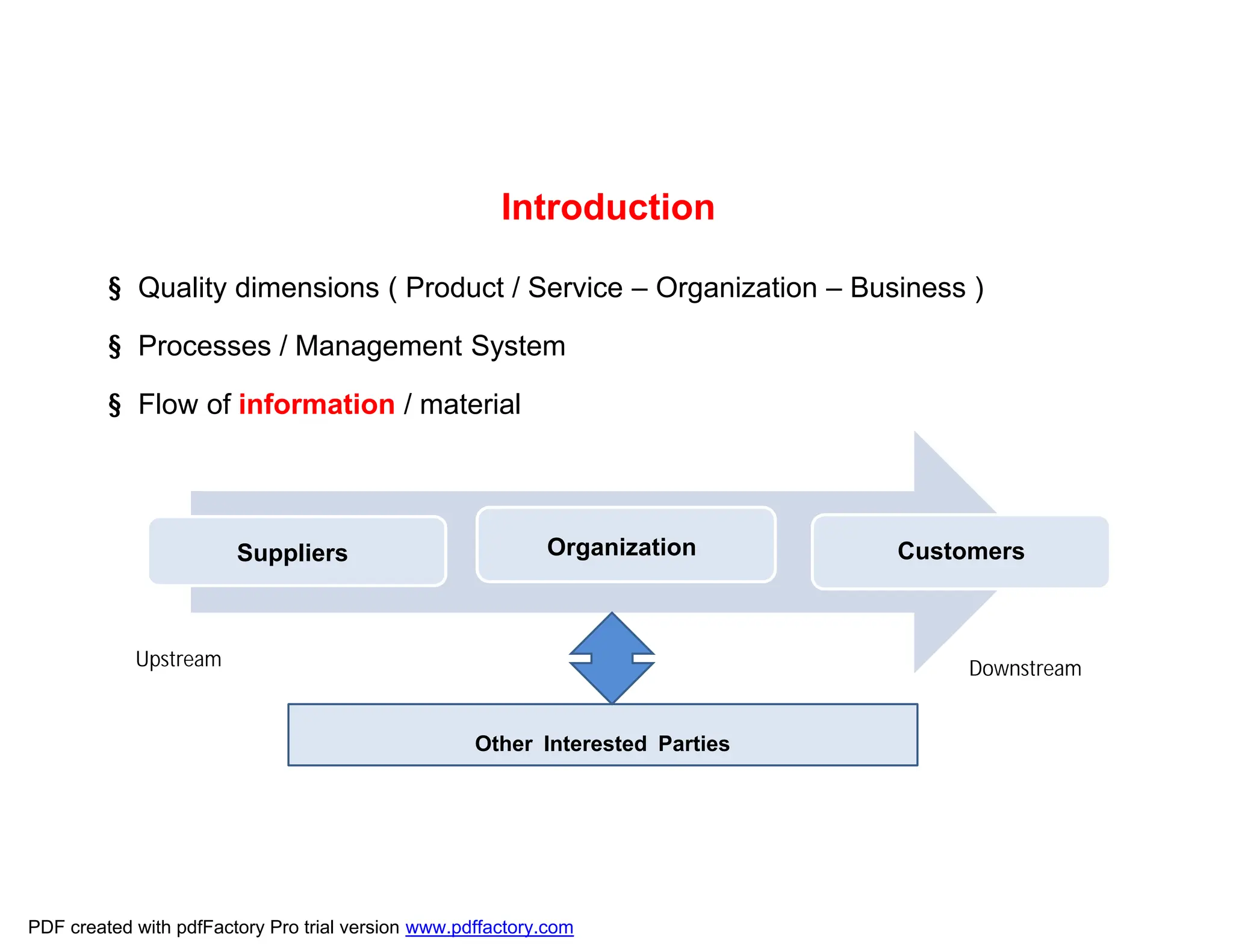
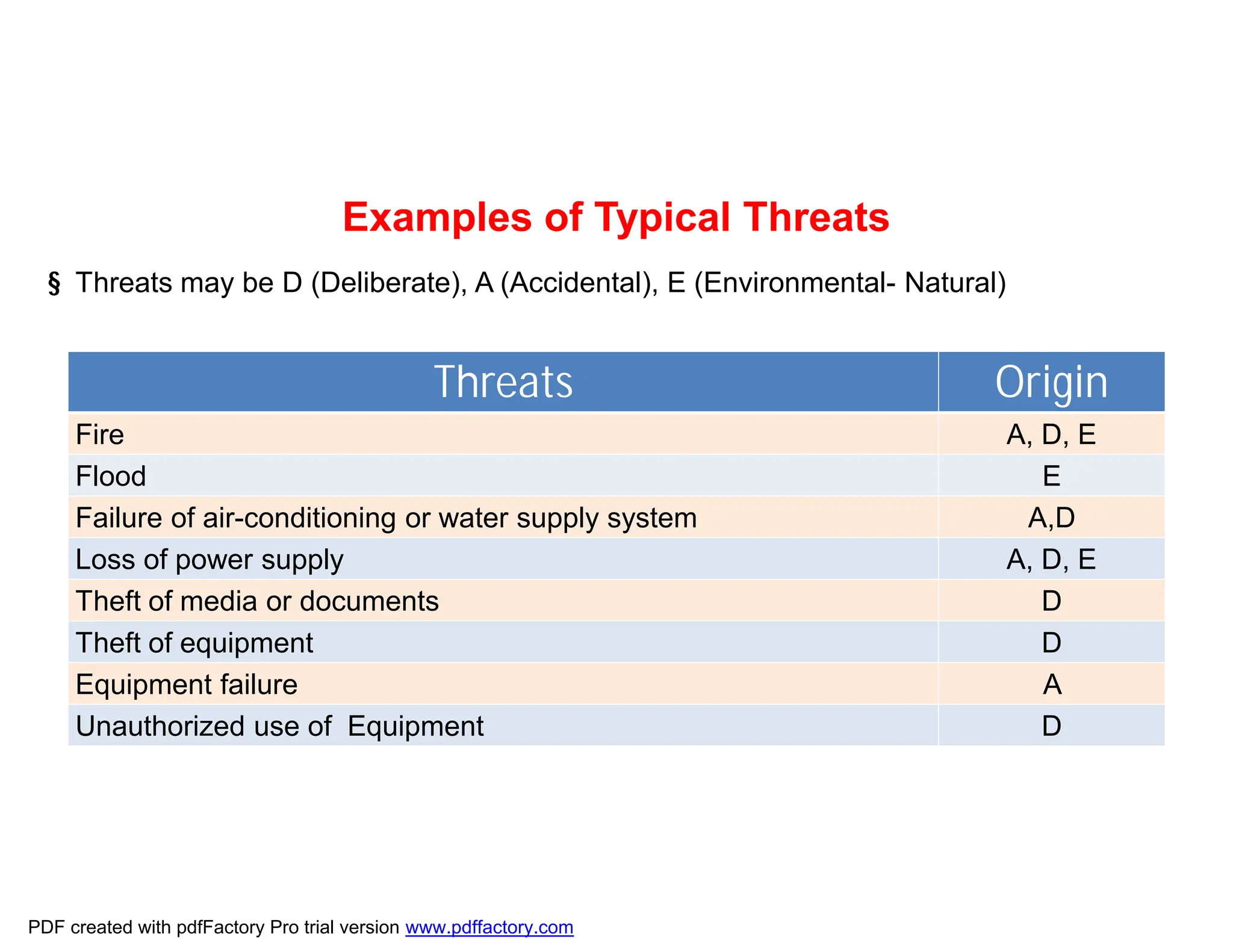
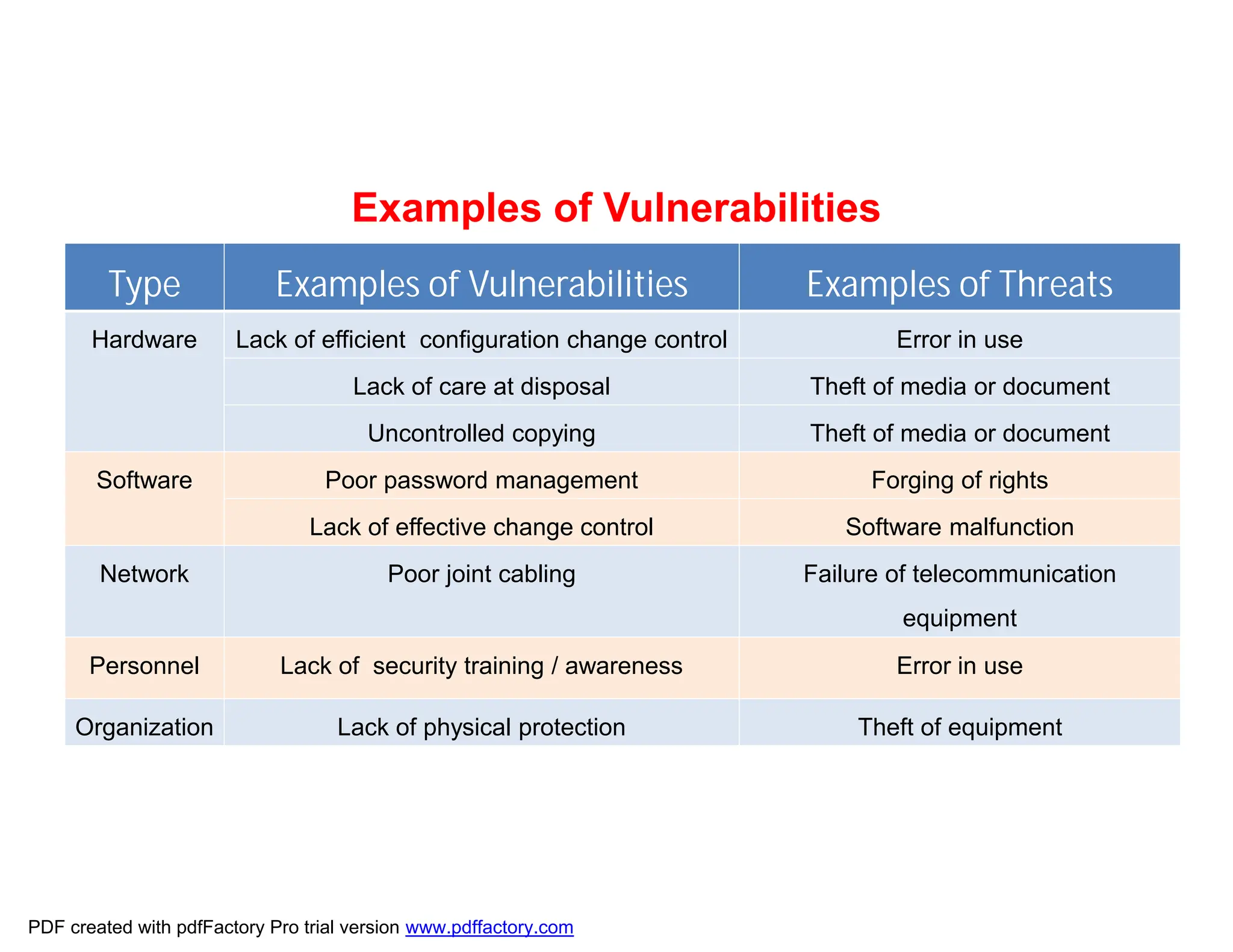
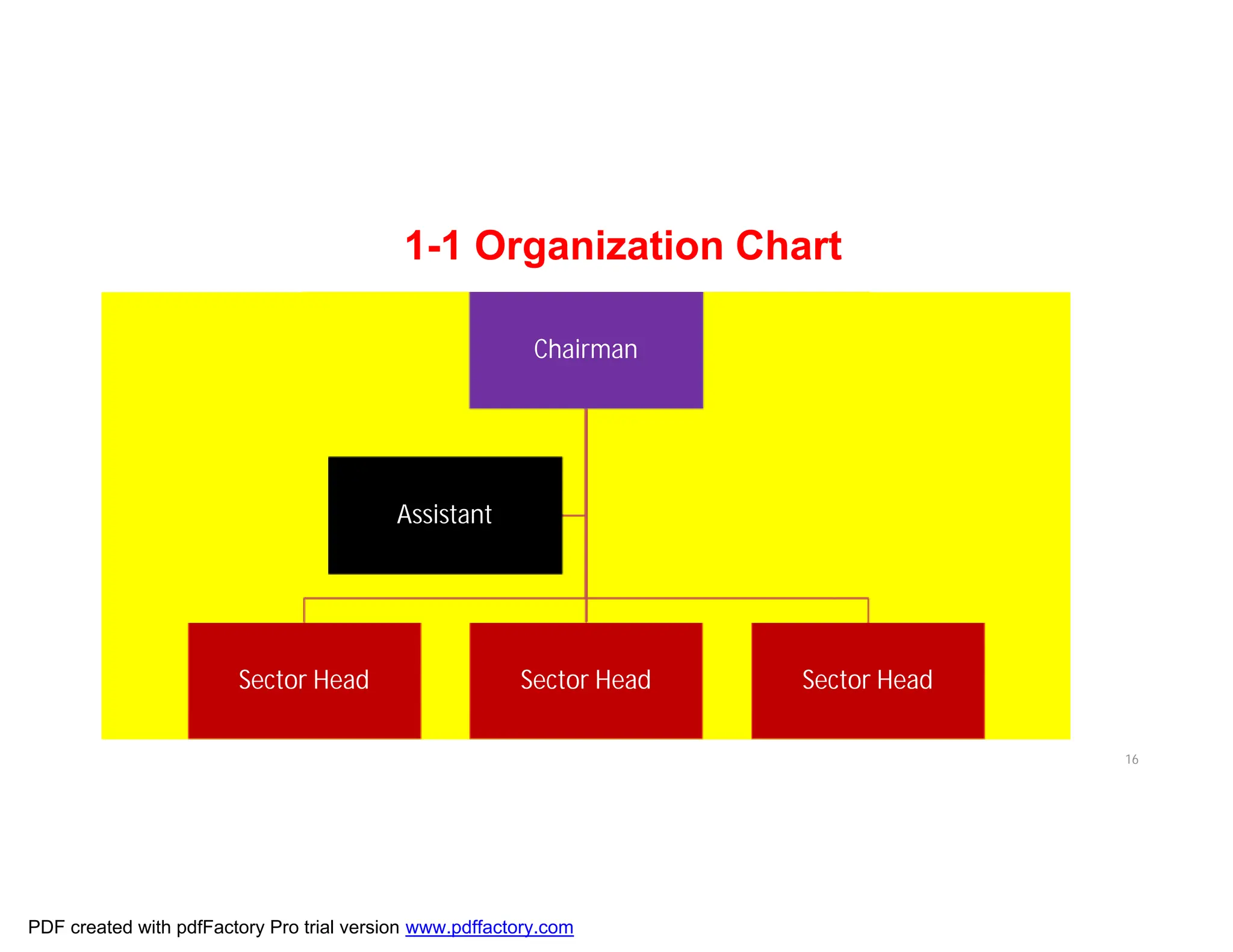
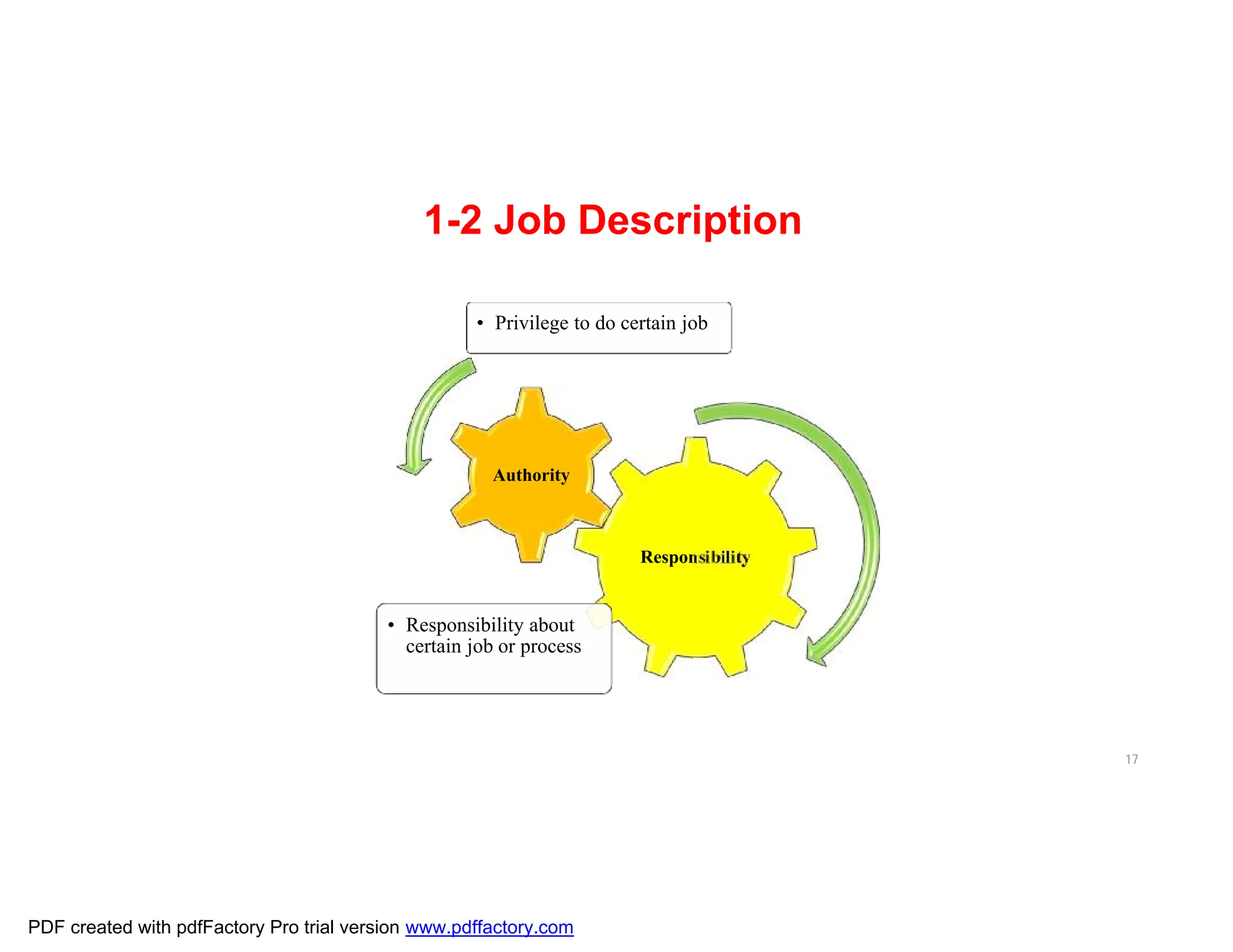
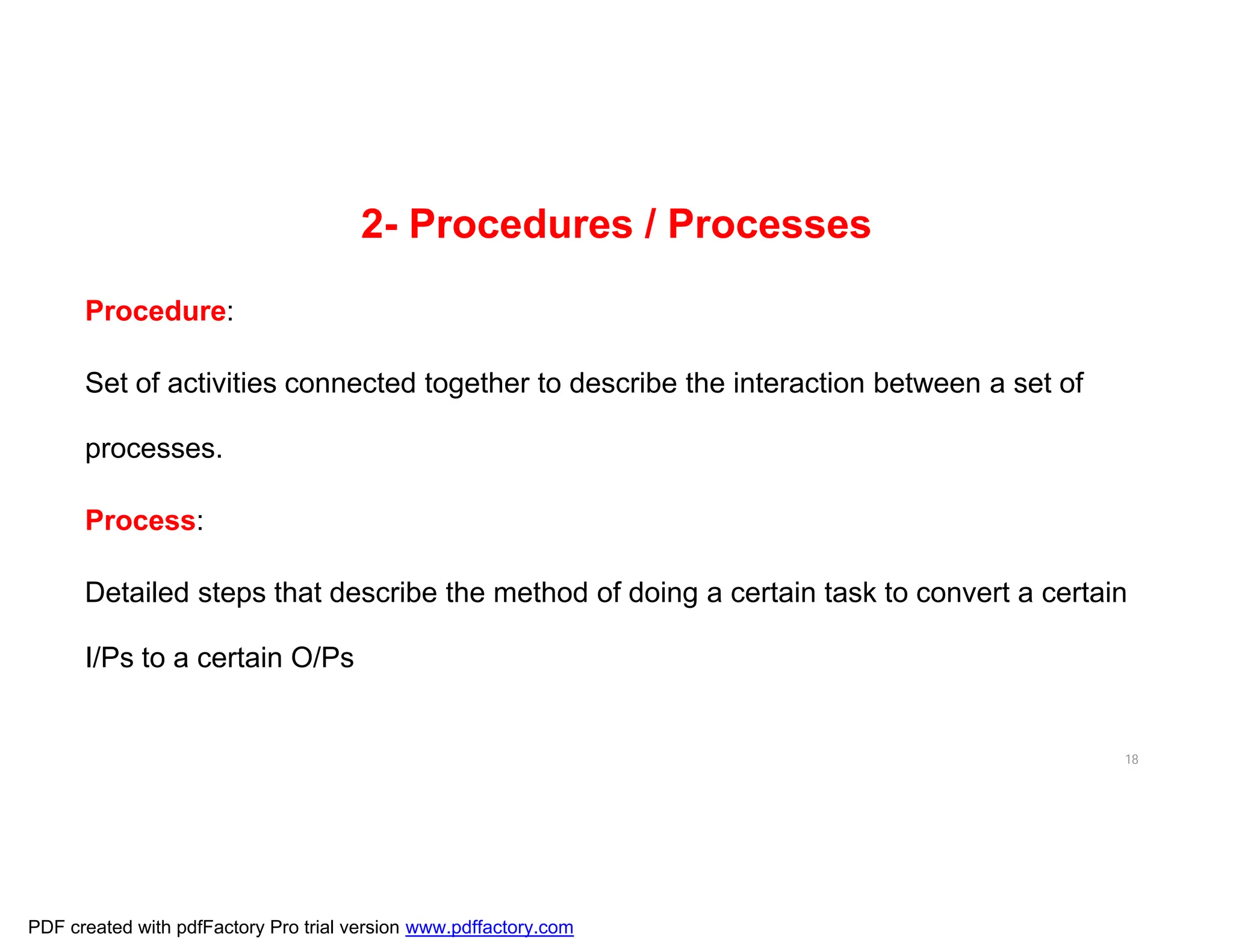
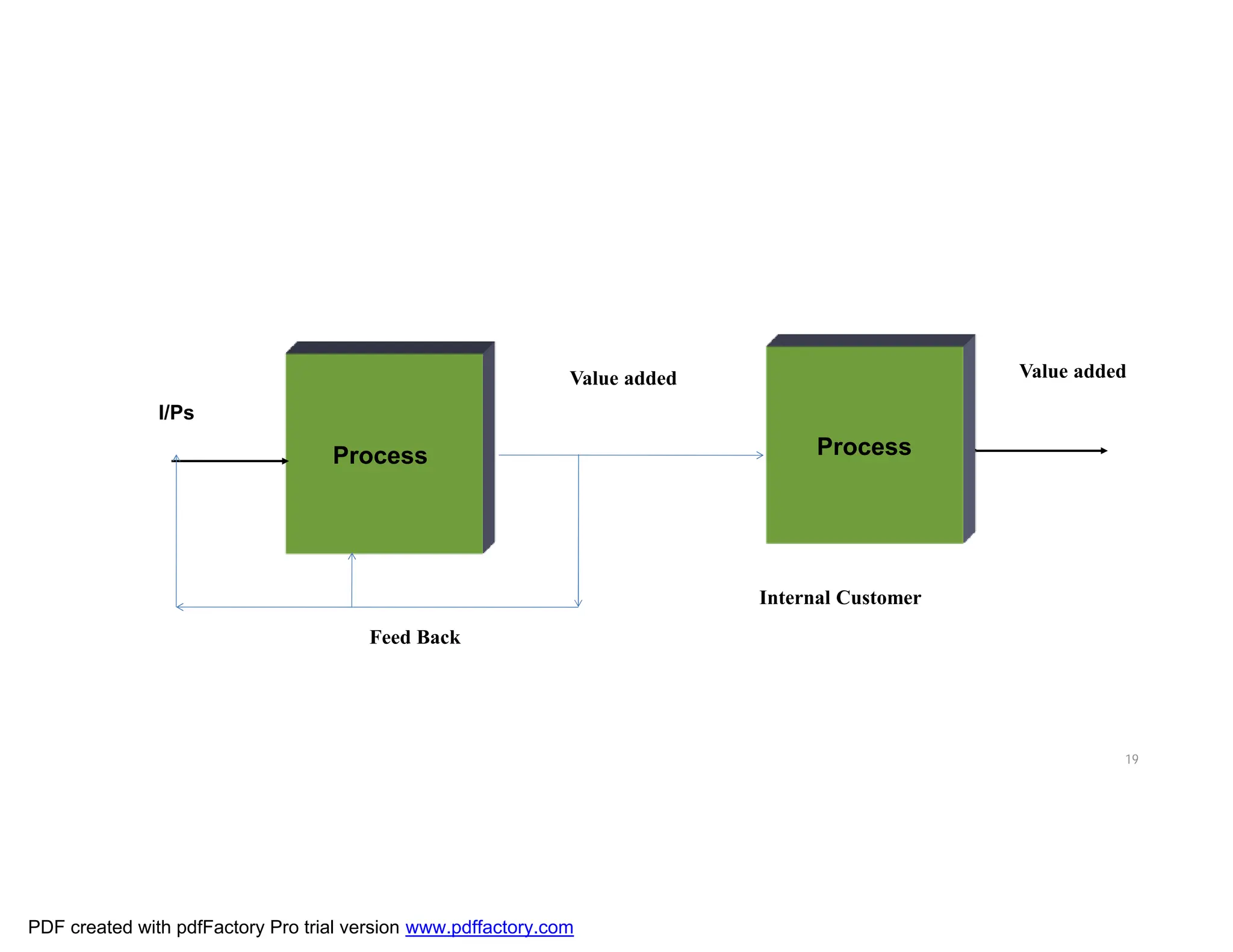
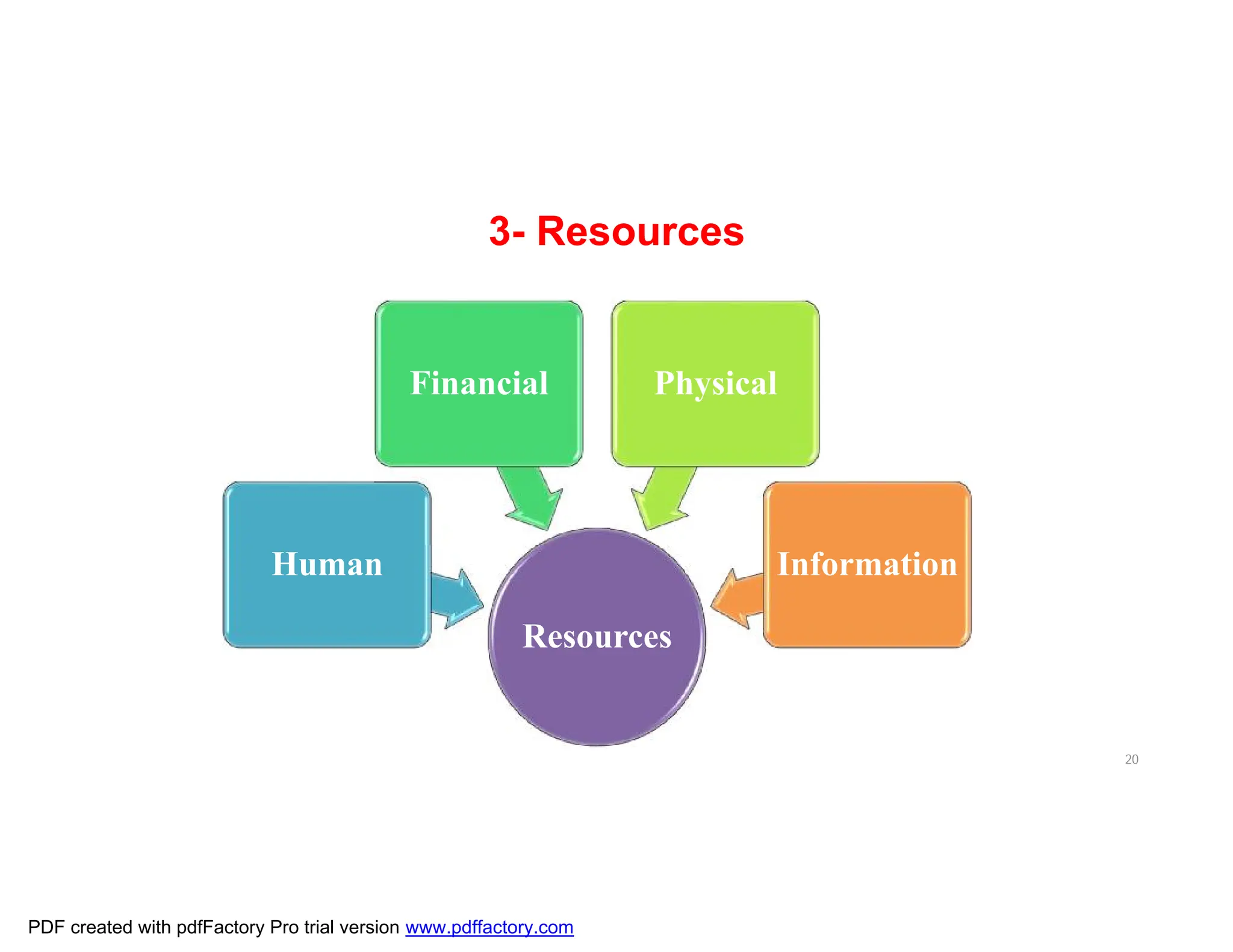
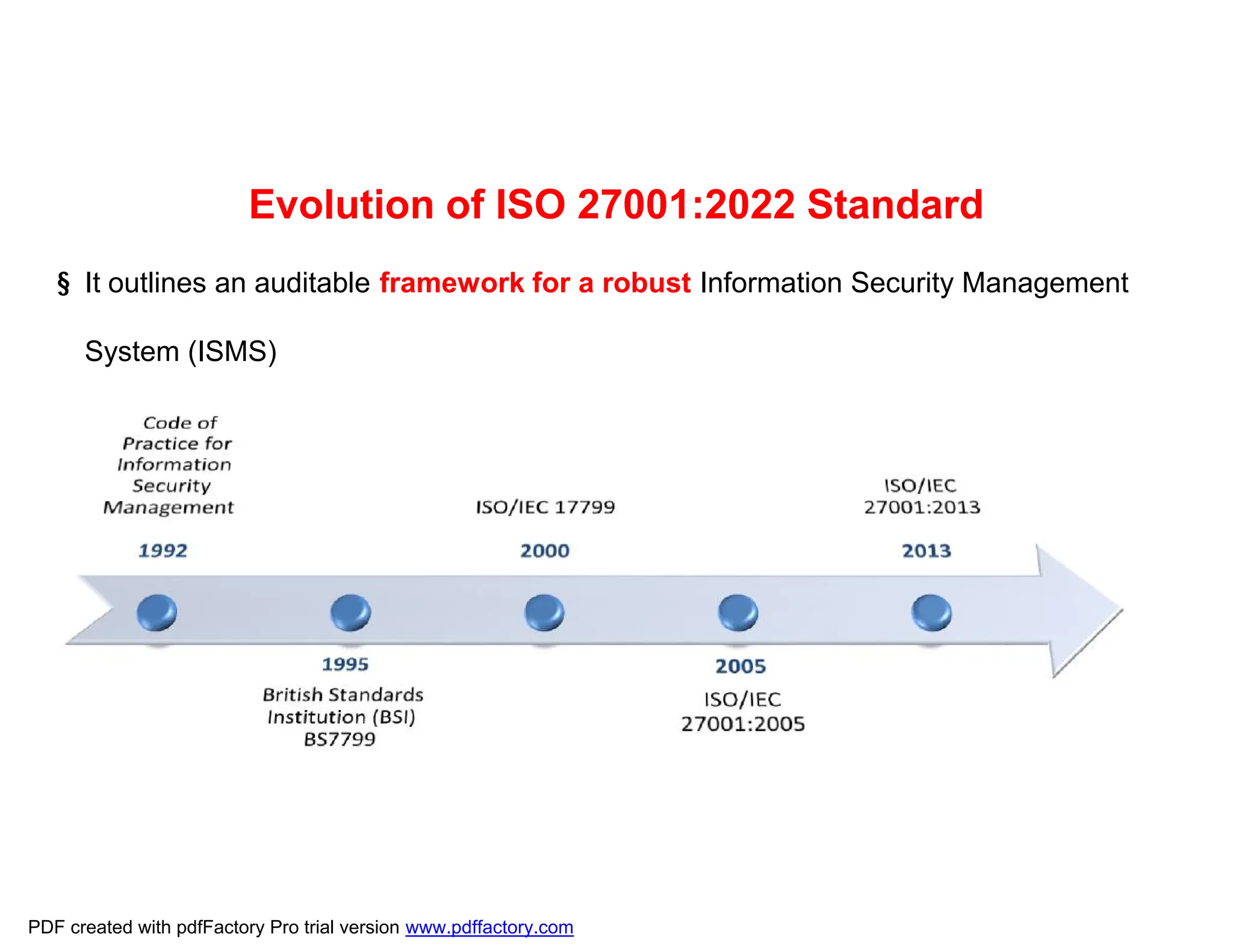
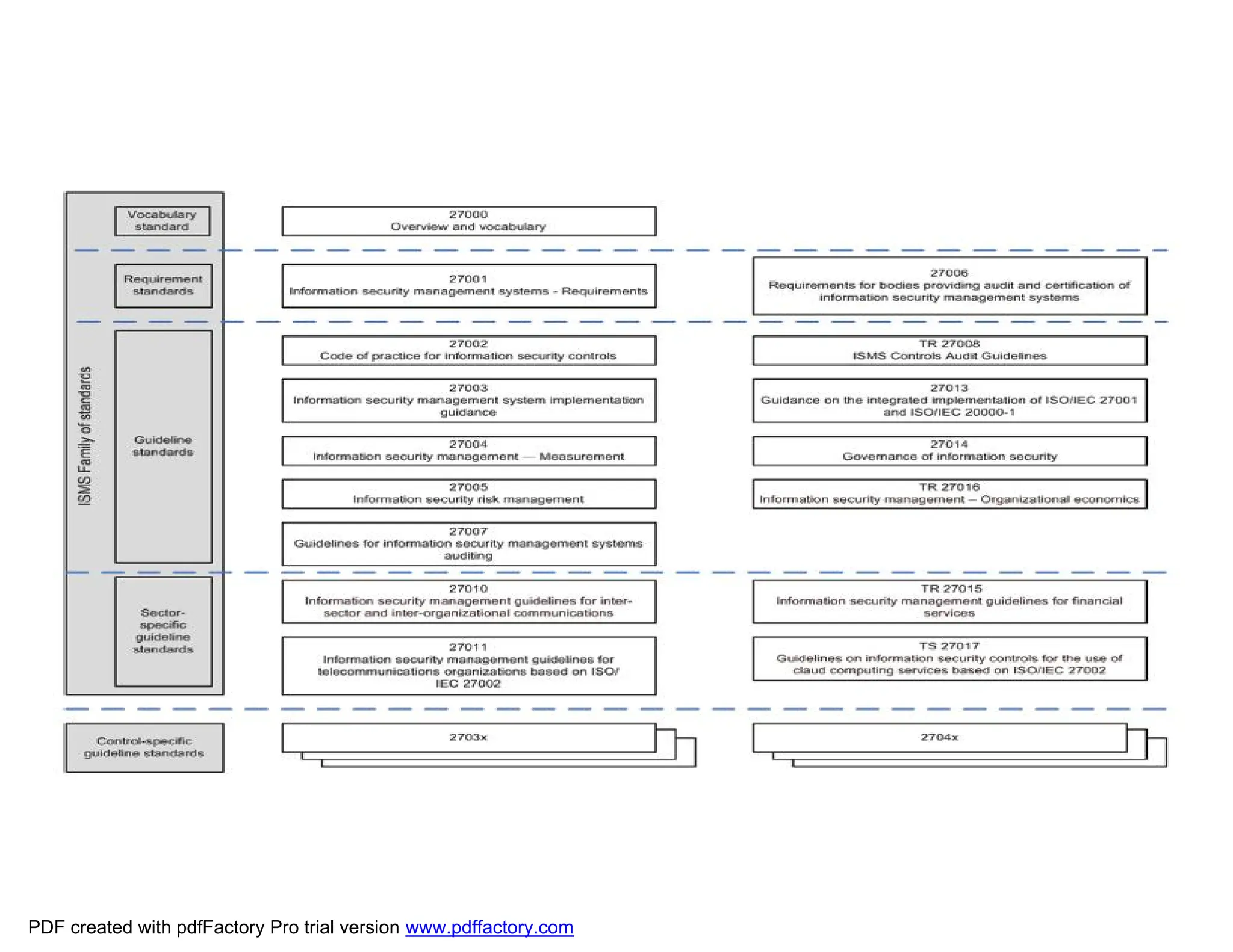
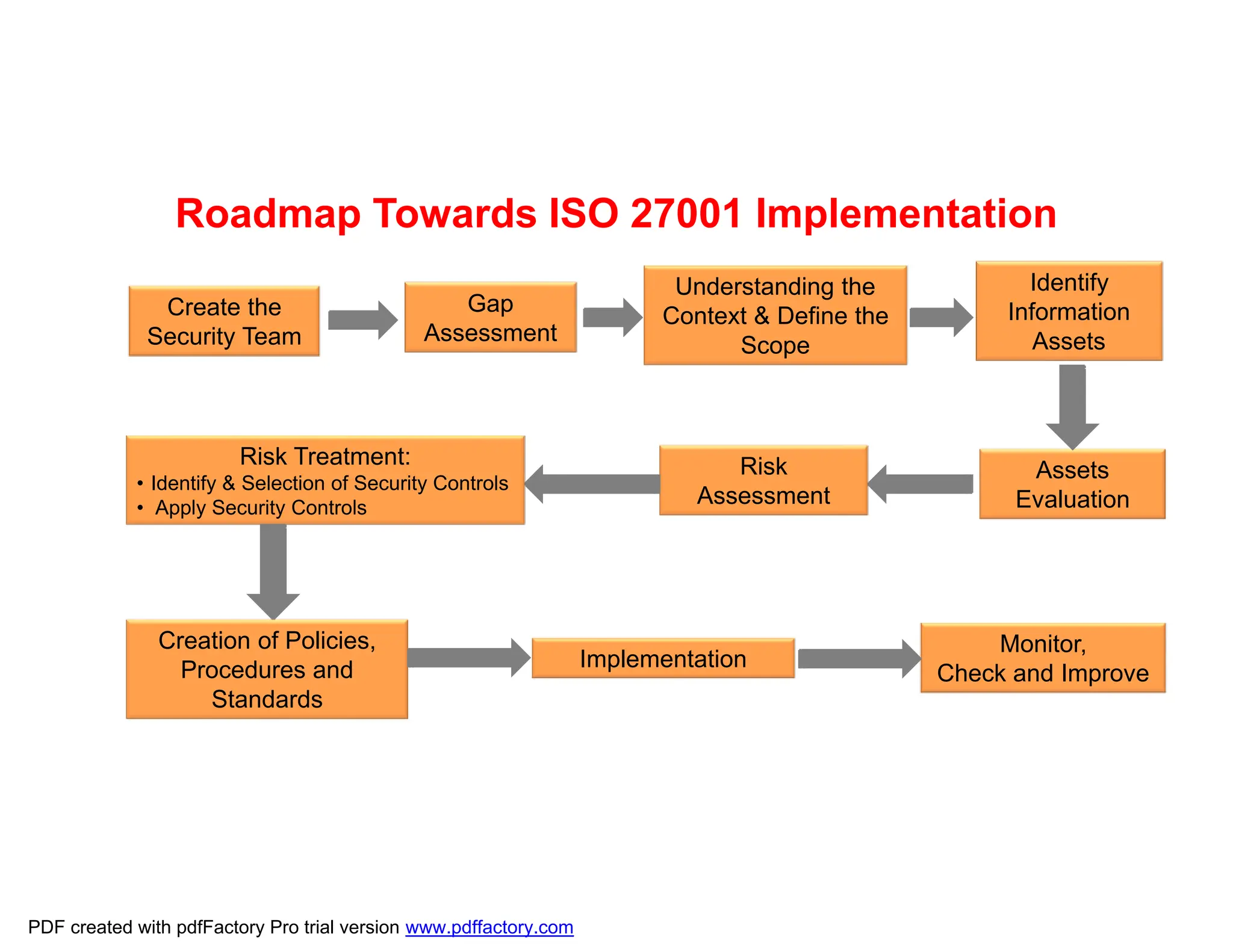
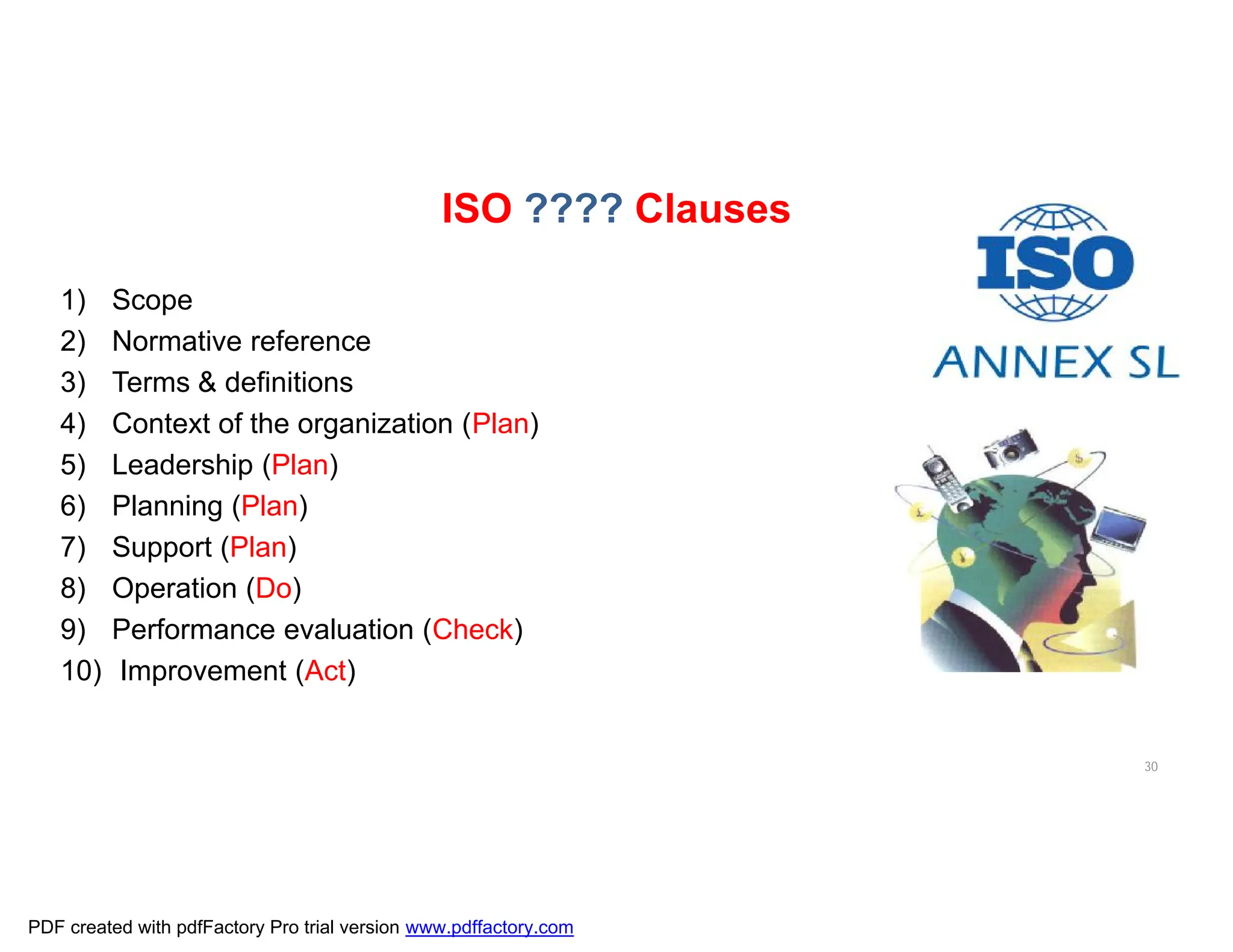
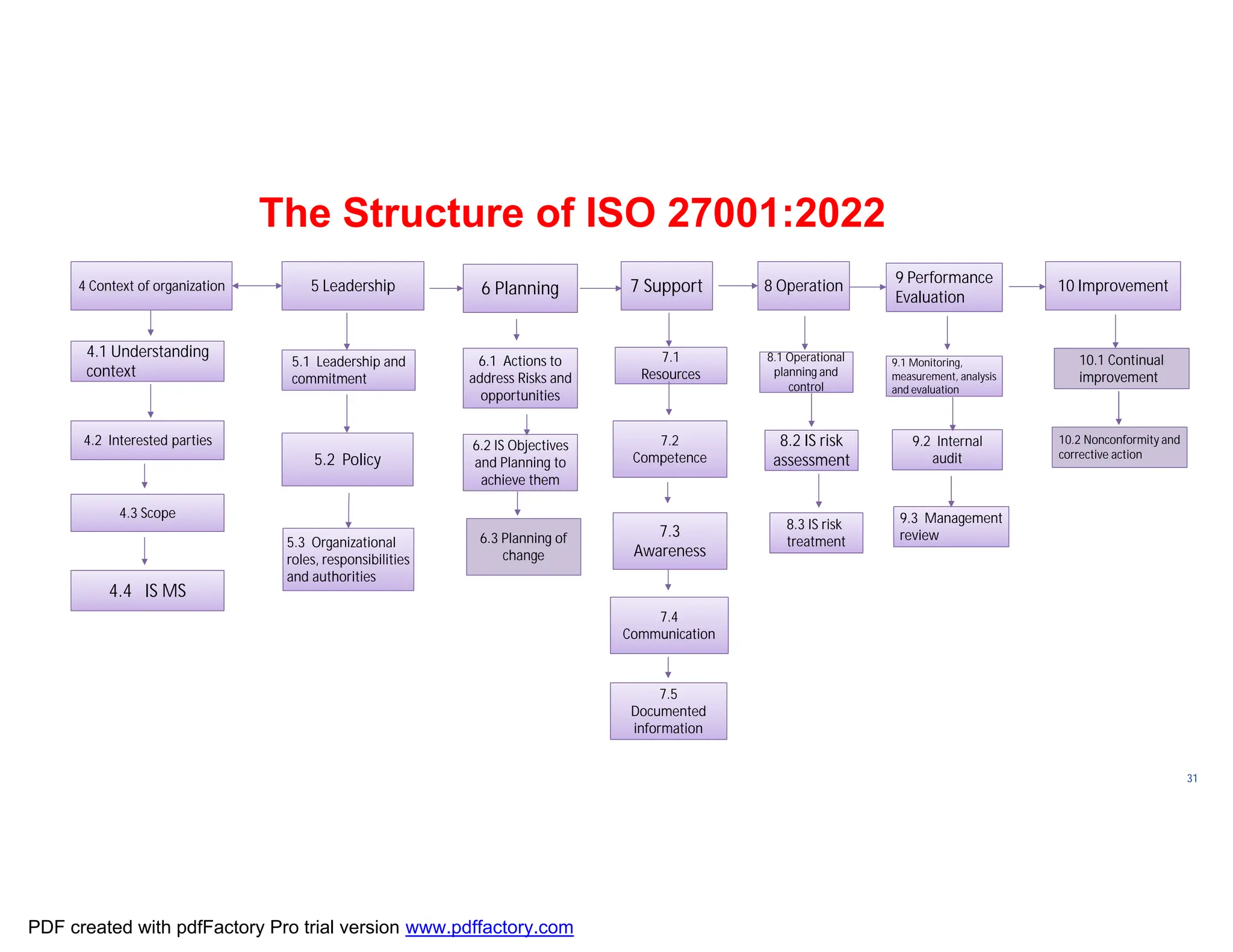
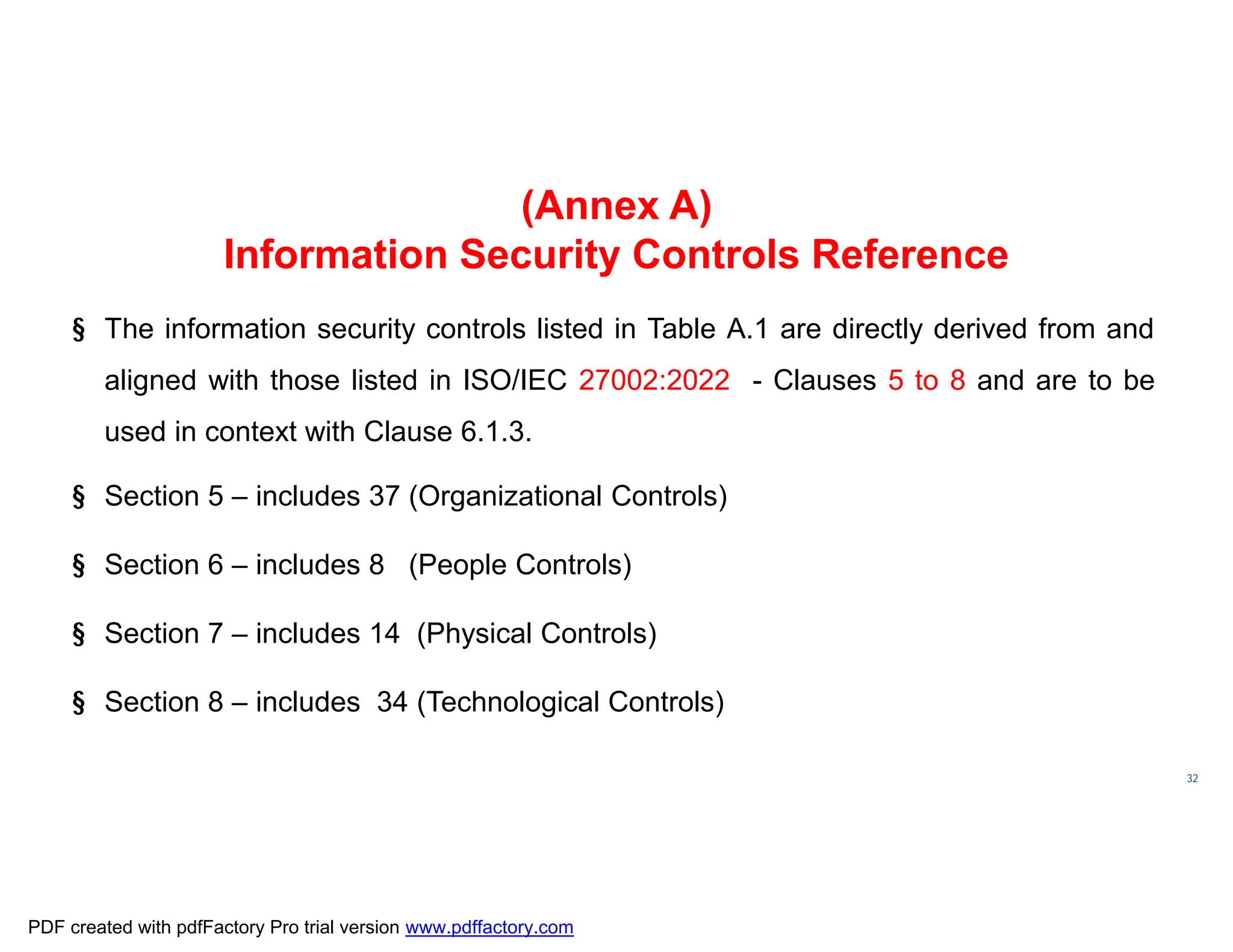
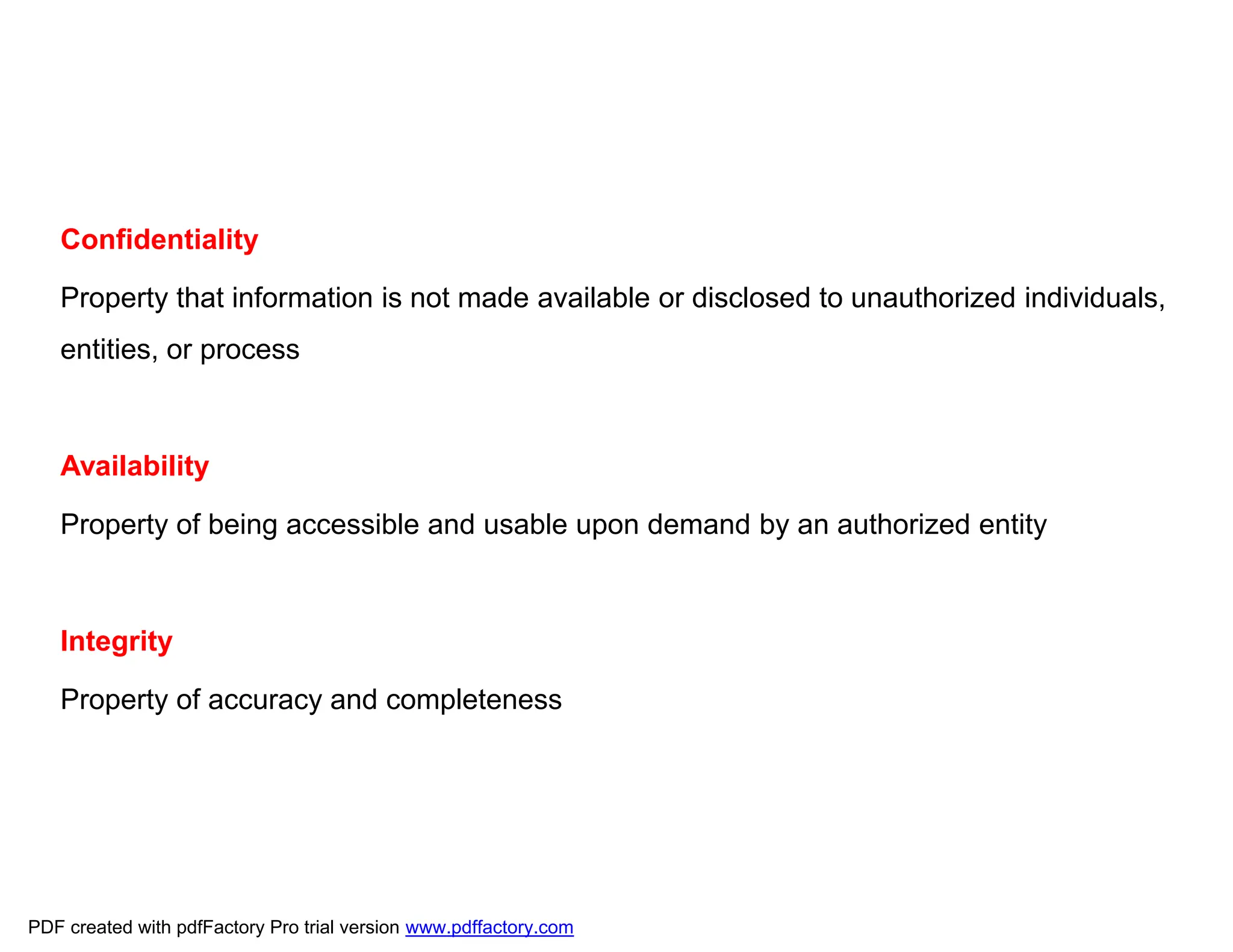
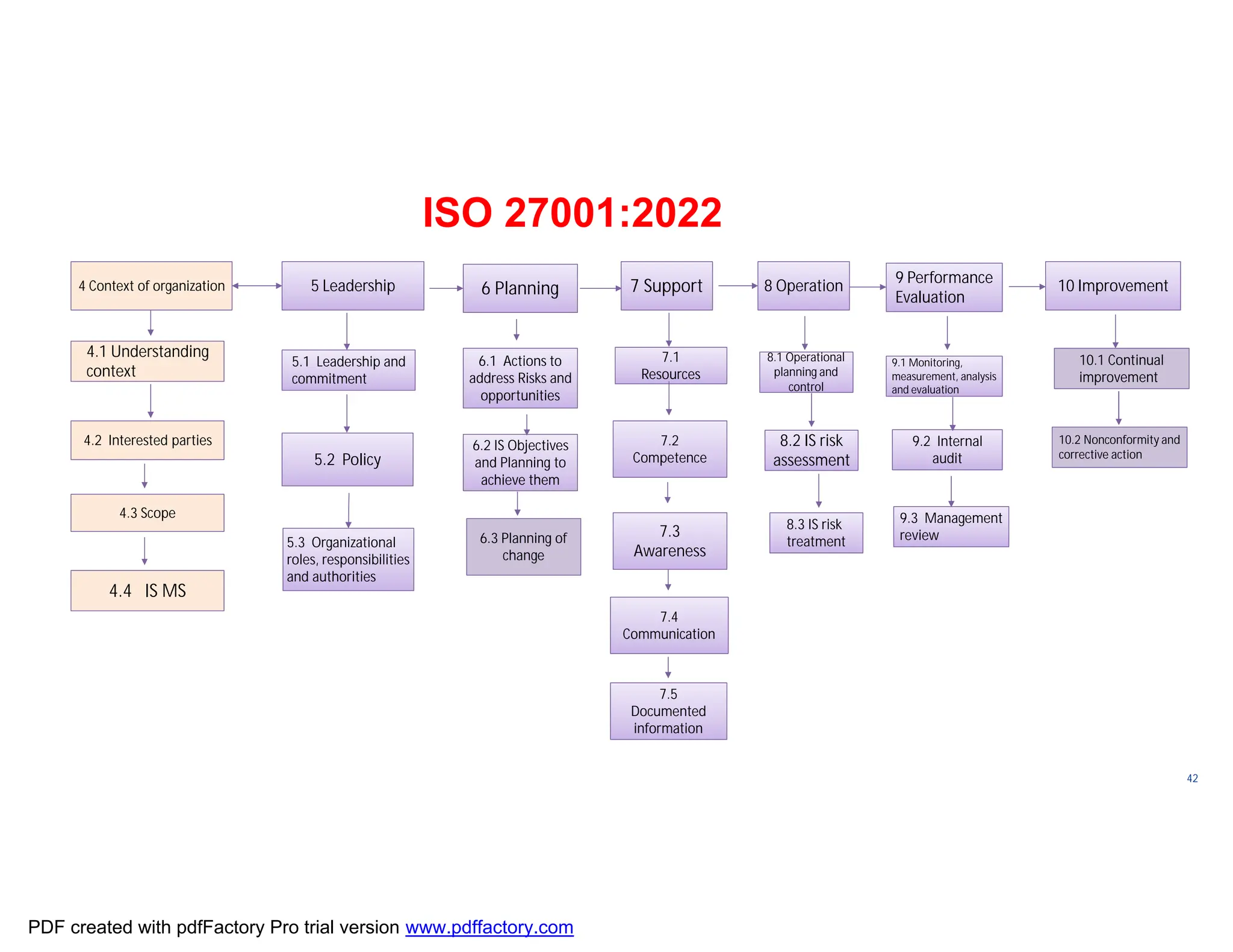
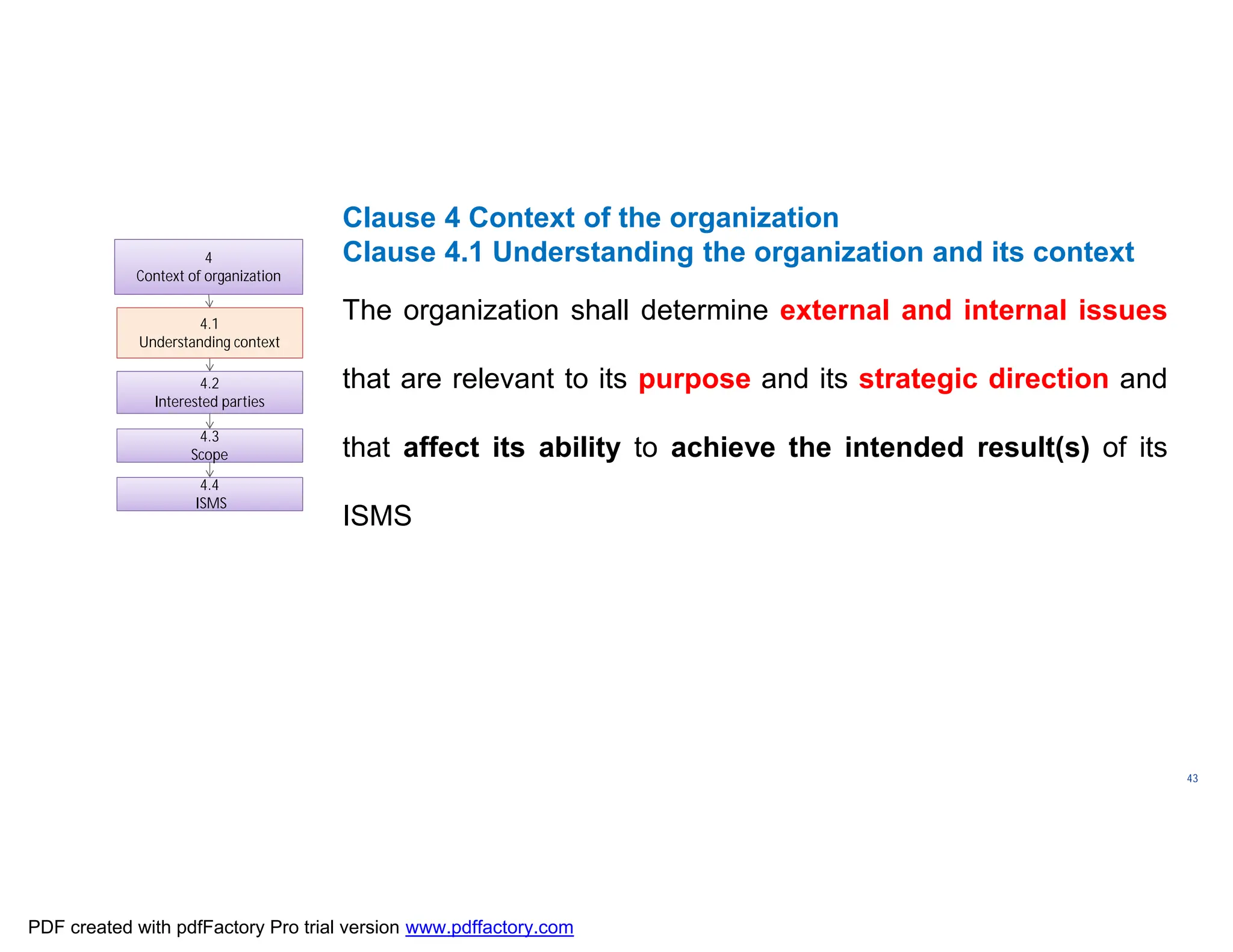
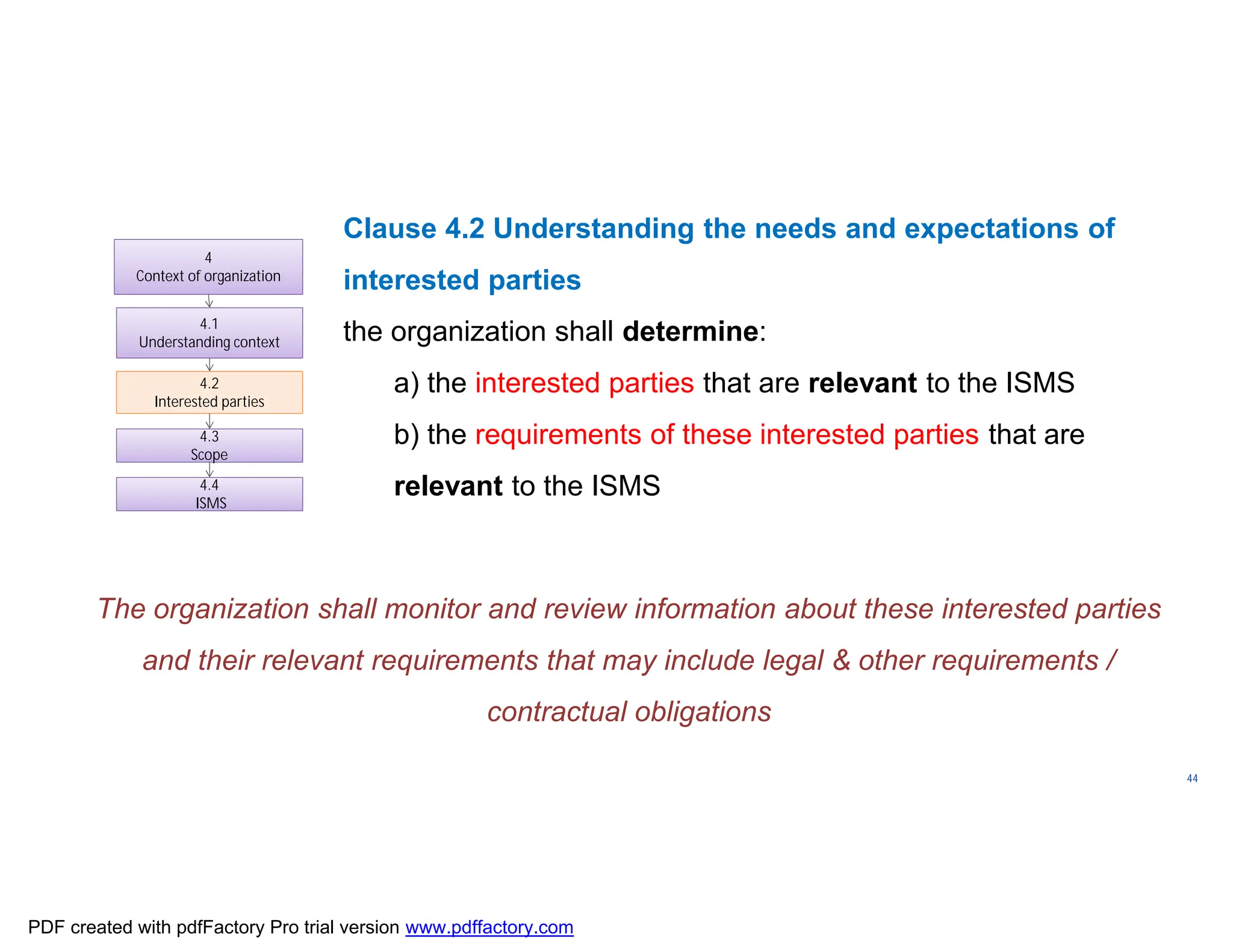
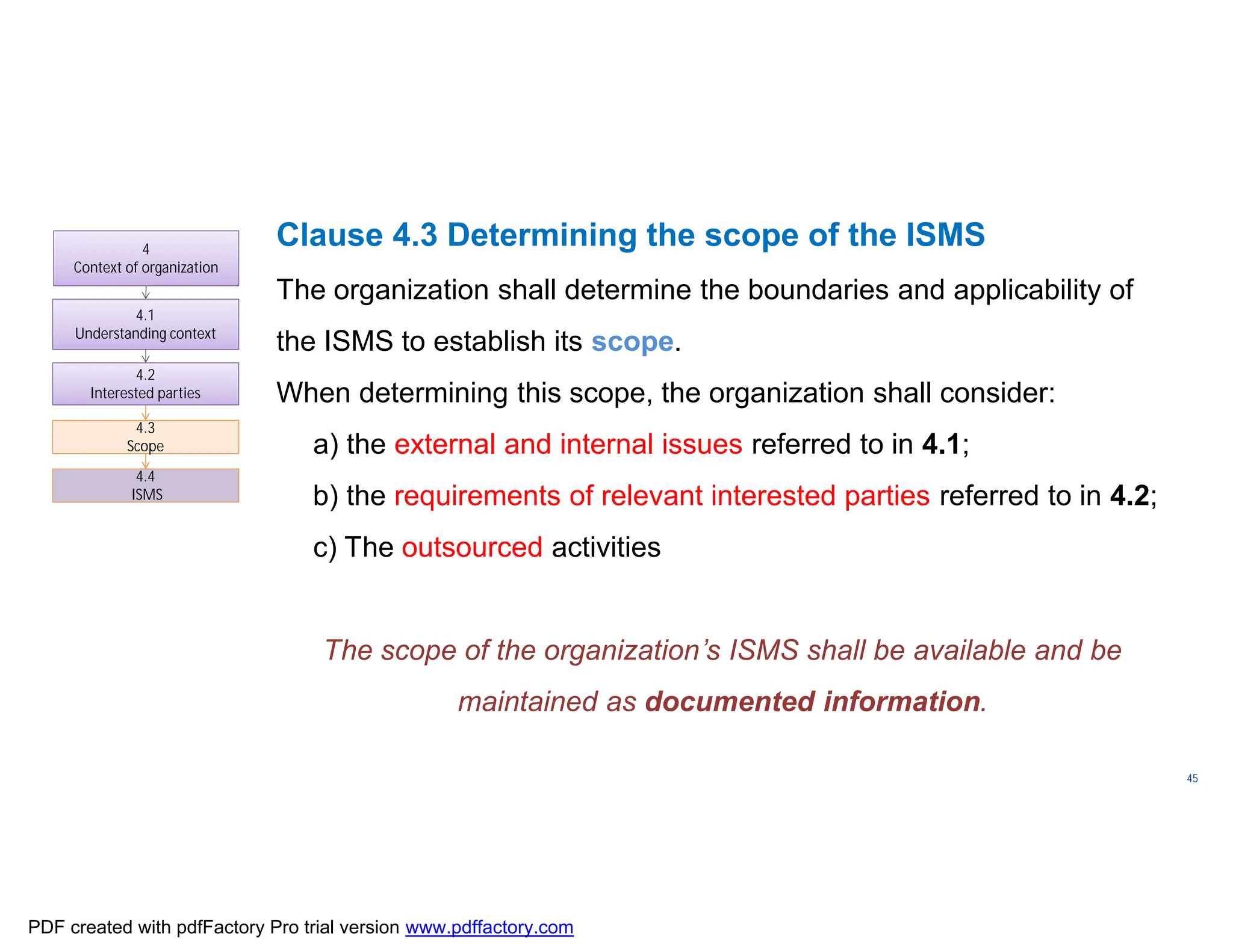
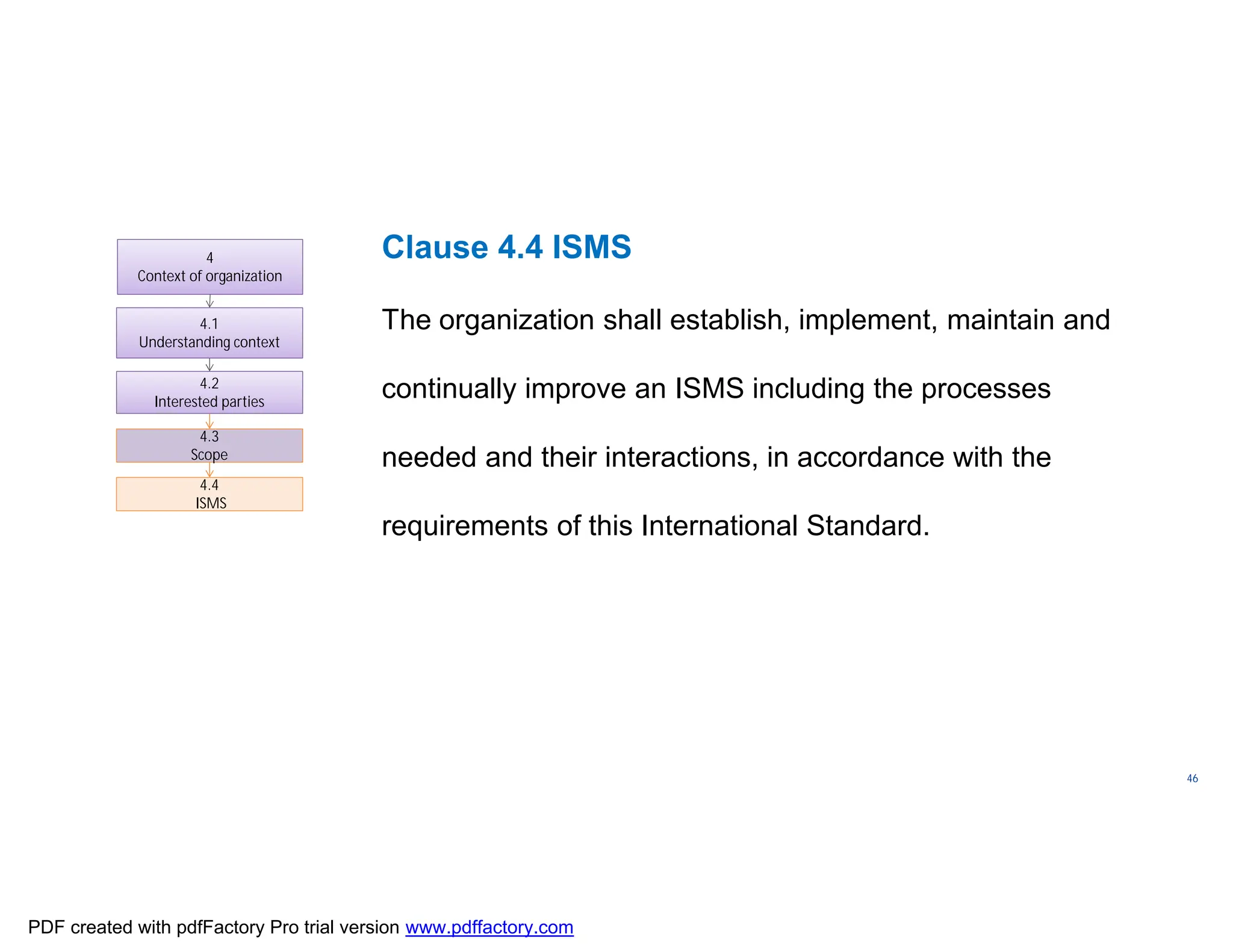
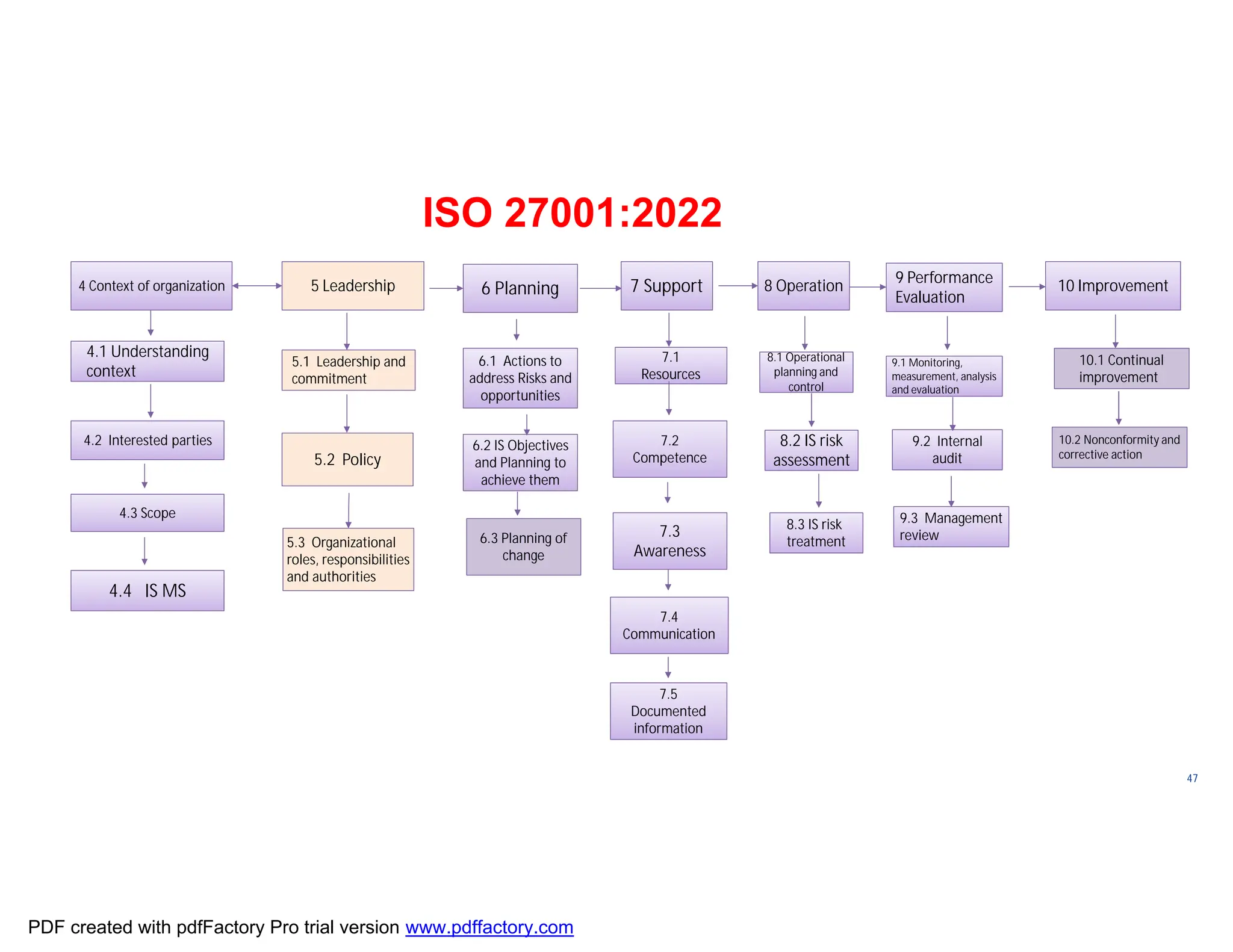
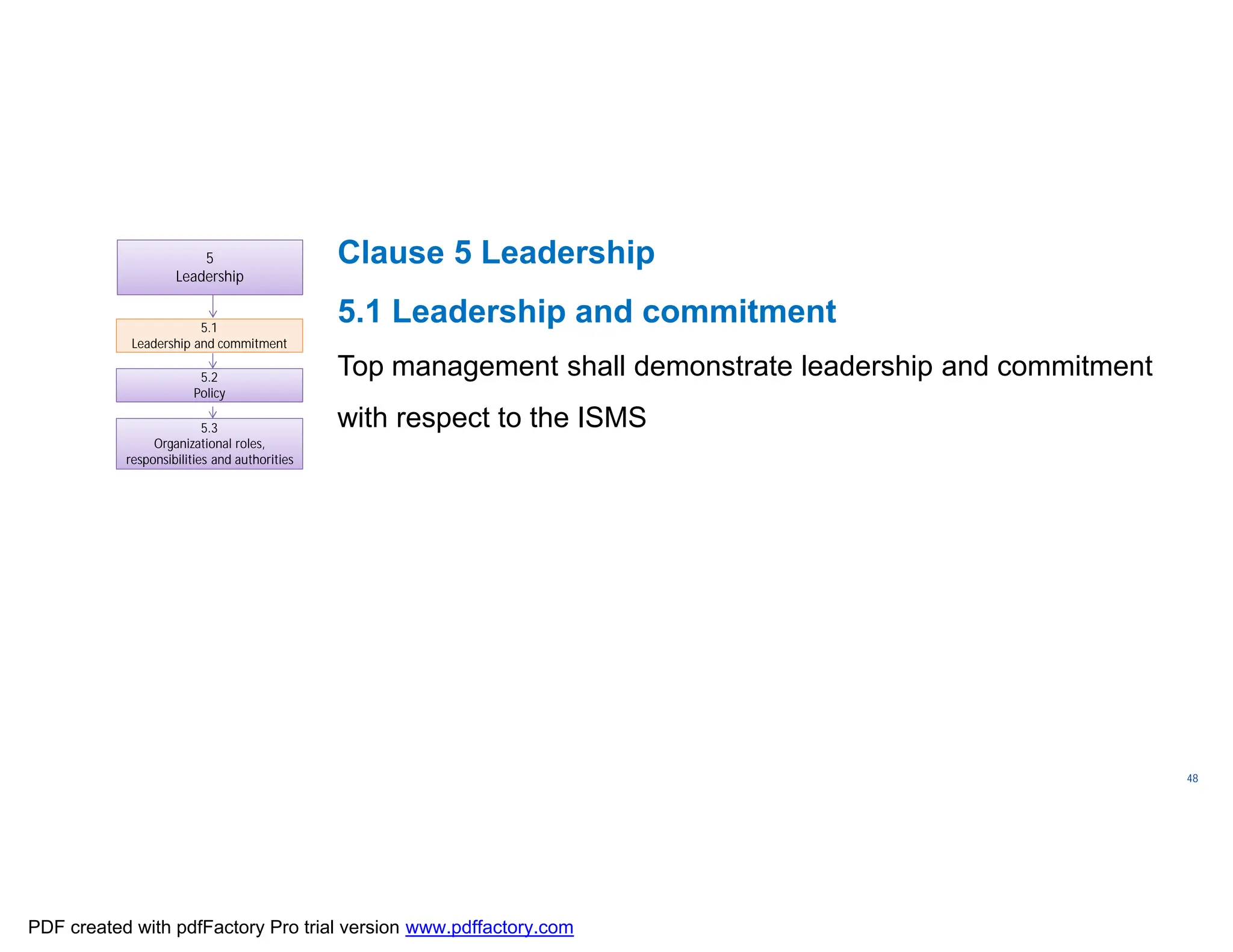
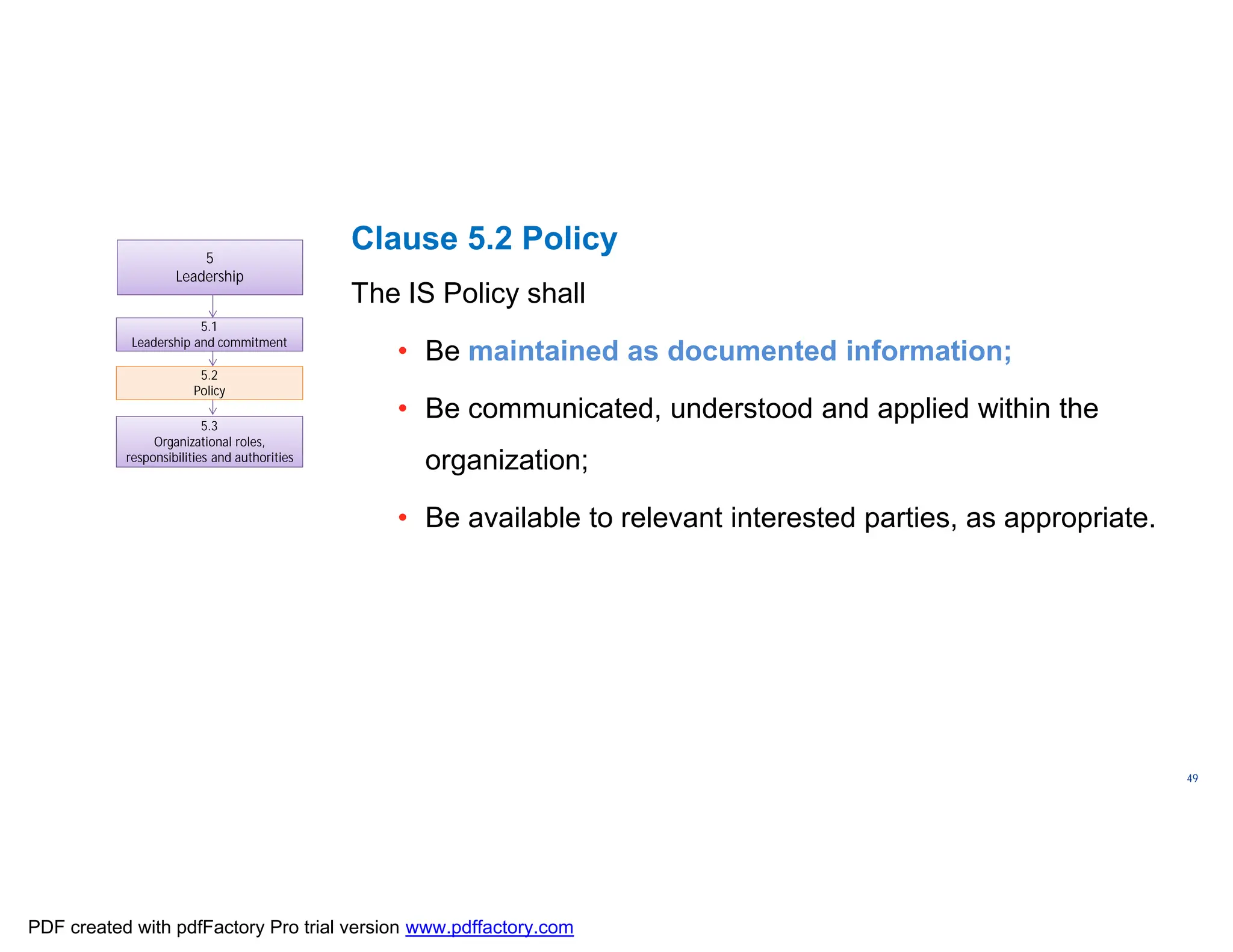
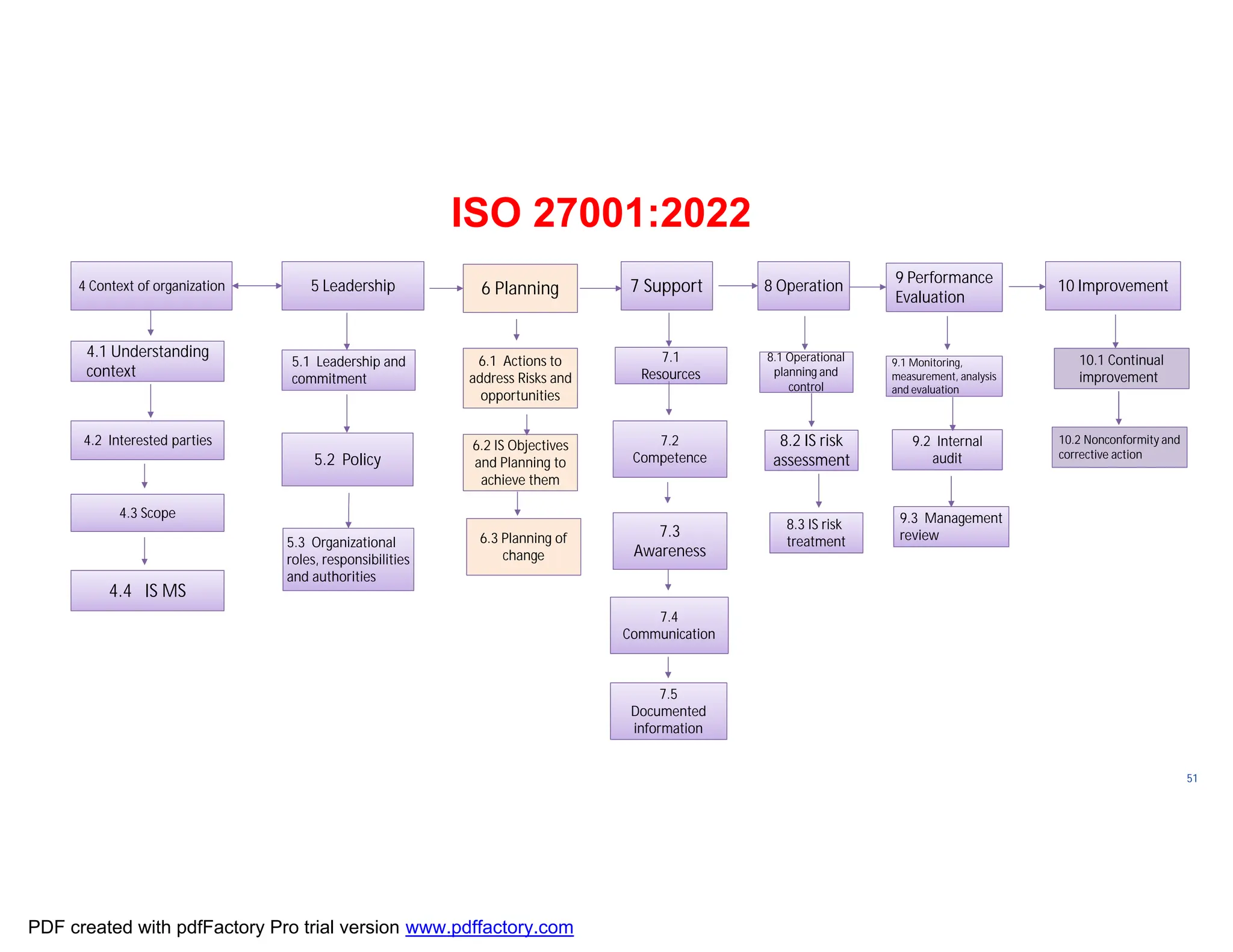
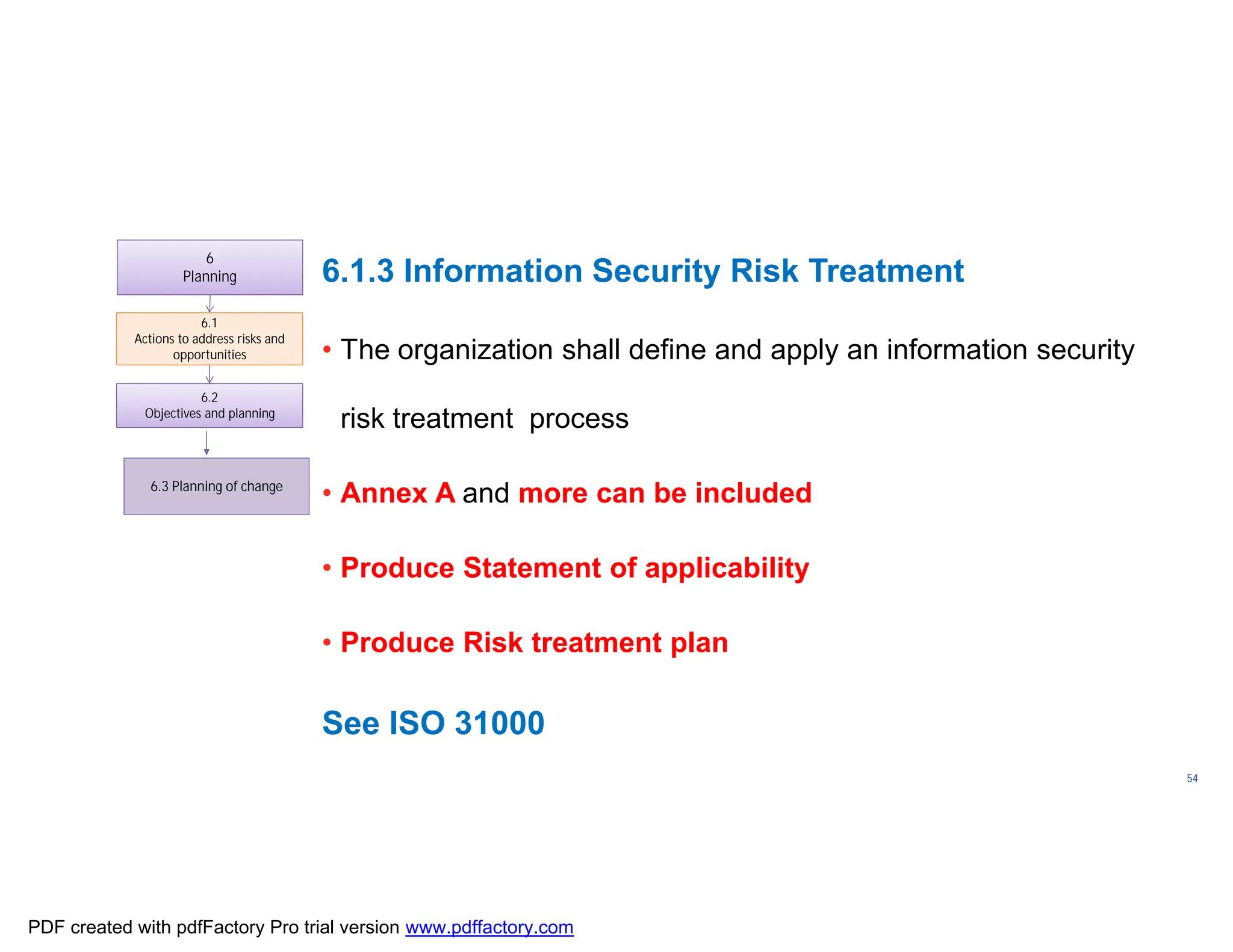
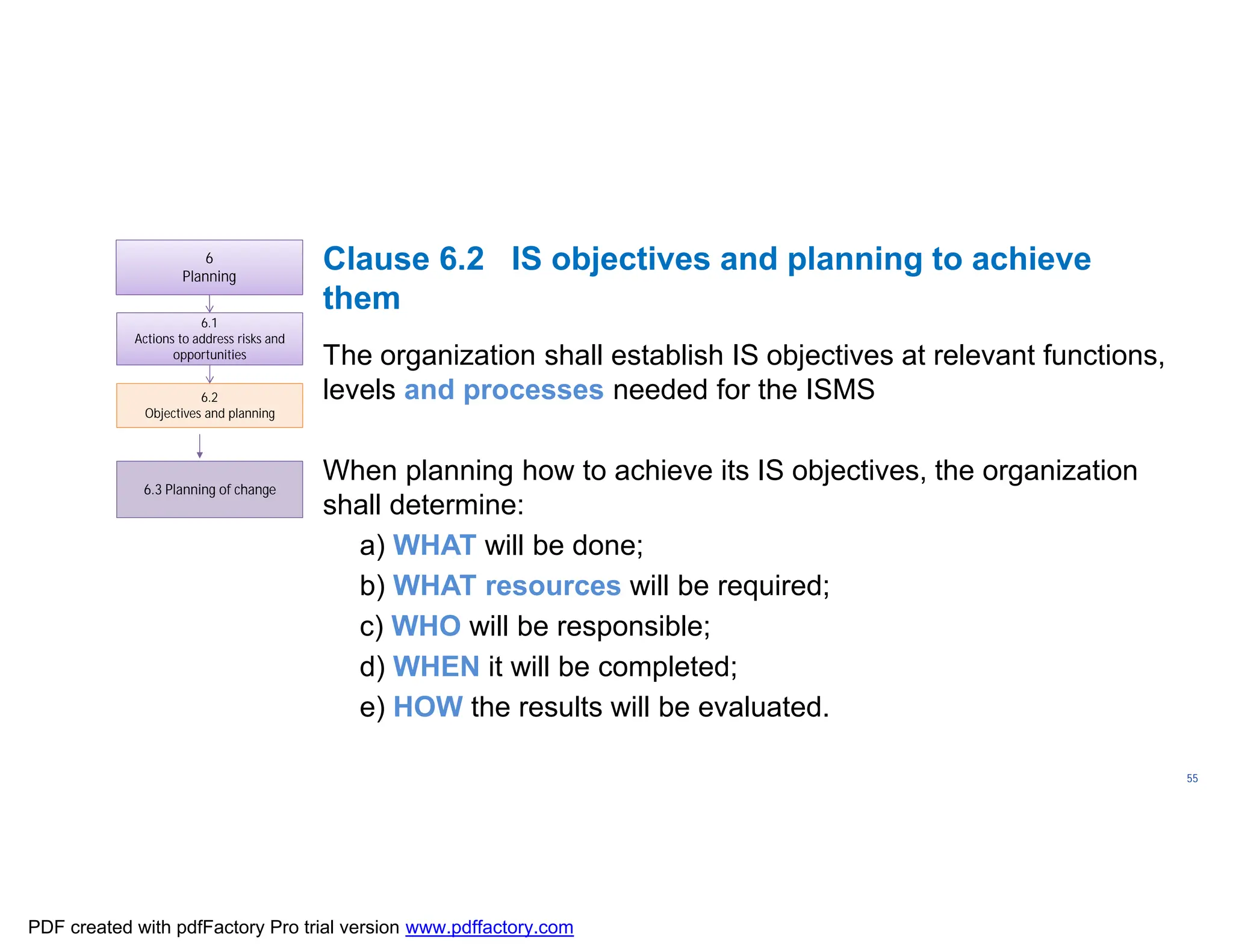
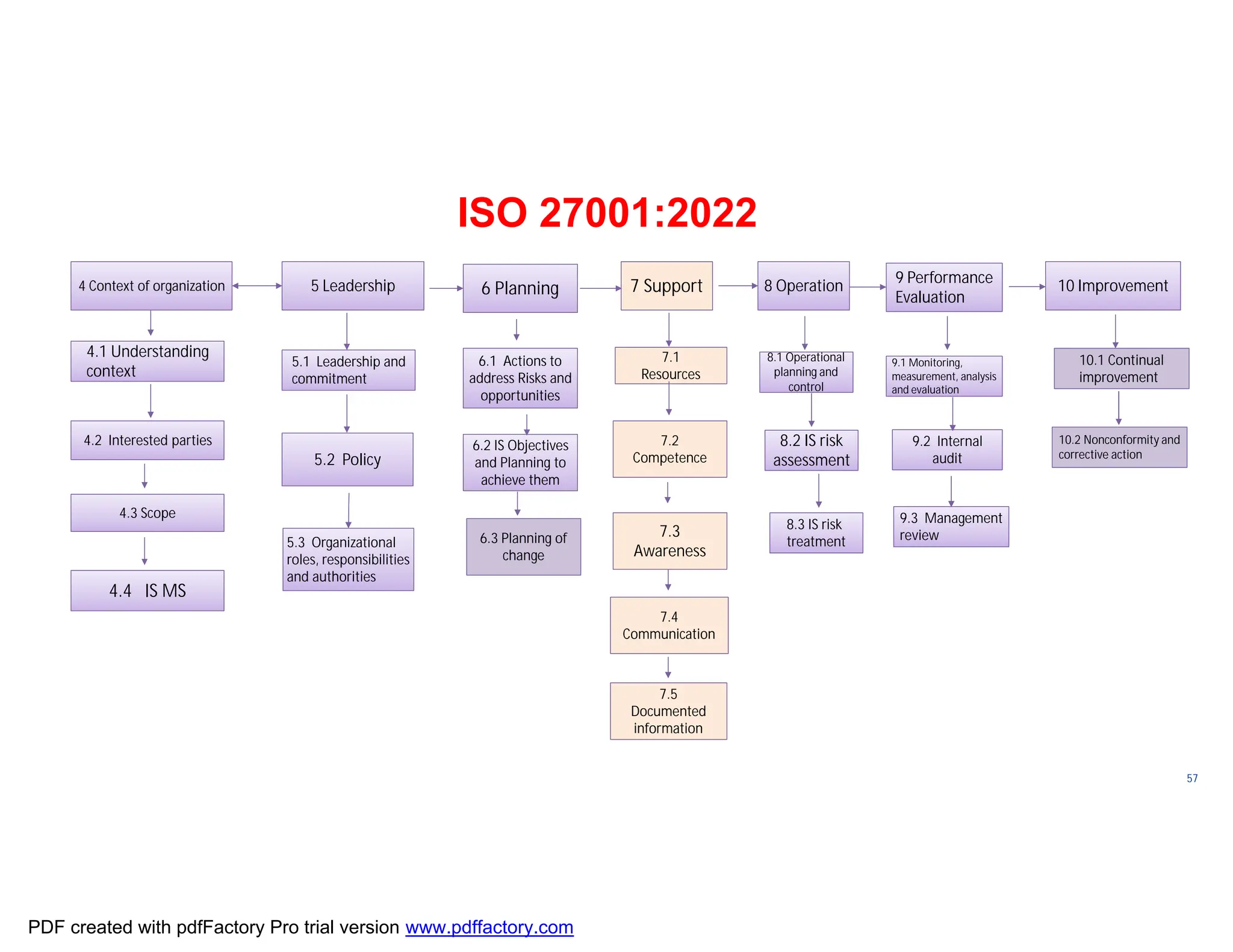
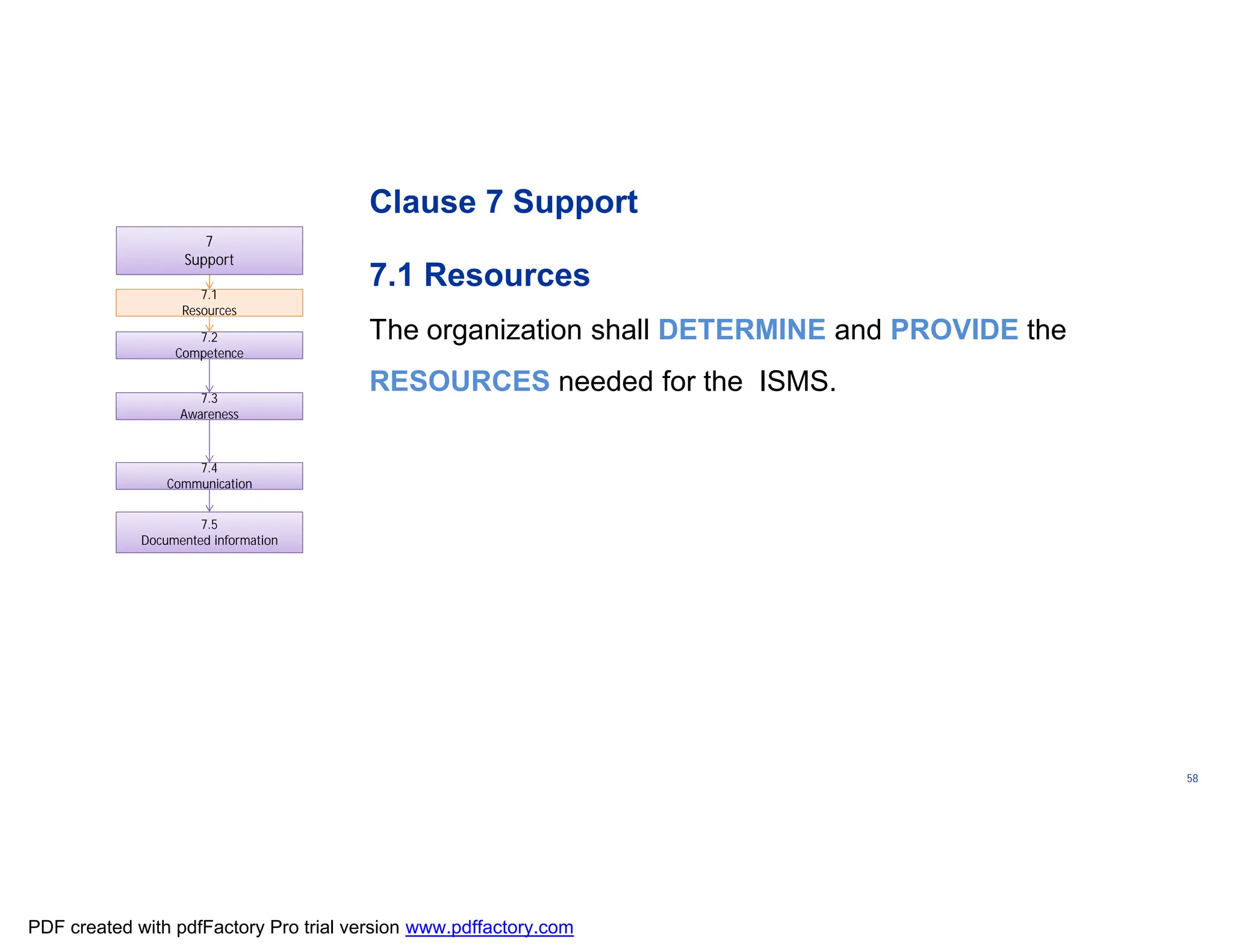
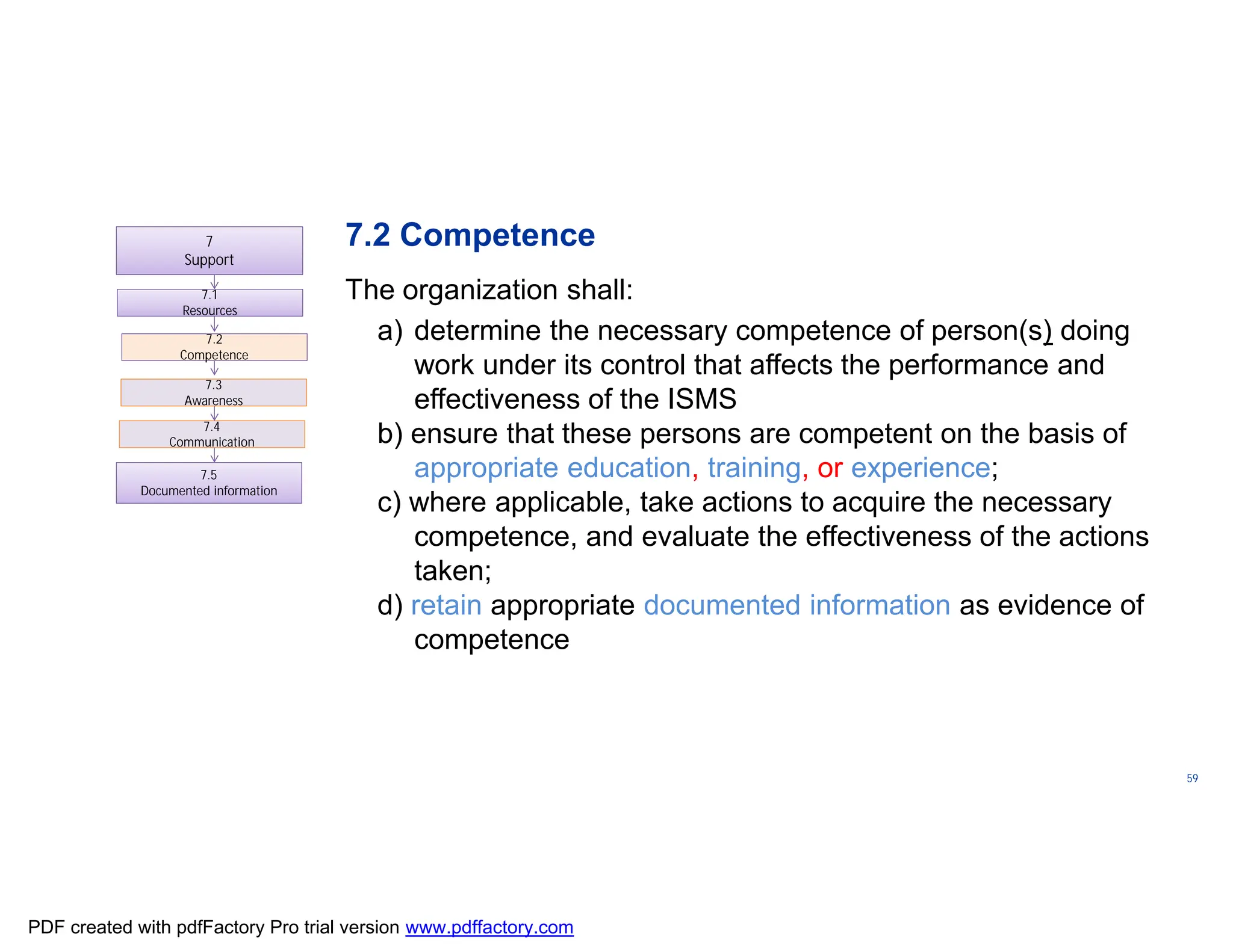
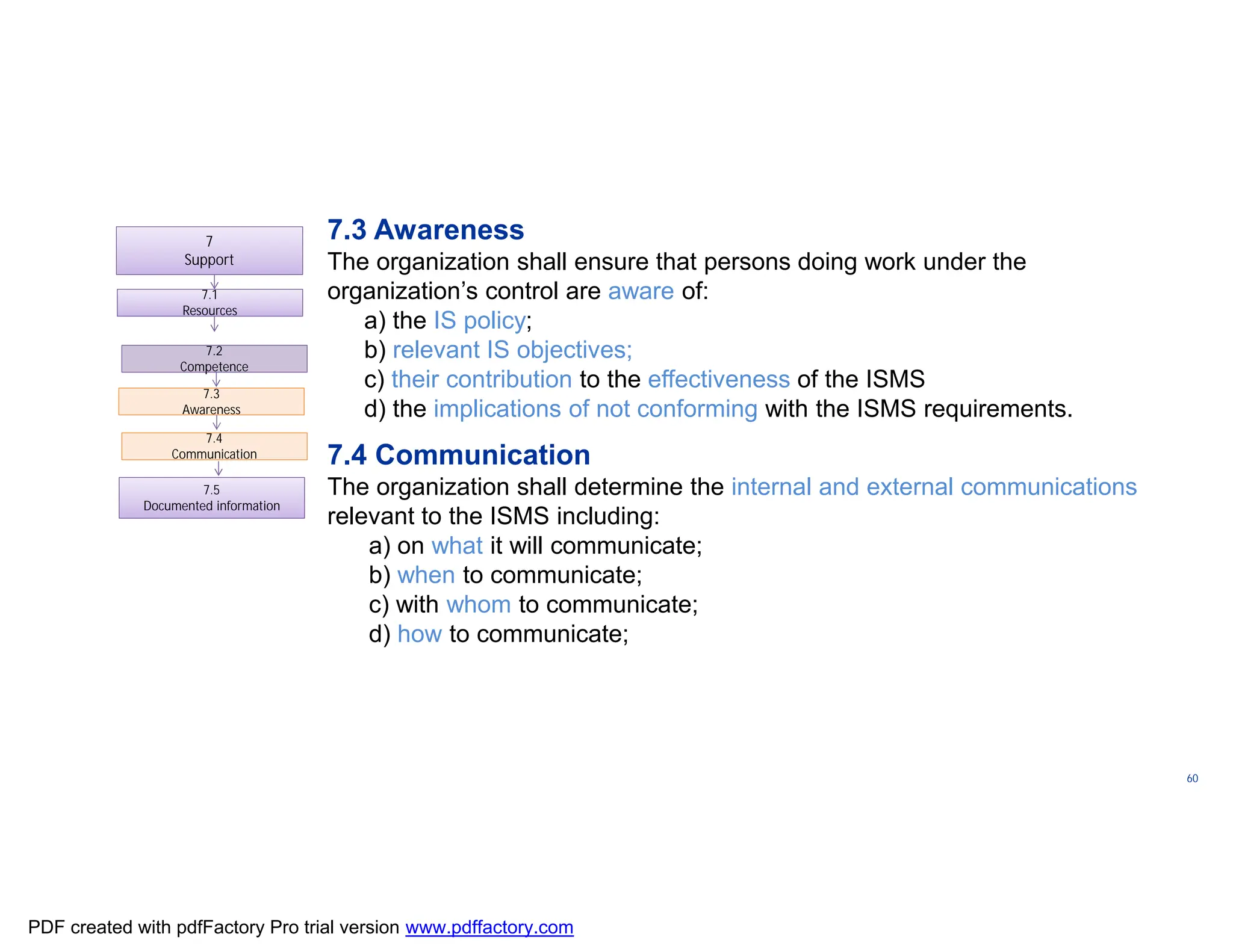
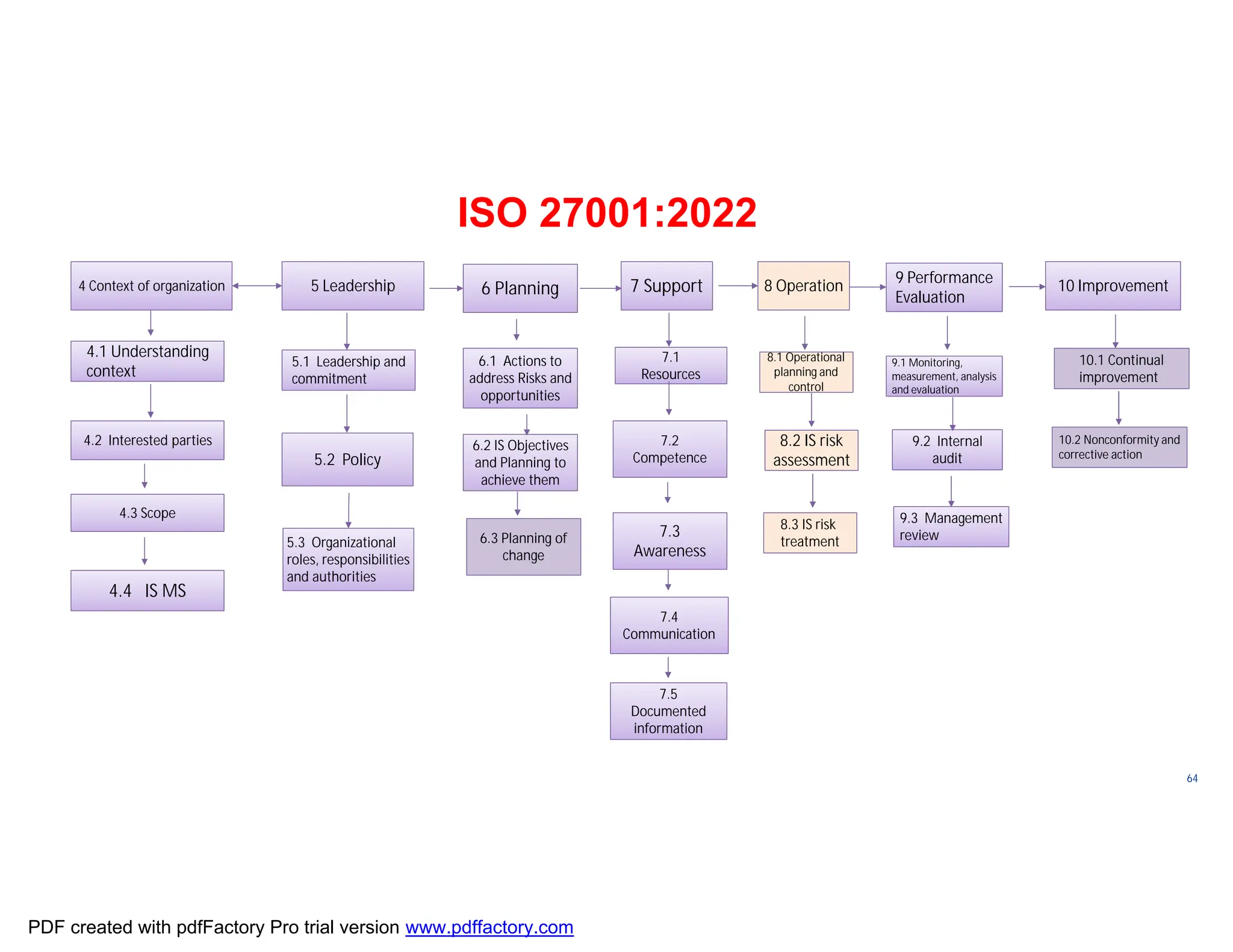
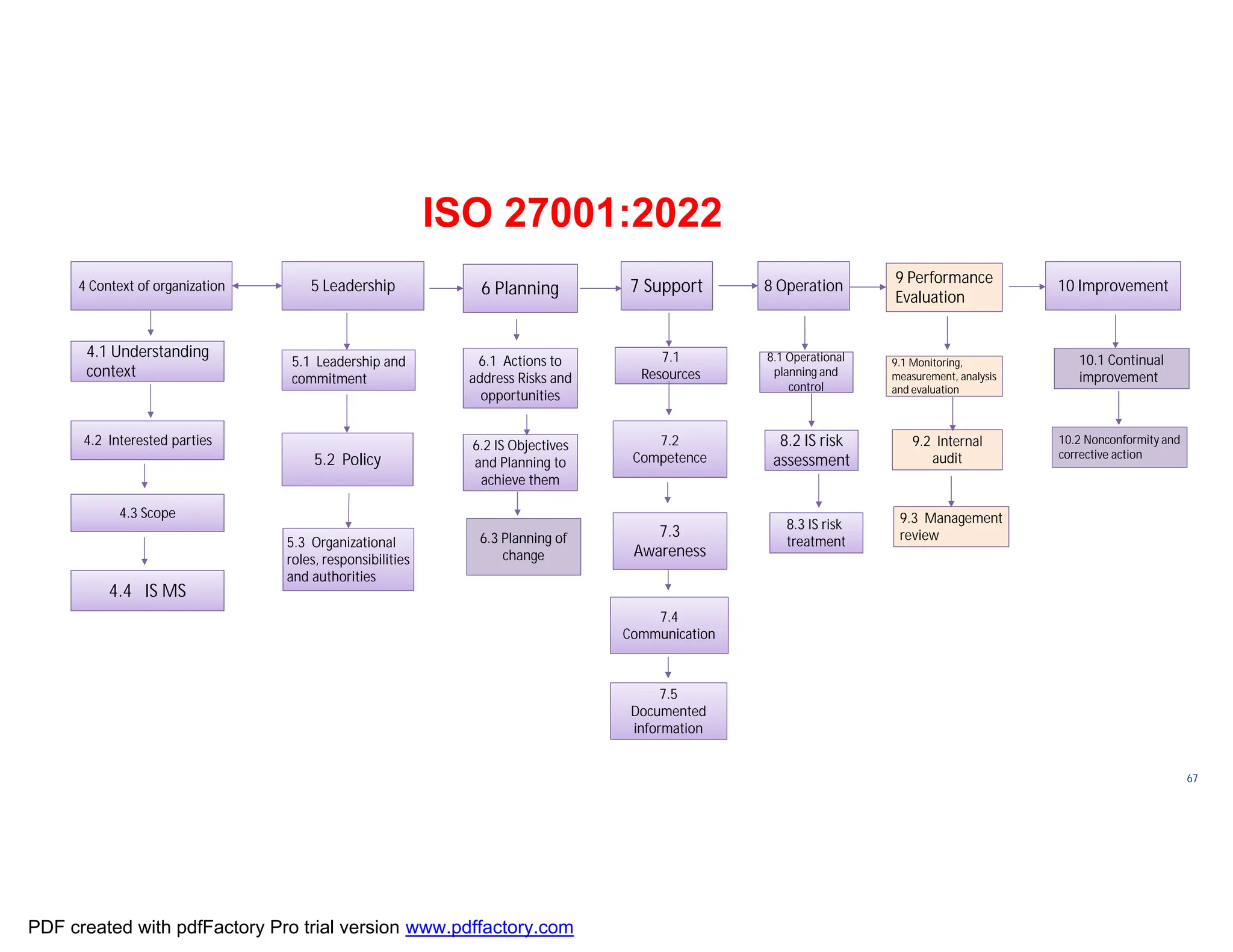
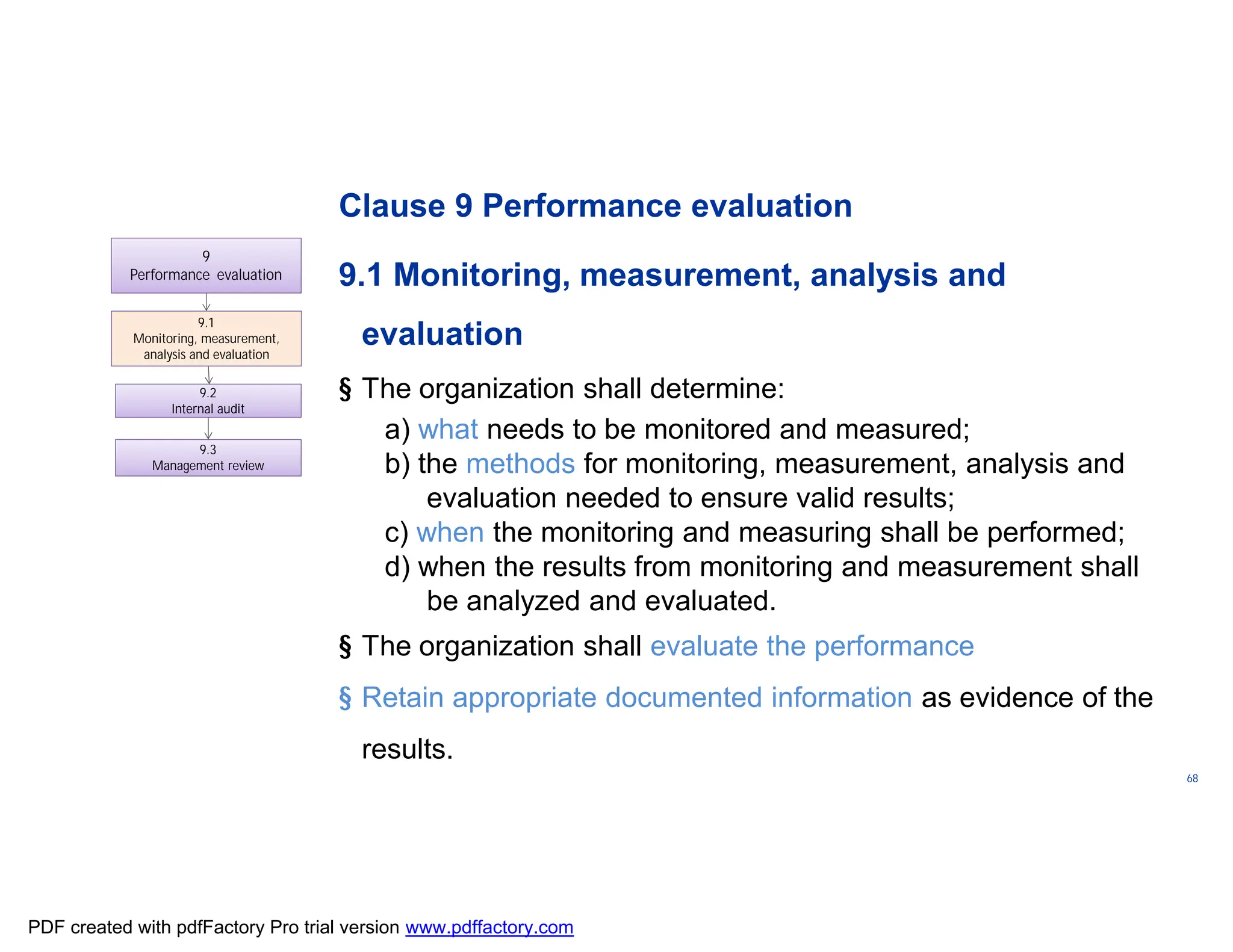
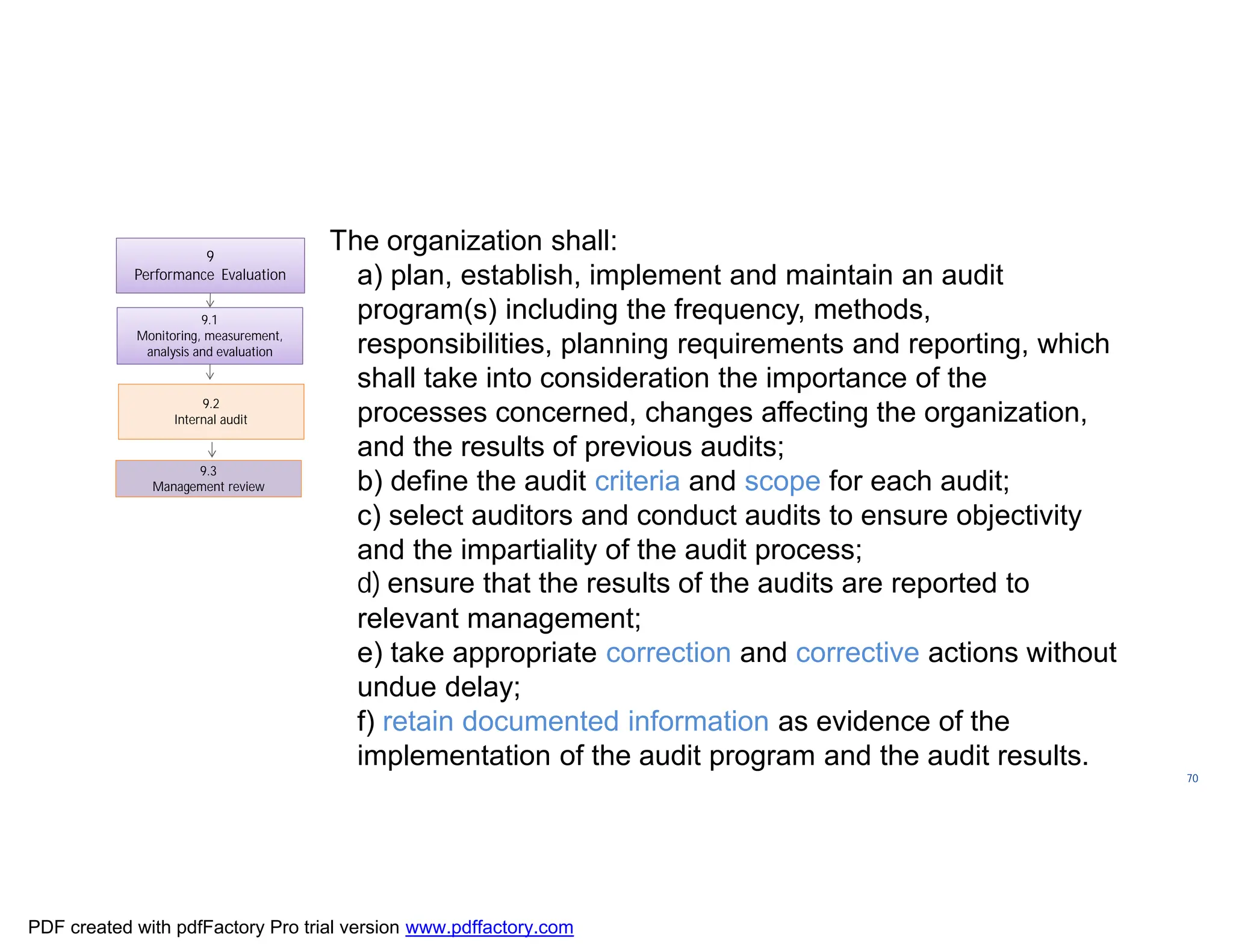
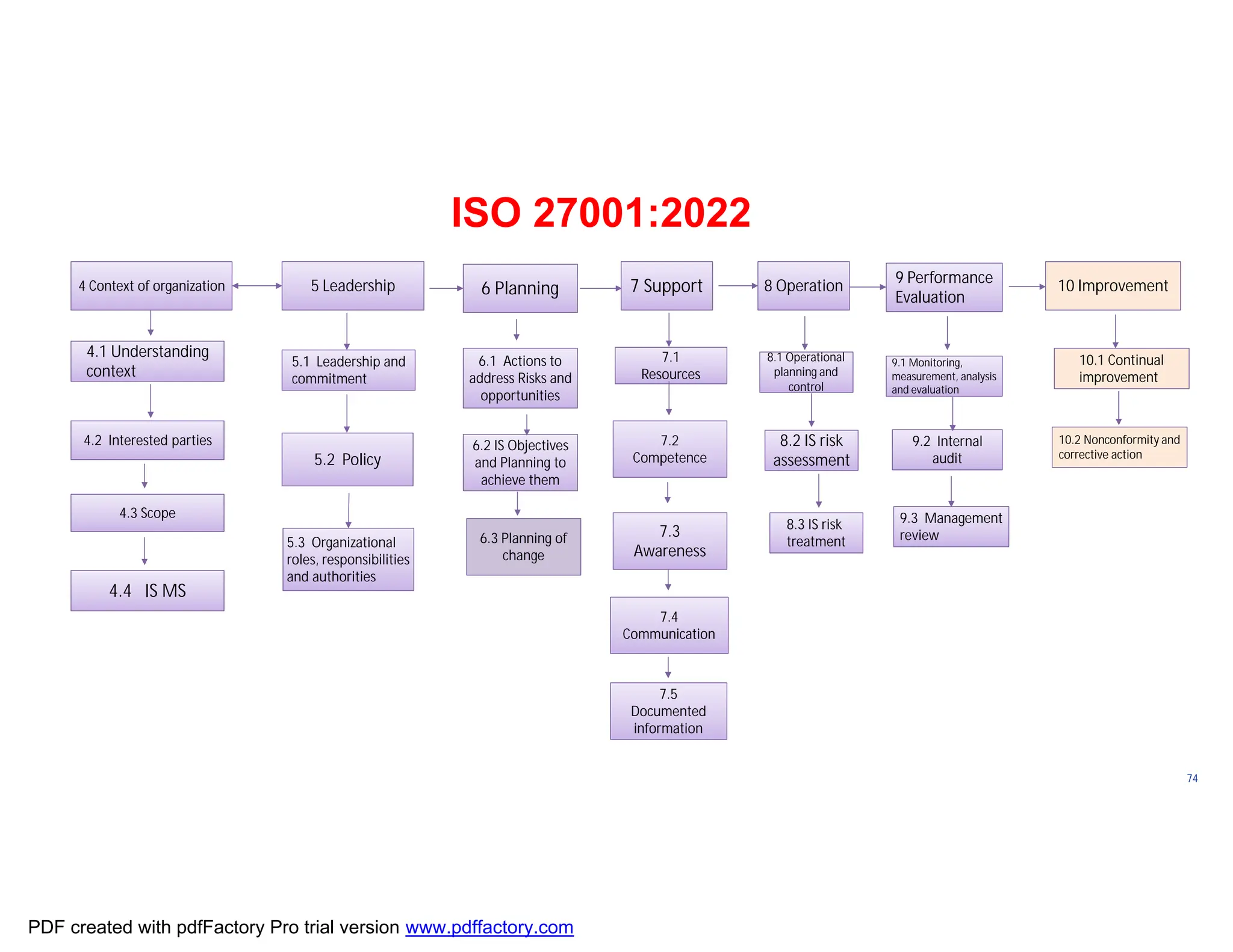
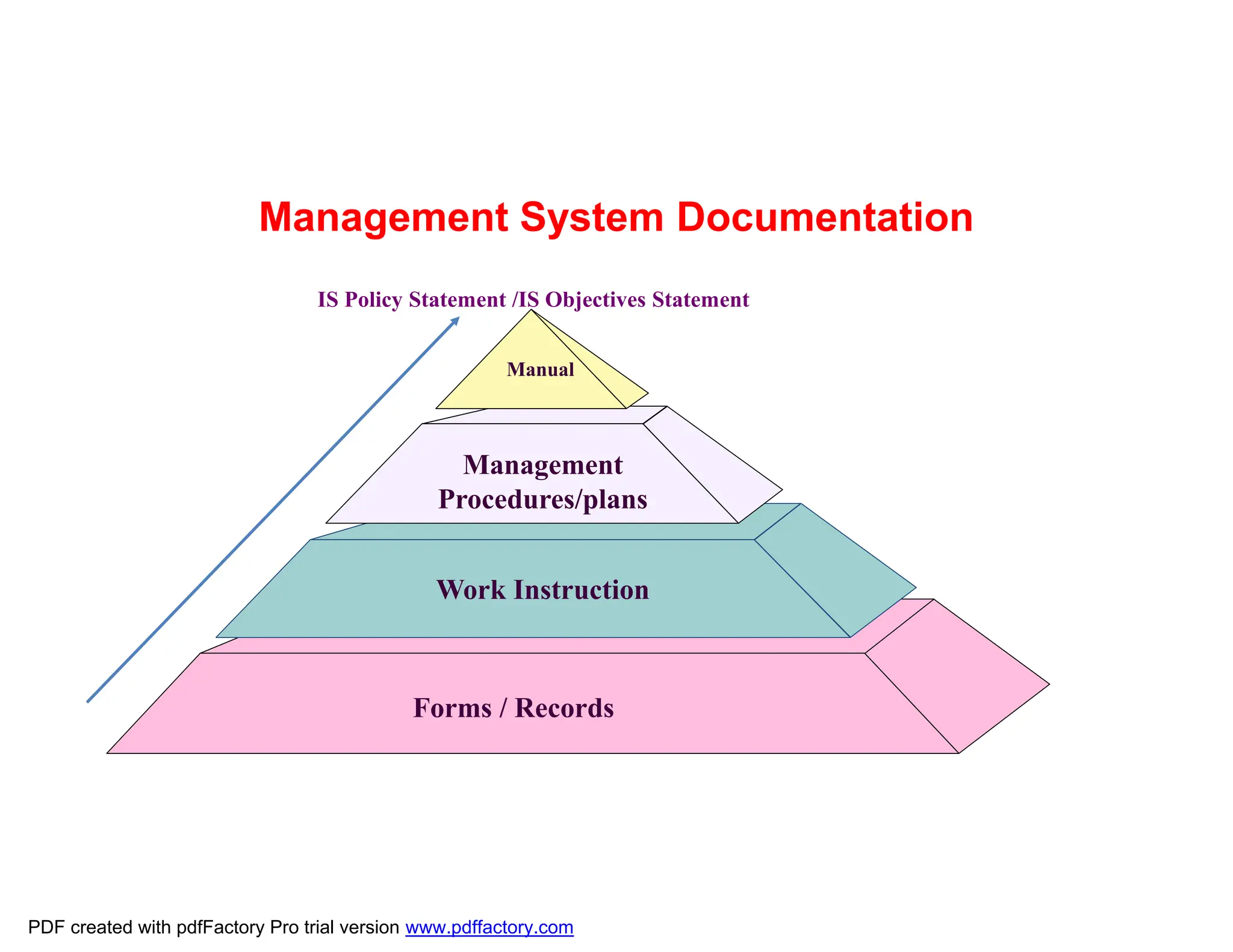
The document discusses the key aspects of implementing an Information Security Management System (ISMS) according to ISO 27001:2022 requirements. It covers the objectives of understanding ISMS, ISO 27001 requirements, and ISMS documents. It then explains important ISMS concepts like assets, threats, vulnerabilities, and security controls. The document outlines the ISO 27001 clauses and structure. Finally, it provides a roadmap for ISO 27001 implementation involving steps like understanding context, risk assessment, creating security policies and procedures, implementation, and monitoring.