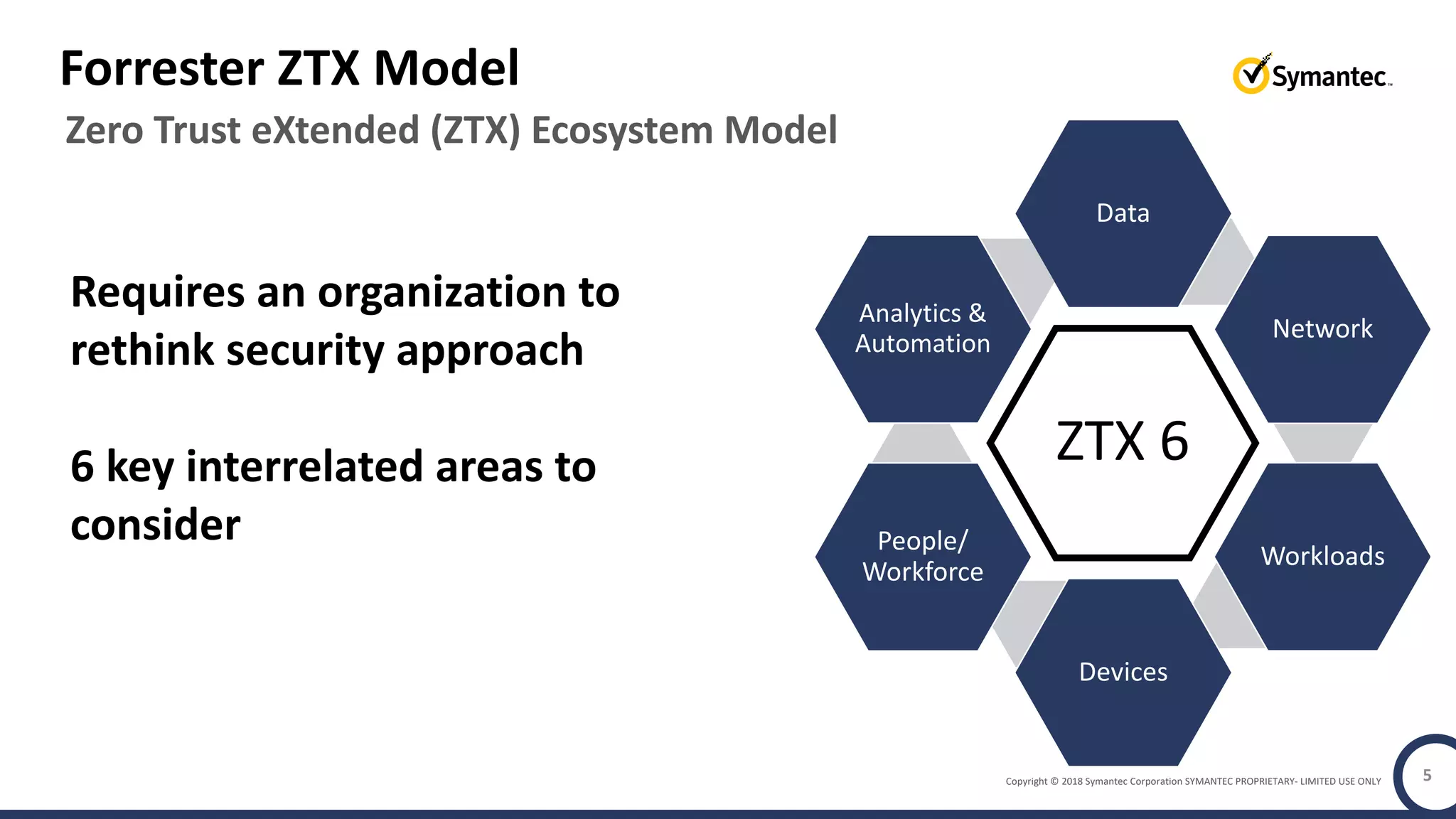
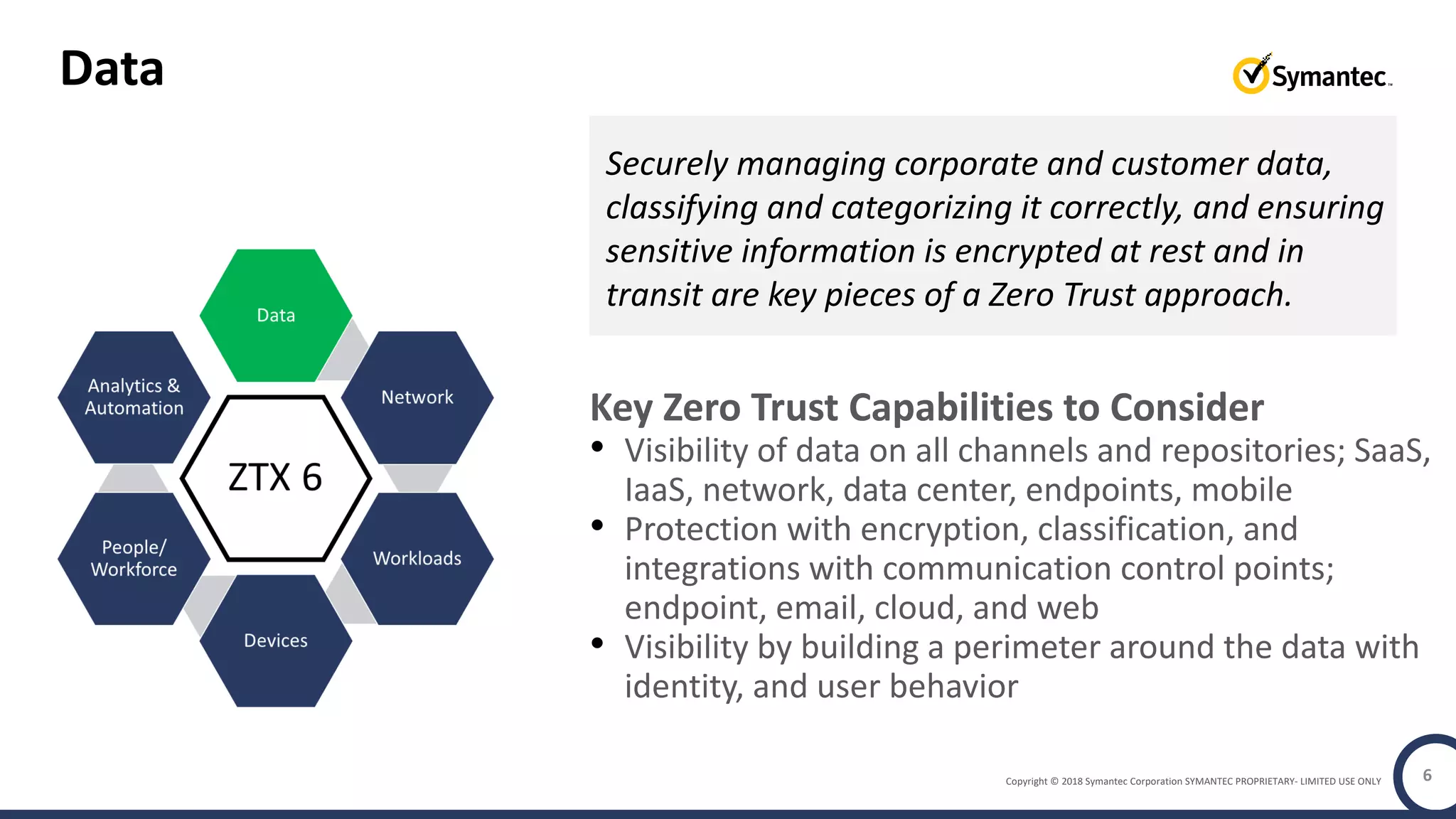
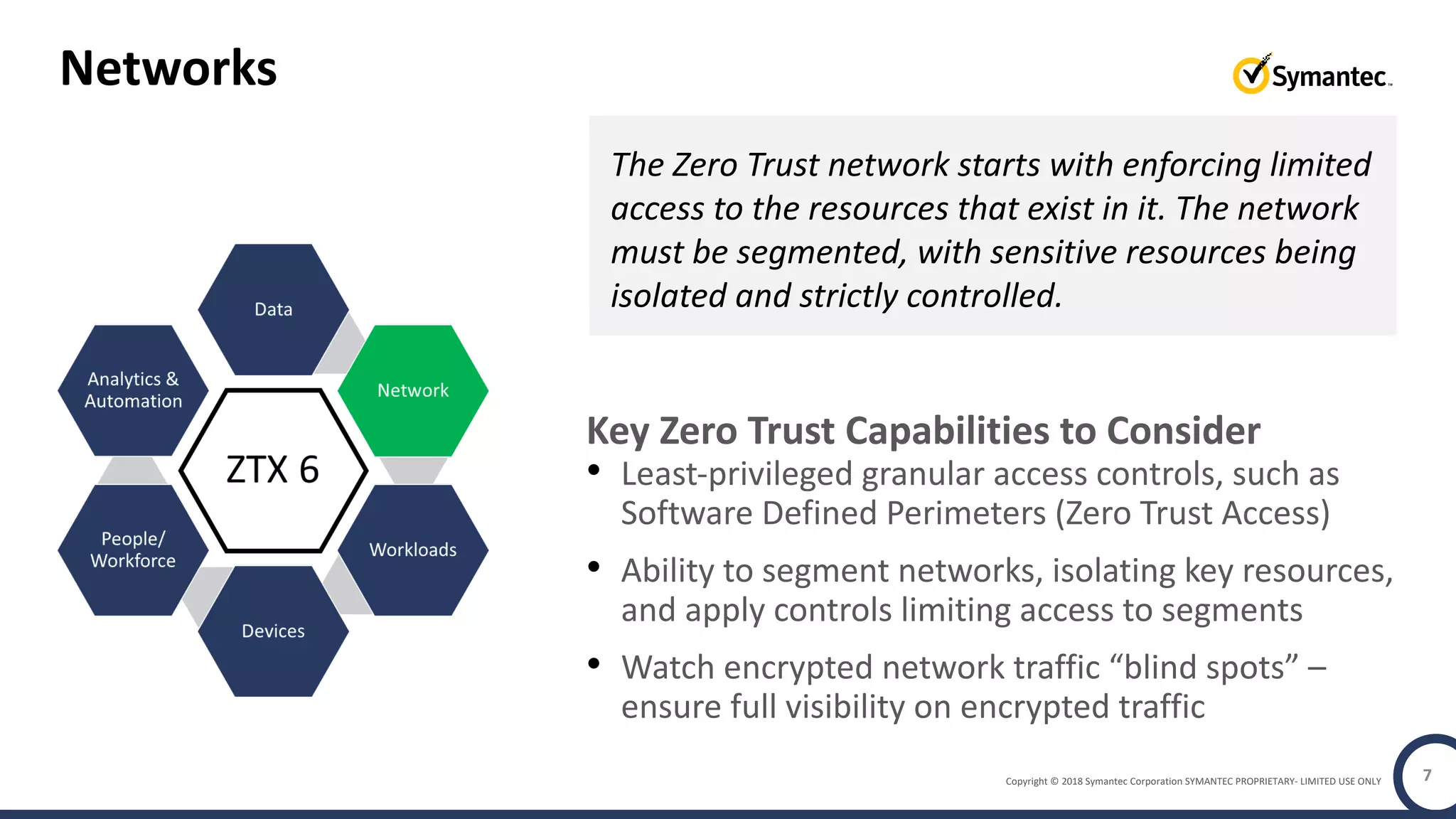
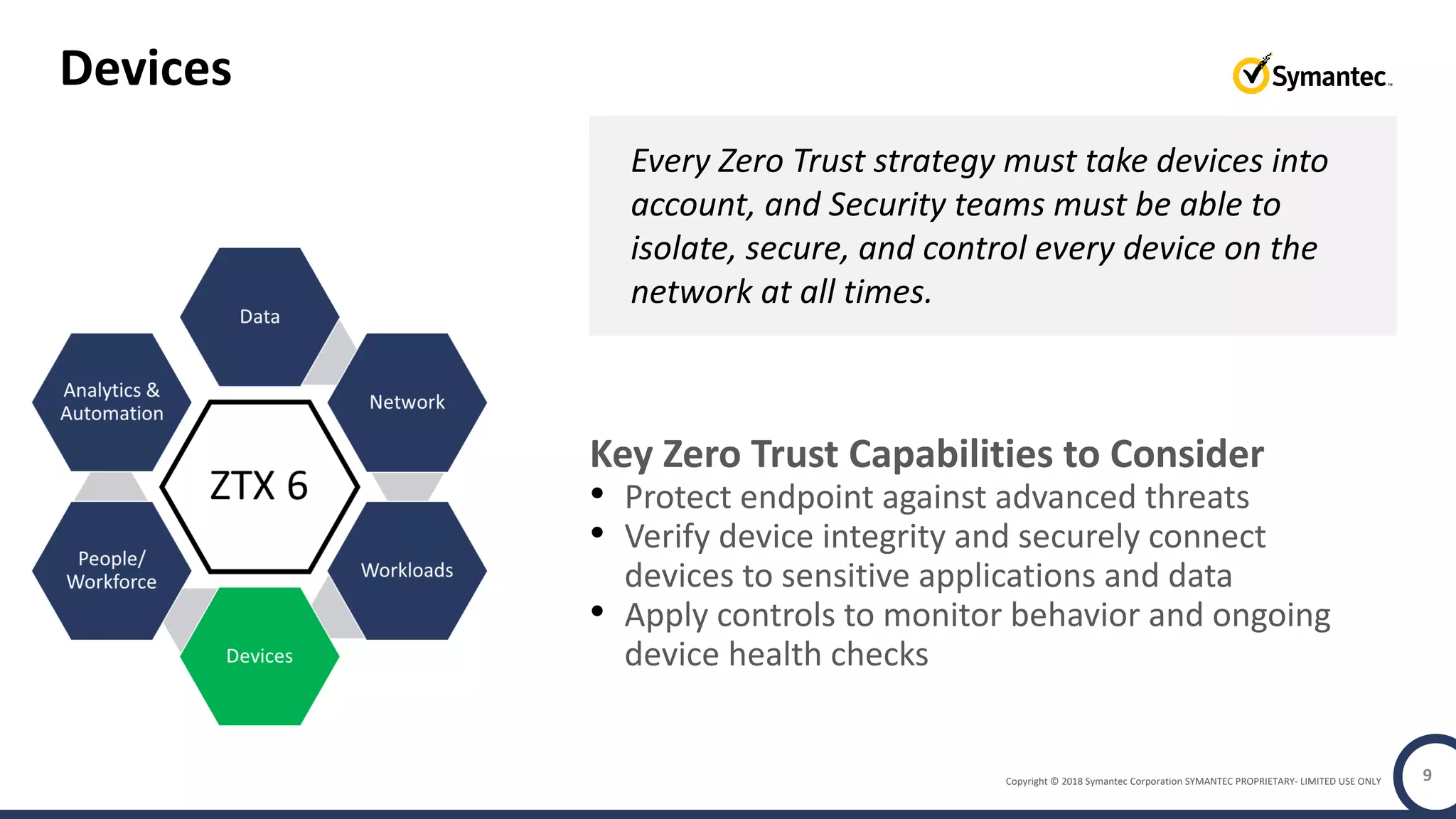
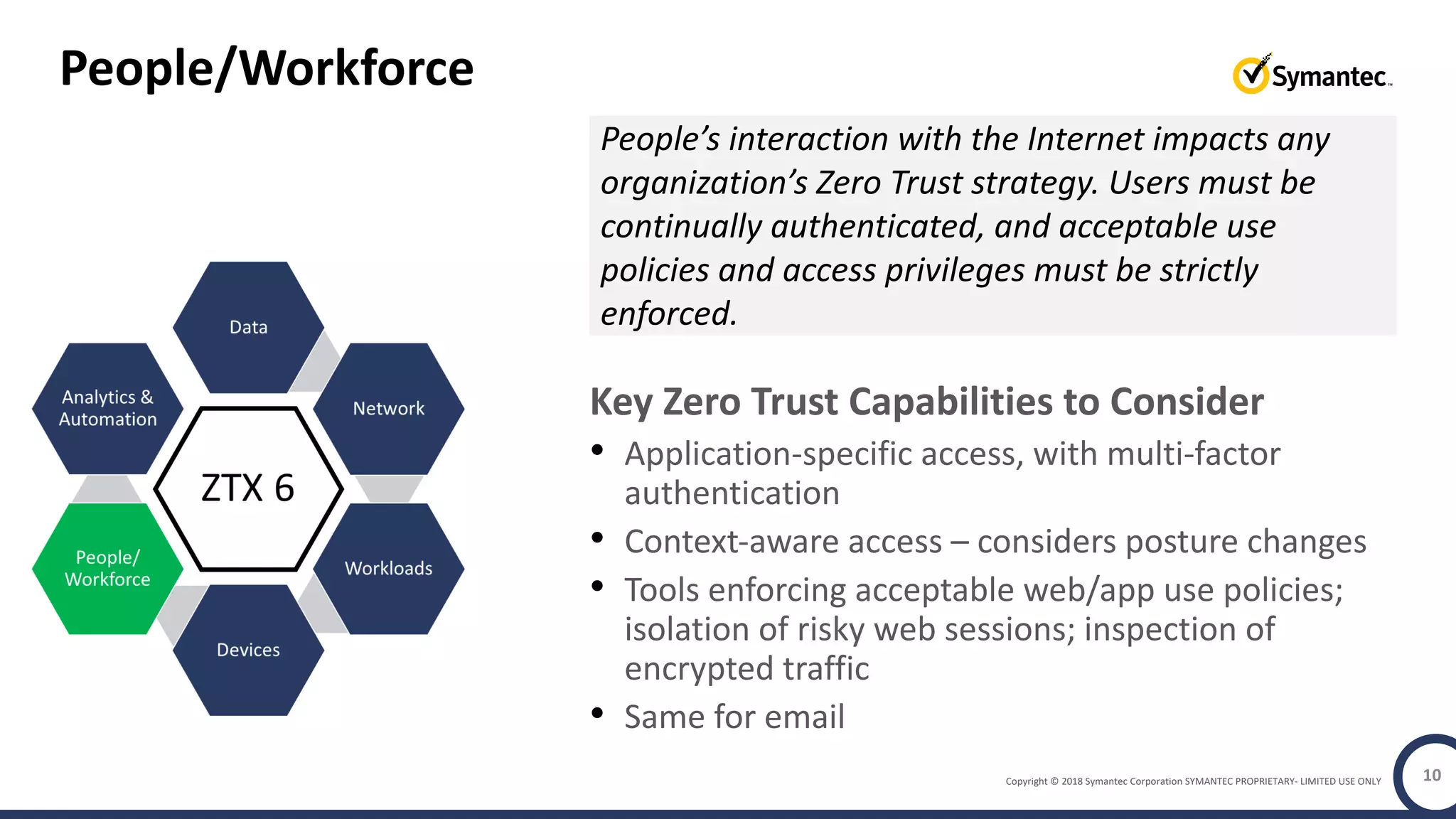
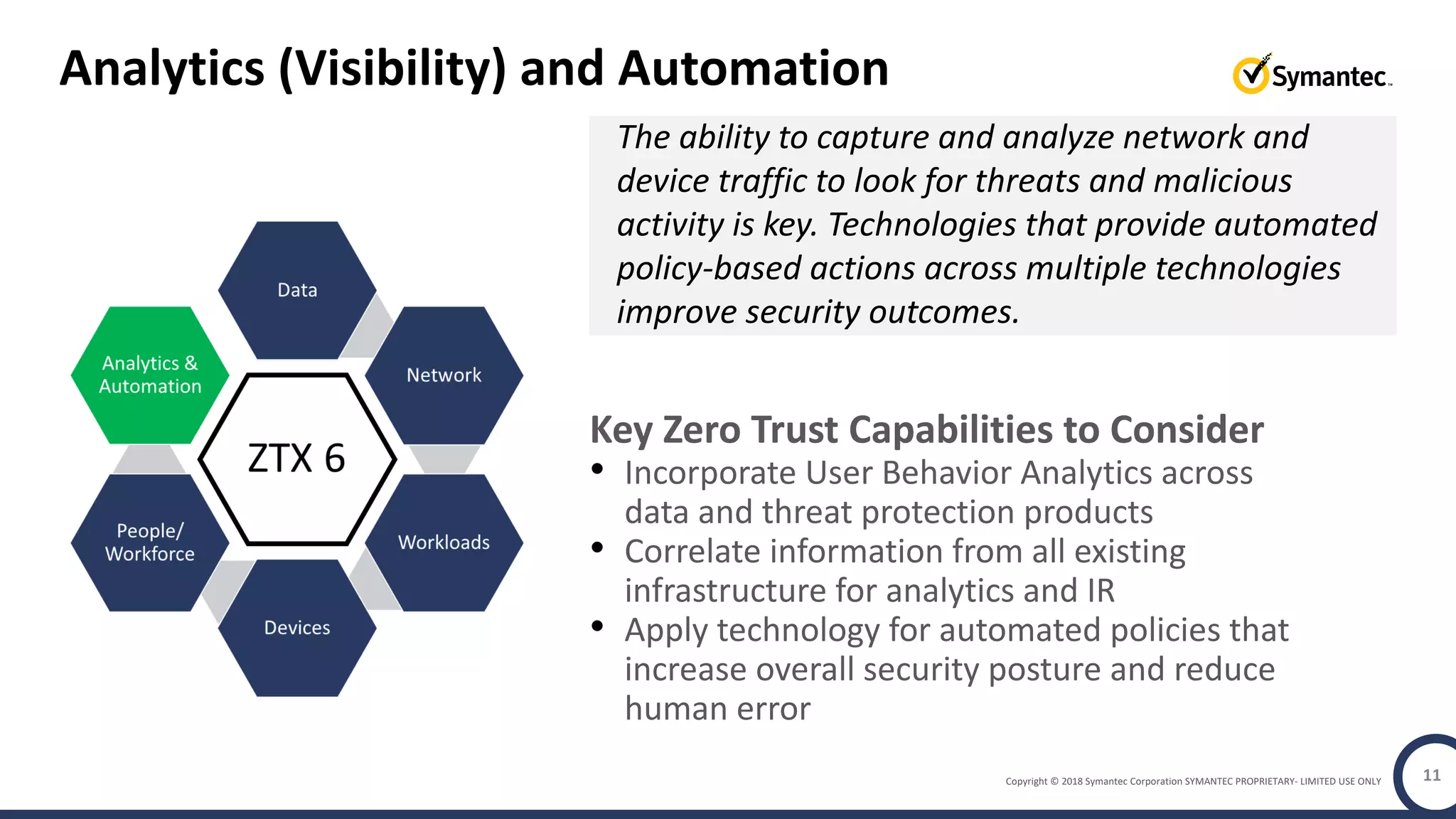
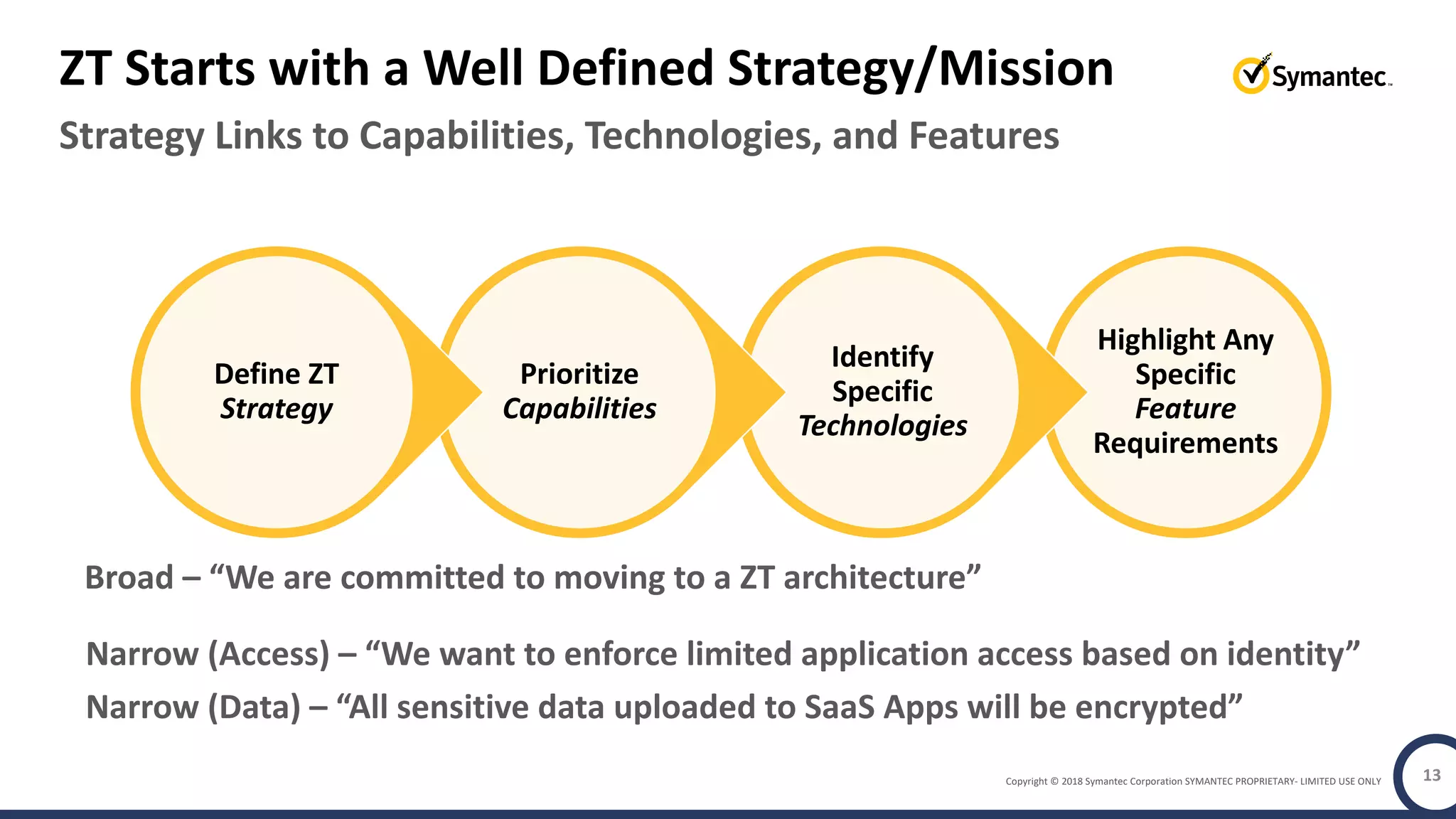
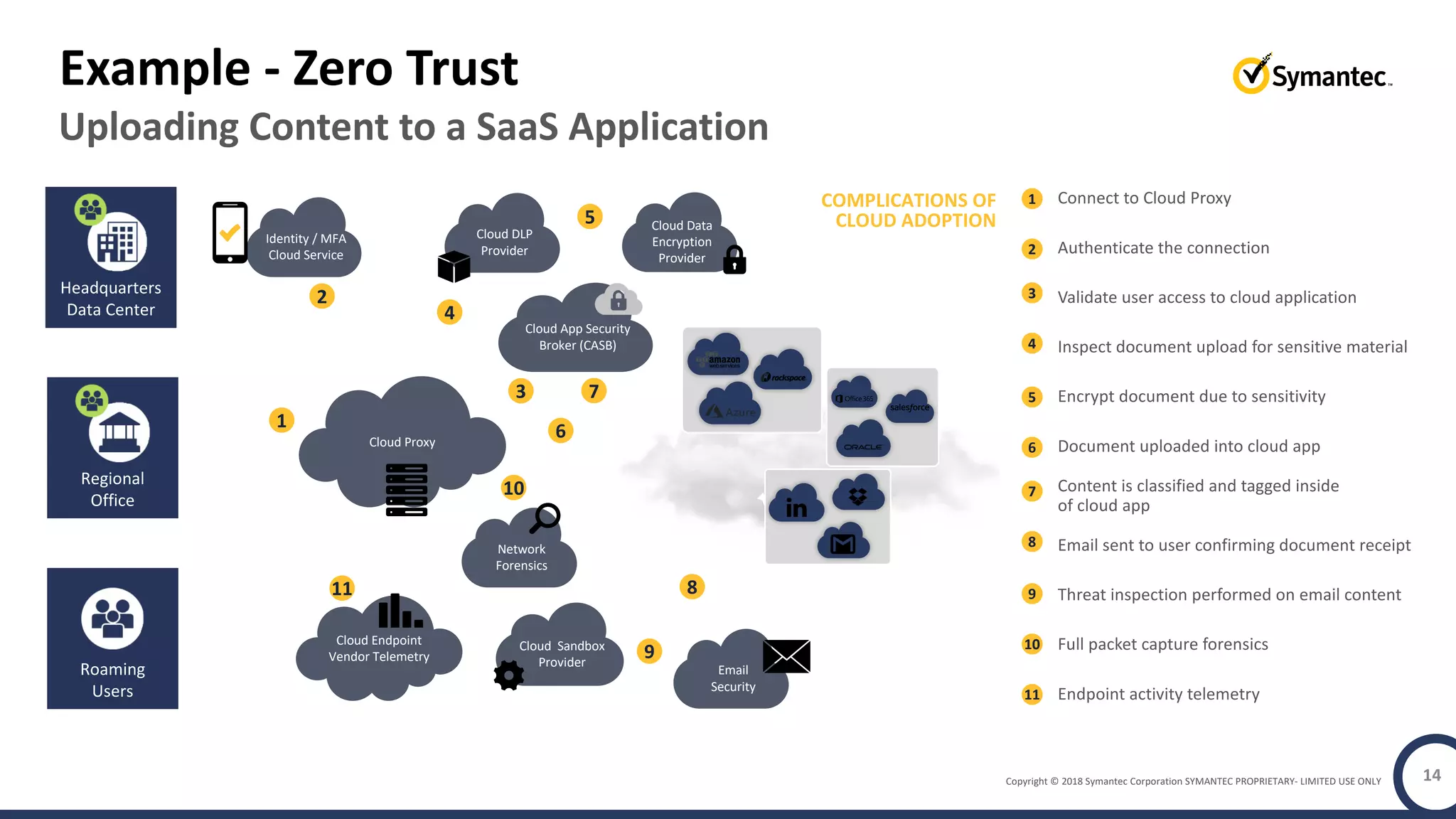
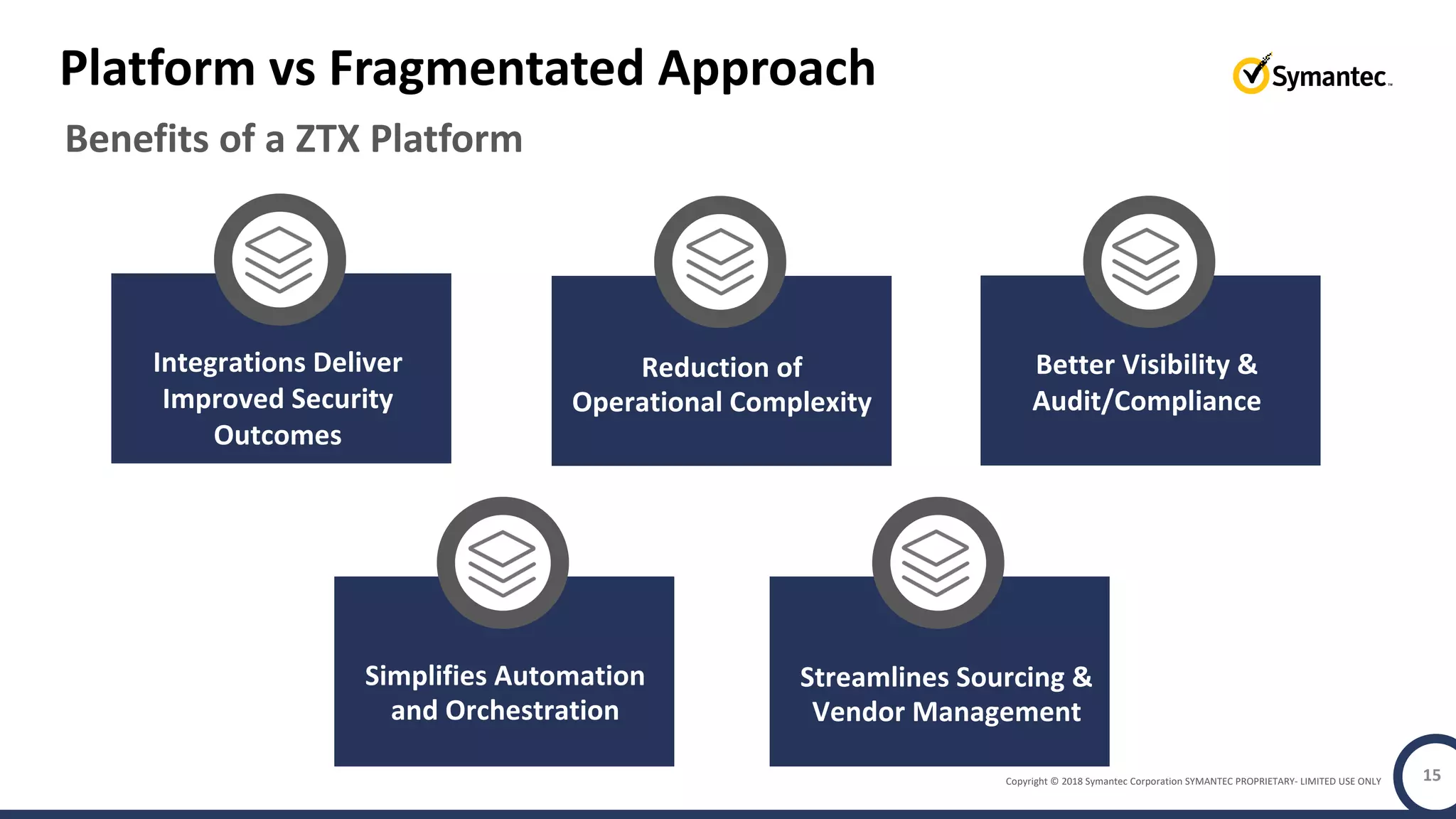
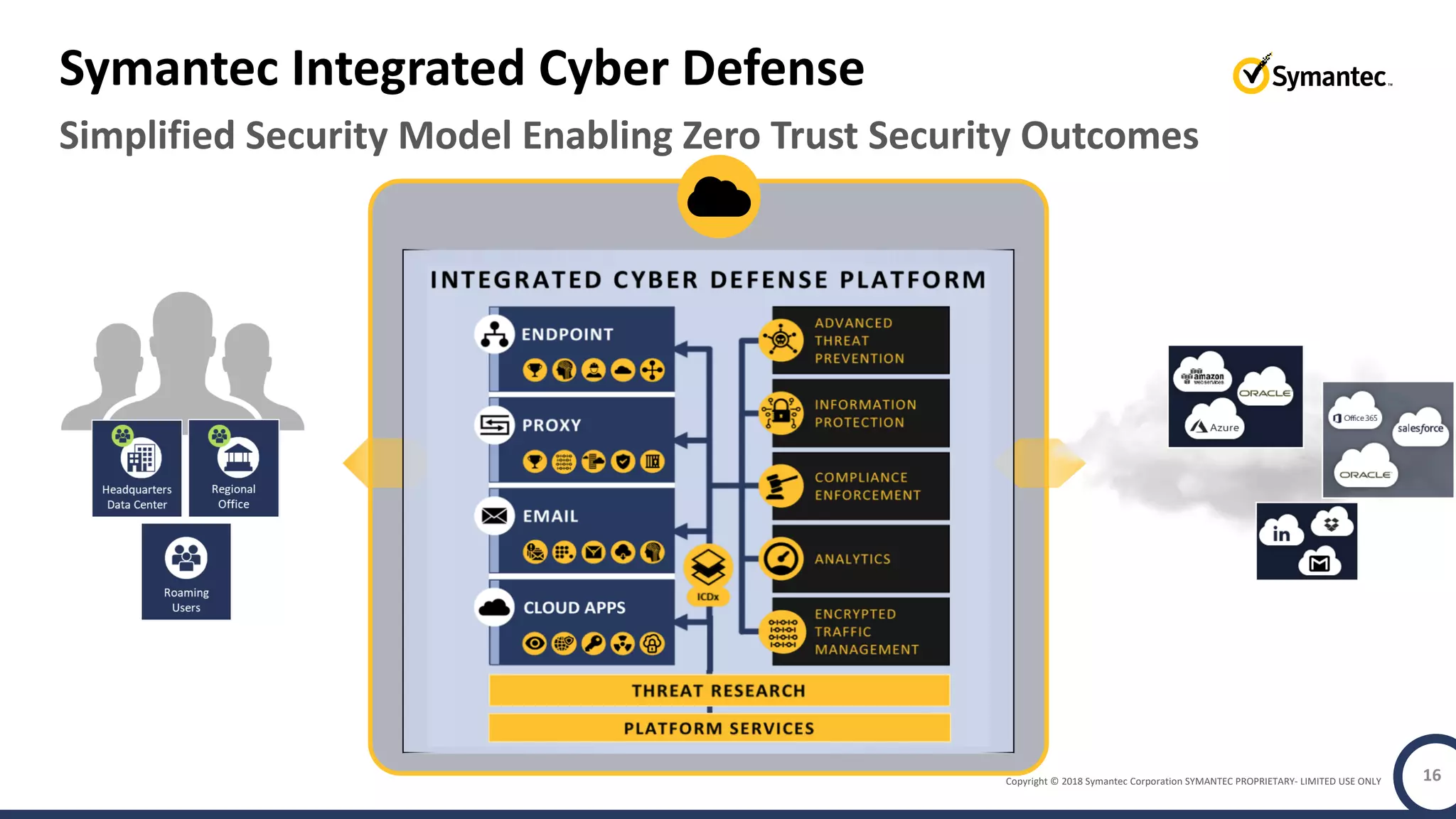
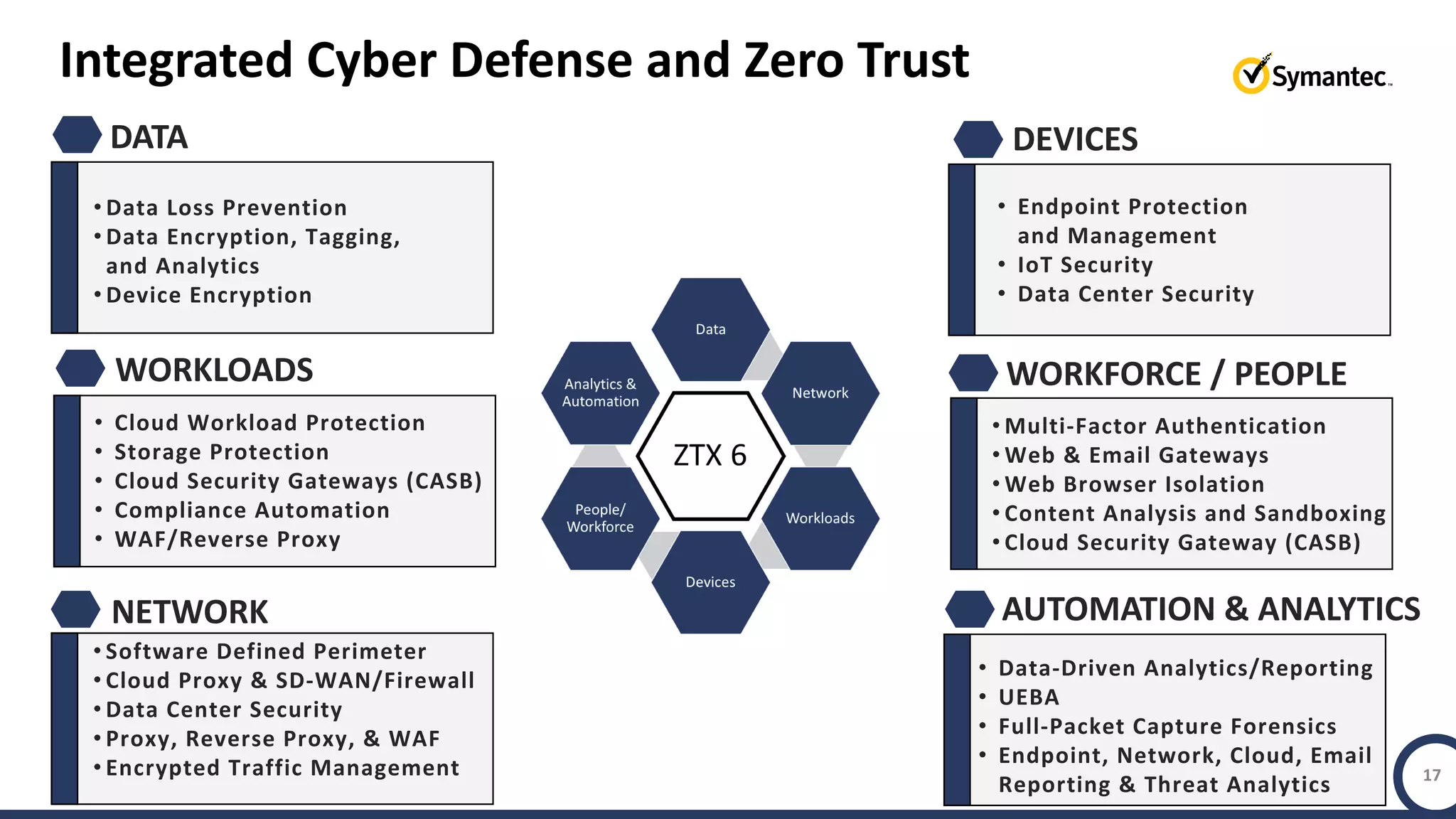
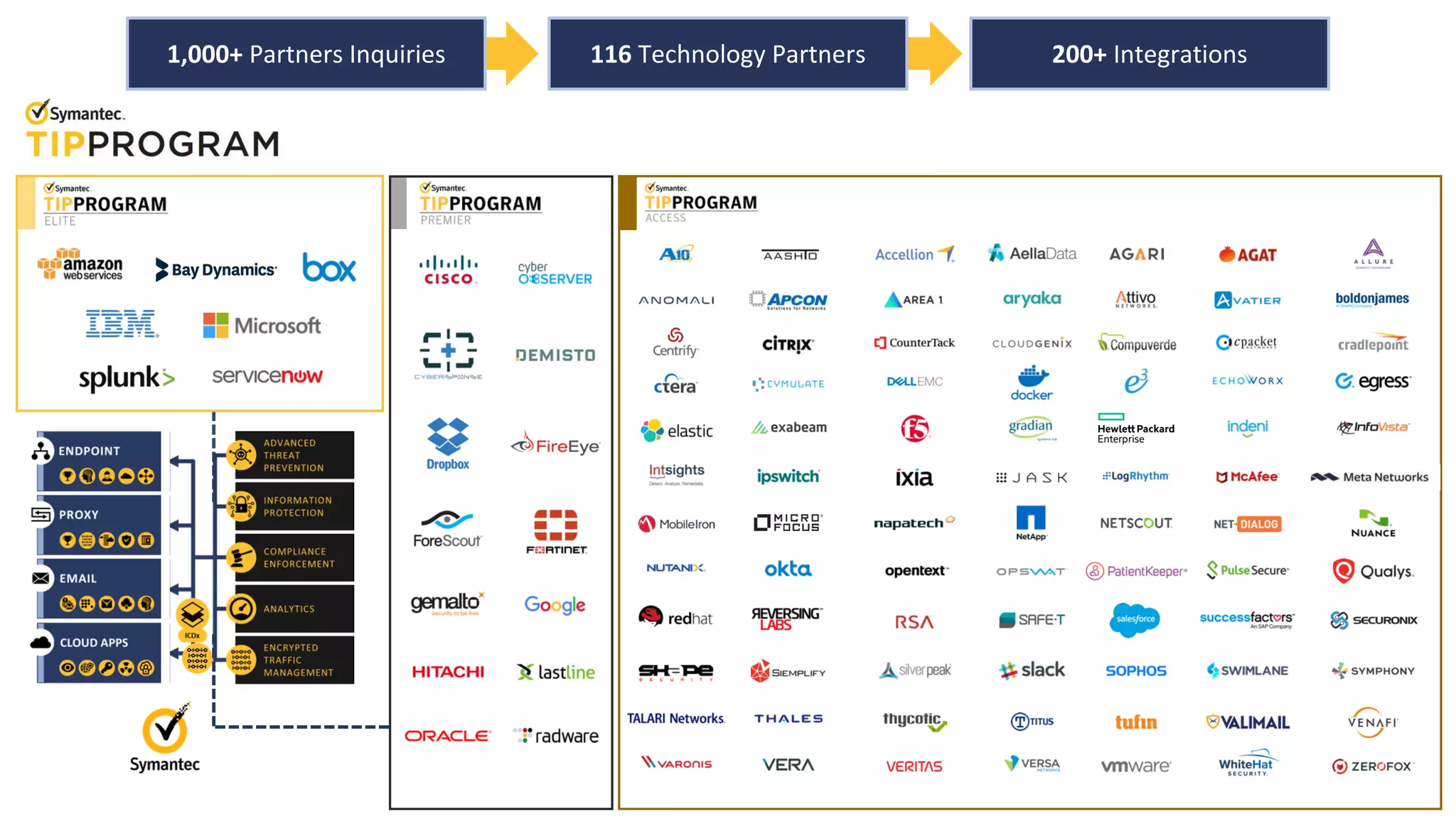
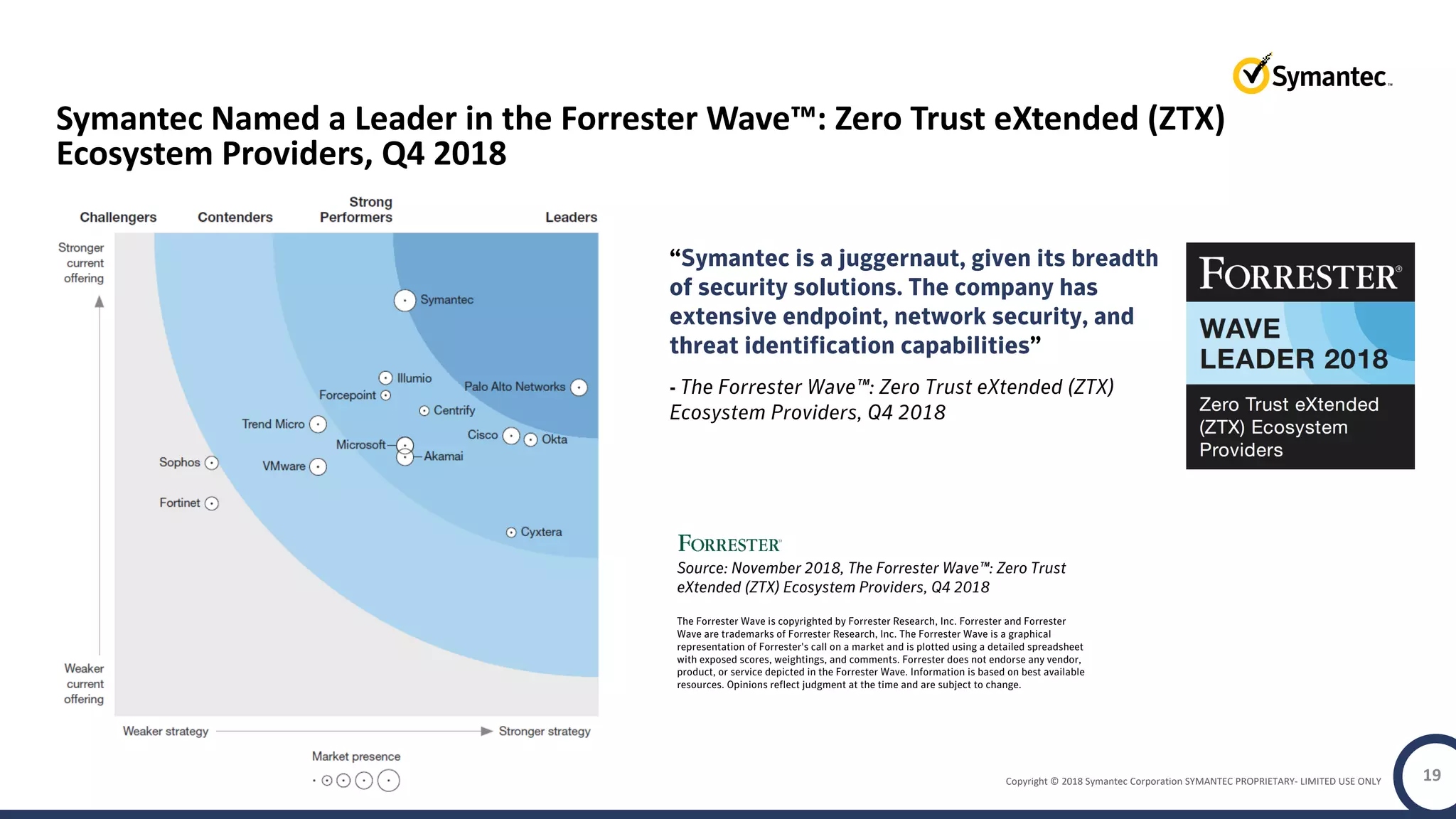
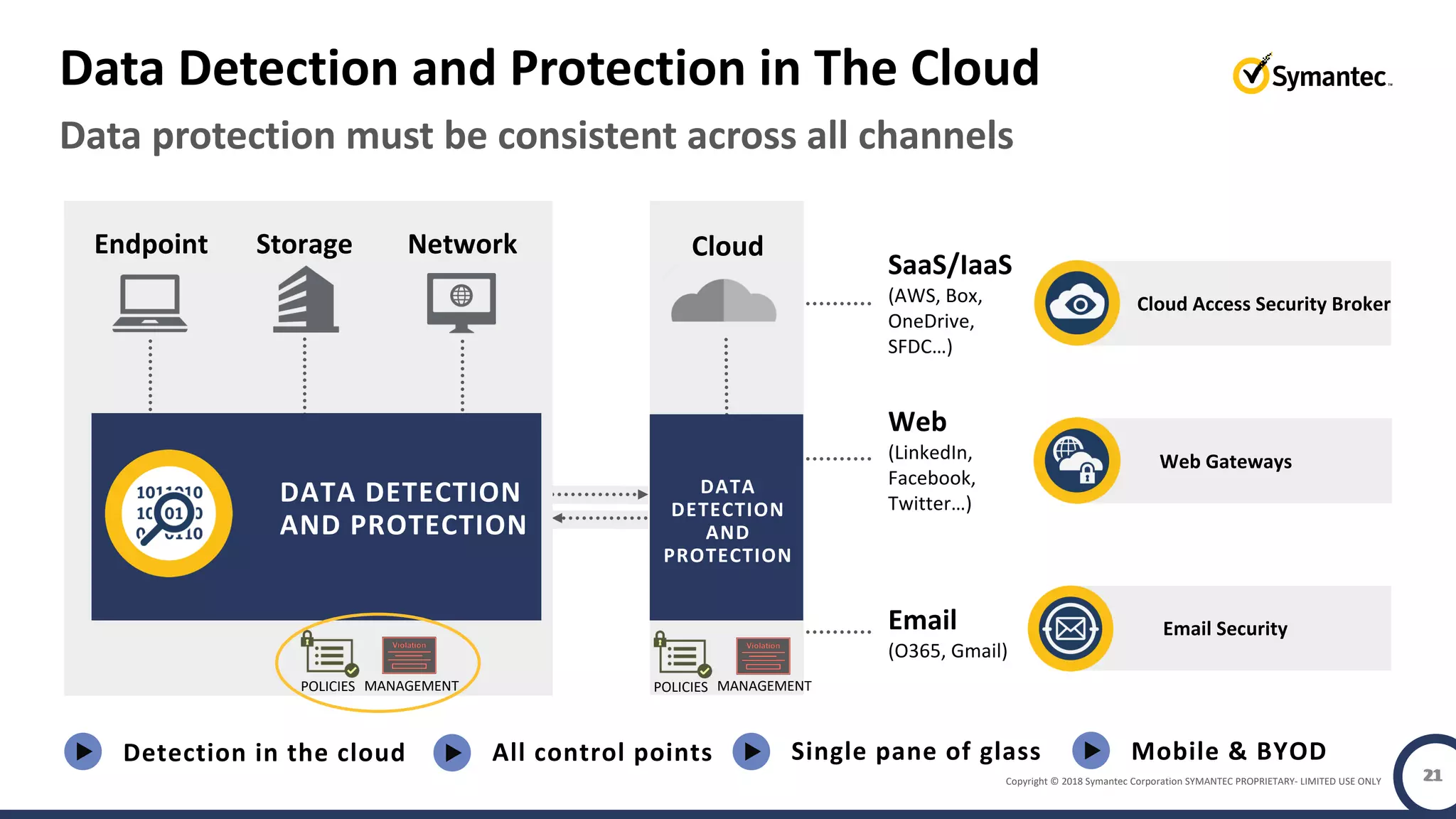
The document discusses building a zero trust program on a solid platform. It emphasizes that a zero trust approach requires considering six interrelated areas: data, networks, workloads, devices, people/workforce, and analytics & automation. A platform that integrates capabilities across these areas provides improved security outcomes, reduces complexity, and simplifies automation compared to a fragmented approach. The document uses Symantec's integrated cyber defense platform as an example and demonstrates how it can operationalize zero trust strategies.