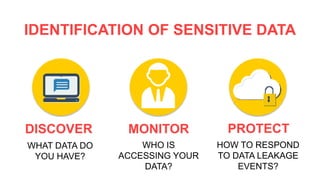
Data loss prevention ensures critical corporate information is kept safely within networks and helps administrators control data transfers. It is important for maintaining corporate image, compliance, and avoiding penalties. DLP identifies sensitive data like credit cards, social security numbers, business plans, and financial records. It monitors, detects, prevents data leakage, and notifies users of violations while protecting sensitive information. Choosing a DLP product requires considering budget, in-house vs outsourcing needs, policies, incident response, and compatibility with existing infrastructure.