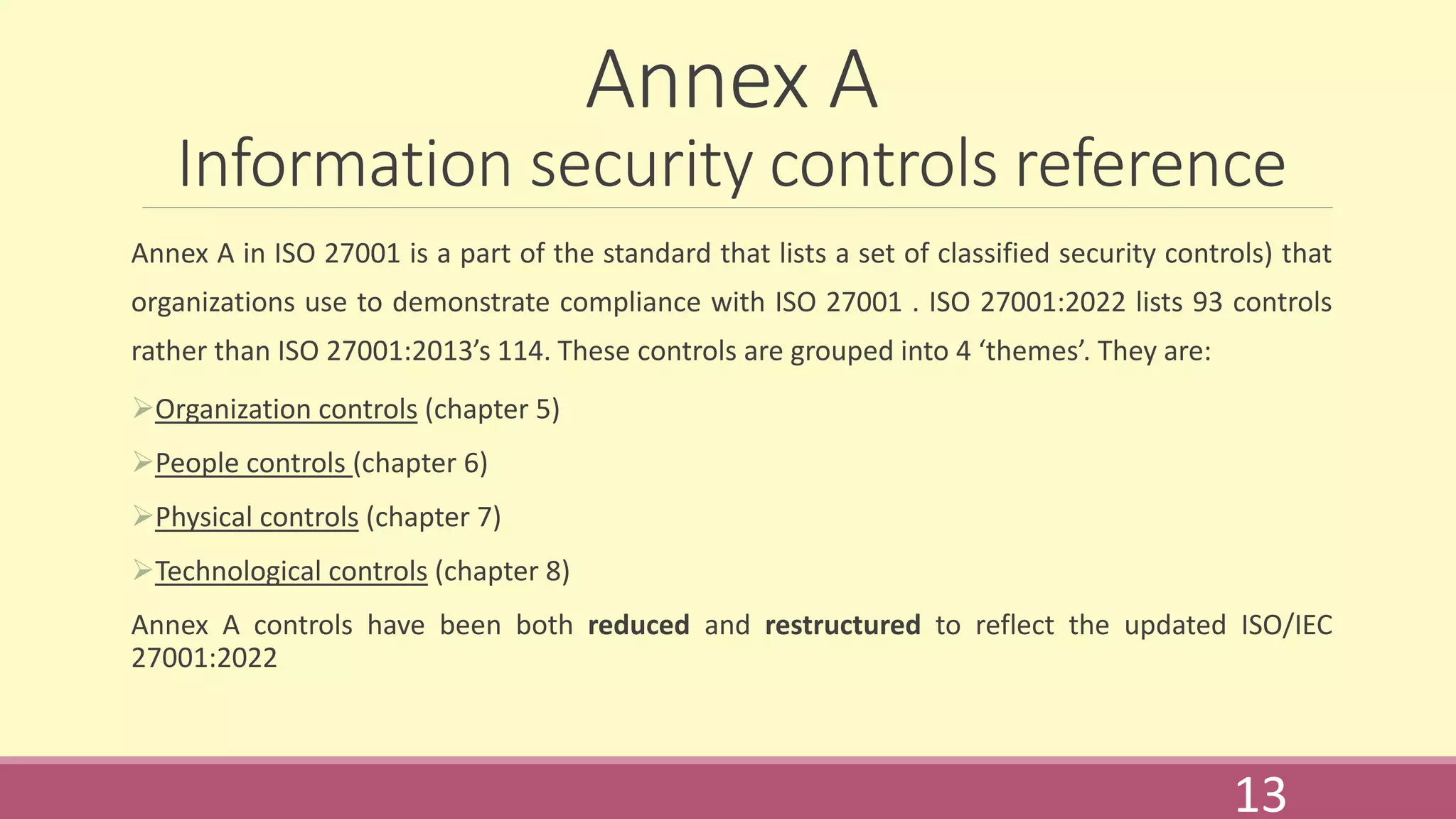
ISO 27001 is the central standard for information security management systems (ISMS). It provides requirements and implementation guidance for organizations to manage risks to security assets. The standard outlines requirements for establishing the scope of the ISMS, leadership responsibilities, risk assessment and treatment processes, resource management, and continual improvement. It includes an annex that lists 93 controls across organizational, people, physical and technological categories that can be used to demonstrate compliance. The 2022 version updates and restructures some controls to better reflect risk-based approaches.