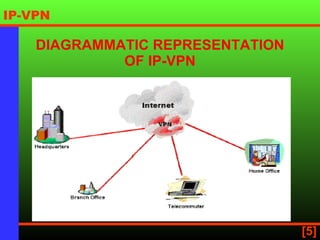
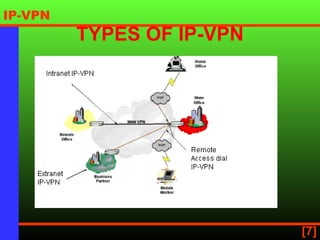
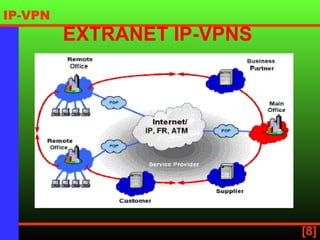
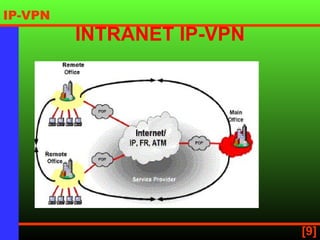
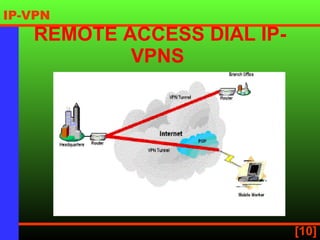
An IP virtual private network (IP VPN) uses a public network like the internet to securely extend a company's internal IP network. It provides secure, scalable connectivity as a more cost-effective alternative to a private wide area network. IP VPNs allow flexible options for intranet, extranet, and remote access connections between multiple sites and remote users. When choosing an IP VPN provider, considerations include security, reliability, availability, scalability, and flexibility.