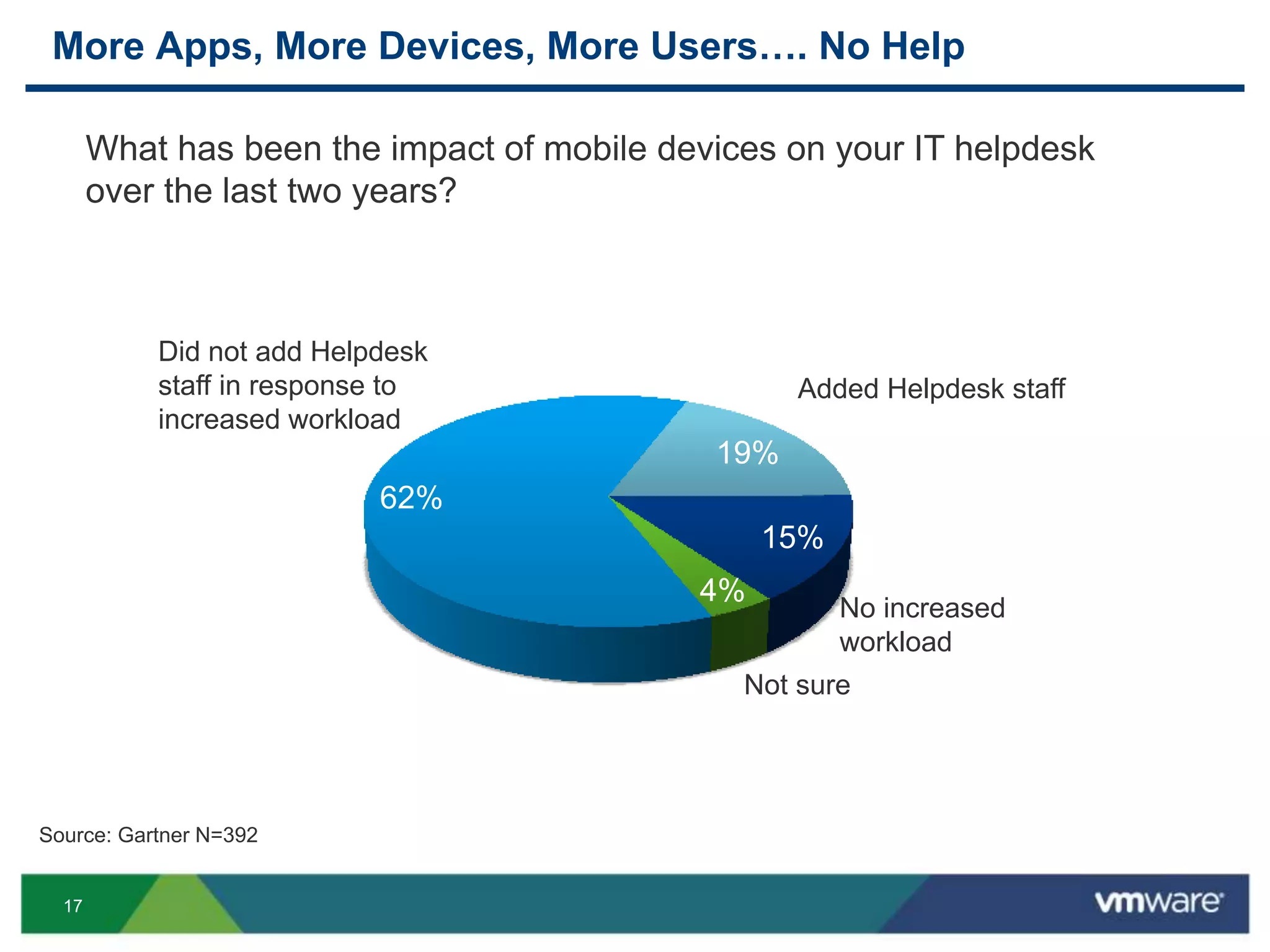
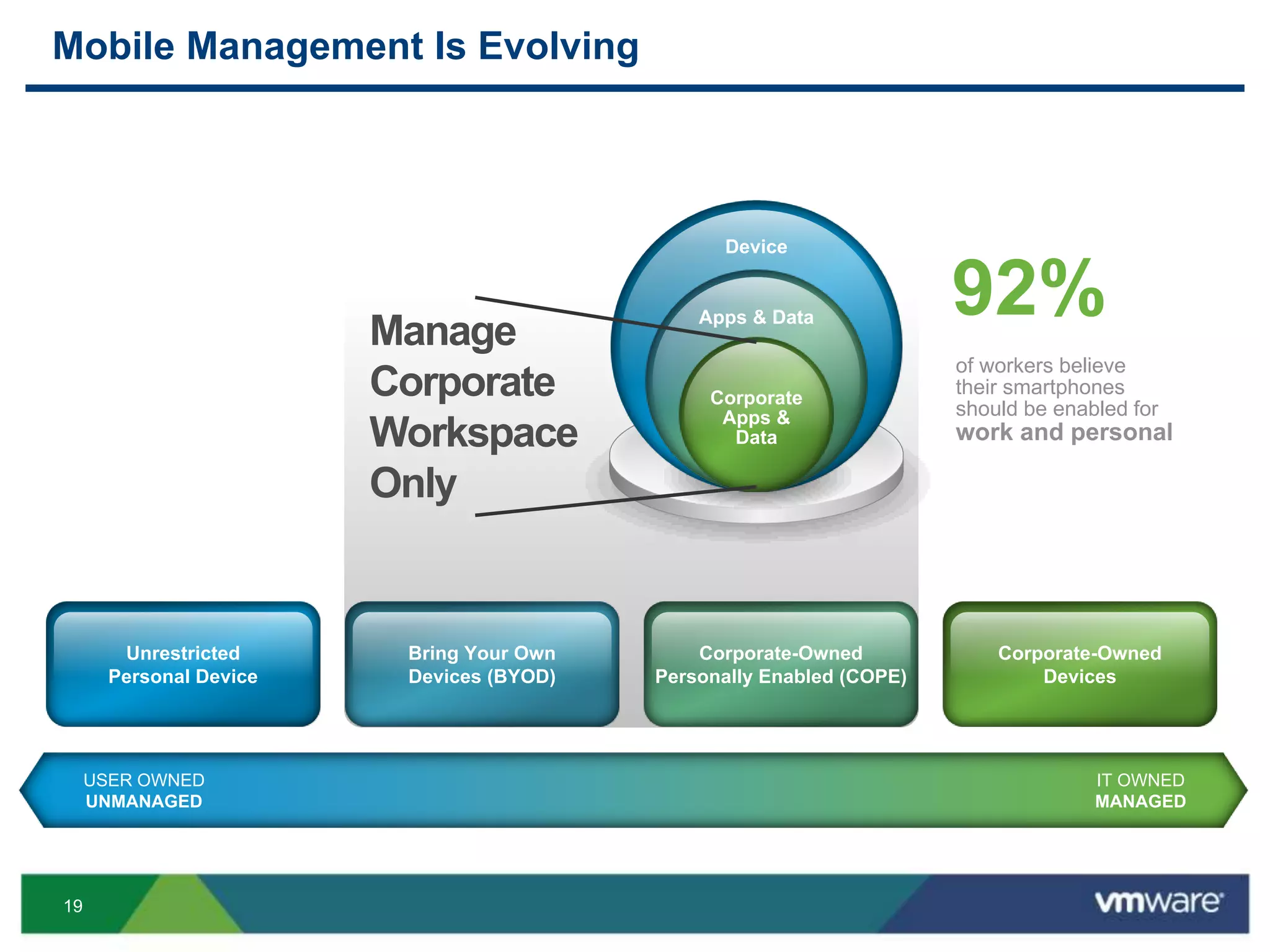
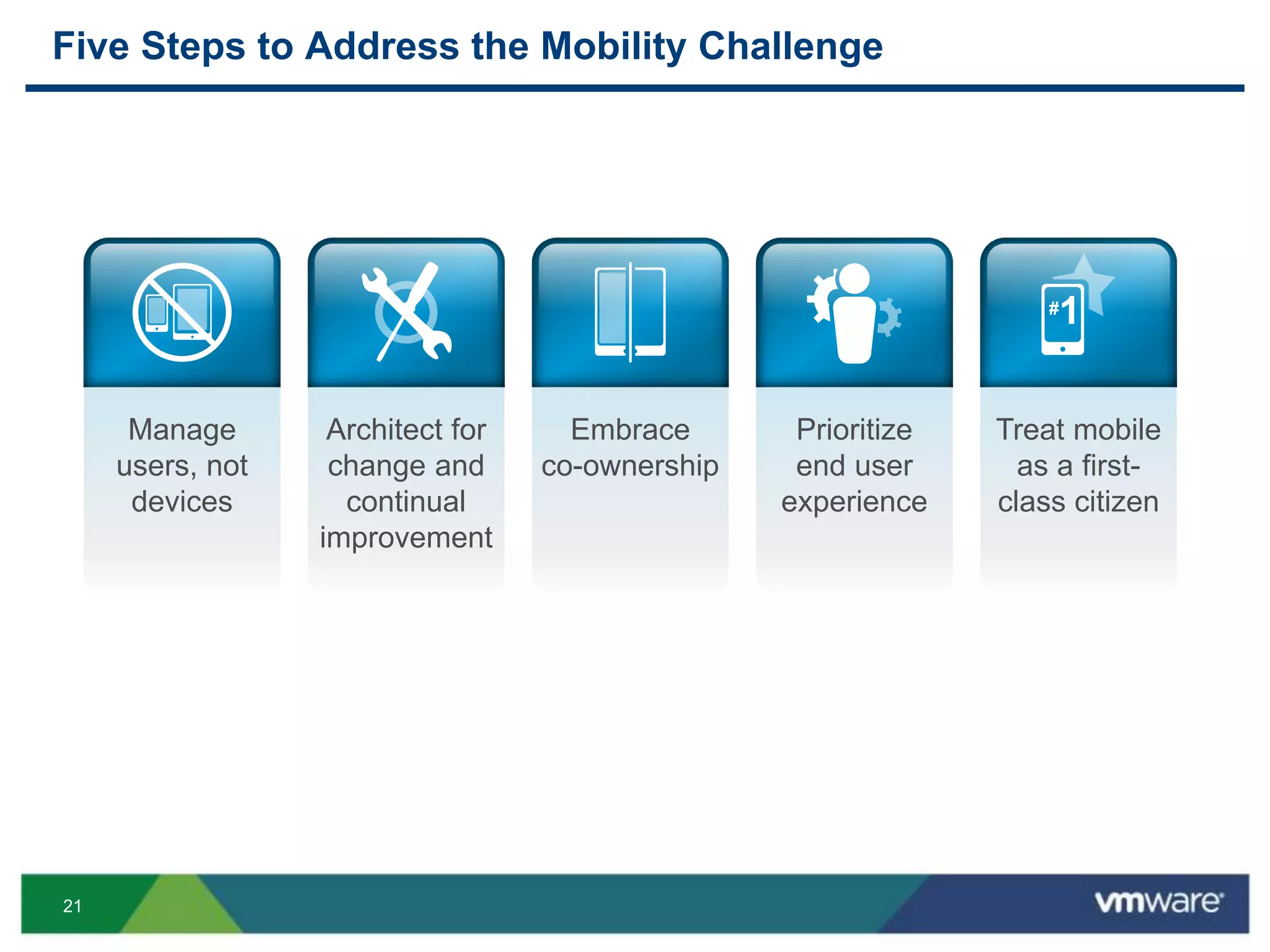
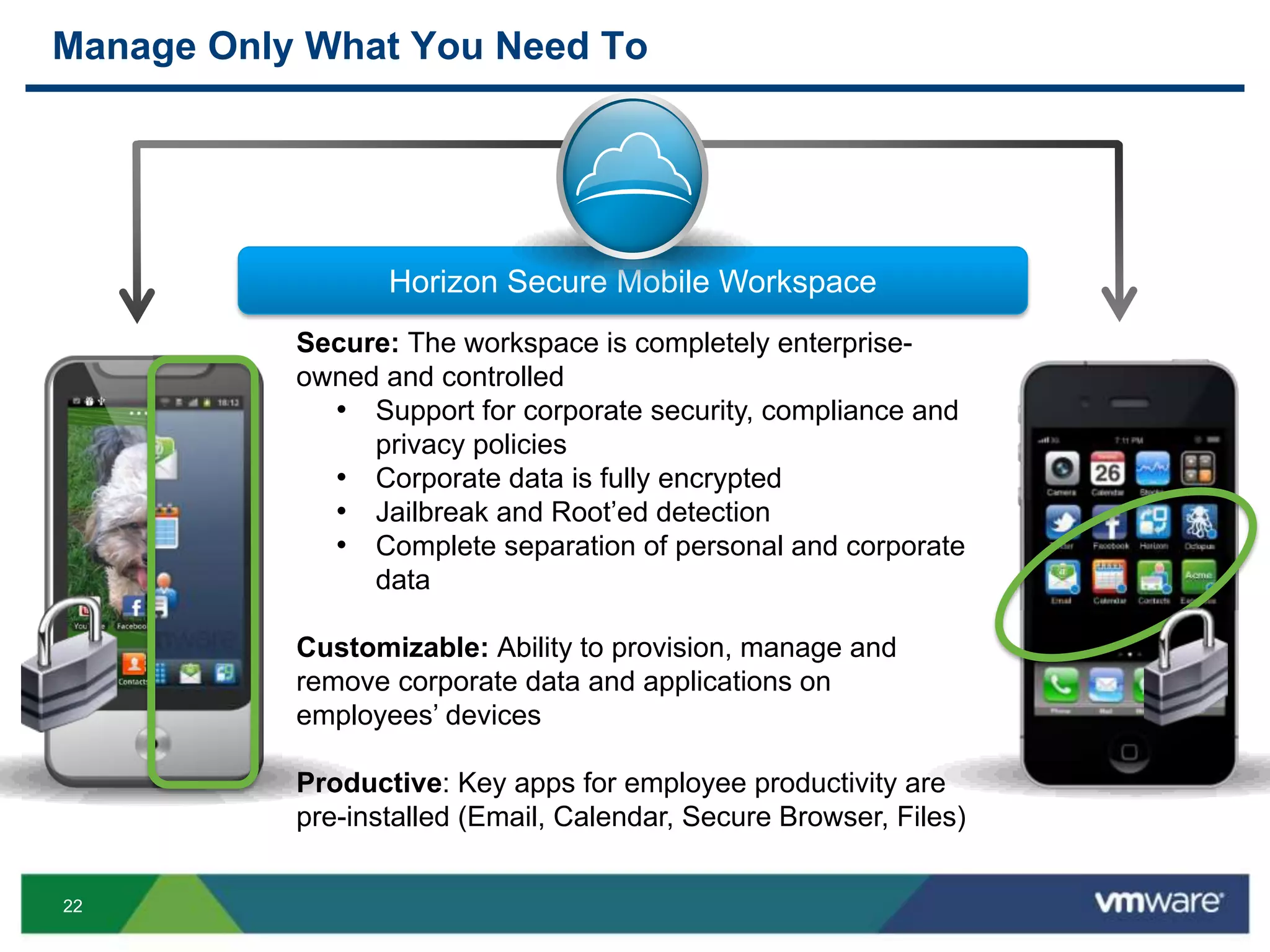
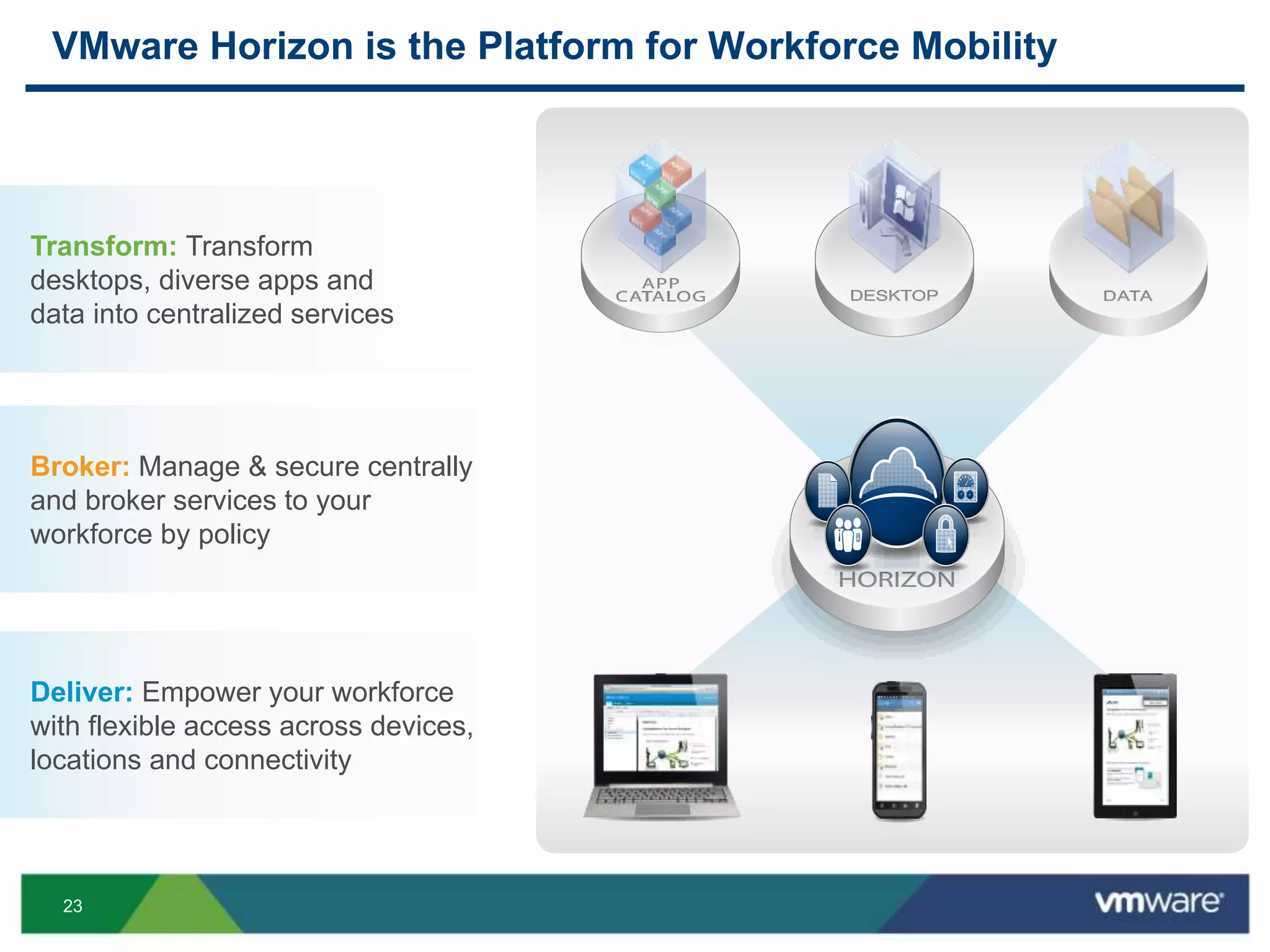
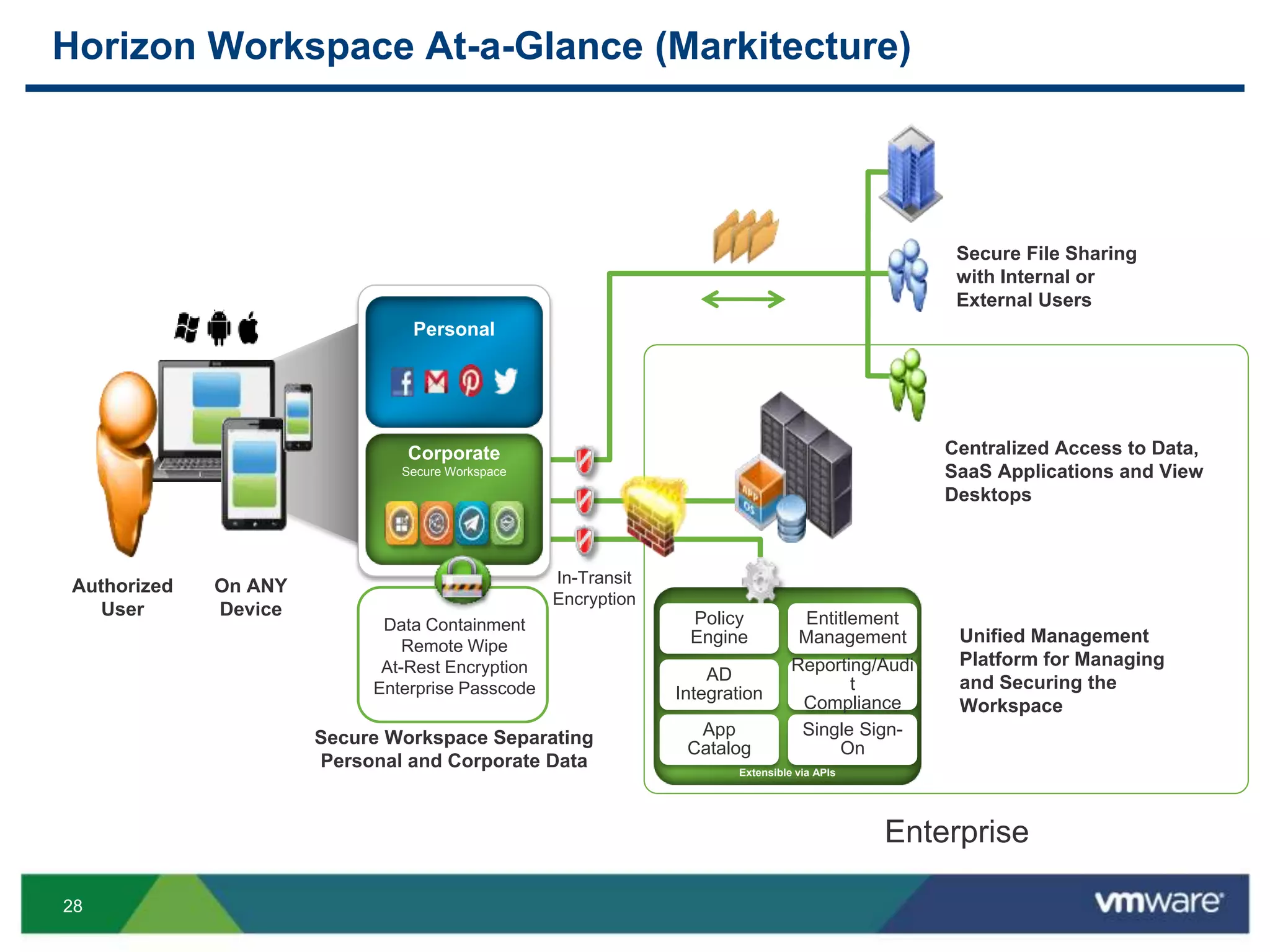
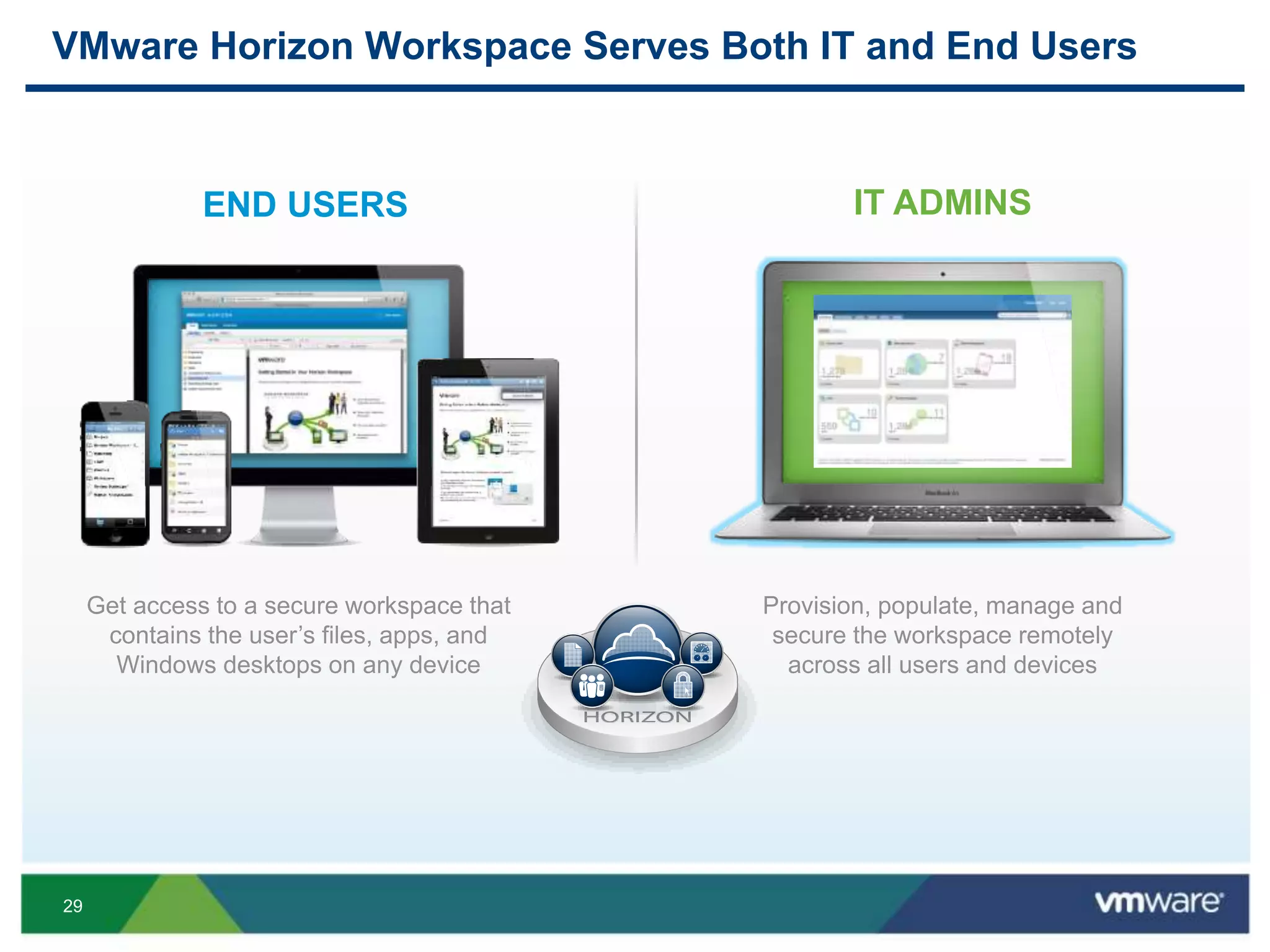
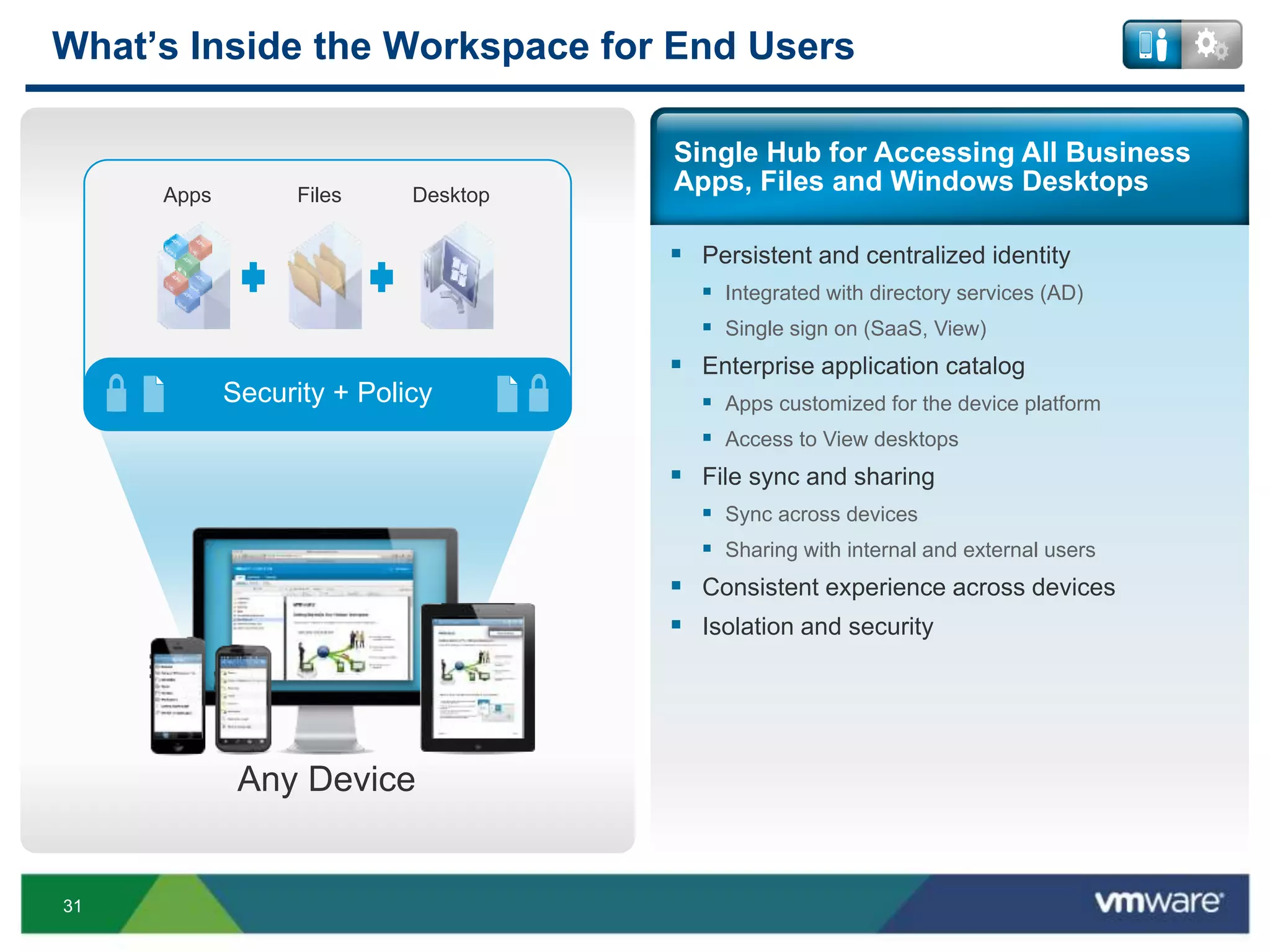
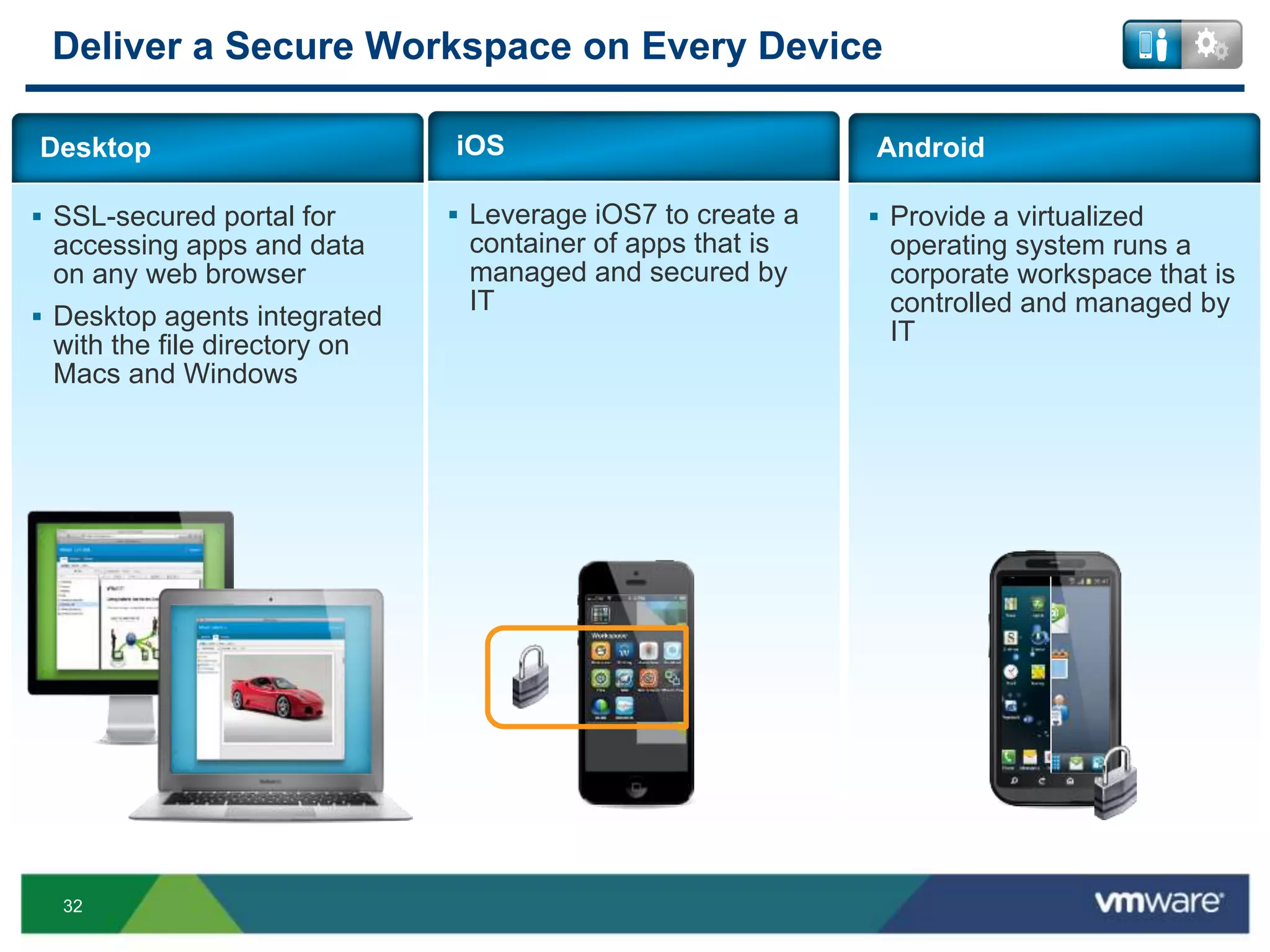
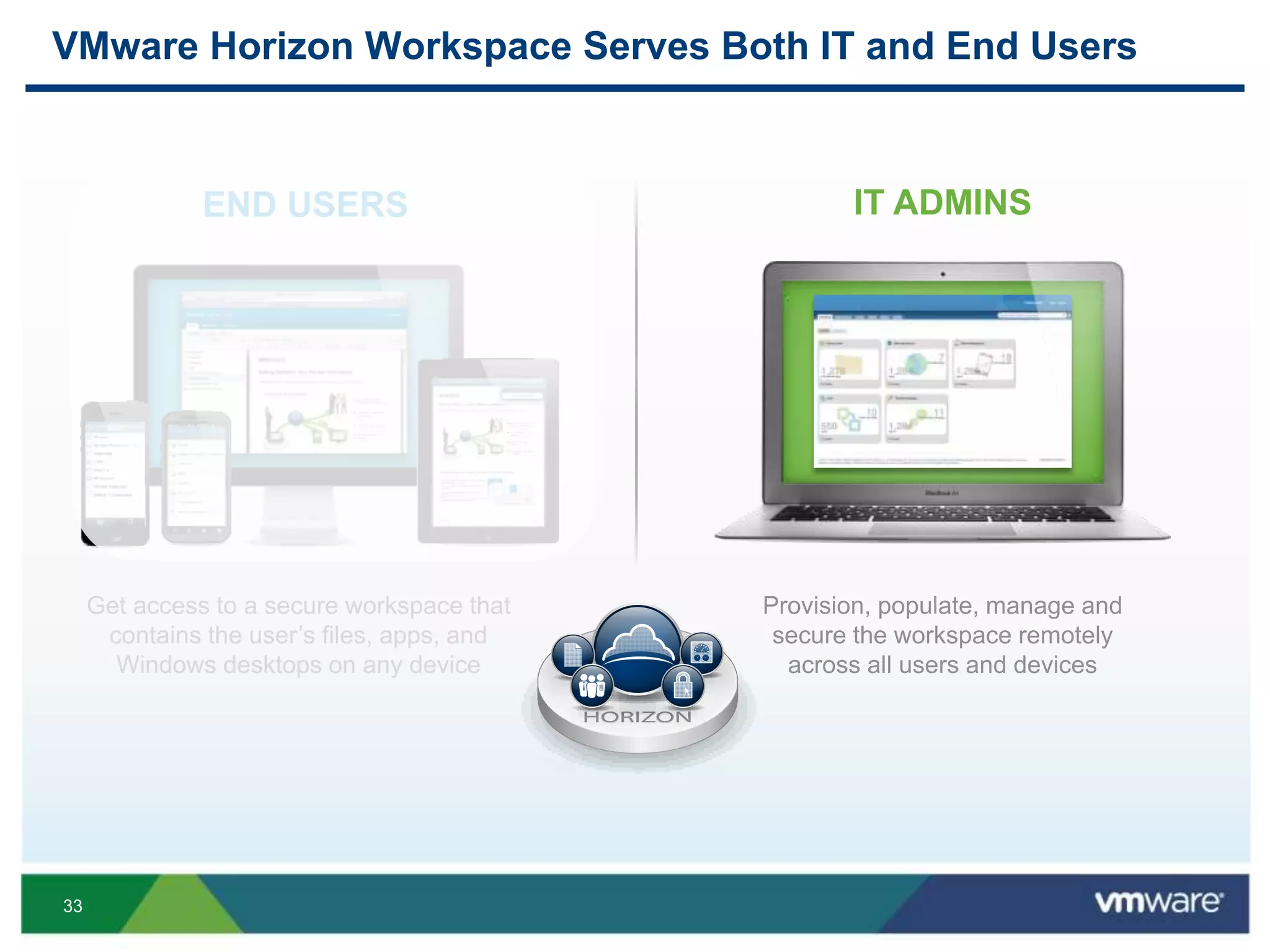
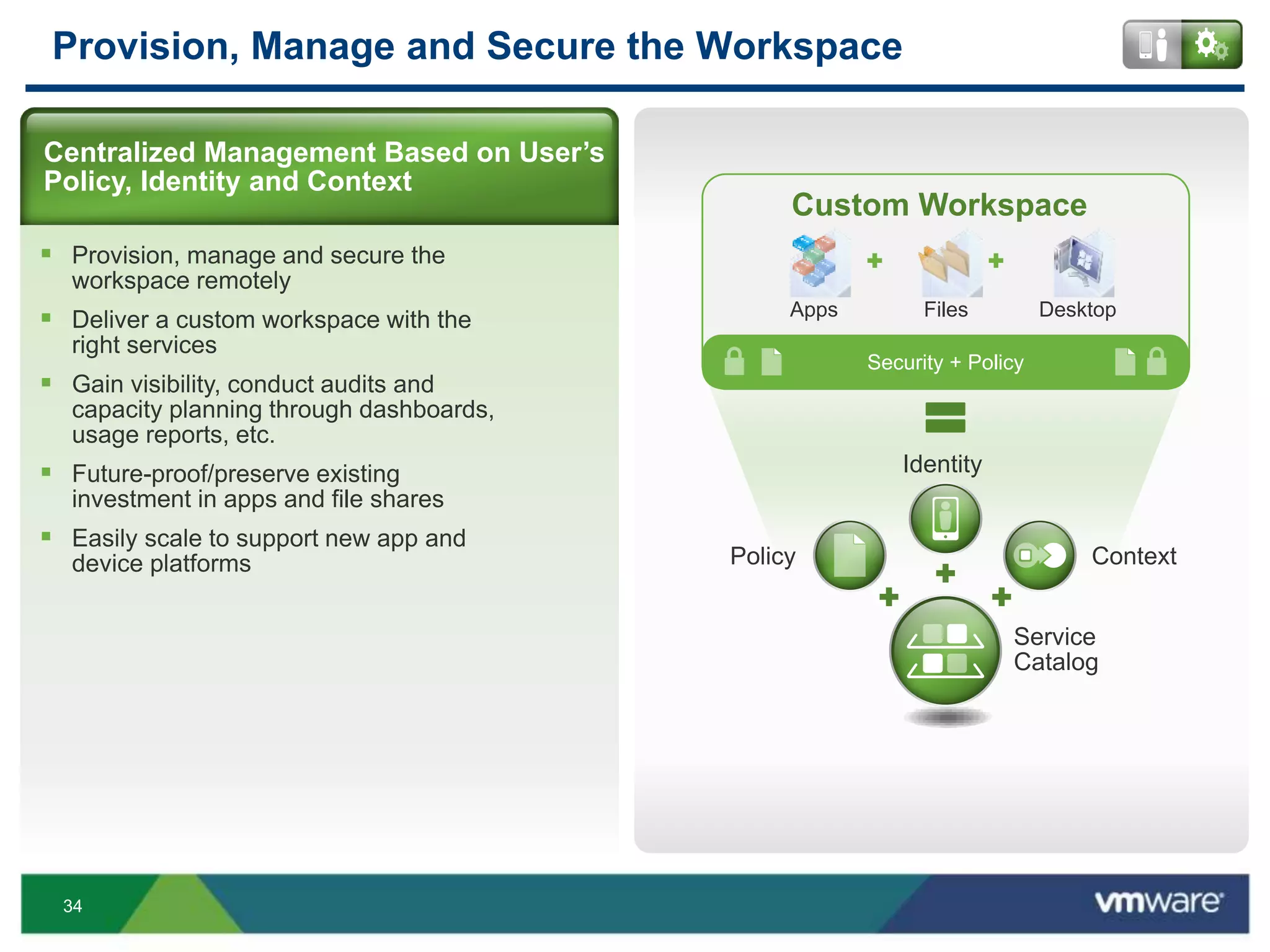
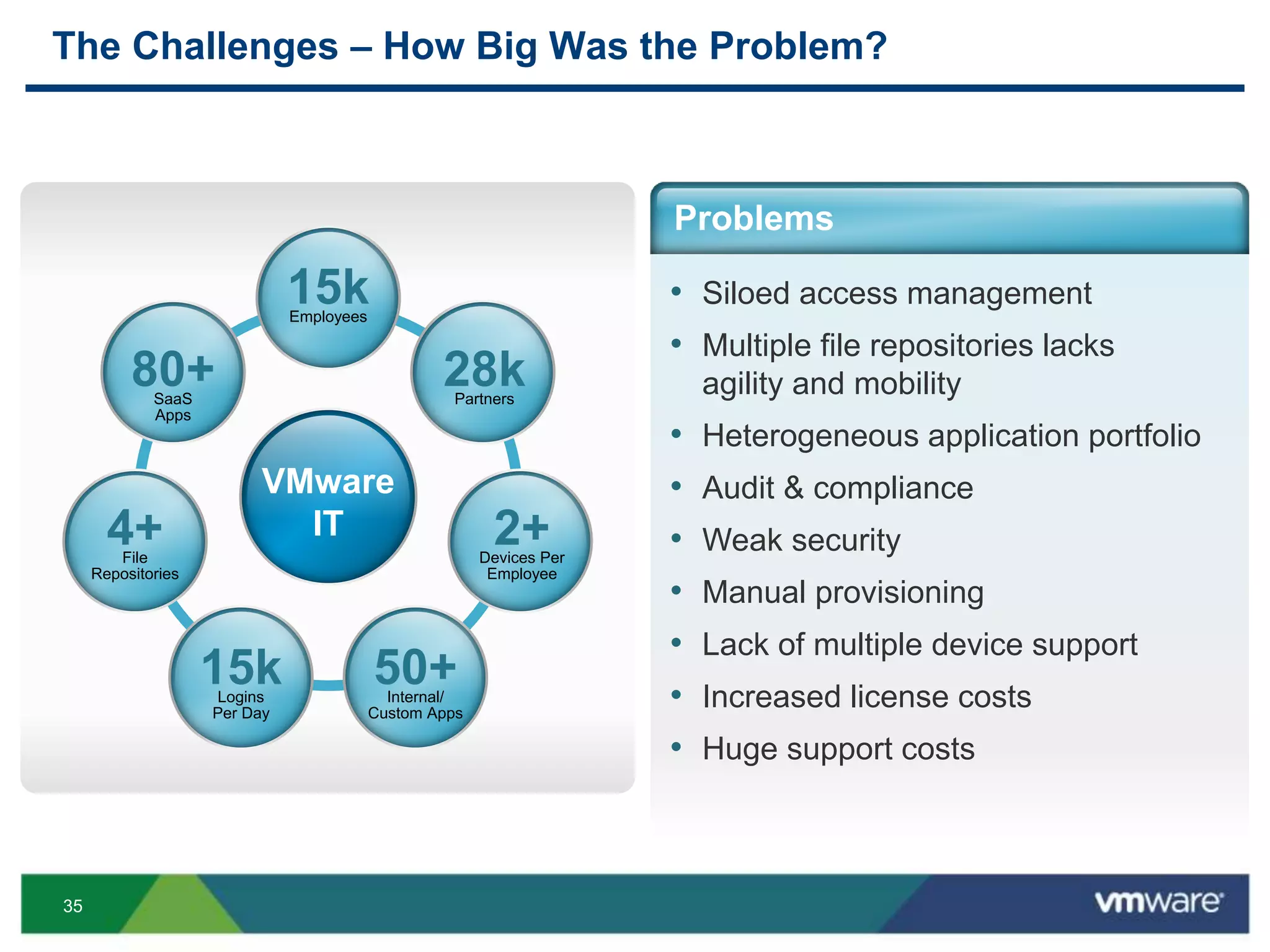
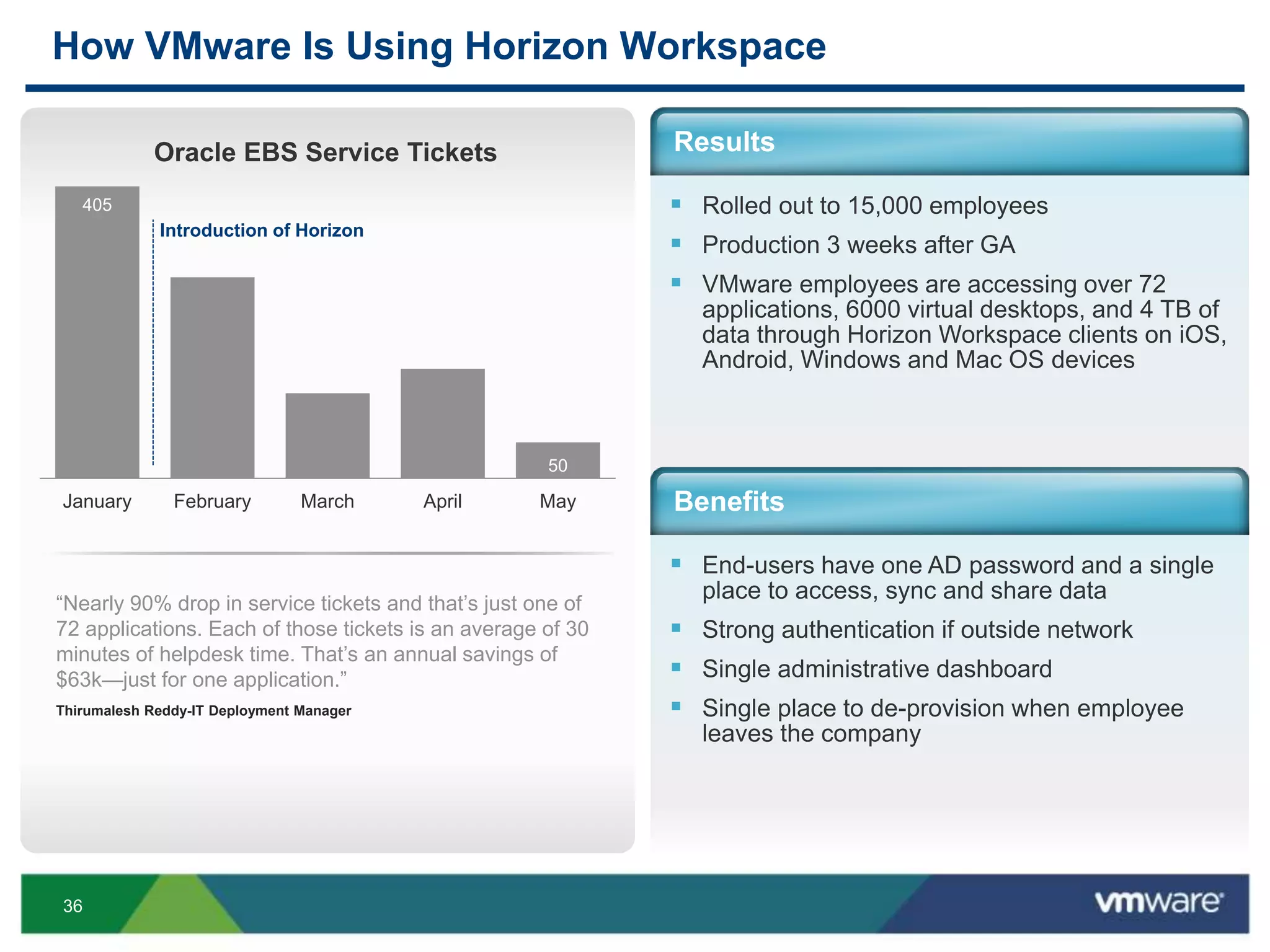
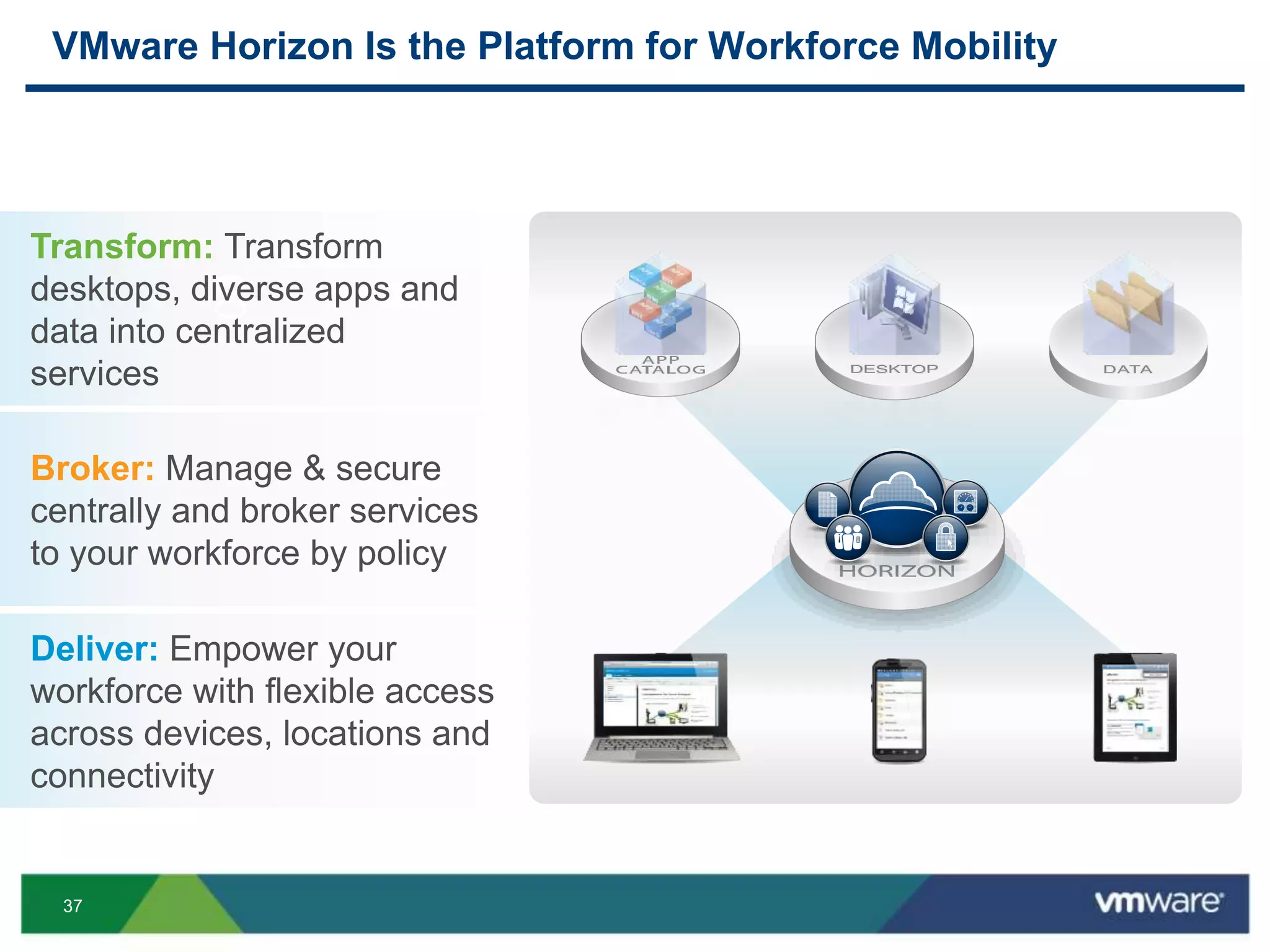
The document discusses the challenges and transformations in IT management due to the rise of mobile devices and BYOD (Bring Your Own Device) policies. It presents VMware's Horizon Workspace as a solution to enhance productivity through centralized management of apps and data, while addressing security and compliance concerns. The emphasis is on adapting IT strategies to meet the evolving needs of users in a multi-device, multi-platform environment.