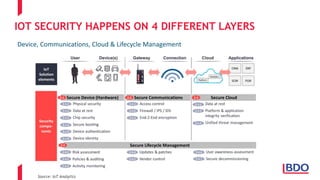
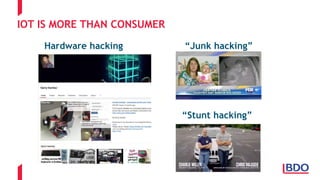
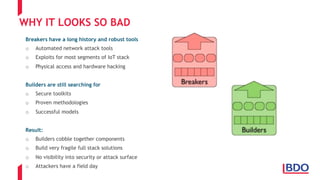
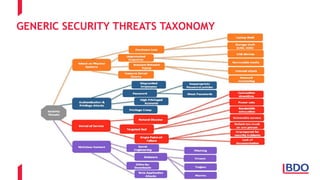
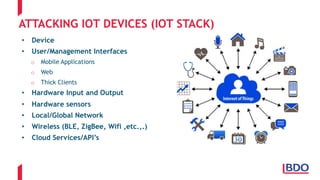
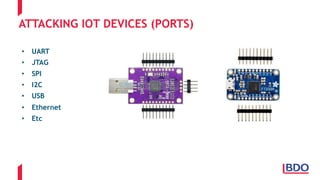
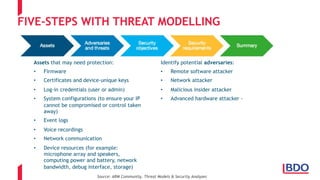
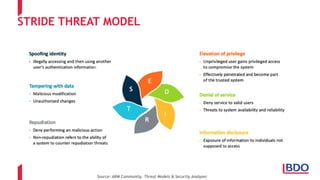
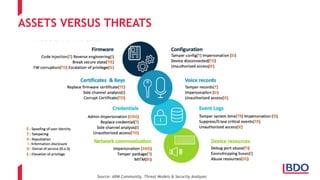
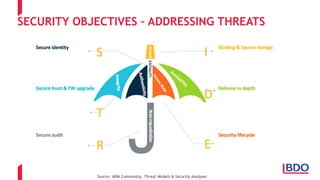
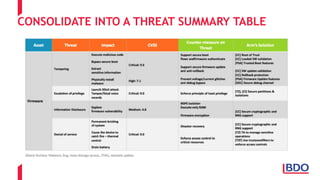
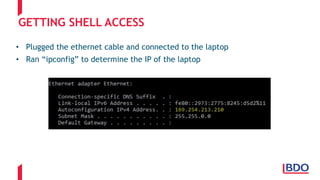
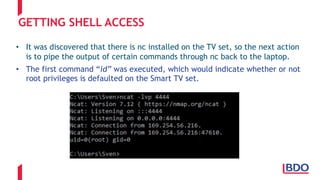
The document discusses the security challenges posed by the Internet of Things (IoT), highlighting vulnerabilities and the need for improved cybersecurity measures. It outlines the OWASP IoT Top 10 risks, illustrating the diversity of attack surfaces and emphasizing insufficient device security practices. The document also reviews various IoT applications across sectors and the implications for data privacy and security compliance.