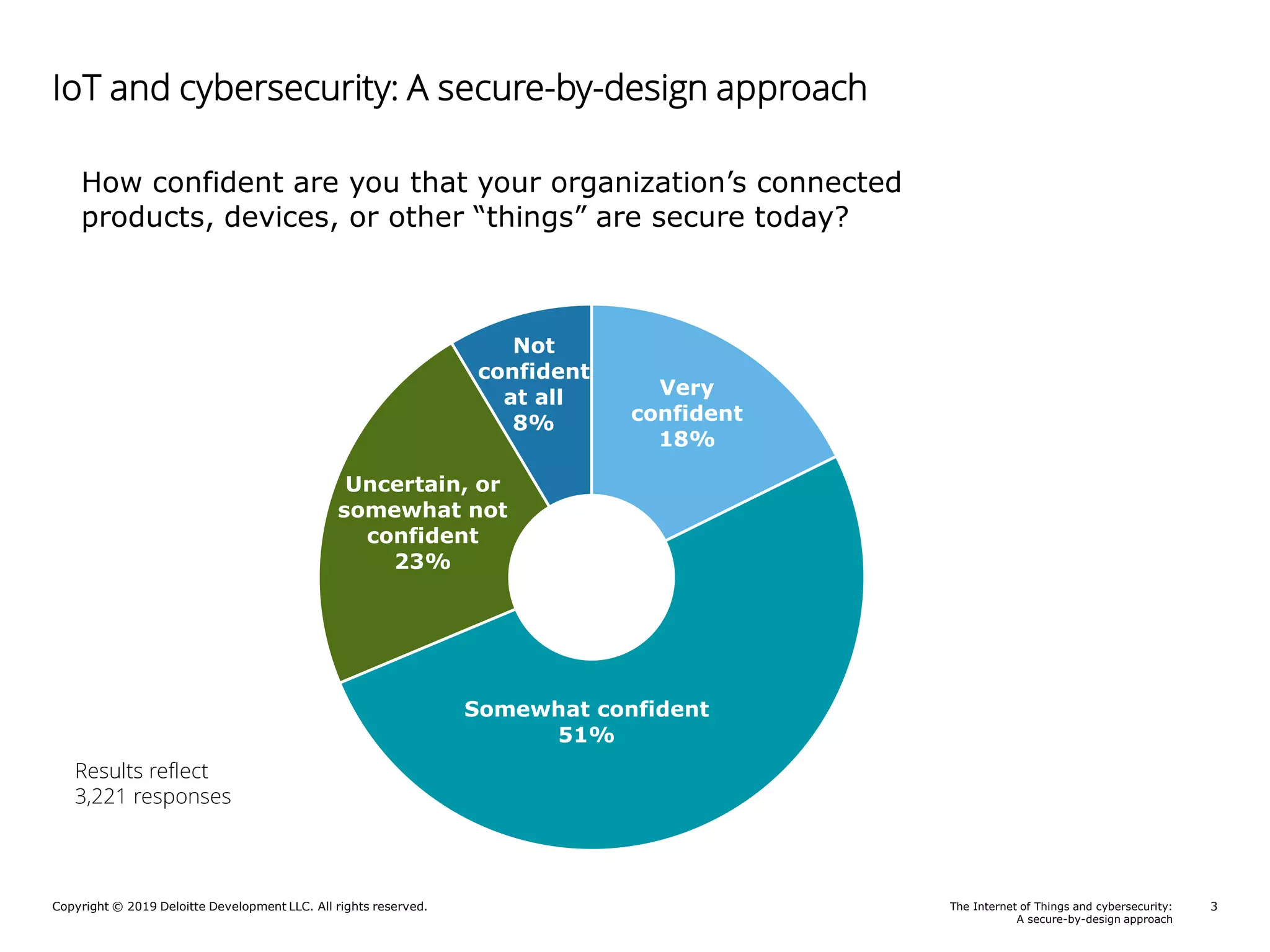
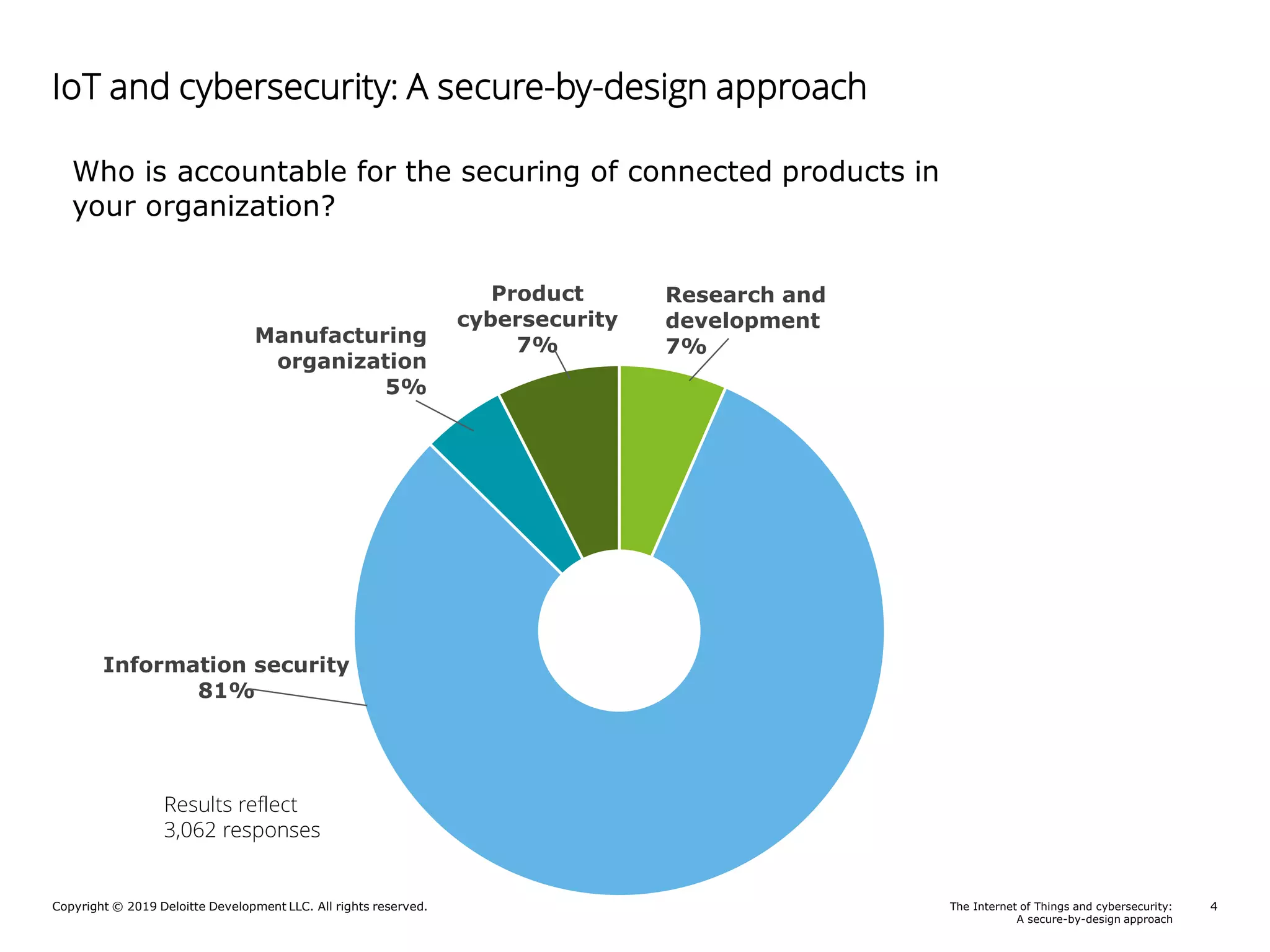
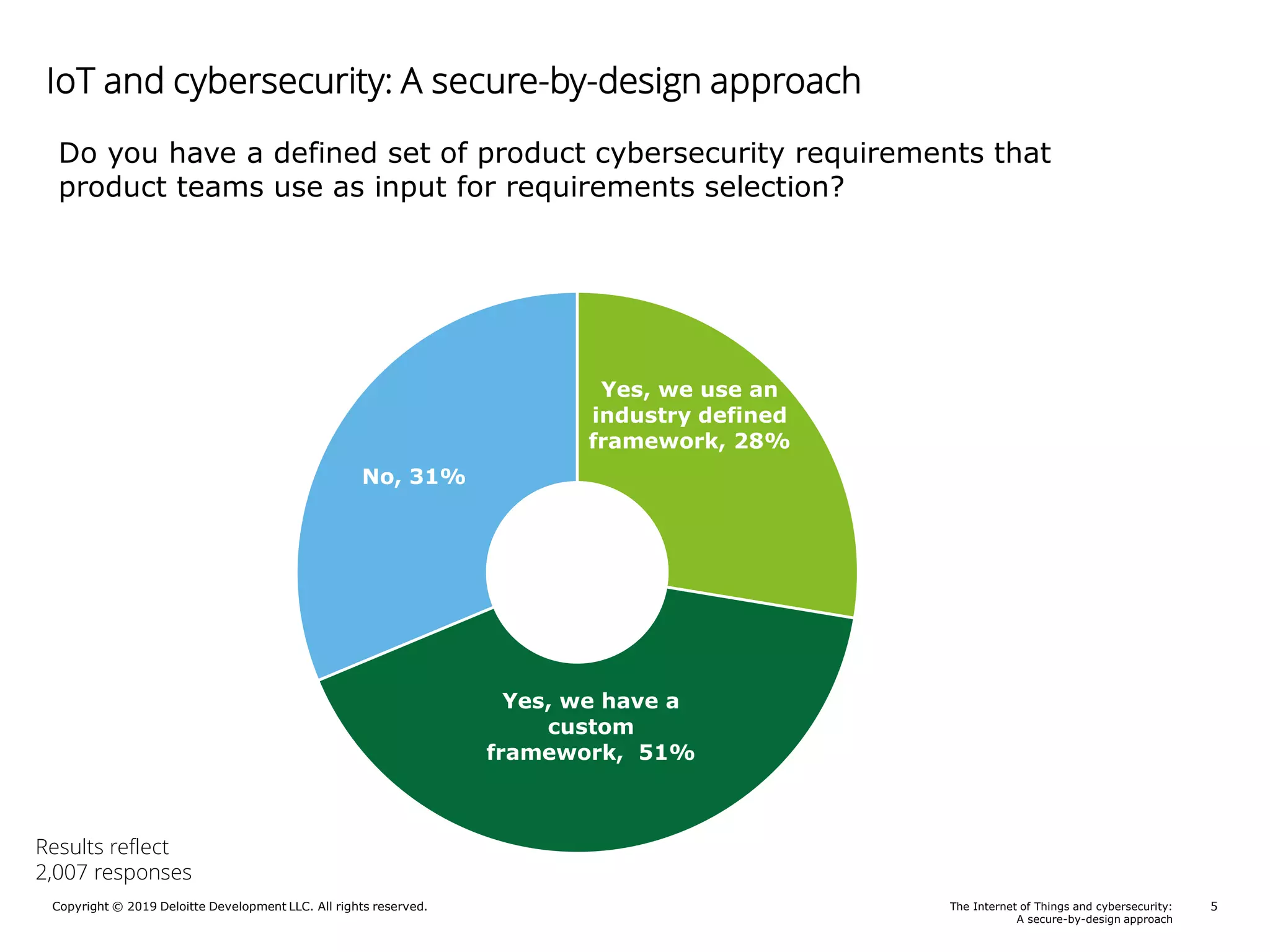
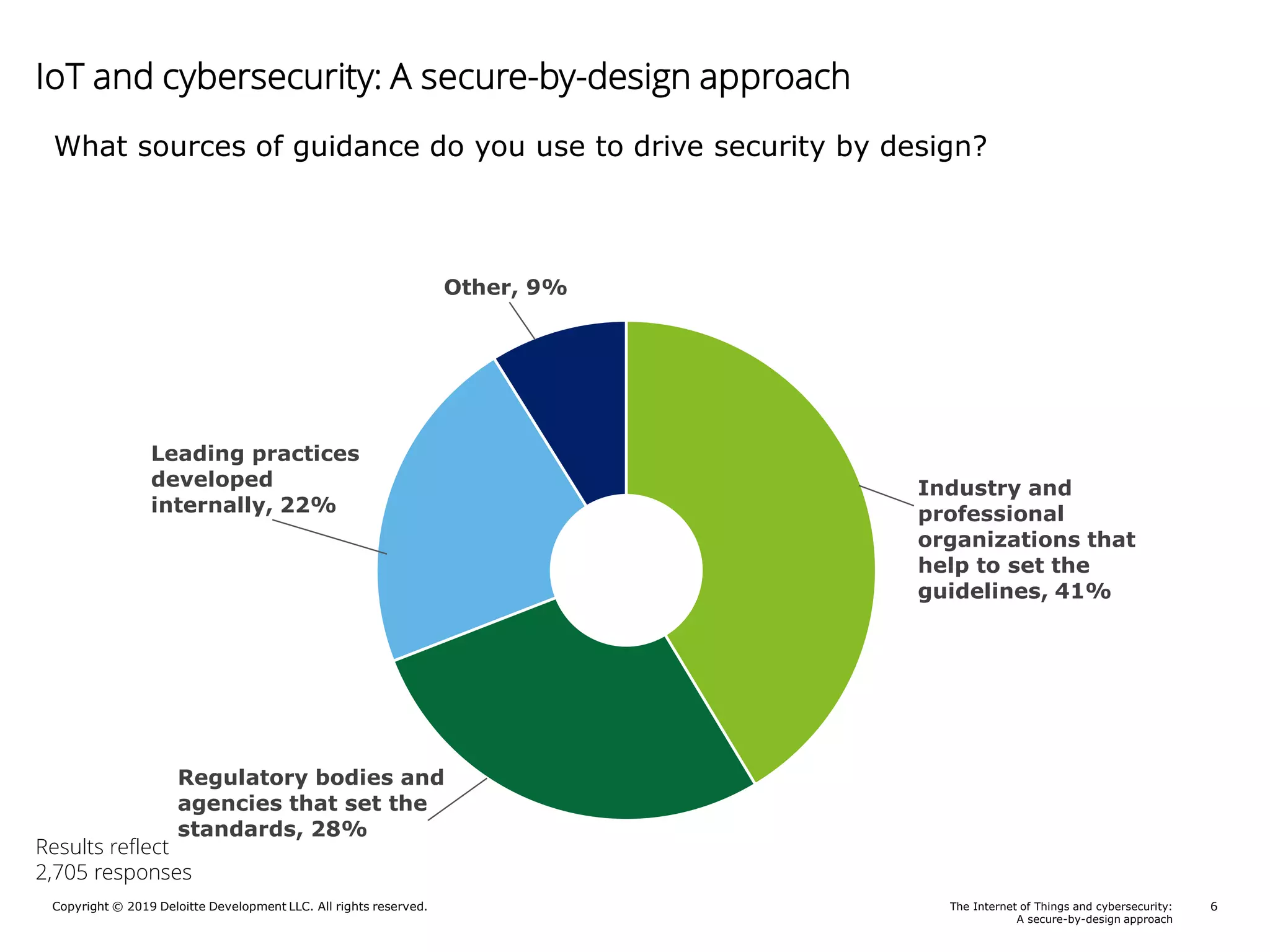
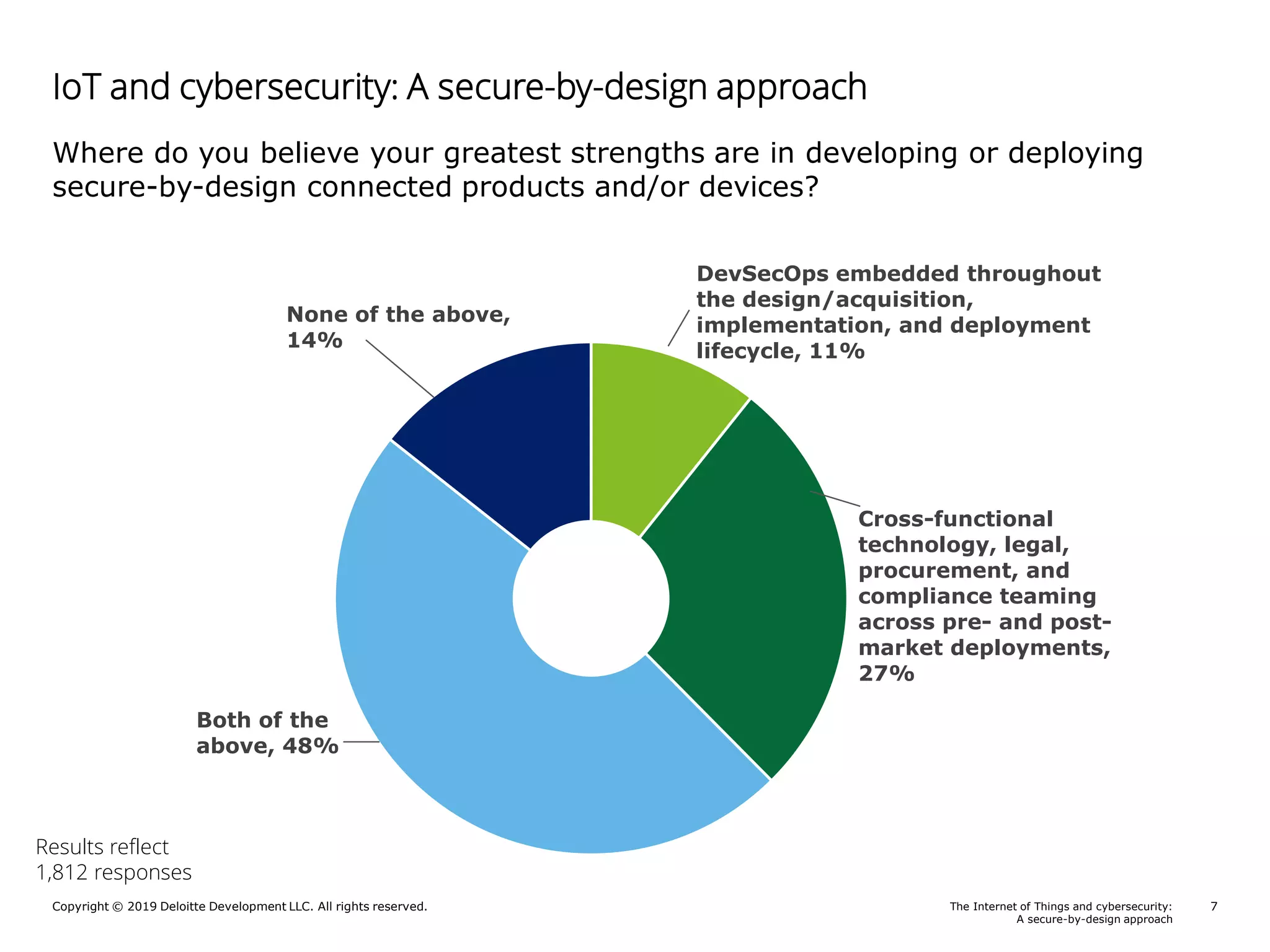
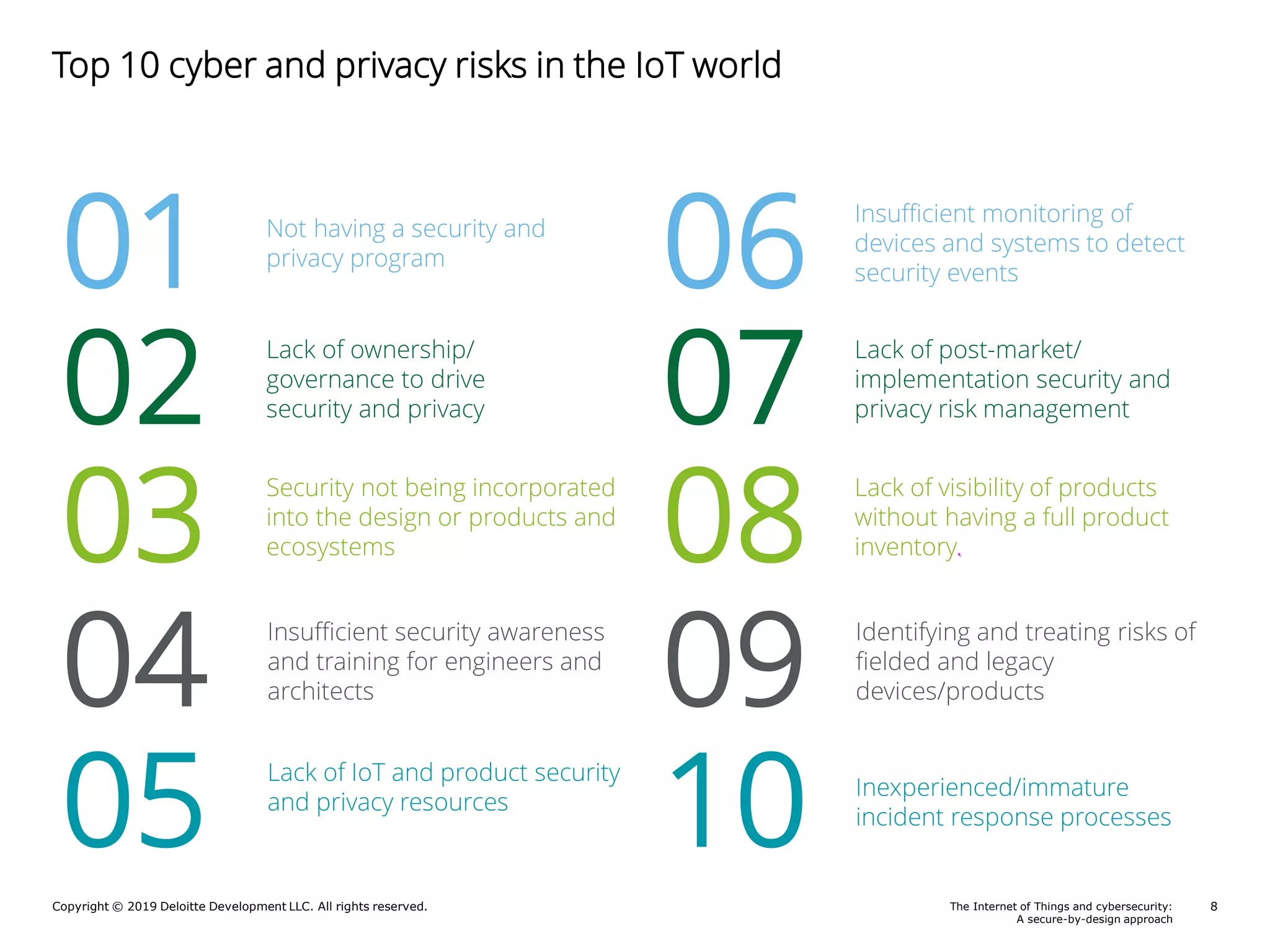
A Deloitte report presents poll results on perceptions of cybersecurity in the Internet of Things (IoT) sector, revealing that 69% of respondents feel somewhat to very confident about the security of their connected products. The report outlines key responsibilities for product security, identifies guidance sources for security by design, and highlights notable risks such as a lack of security awareness and ineffective incident response. Additionally, it emphasizes the importance of integrating security throughout the product lifecycle to mitigate cybersecurity threats.