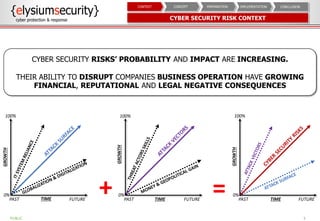
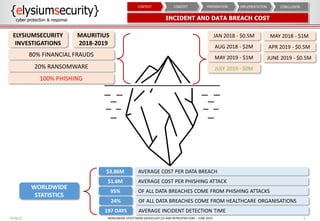
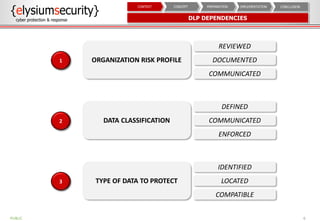
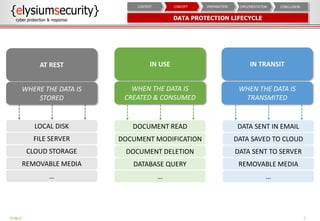
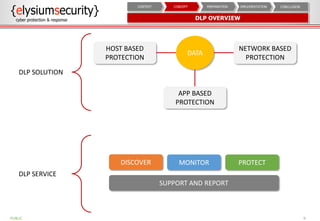
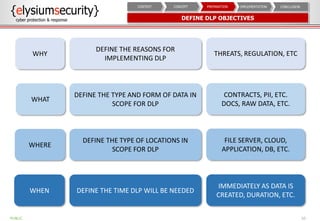
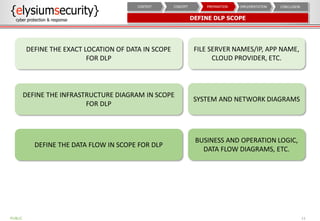
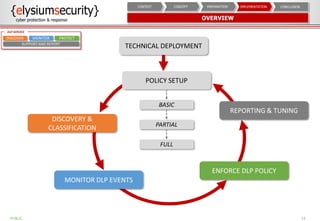
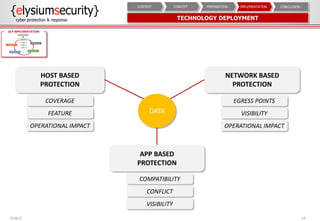
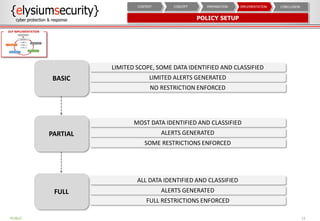
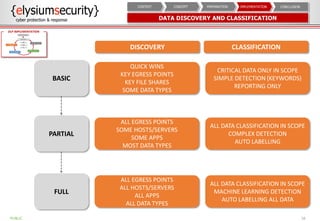
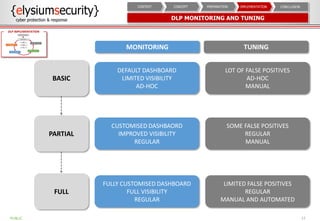
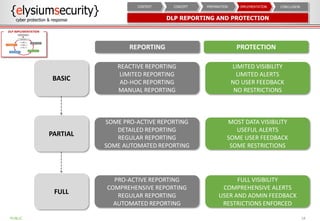
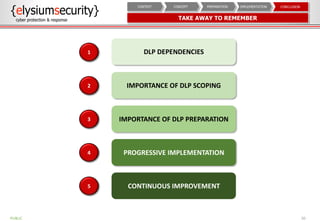
This document provides an overview of data loss prevention (DLP). It discusses cyber security risks and increasing data breach statistics and costs. It defines DLP and the lifecycle of data protection. Key aspects of a DLP implementation are outlined, including defining objectives and scope, policy setup, data discovery and classification, monitoring and tuning, and reporting. The benefits of visibility, monitoring, and improved protection are highlighted.