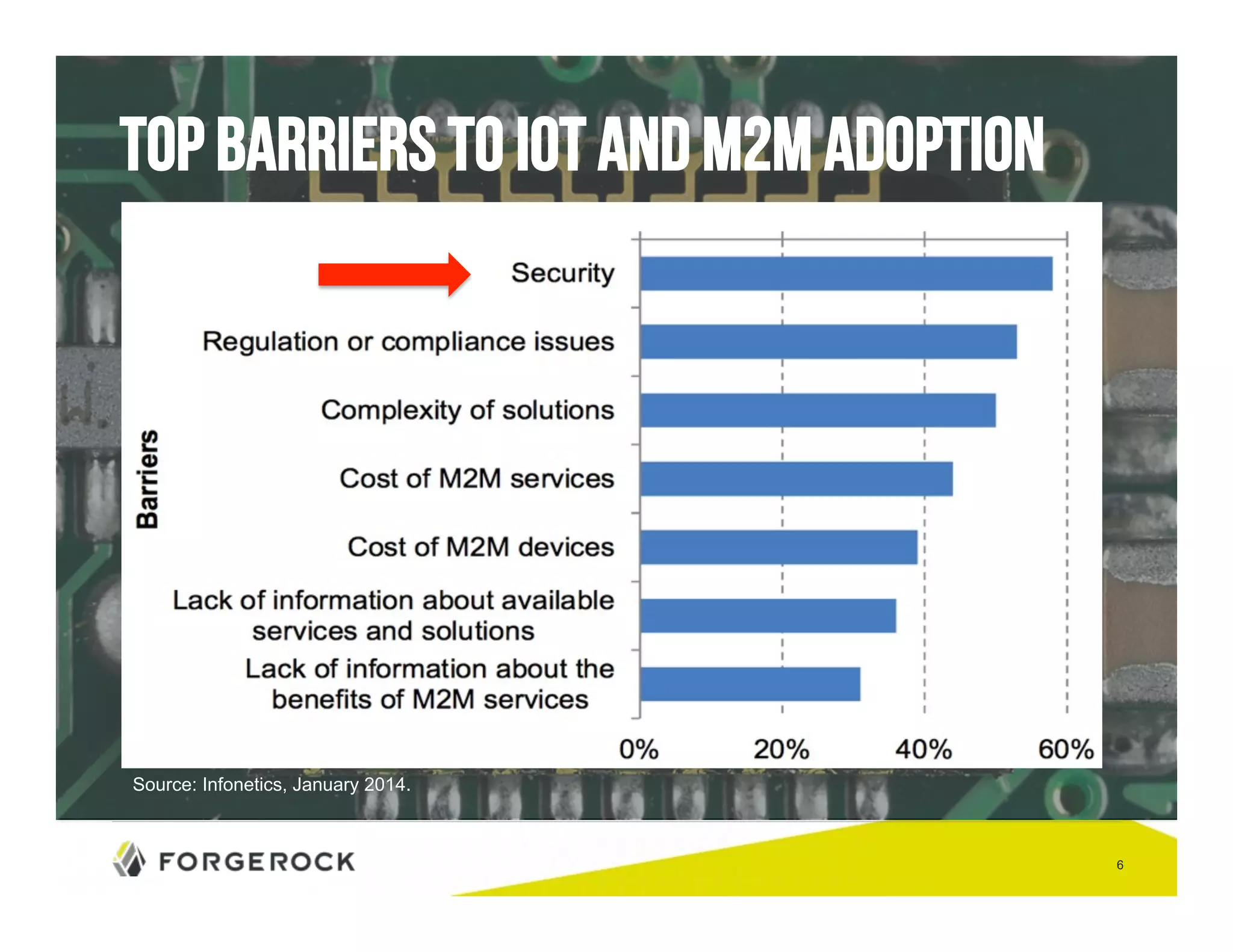
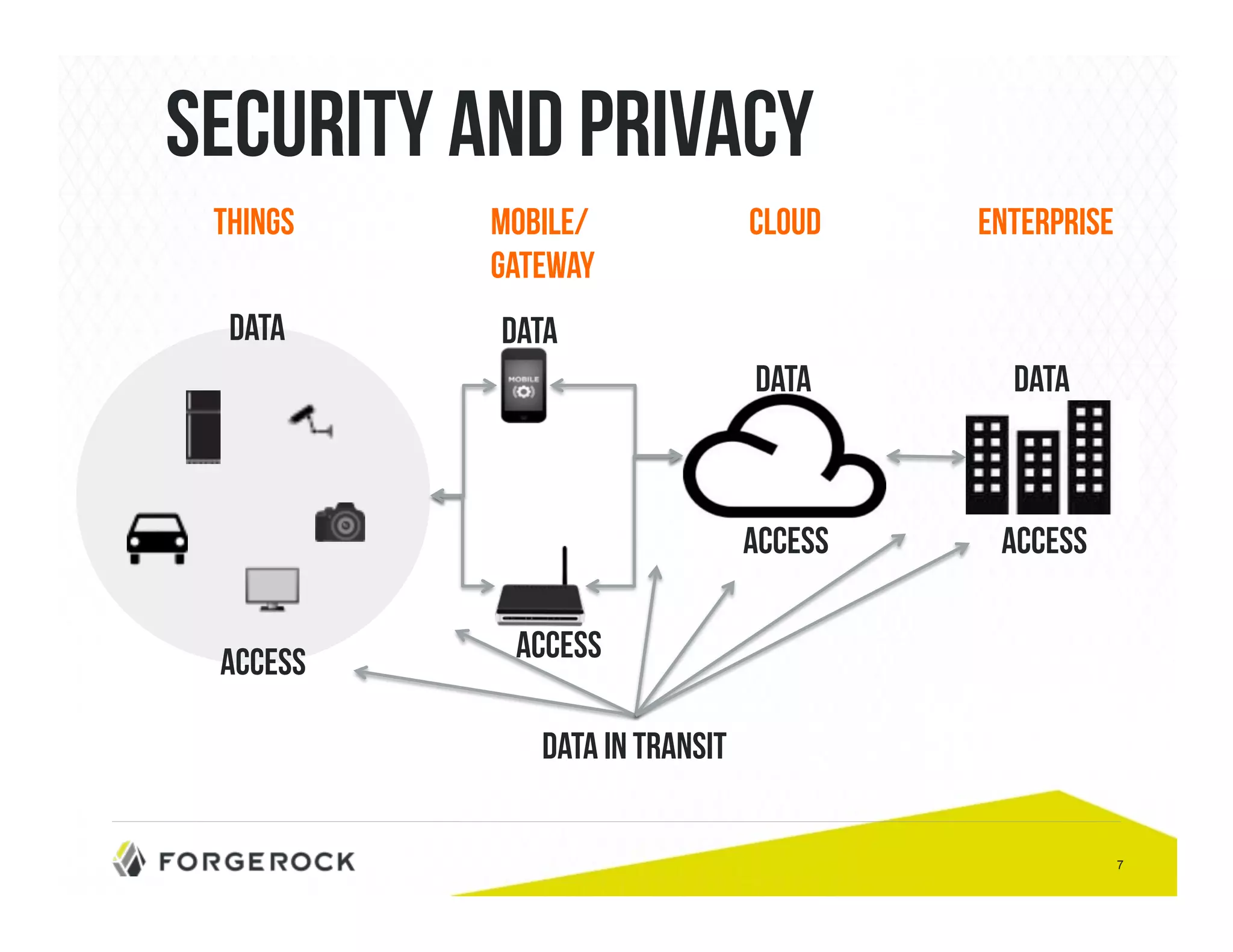
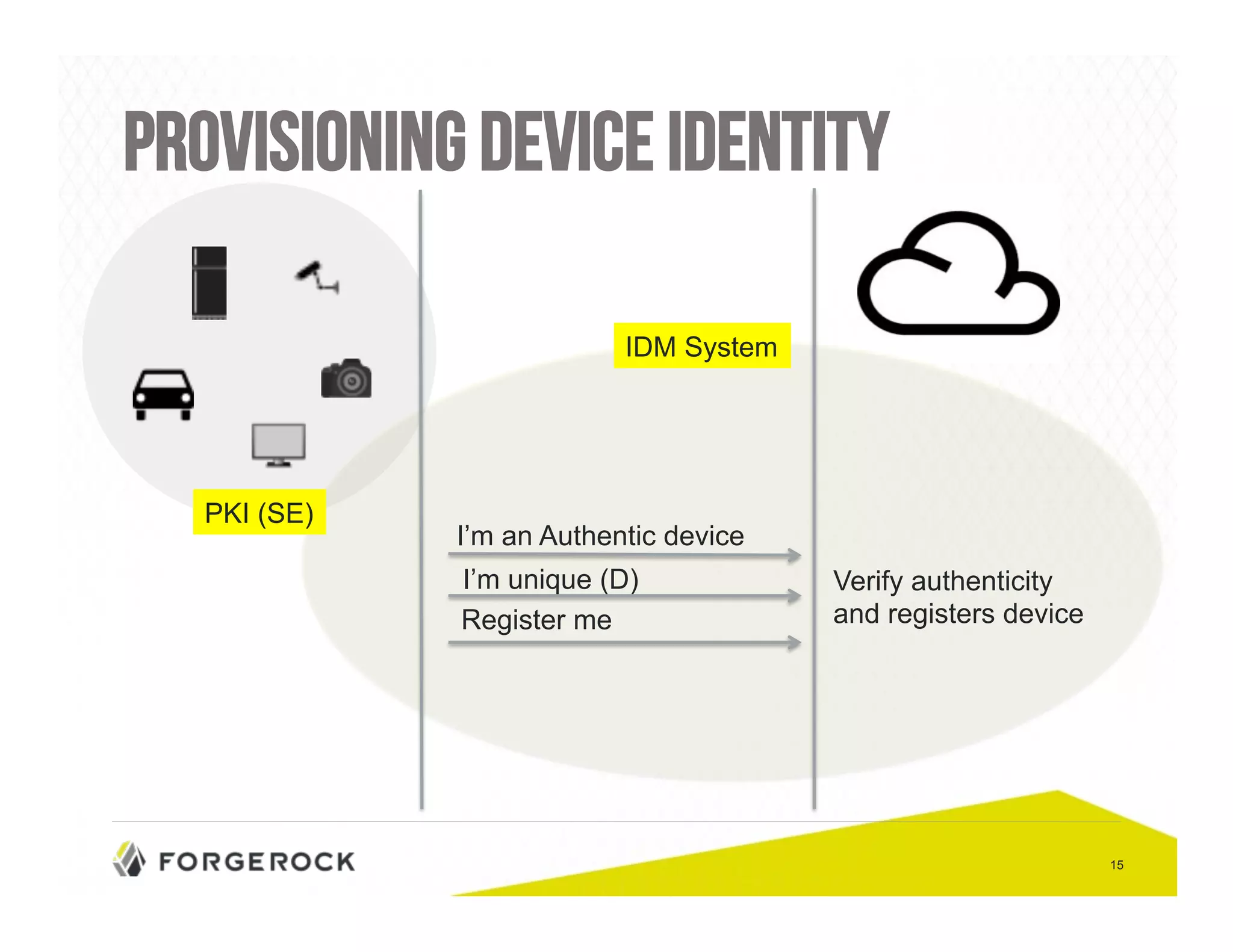
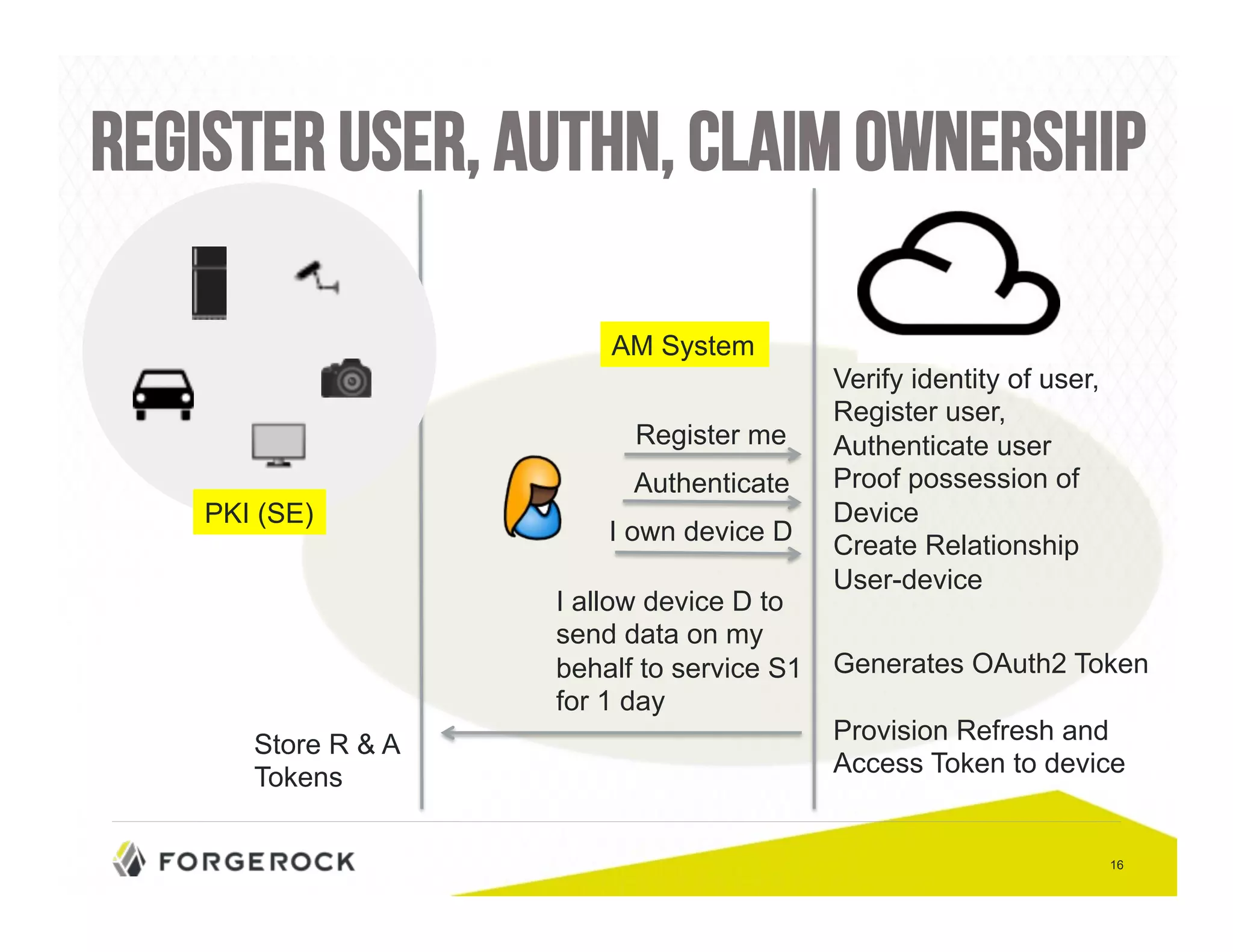
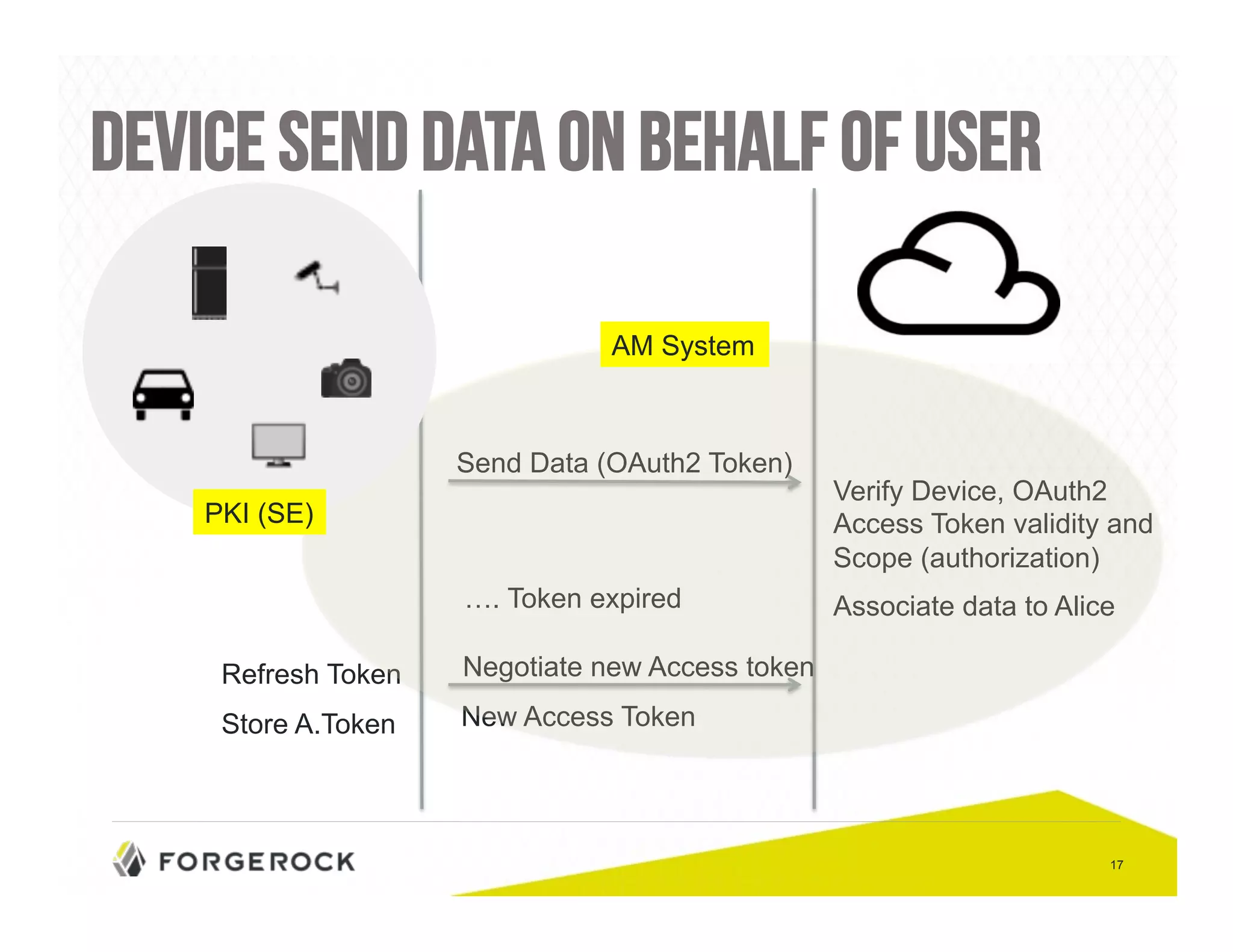
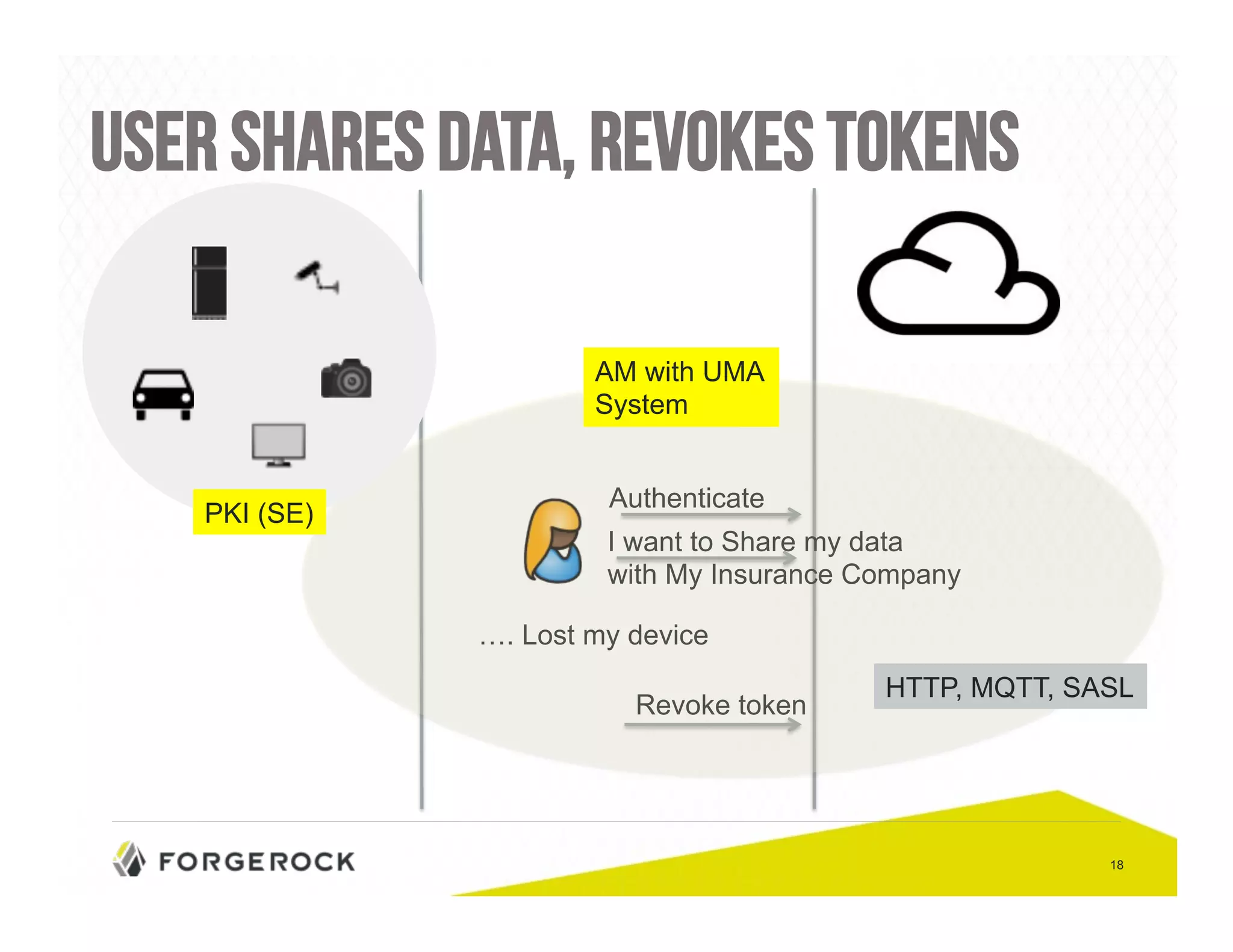
The document outlines security challenges and design principles in the Internet of Things (IoT) space, emphasizing the importance of integrating security from the outset. It highlights common security issues, data handling, and the need for effective identity and access management systems. Additionally, it stresses the necessity of encryption for data both at rest and in transit to ensure privacy and safety concerns are adequately addressed.