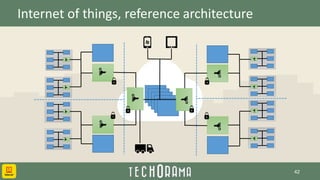
This document discusses privacy and security considerations for the Internet of Things (IoT). It outlines several dangers posed by IoT devices, including lack of physical and virtual security, potential for tampering, and privacy issues if personal data is not properly protected or consent is not obtained. The document then provides options for improving IoT security, such as preventing physical/virtual access, detecting tampering, tracking device identities, analyzing behavior for anomalies, and blocking compromised devices. It also discusses challenges of encryption for low-power devices and the importance of data privacy laws and user consent. Overall, the document examines both security and privacy risks posed by IoT and potential strategies to address them.