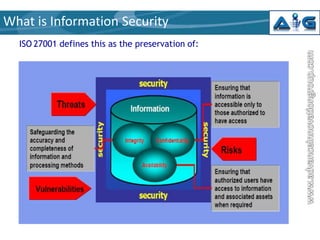
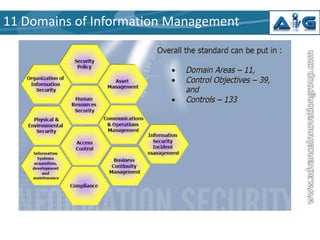
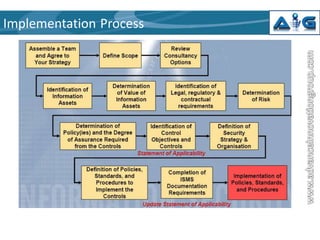
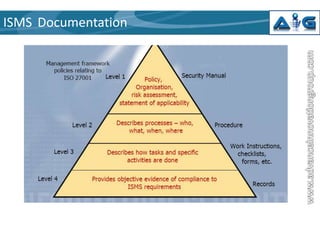
This document provides an introduction to ISO 27001, an internationally recognized standard for information security management. It defines information security as preserving the confidentiality, integrity and availability of information. ISO 27001 describes a structured methodology for establishing an Information Security Management System (ISMS) based on best practices. The standard takes a holistic approach, balancing physical, technical, procedural and personnel security controls. It outlines five mandatory requirements for an ISMS including management responsibility, internal audits, and management review. The standard also describes 11 domains of information security and the documentation required in an ISMS.