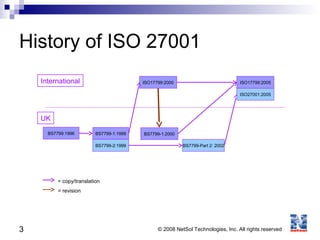
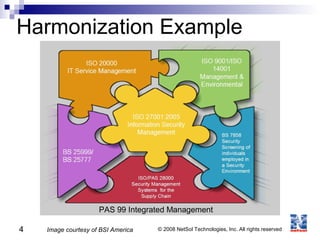
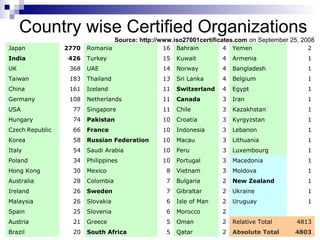
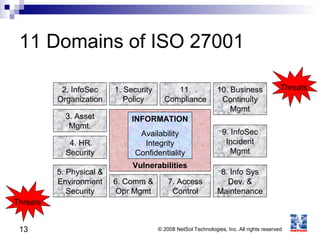
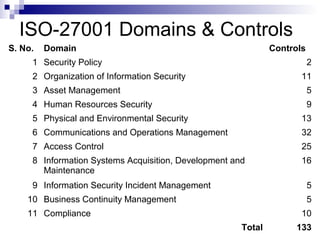
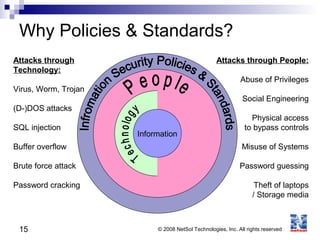
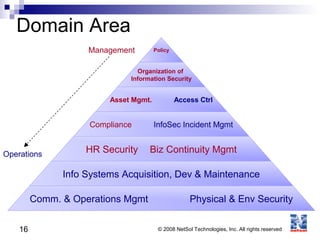
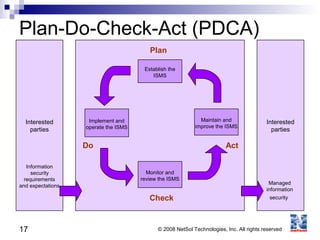
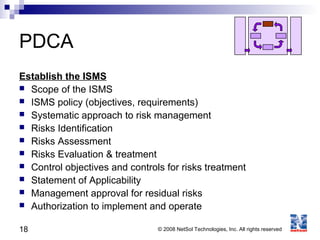
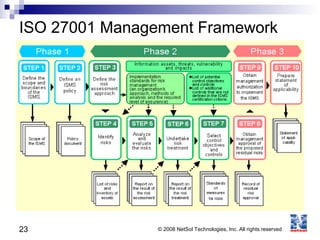
ISO 27001 is an information security standard that specifies requirements for an information security management system (ISMS). It contains 11 domains that describe 133 controls/countermeasures to manage vulnerabilities and threats to information. An organization implements an ISMS based on the Plan-Do-Check-Act cycle to establish, operate, monitor, maintain, and improve their information security system over time.