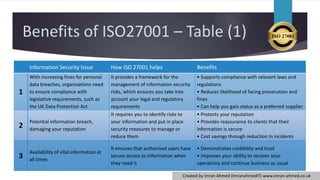
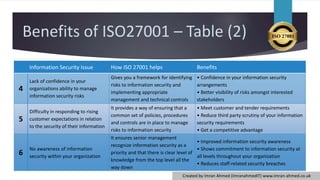
ISO 27001 is an international standard for establishing an information security management system (ISMS), providing a framework for managing information risk and ensuring compliance with legal requirements. The certification enhances organizational credibility, helps protect against data breaches, and fosters confidence in information security practices. The document also outlines related standards, including ISO 27002, which details best practices for security controls.