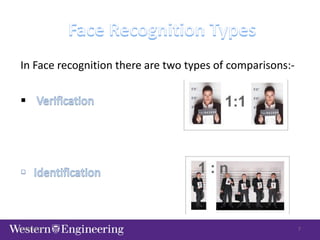
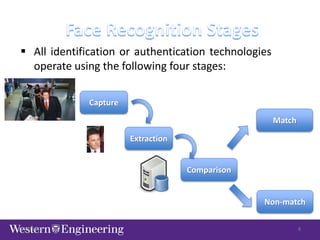
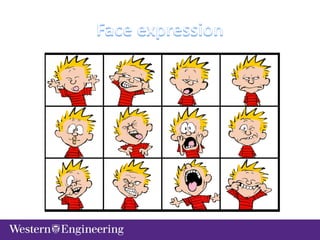
This document discusses issues with biometrics technologies, specifically face recognition. It provides an overview of image issues including resolution, orientation, scale, lighting, image currency, and facial expressions. It also discusses privacy issues regarding video surveillance and personal data security. The document outlines the typical stages of identification/authentication technologies and notes some common places public assumes they are under video surveillance like stores, banks, and gas stations. It closes by stating biometrics will be widespread but users should be aware of its issues and limitations.