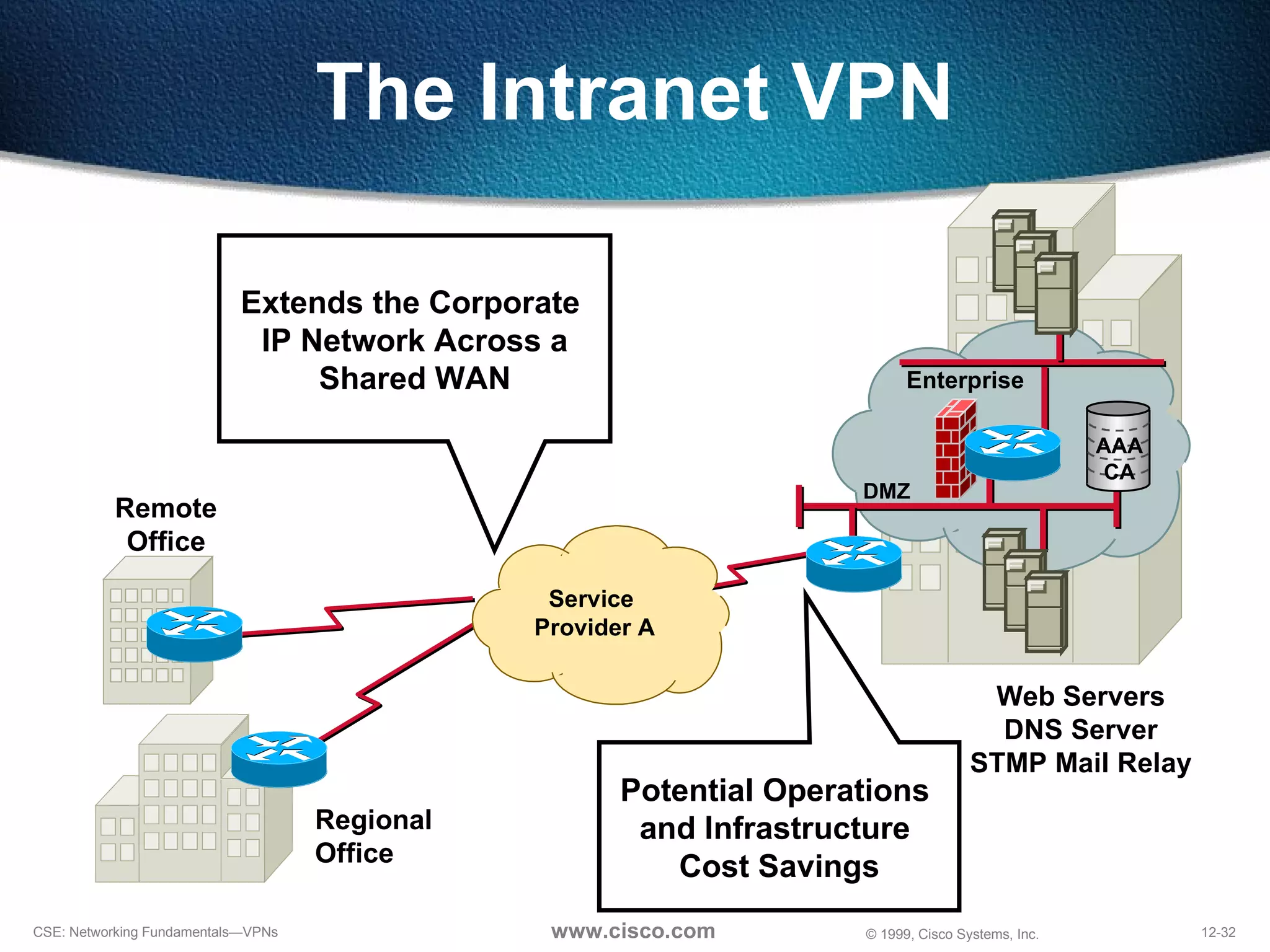
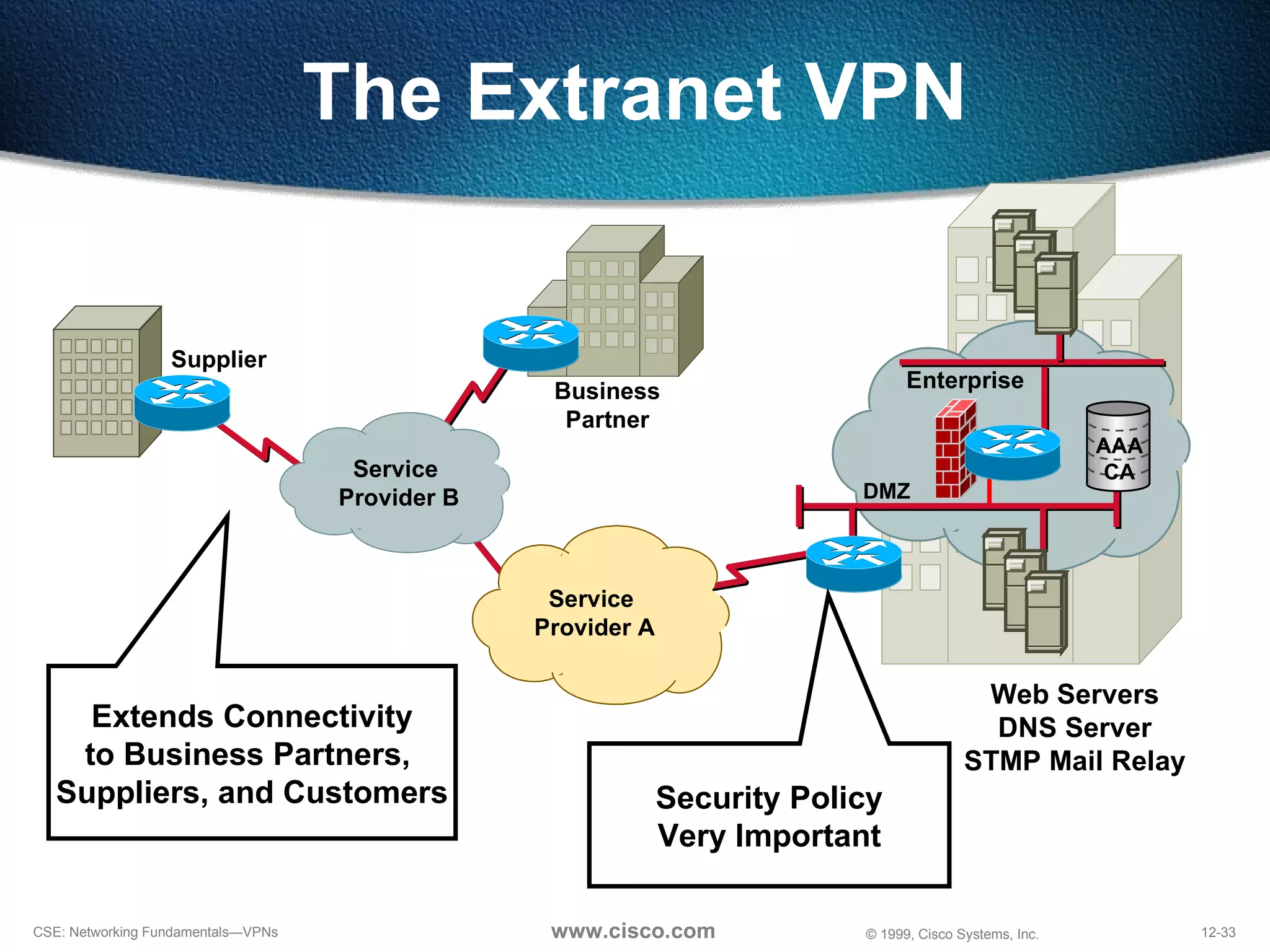
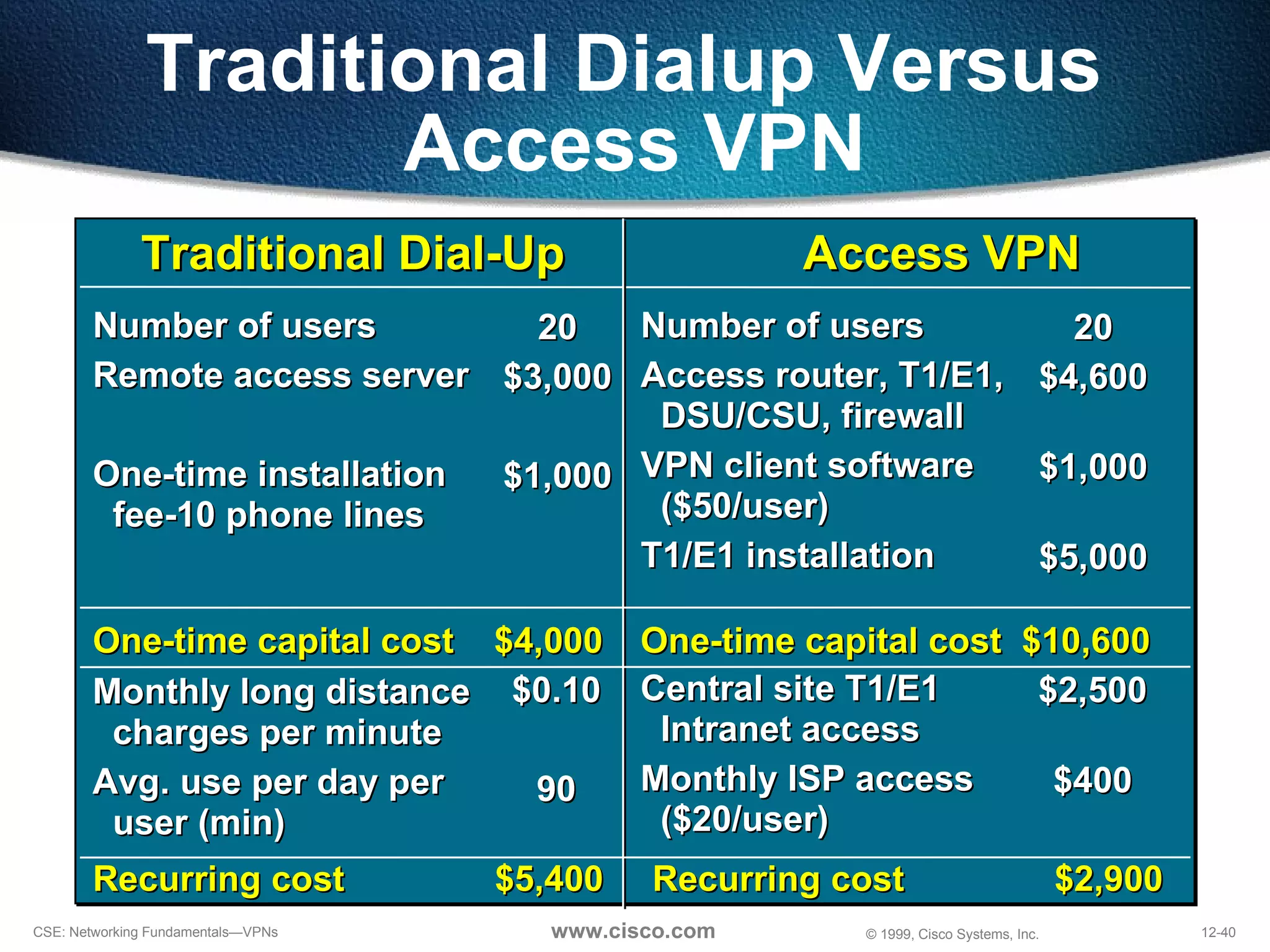
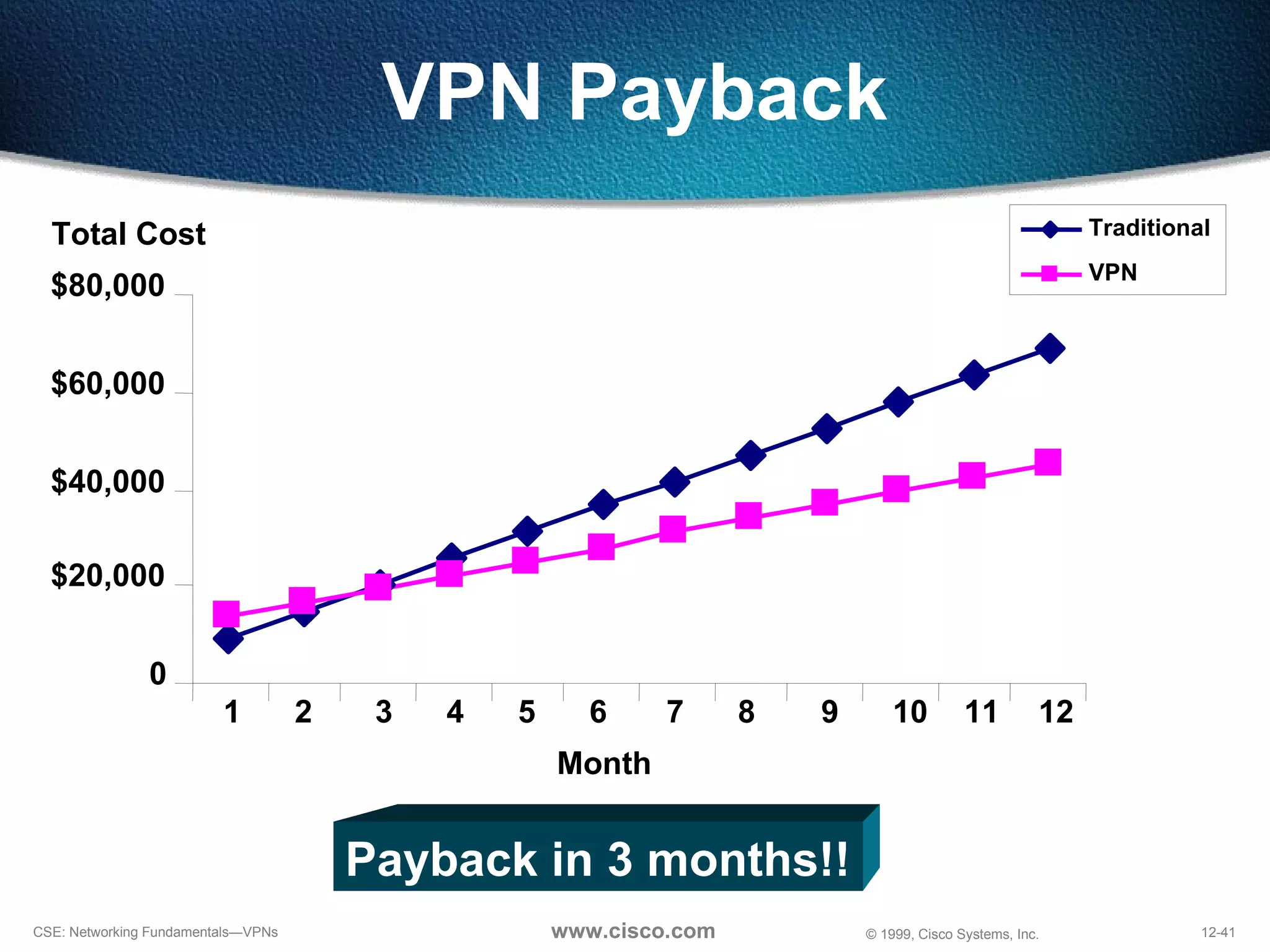
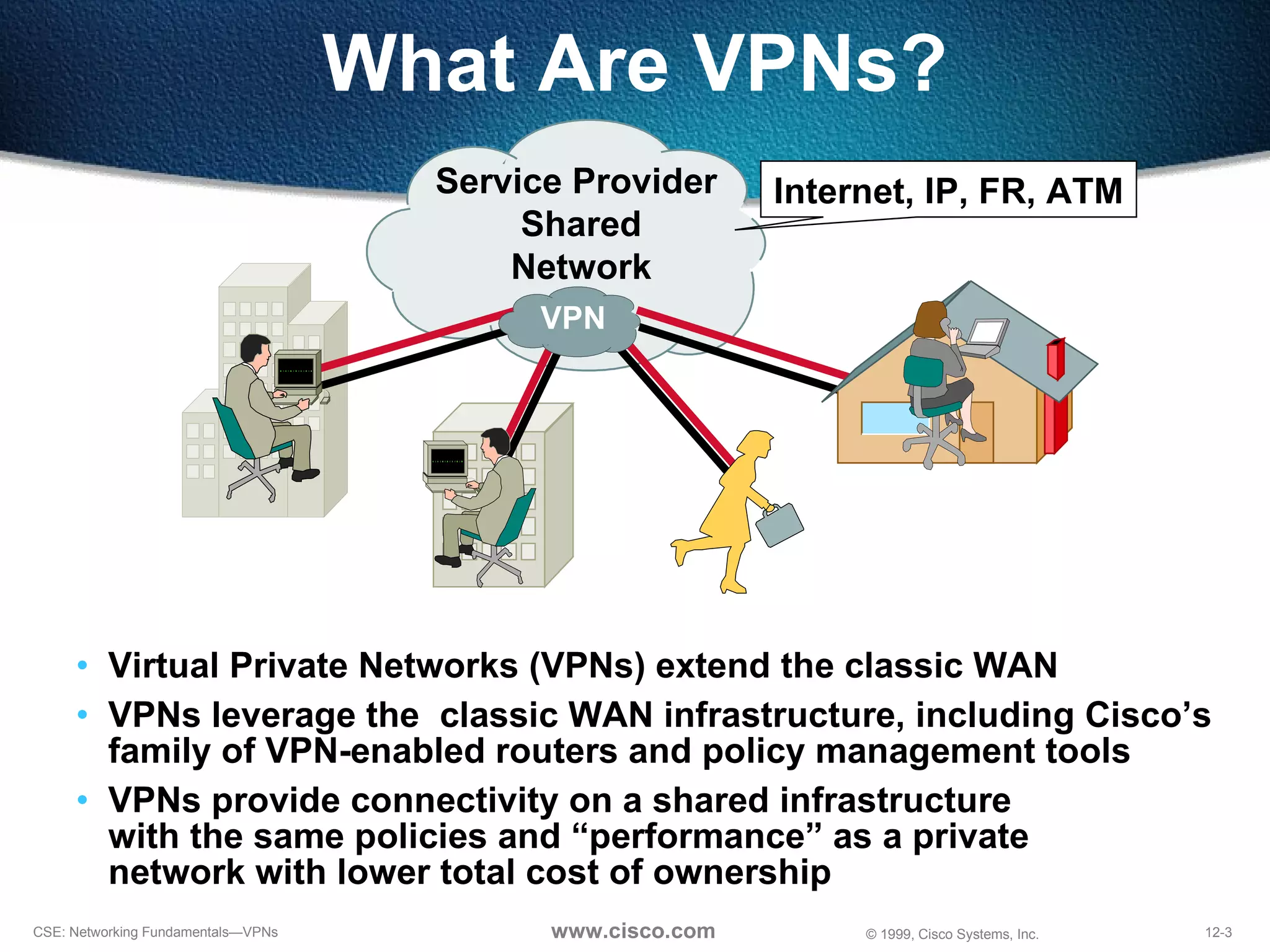
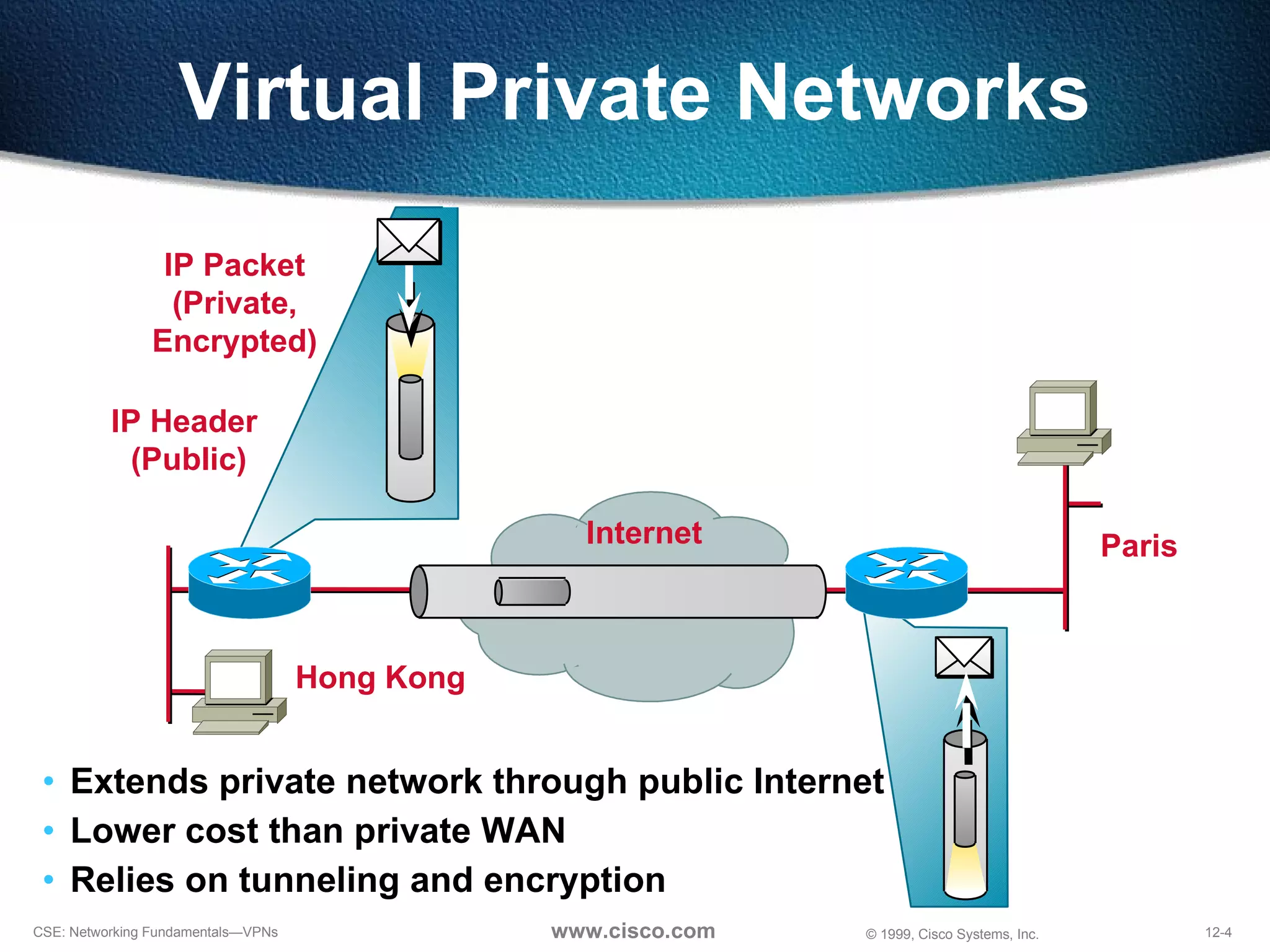
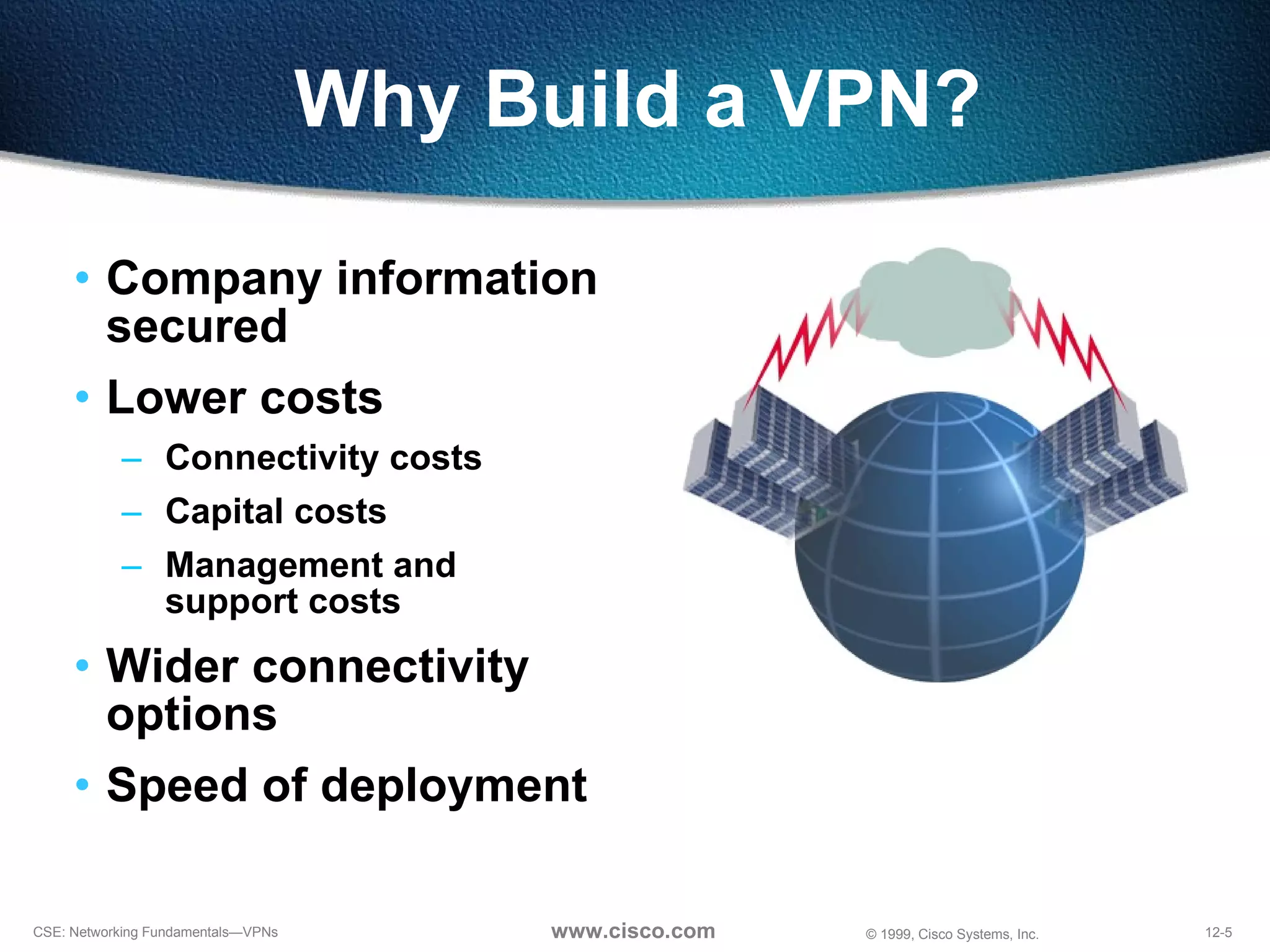
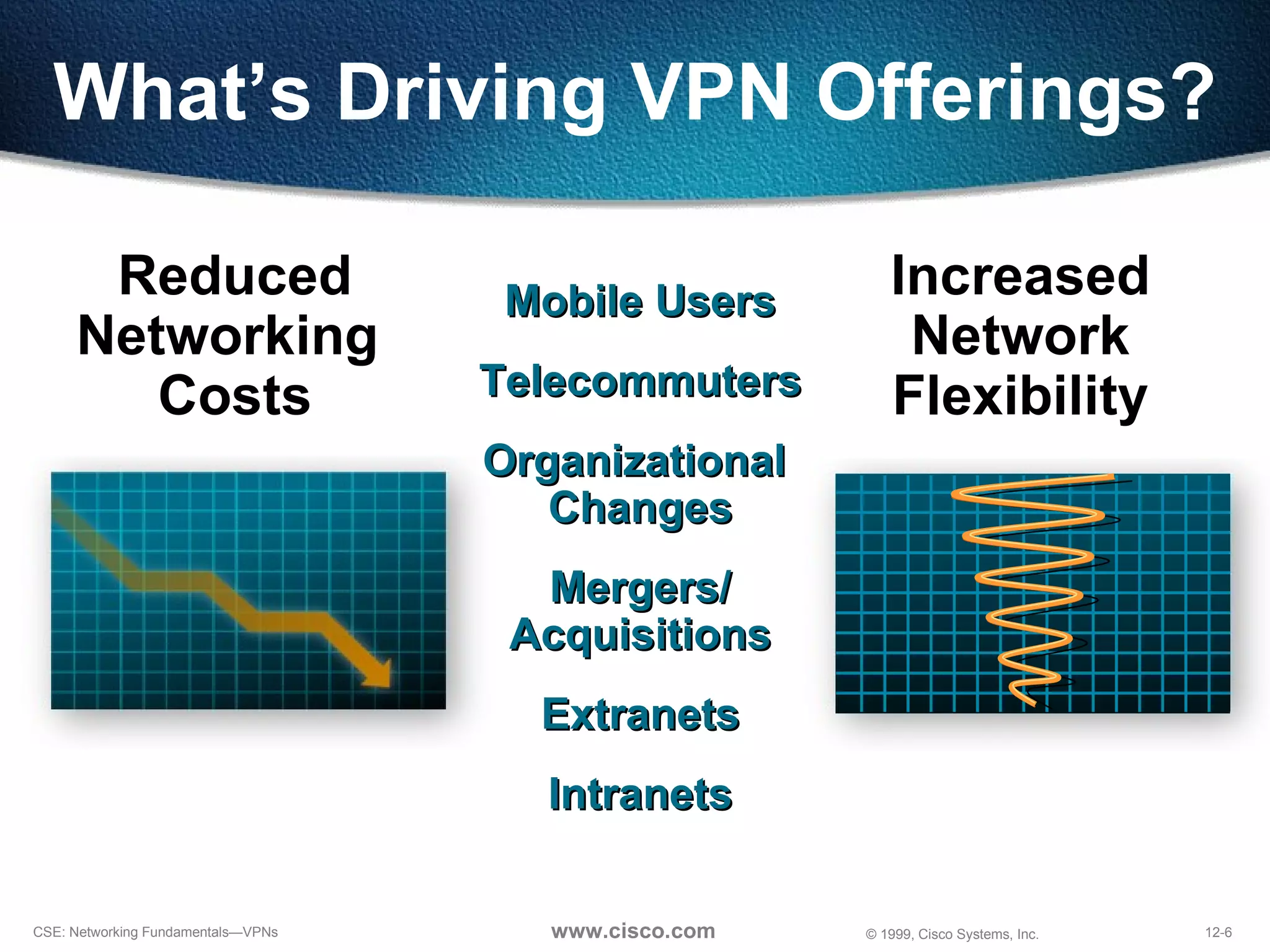
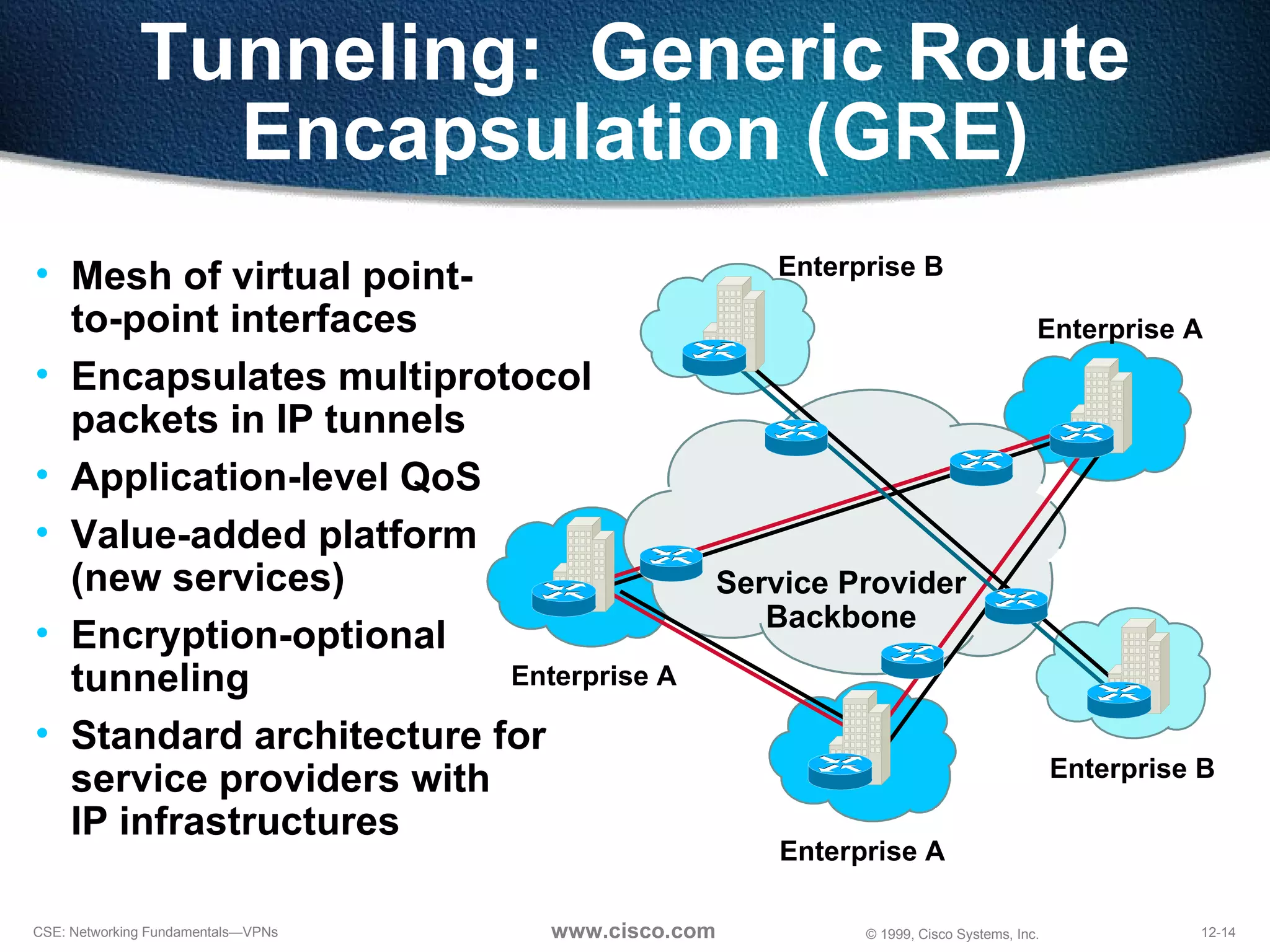
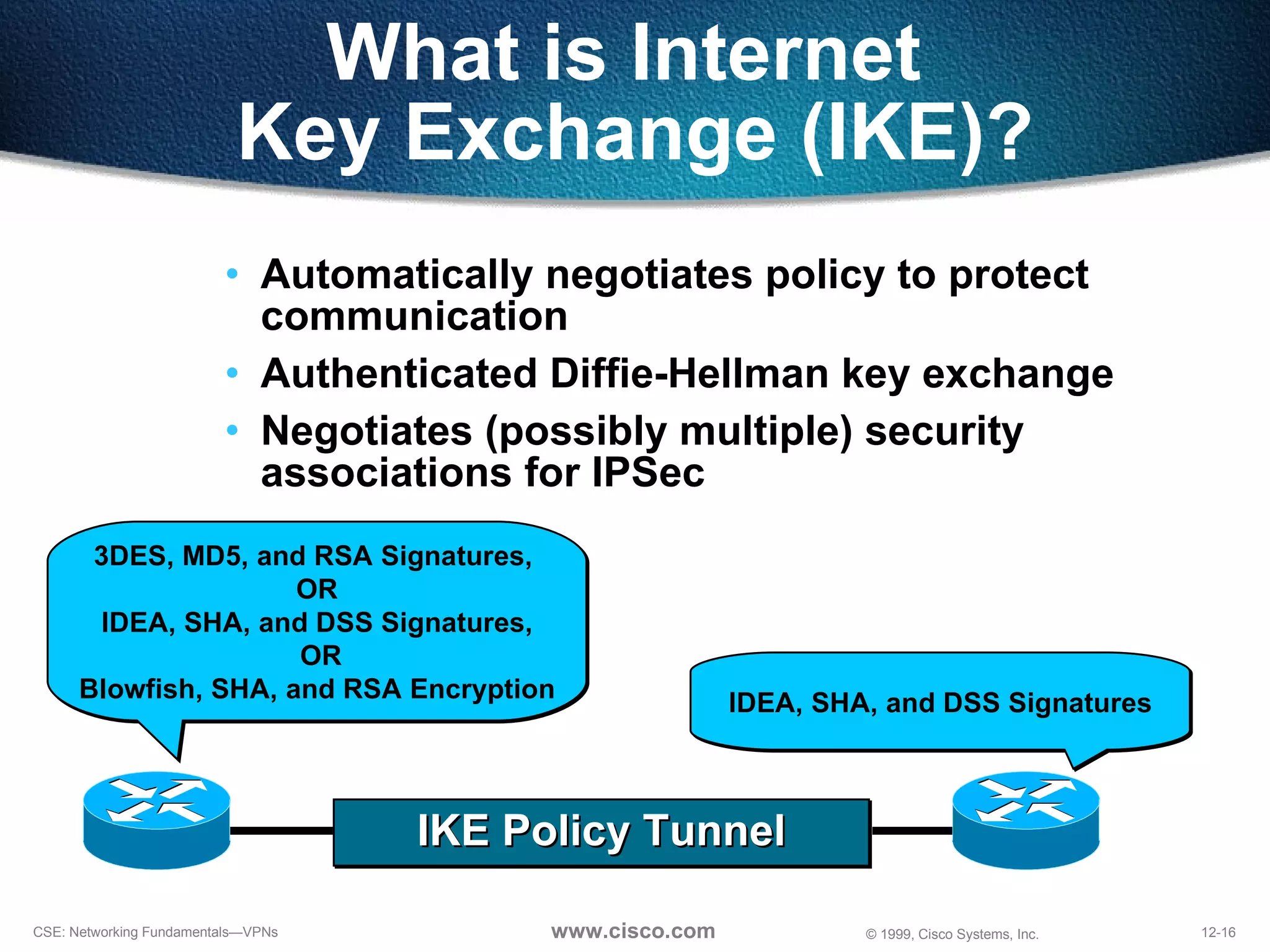
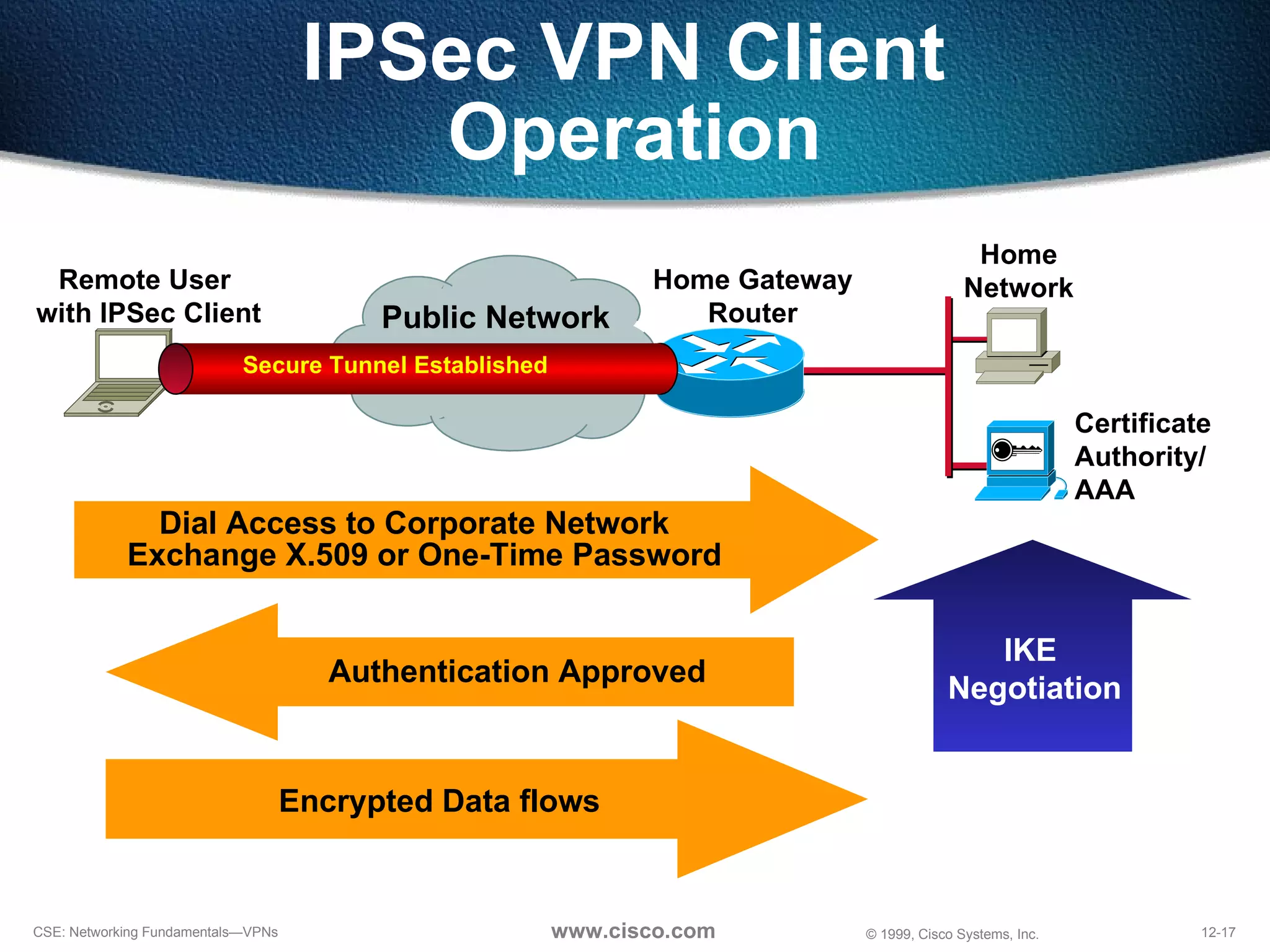
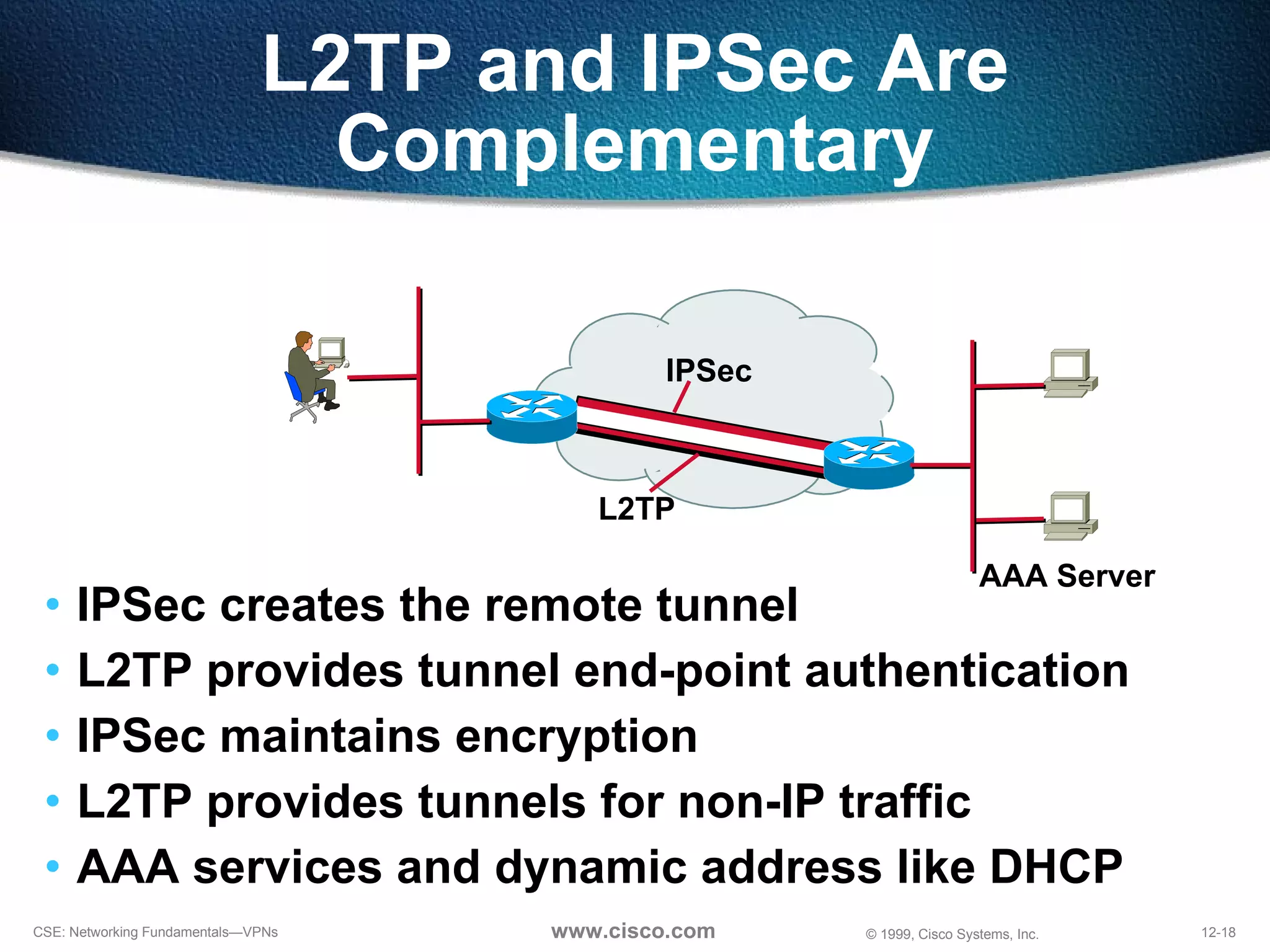
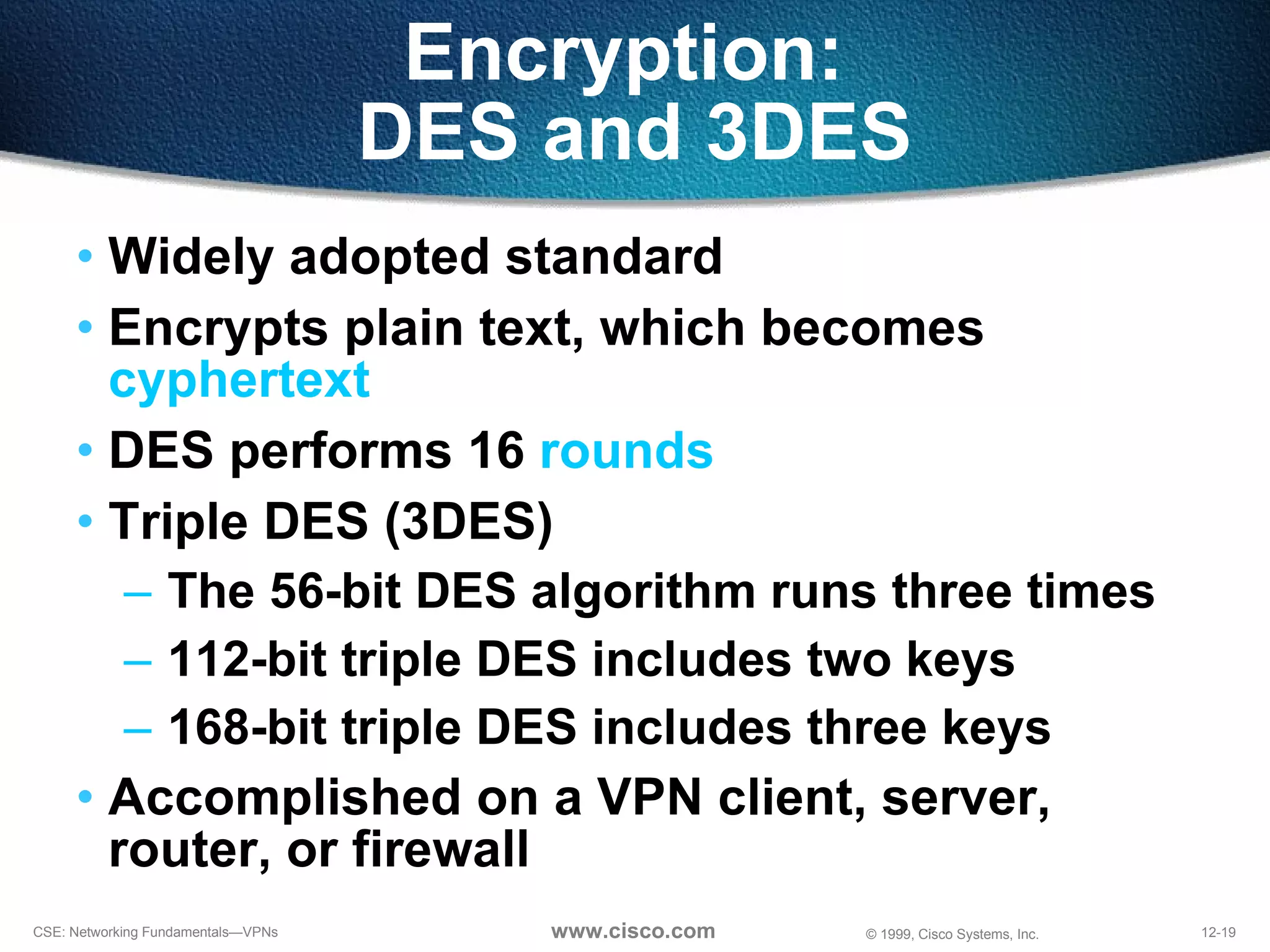
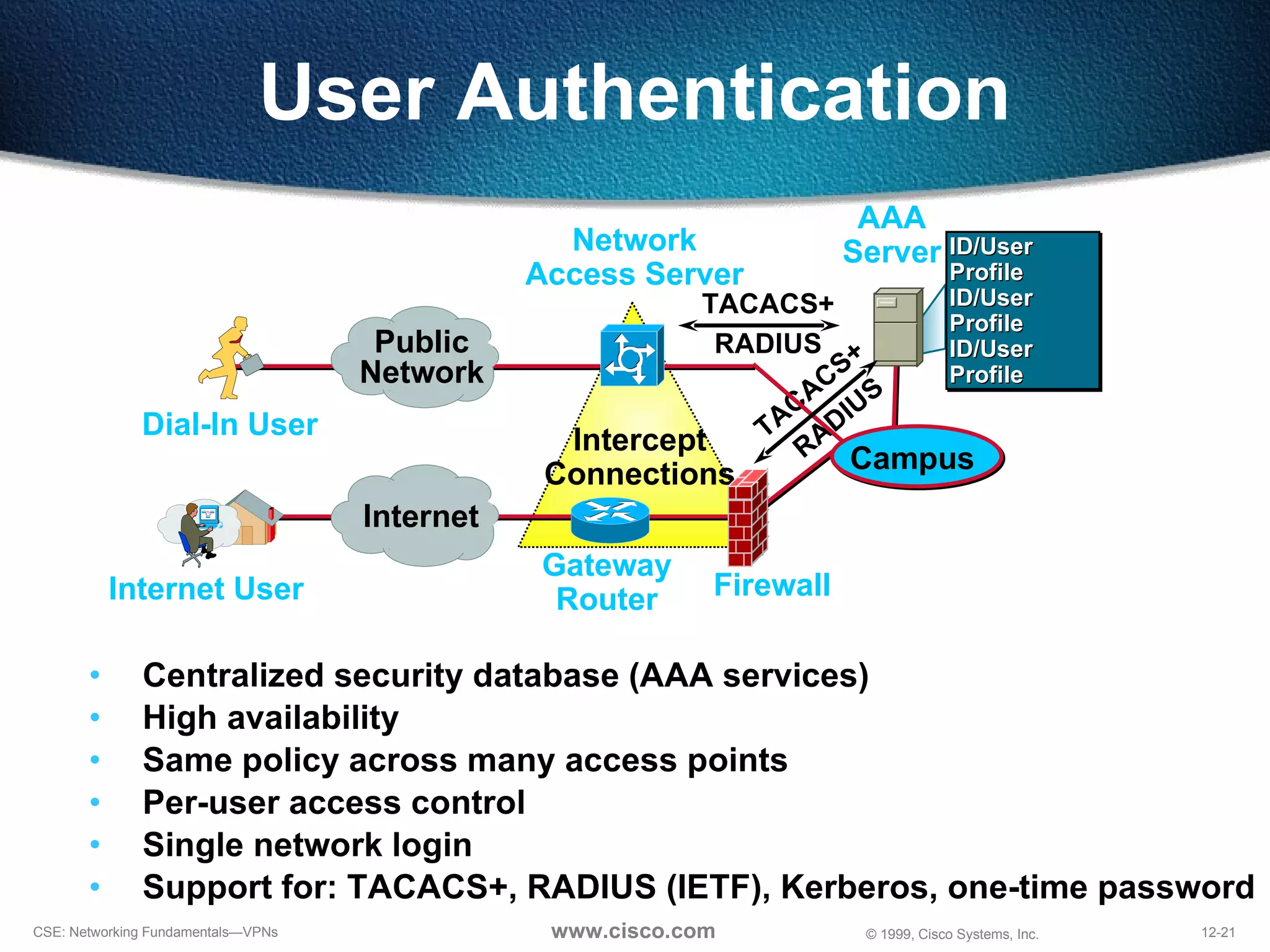
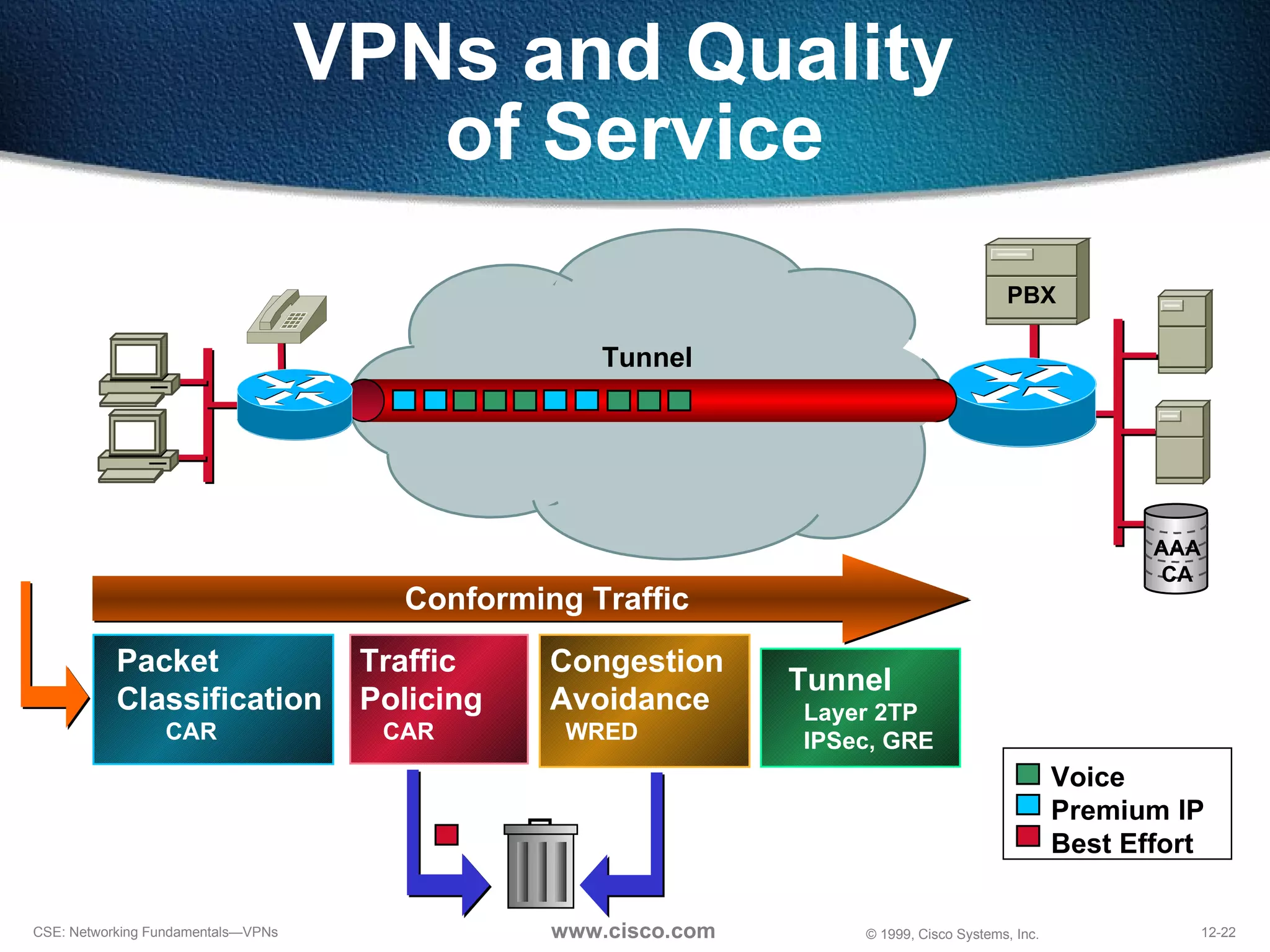
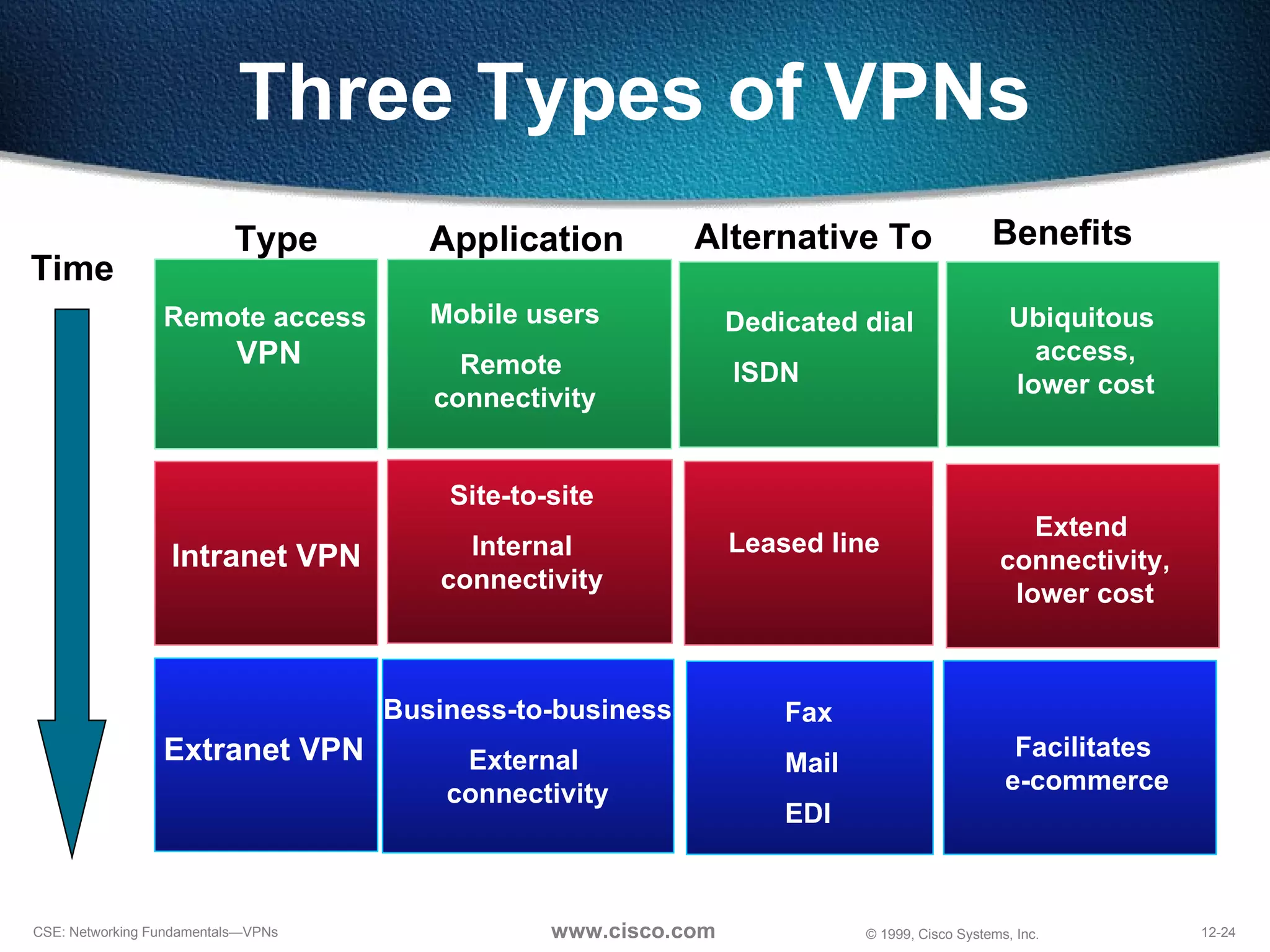
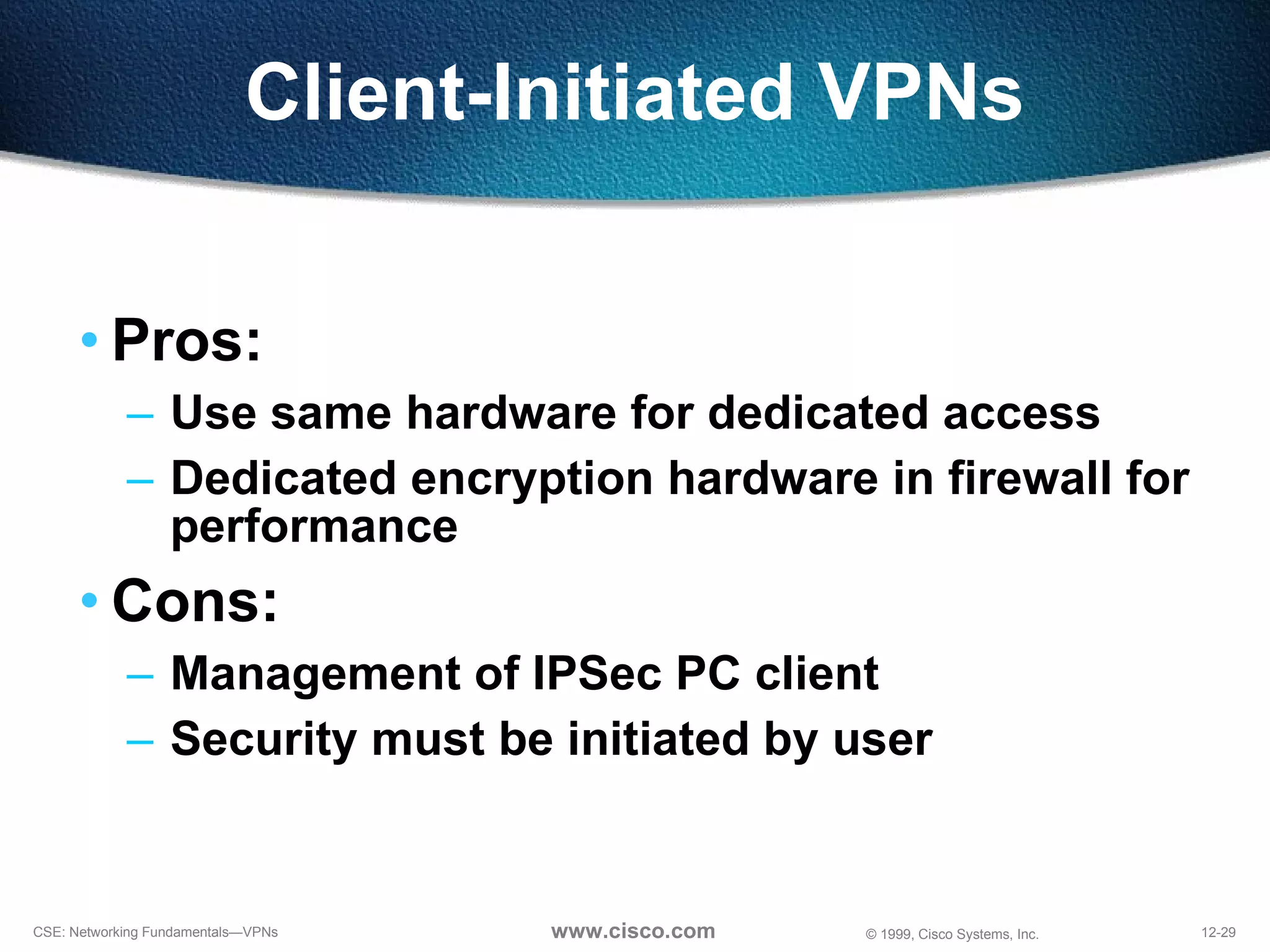
VPNs extend private networks over shared public infrastructure like the internet. VPNs use encryption and tunneling to provide secure connectivity similar to a private network but at lower cost. Common VPN types include remote access VPNs for mobile users, intranet VPNs for connecting multiple company sites, and extranet VPNs for connecting to business partners. VPNs can reduce networking costs and improve flexibility while maintaining security.






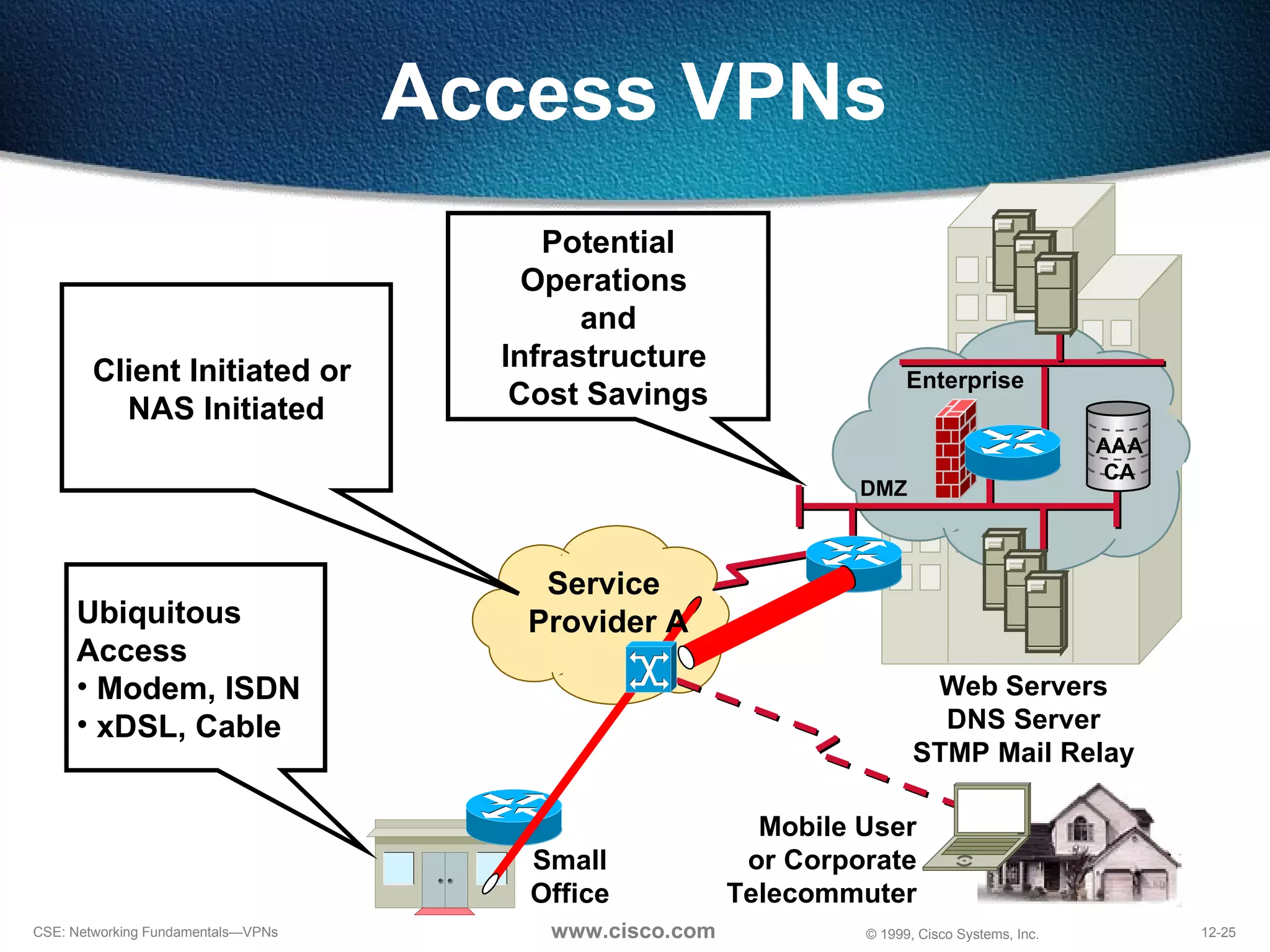
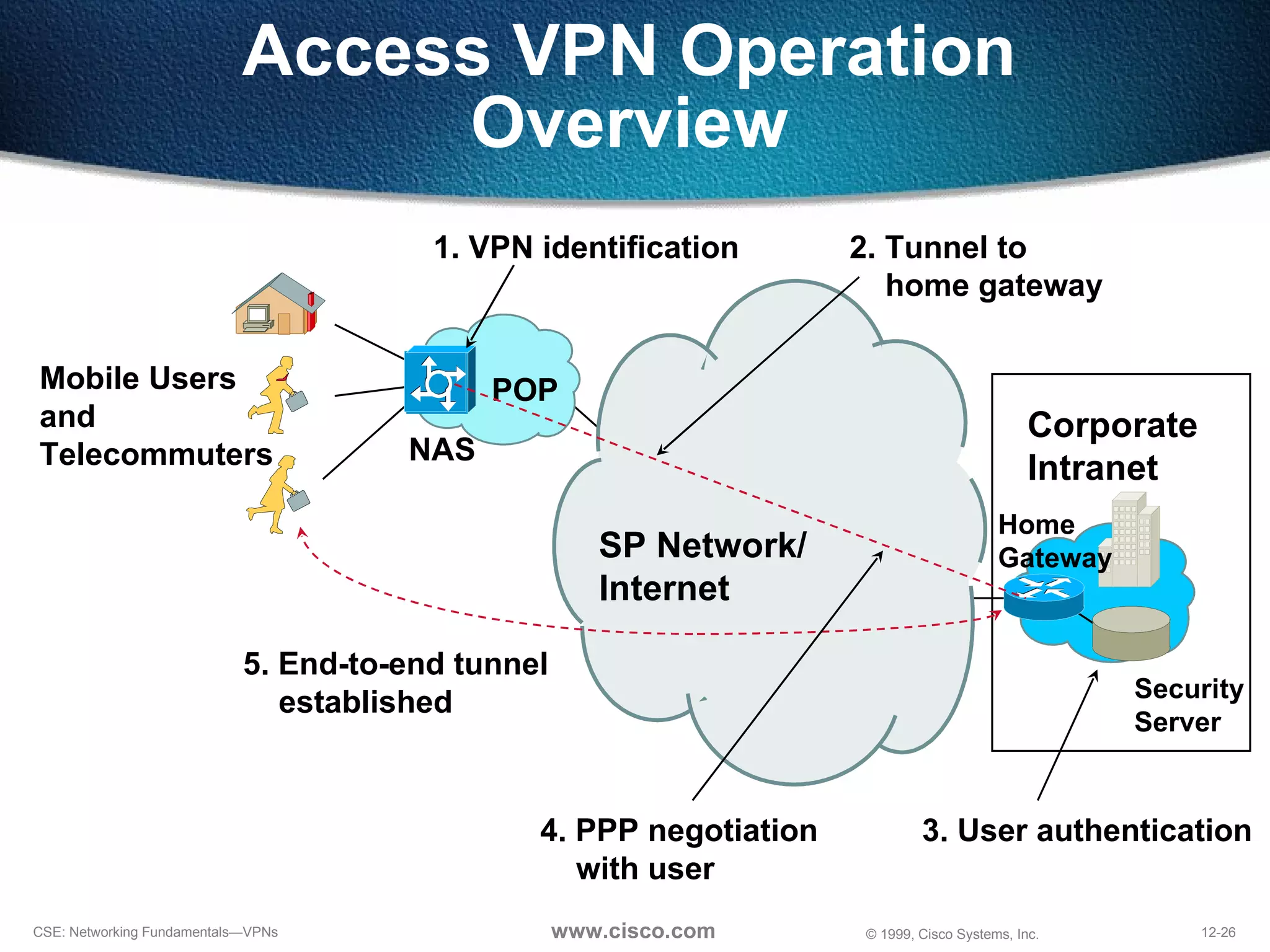
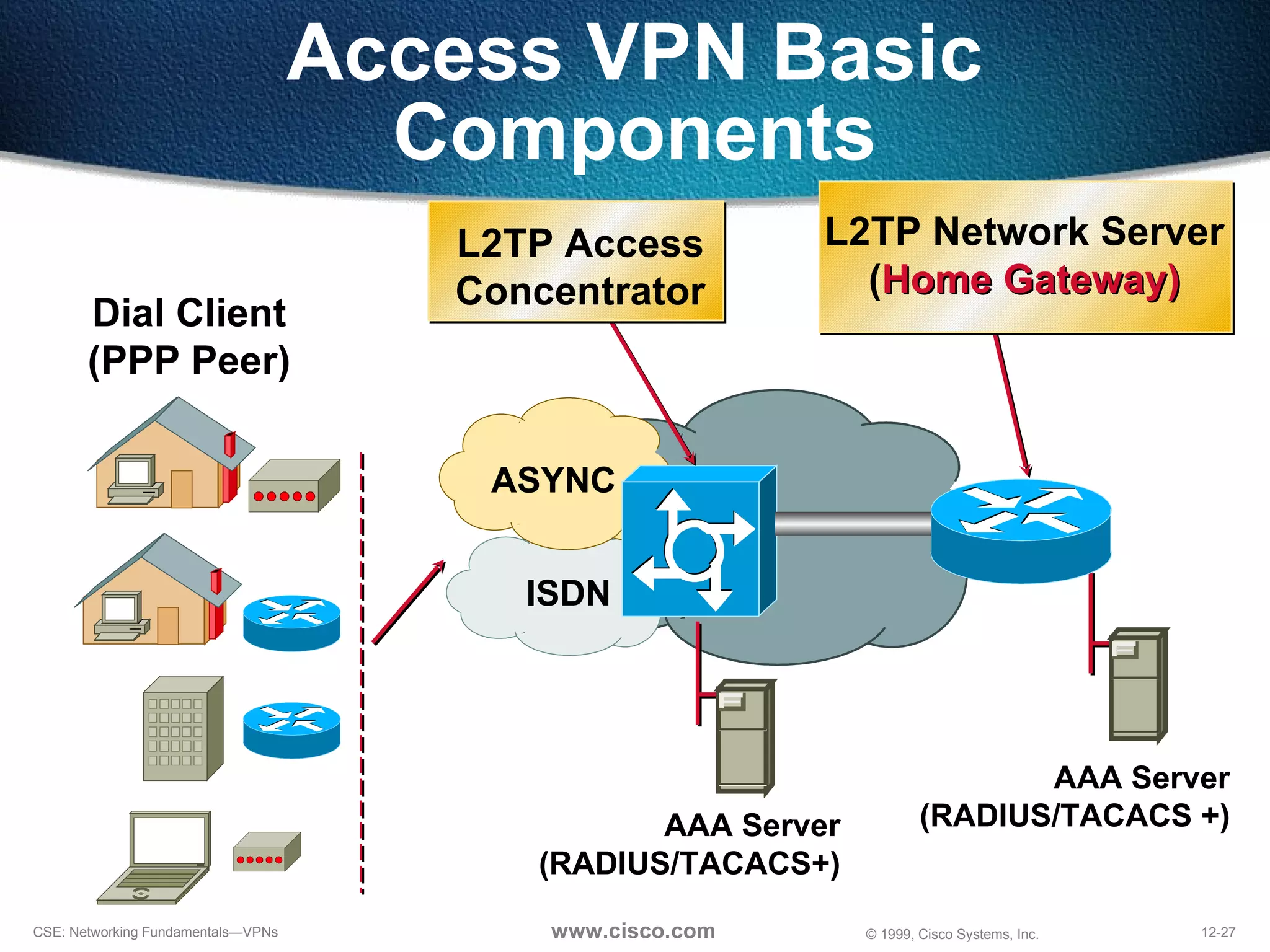
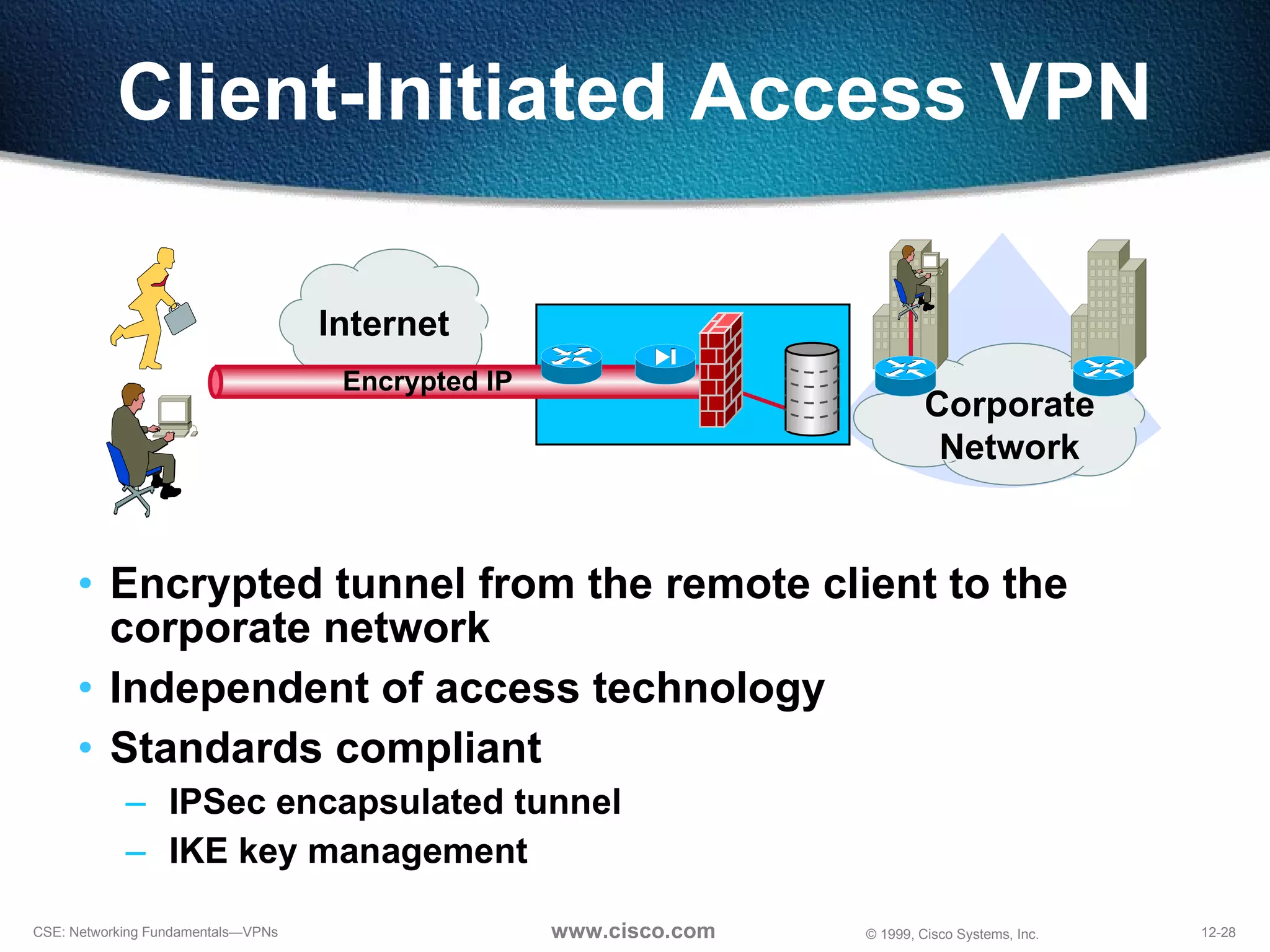
![NAS-Initiated Access VPN NAS [email_address] Home Gateway IP Network](https://image.slidesharecdn.com/12understandingvpns-1243495143-phpapp02/75/12-Understanding-V-P-Ns-30-2048.jpg)