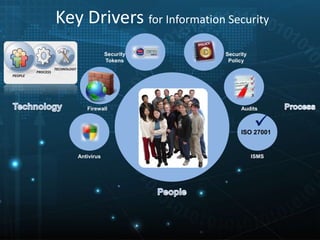
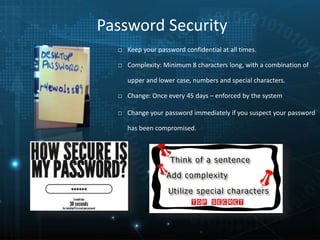
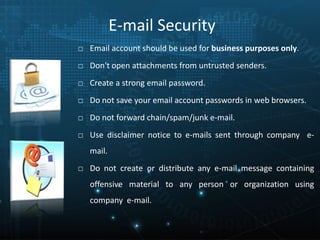
This document provides an overview of information security awareness training based on ISO/IEC 27001:2013. It discusses what information is, the key aspects of information security including confidentiality, integrity and availability. It then outlines various practices for maintaining confidentiality, integrity and availability such as access controls, backups and policies. The document also discusses the benefits of information security, key drivers, why security breaches occur, and important security topics for end users including policies, asset classification, physical security, passwords and more.