This document discusses sovereignty and governance in cyberspace, focusing on three key sites: the NSA and encryption policy, WIPO and anti-circumvention measures, and ICANN and internet identifier management. For each site, it analyzes the rhetoric used, realpolitik motivations, governance processes and challenges, and lack of legitimacy and effectiveness due to limited stakeholder participation and global technical constraints. Overall it argues that regulating technology and technologizing regulation in these areas has faced major challenges due to differing stakeholder positions and the difficulty of controlling cryptography, code, and network protocols on an open global internet.






![Encryption realpolitik
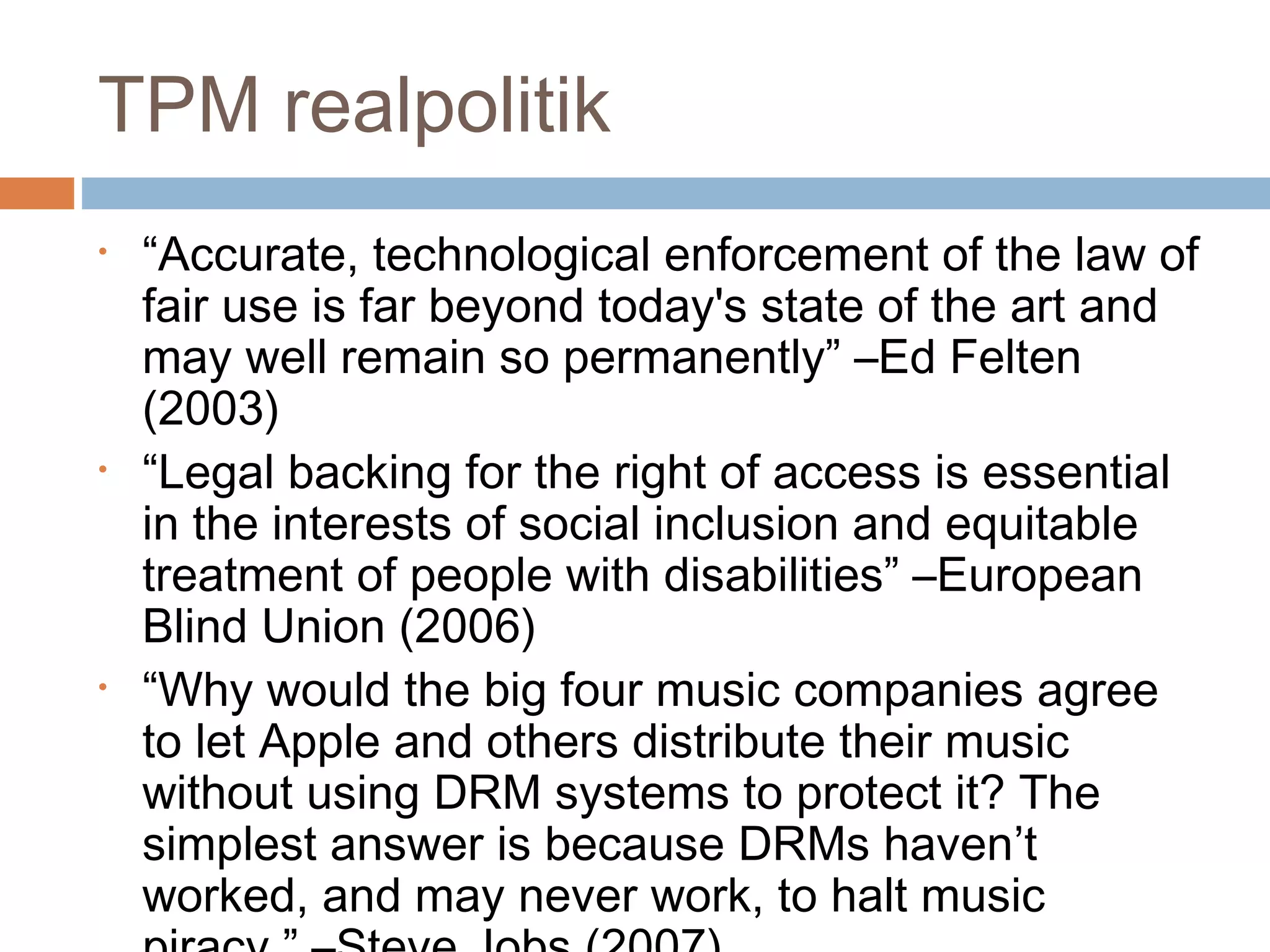
• “Law enforcement is a protective shield for all the
other governmental activities. You should use the
right word – we’re talking about foreign
intelligence… The Law enforcement is a smoke
screen” –David Herson, SOGIS (1996)
• “We steal [economic] secrets with espionage, with
communications, with reconnaissance satellites” –
James Woolsey, CIA (2002)
• "Encryption is no more prevalent amongst
terrorists than the general population. Al-Qaeda
has used encryption, but less than commercial
enterprises.” –Juliette Bird, NATO (2006)](https://image.slidesharecdn.com/sovereigntyincyberspaceianbrown-121009234332-phpapp02/75/Sovereignty-in-Cyberspace-7-2048.jpg)



![© rhetoric
• “the VCR is to the American film
producer and the American
public as the Boston strangler is
to the woman home alone.” –
Jack Valenti (1982)
• “The answer to the machine is in
the machine” –Charles Clark
(1996)
• “If we can find some way to [stop
filesharing] without destroying
their machines, we'd be
interested in hearing about that.
If that's the only way, then I'm all
for destroying their machines.” –
Senator Orrin Hatch (2003)](https://image.slidesharecdn.com/sovereigntyincyberspaceianbrown-121009234332-phpapp02/75/Sovereignty-in-Cyberspace-11-2048.jpg)






![ICANN realpolitik
• Internet governance is “definitely a travelling
roadshow, if not a flying circus”-Markus
Kummer (2004)
• “The ITU version of [the Internet] blurs…
boundaries and takes us a step backwards
into a centrally controlled, centrally managed,
‘more than good enough’network—
administered, of course, by the ITU.” –Ross
Rader (2004)
• "Using 'talking shop' as a negative suggests
communication is a bad thing” –Emily Taylor](https://image.slidesharecdn.com/sovereigntyincyberspaceianbrown-121009234332-phpapp02/75/Sovereignty-in-Cyberspace-19-2048.jpg)



