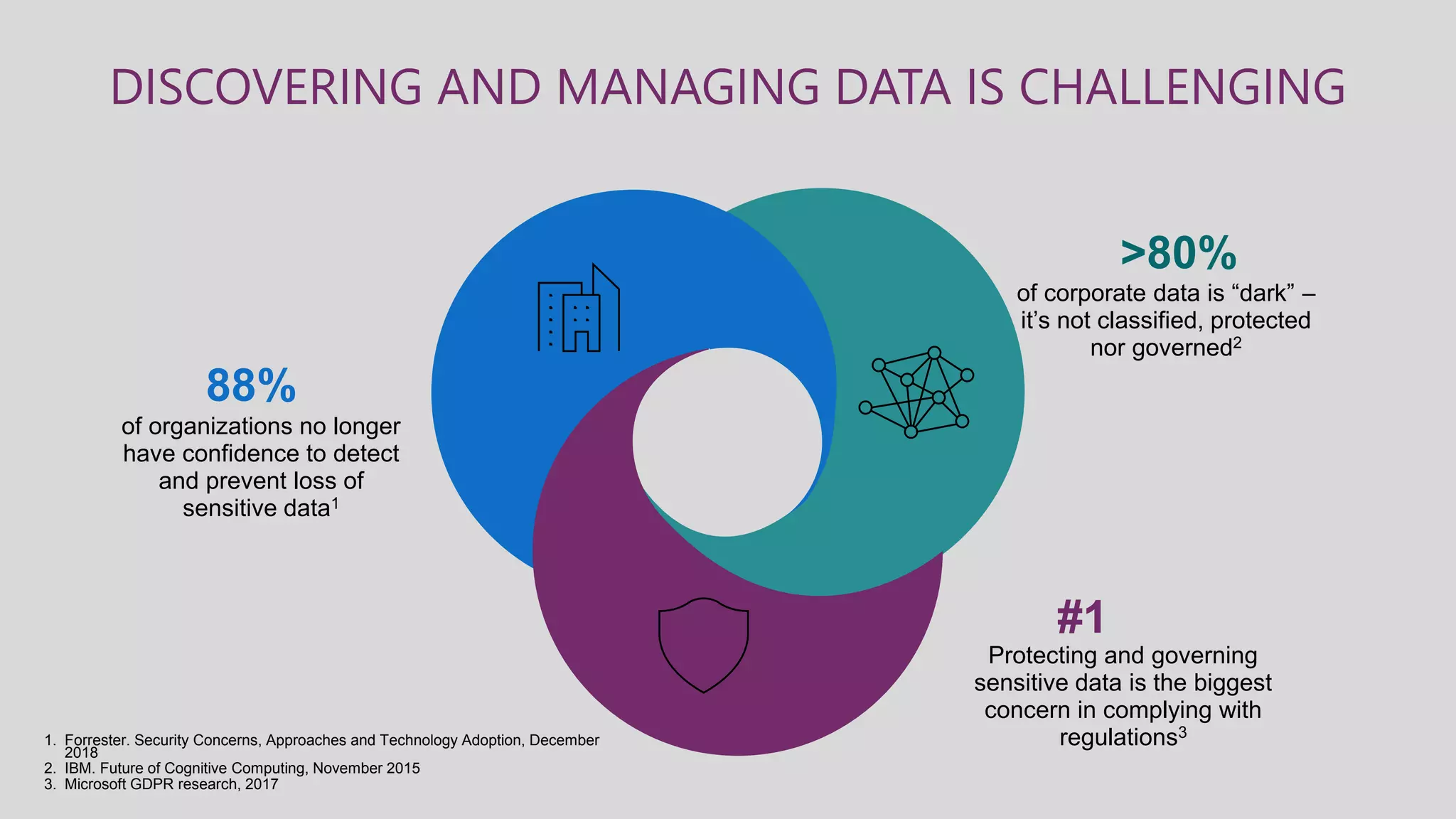
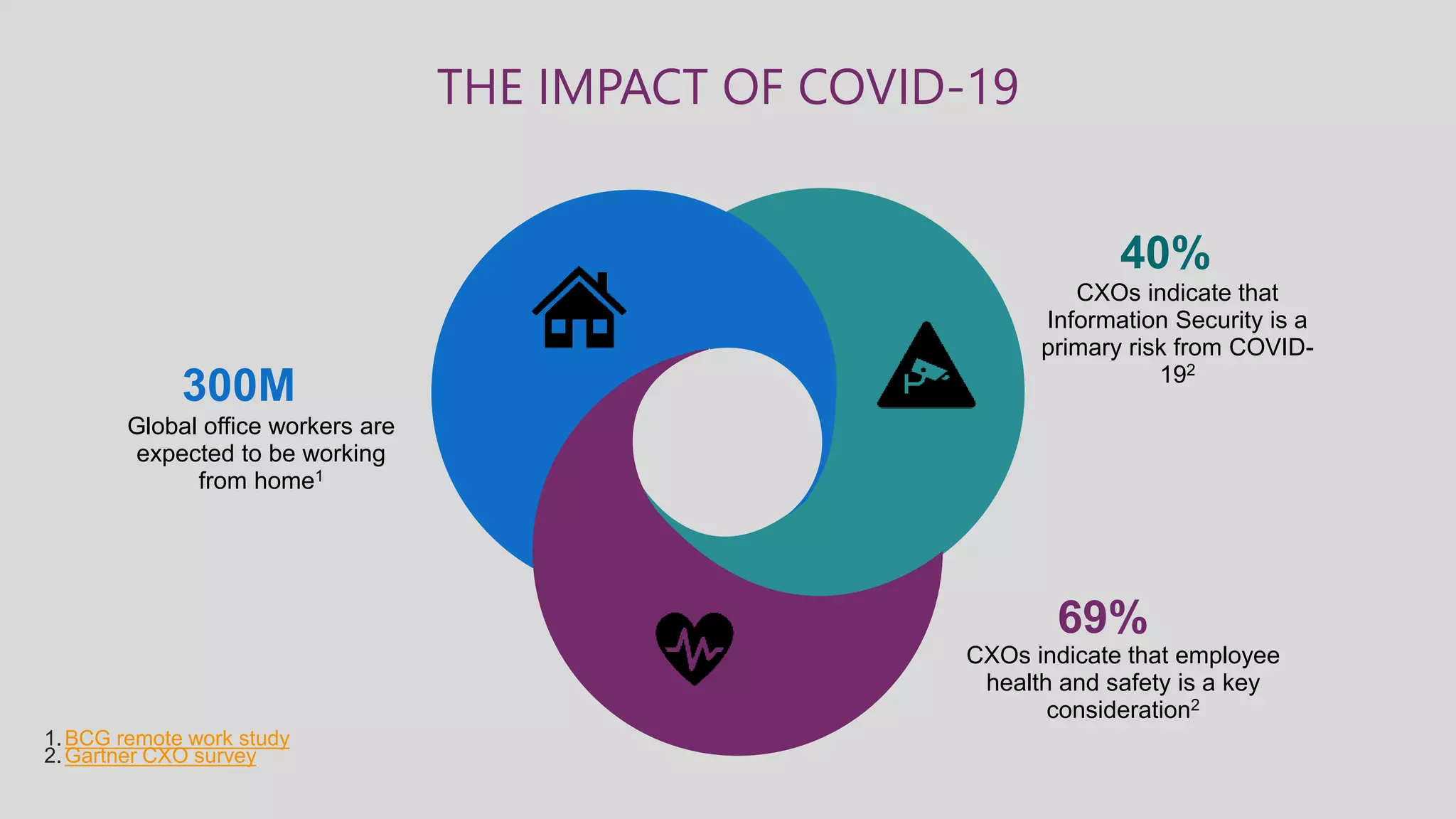
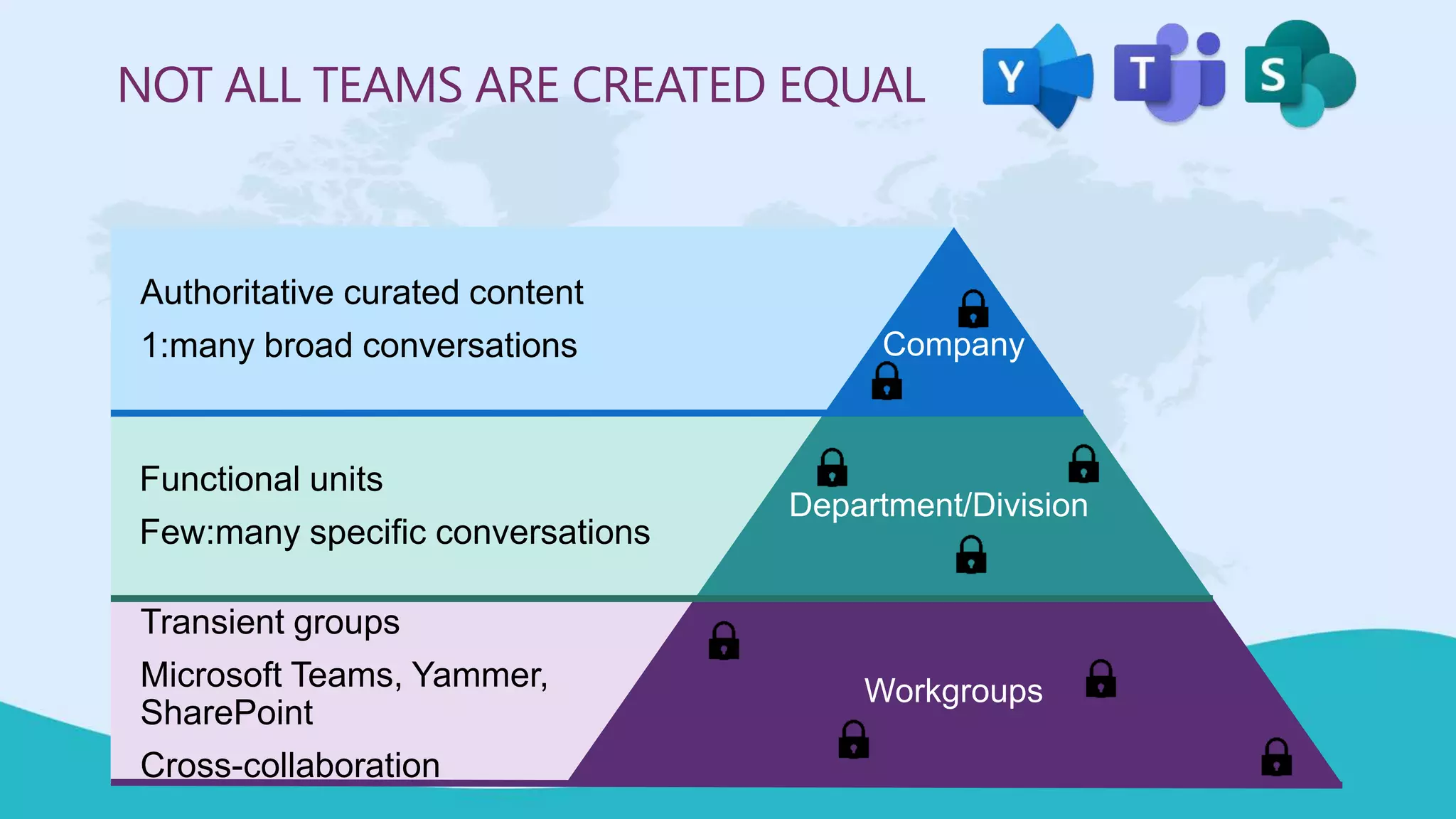
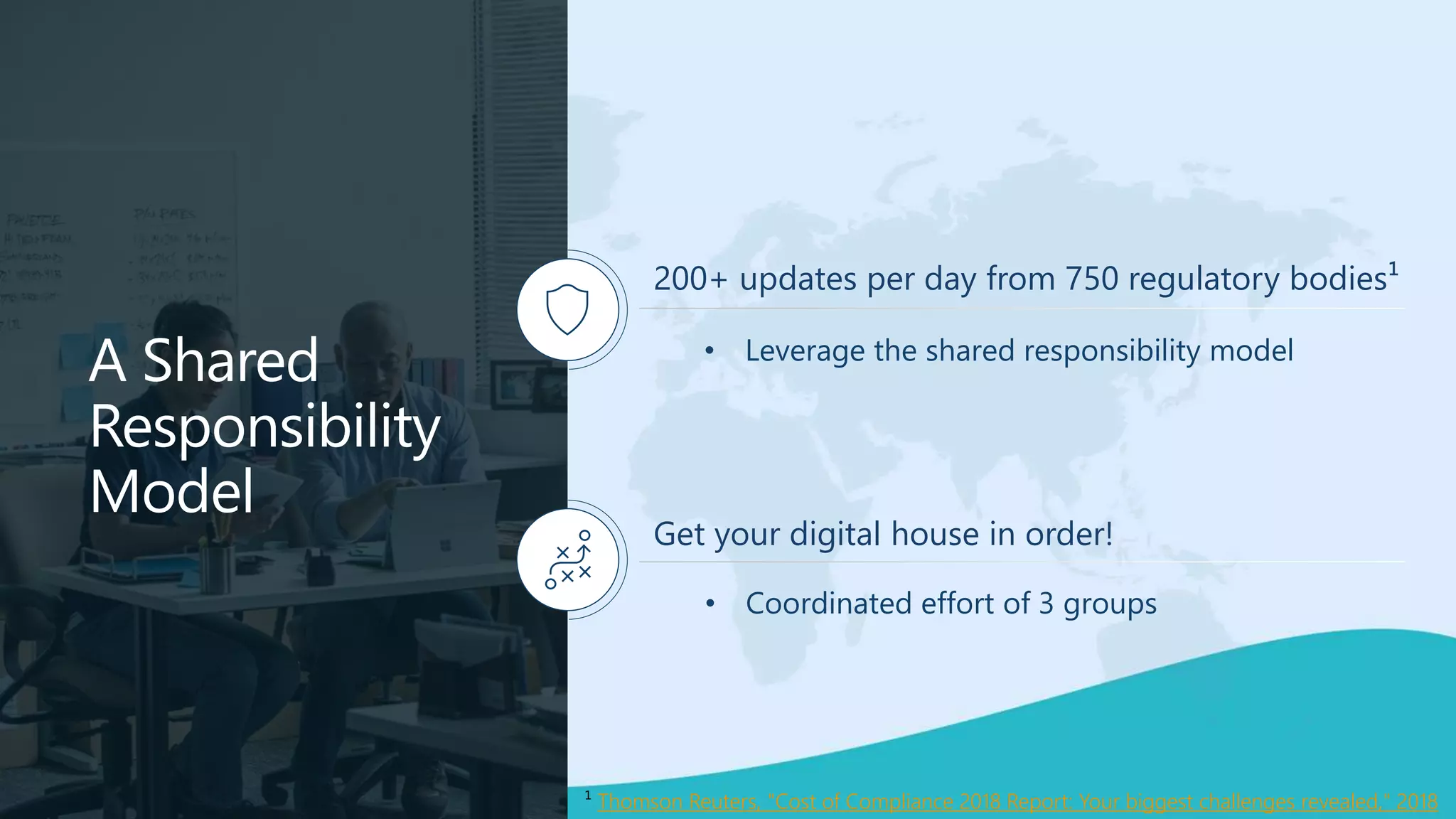
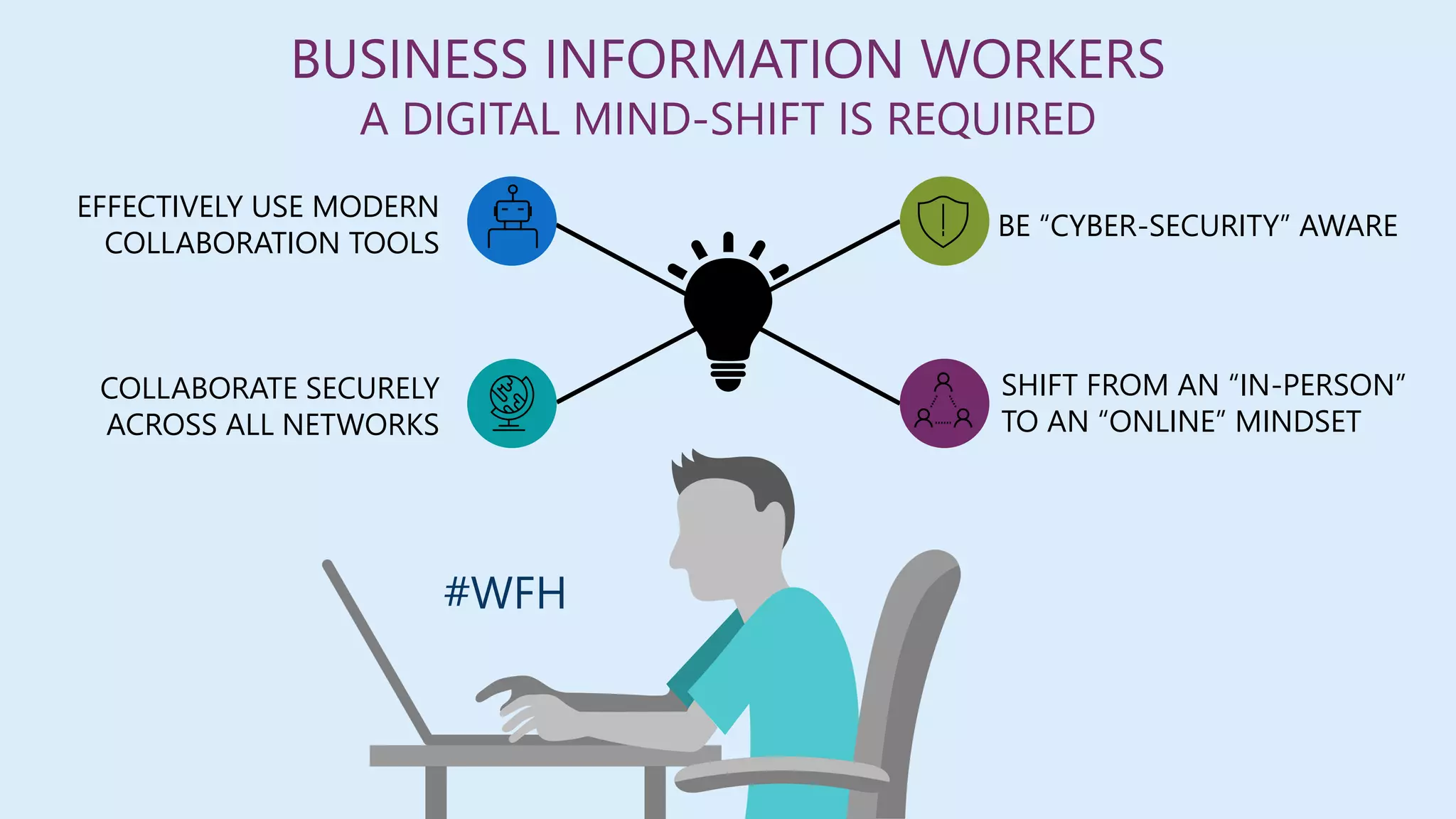
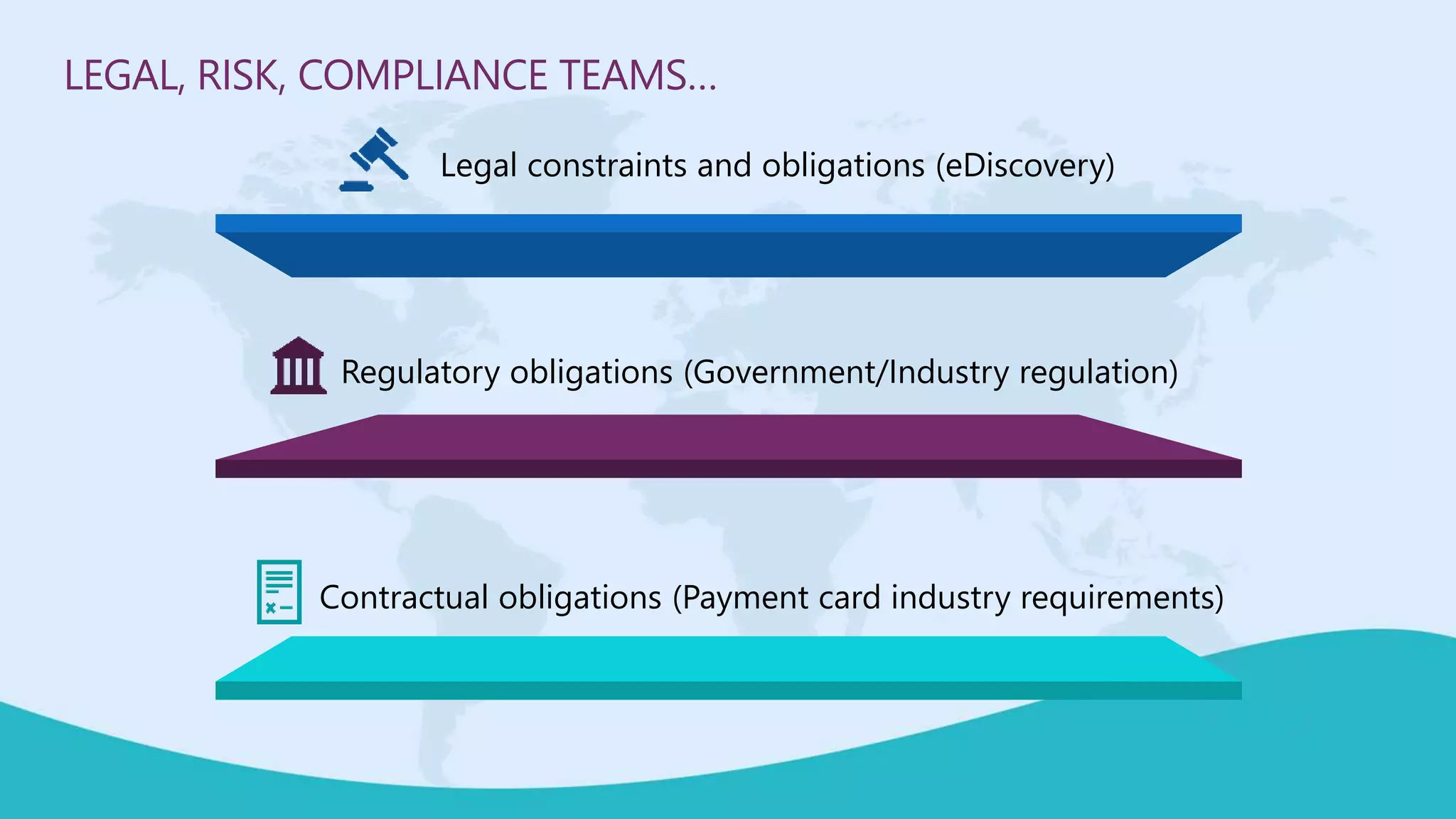
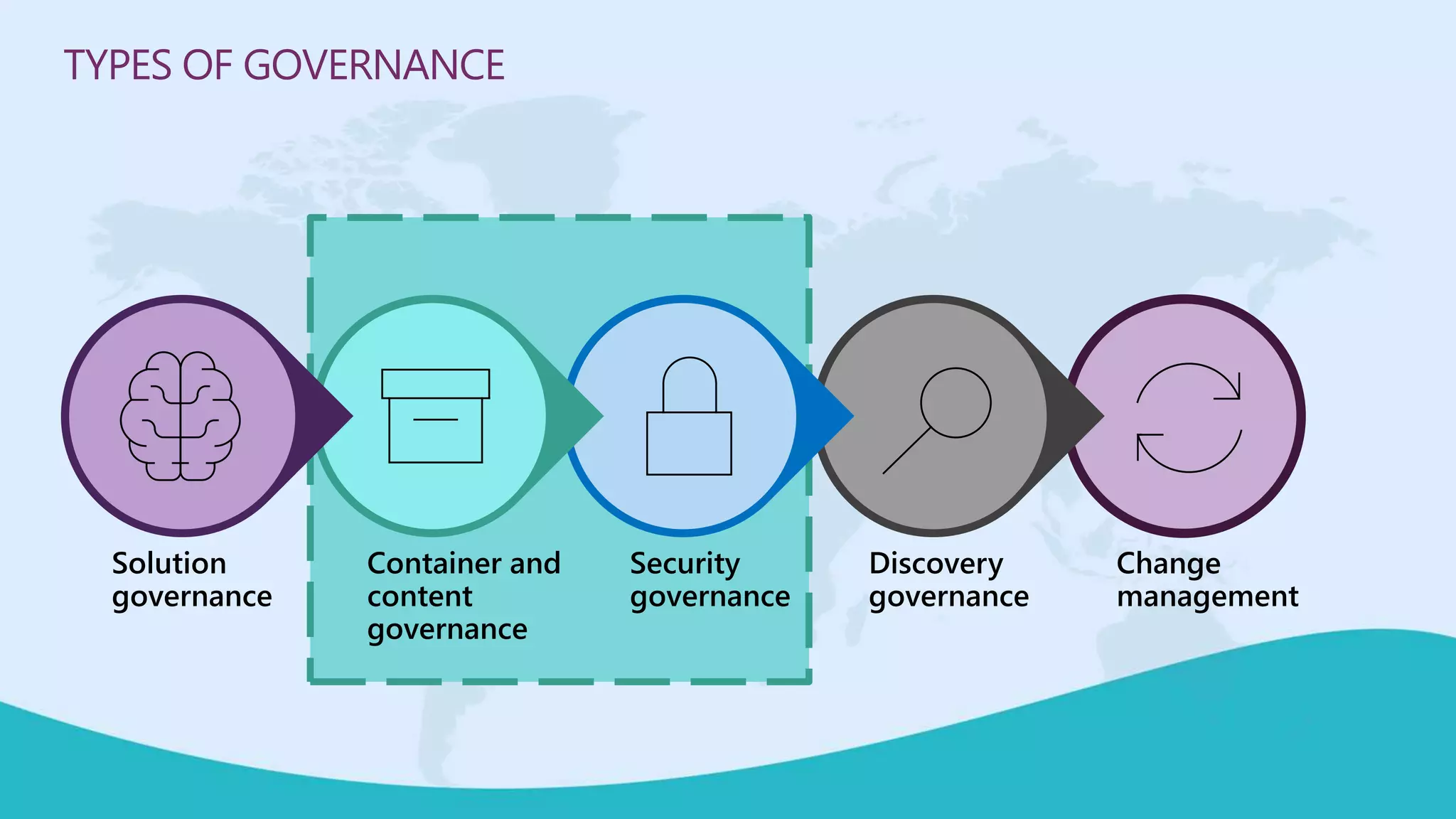
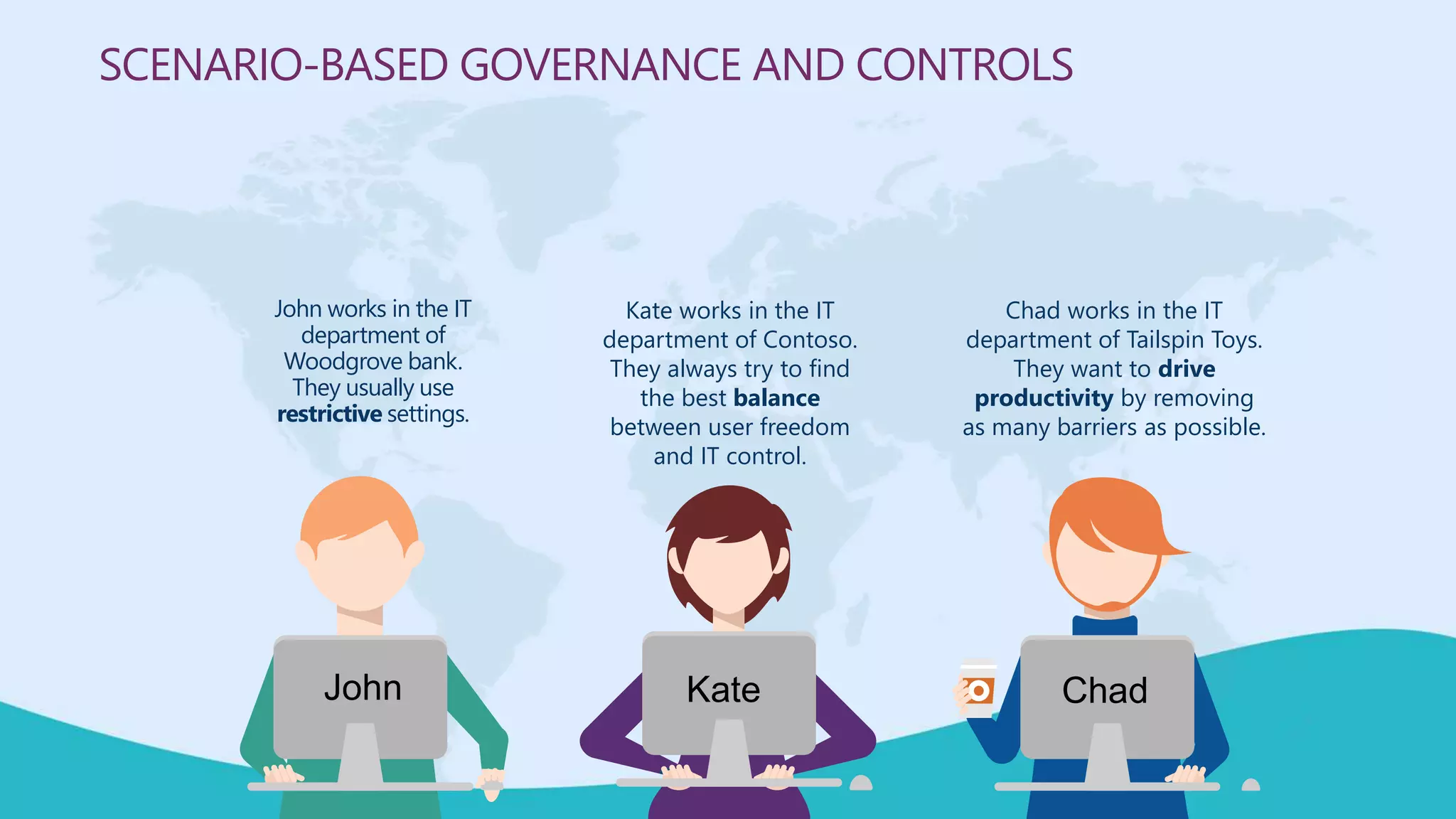
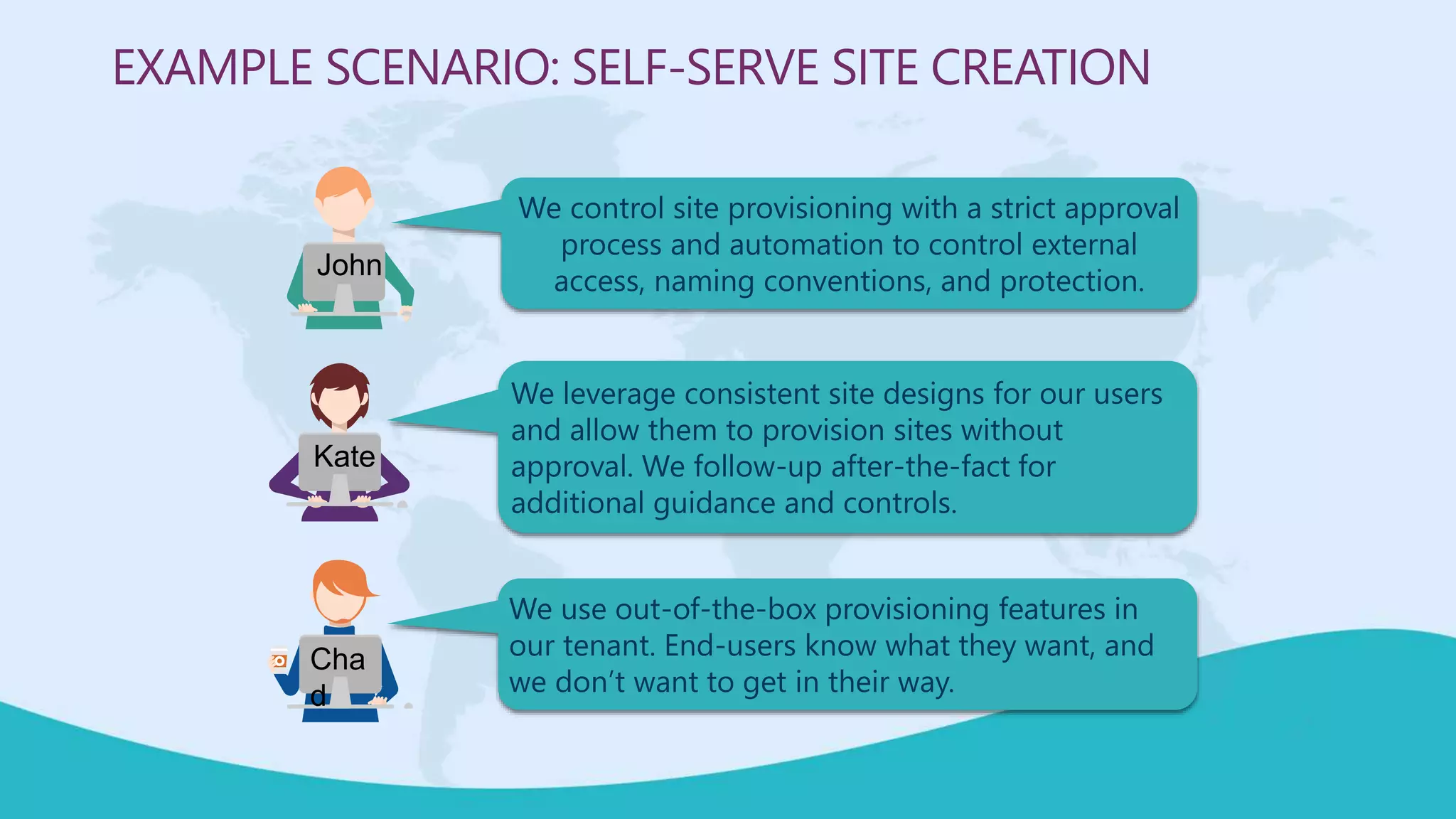
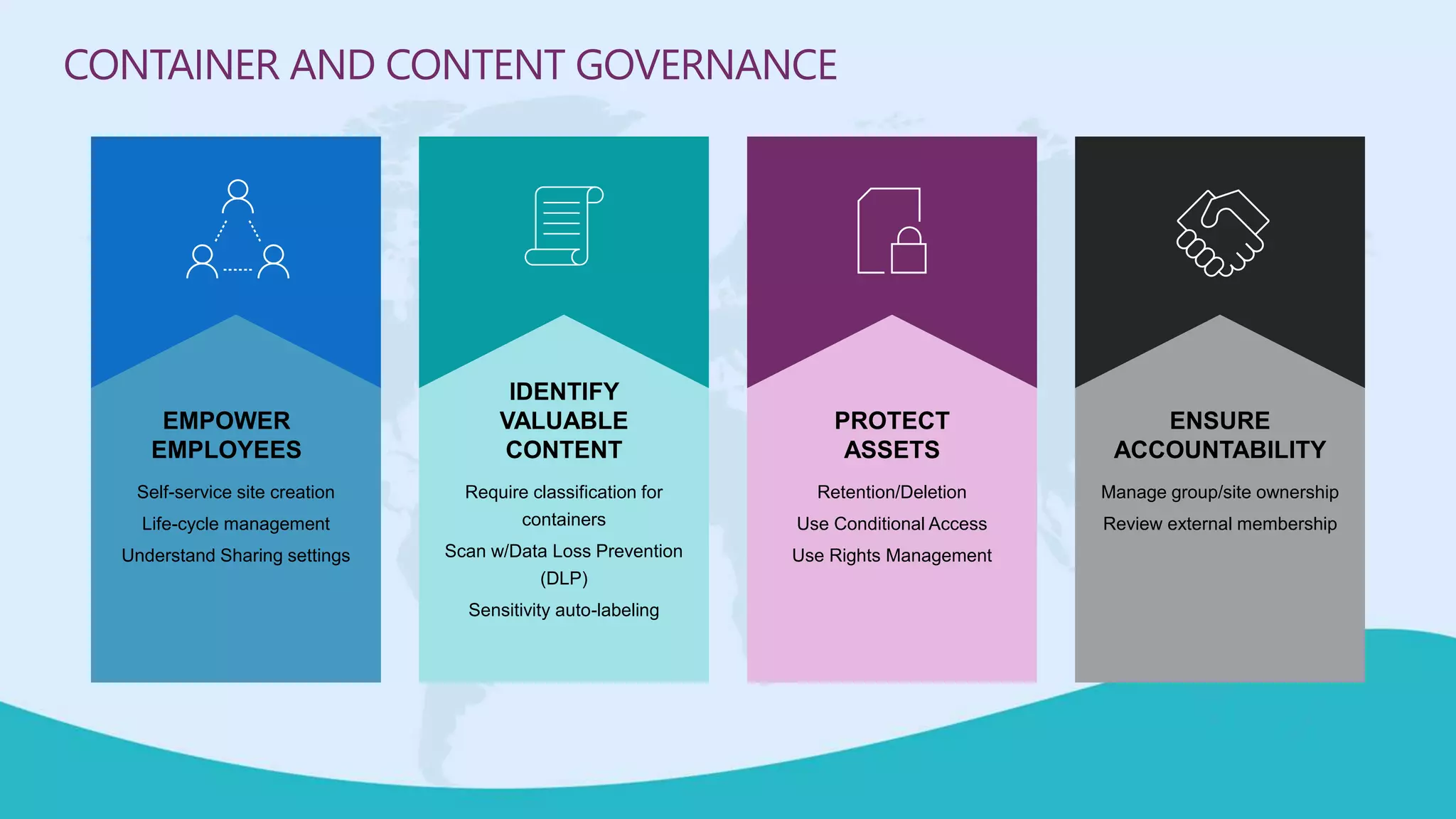
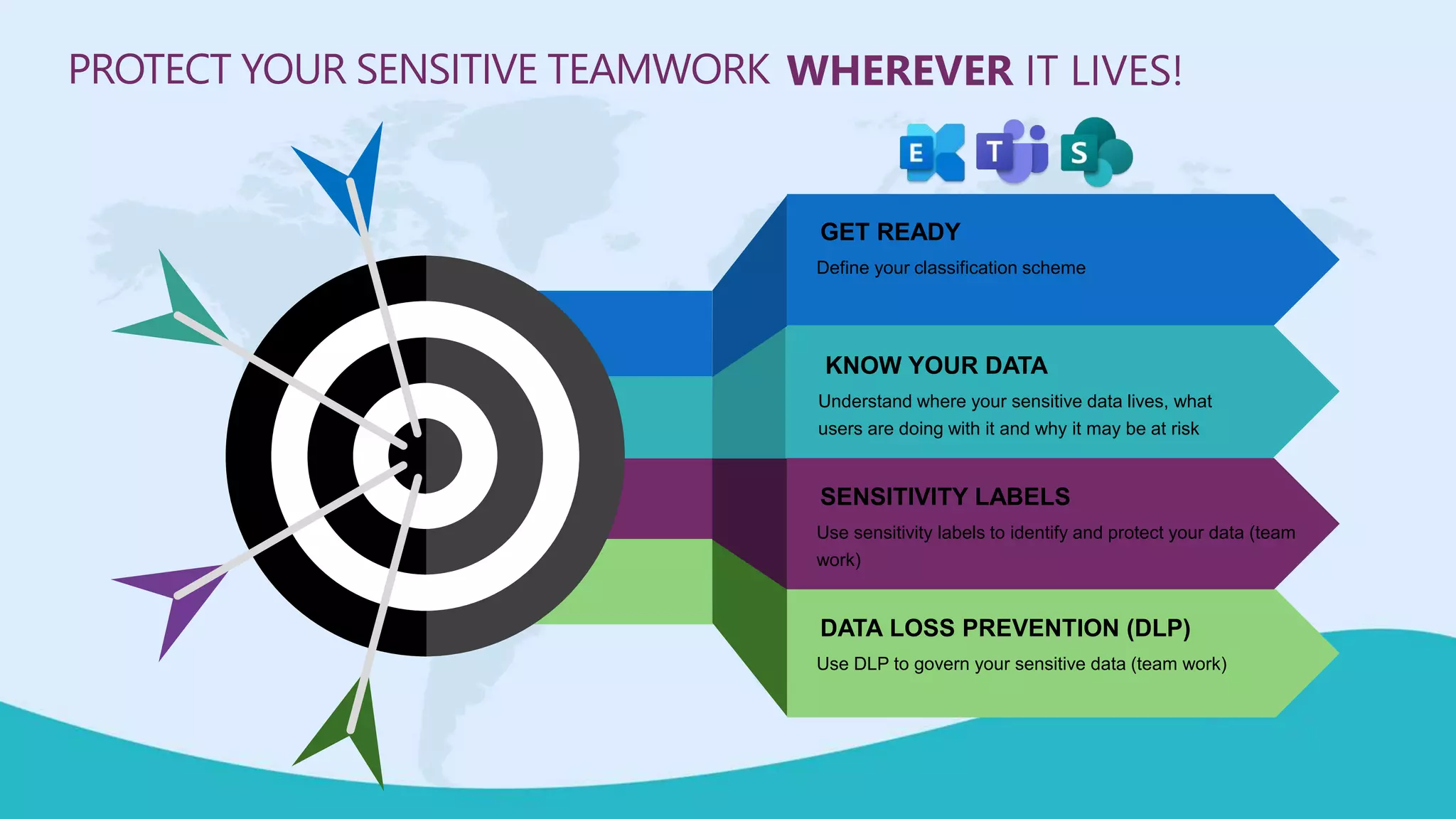
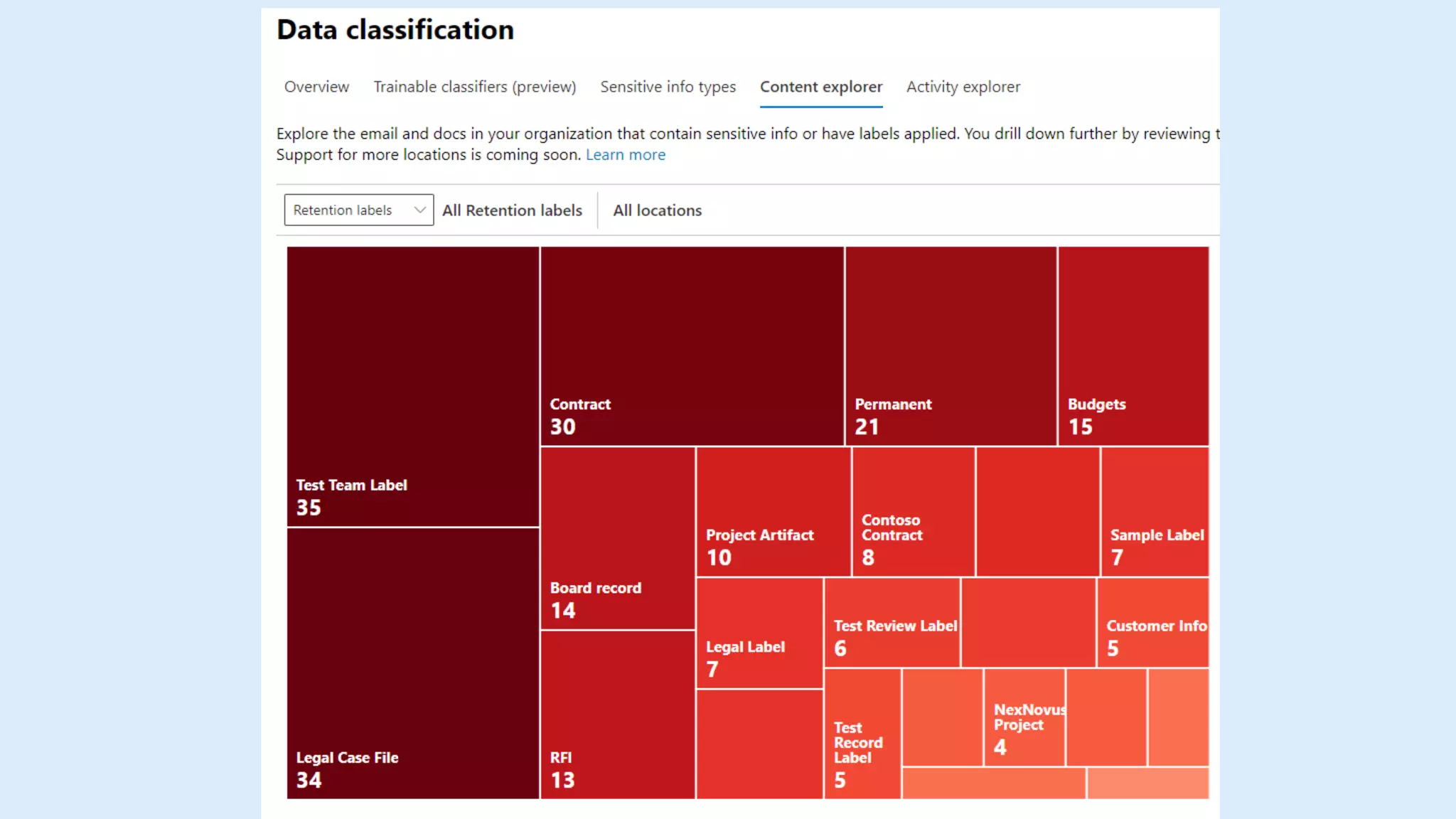
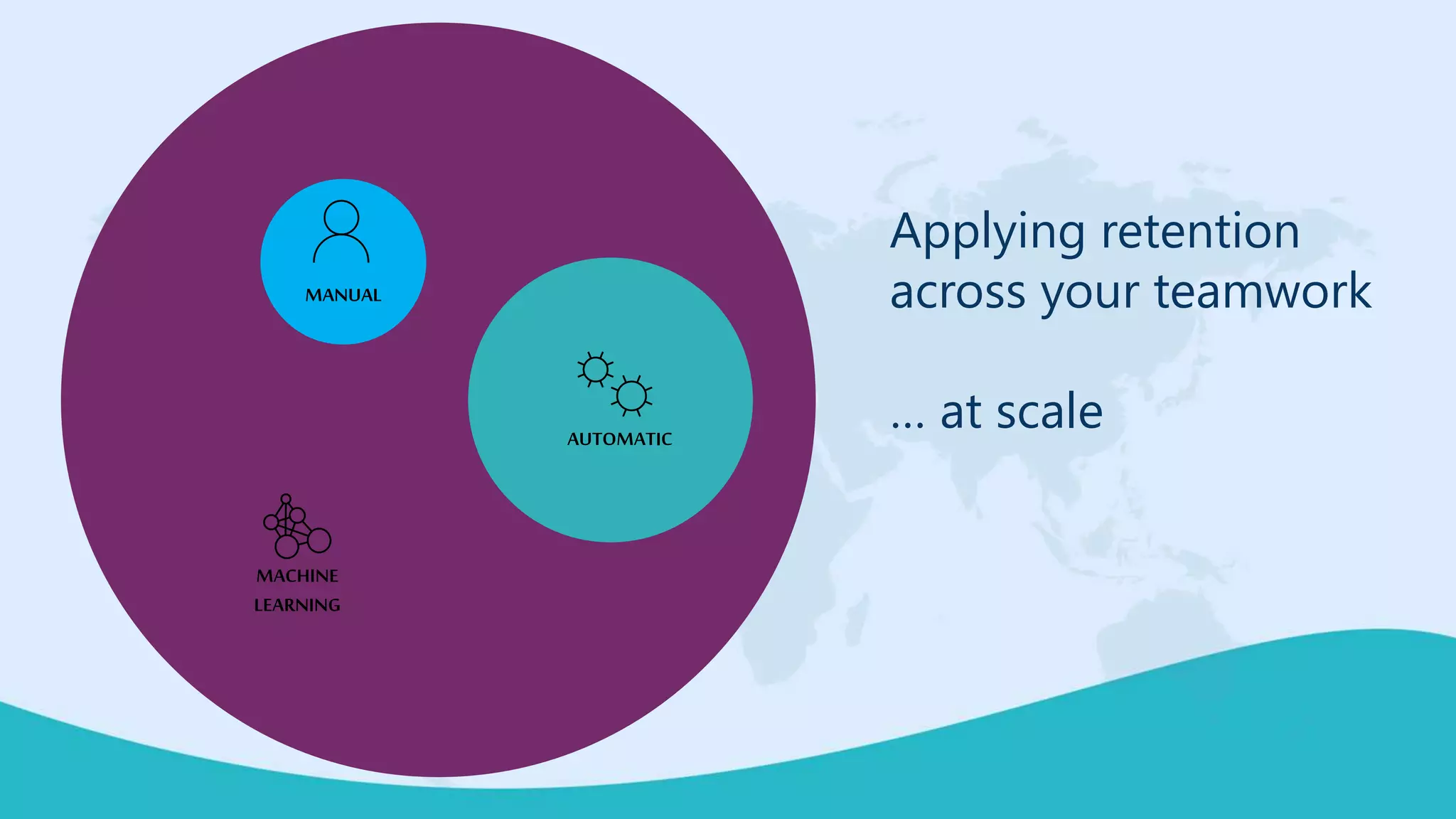
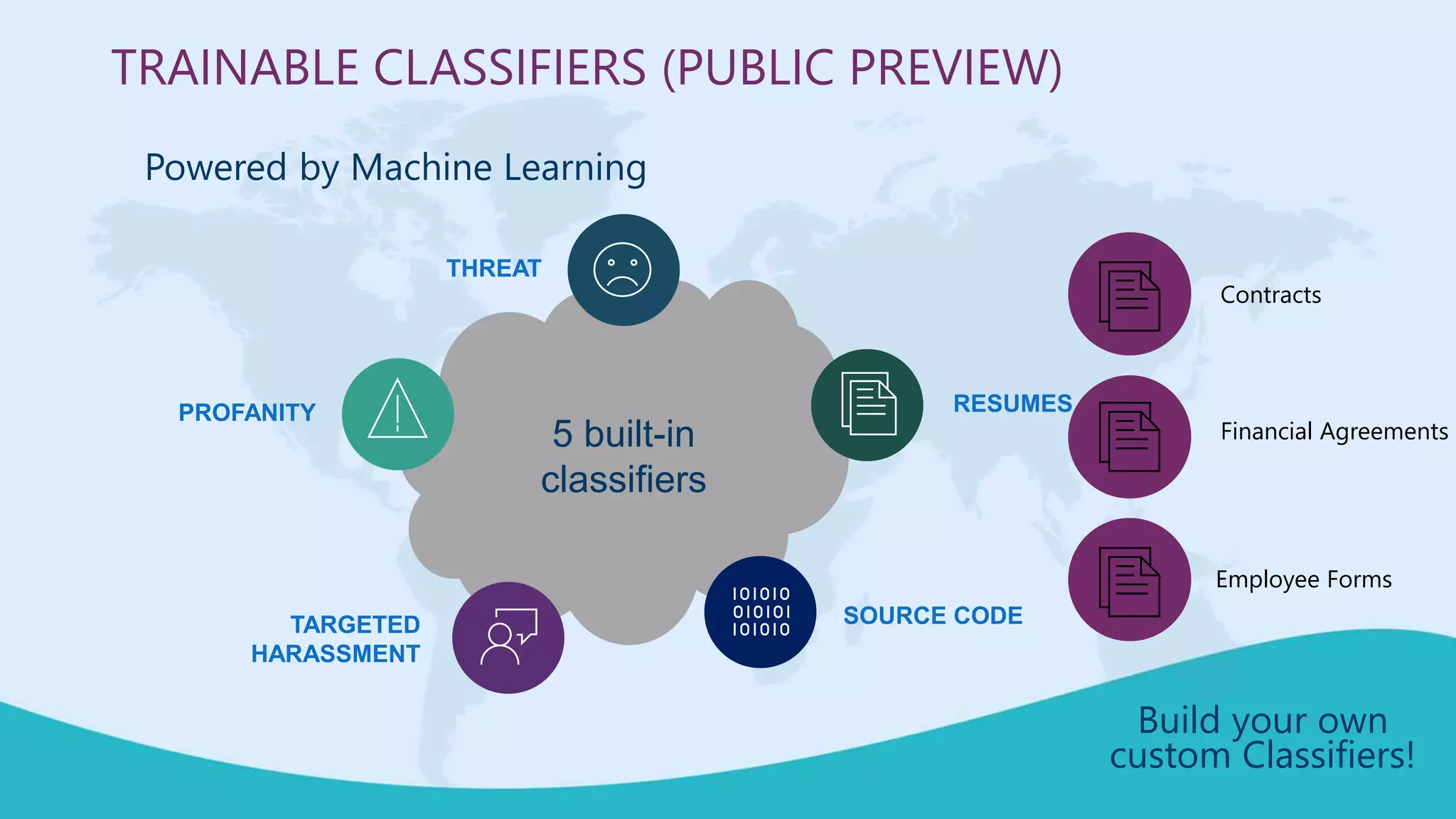
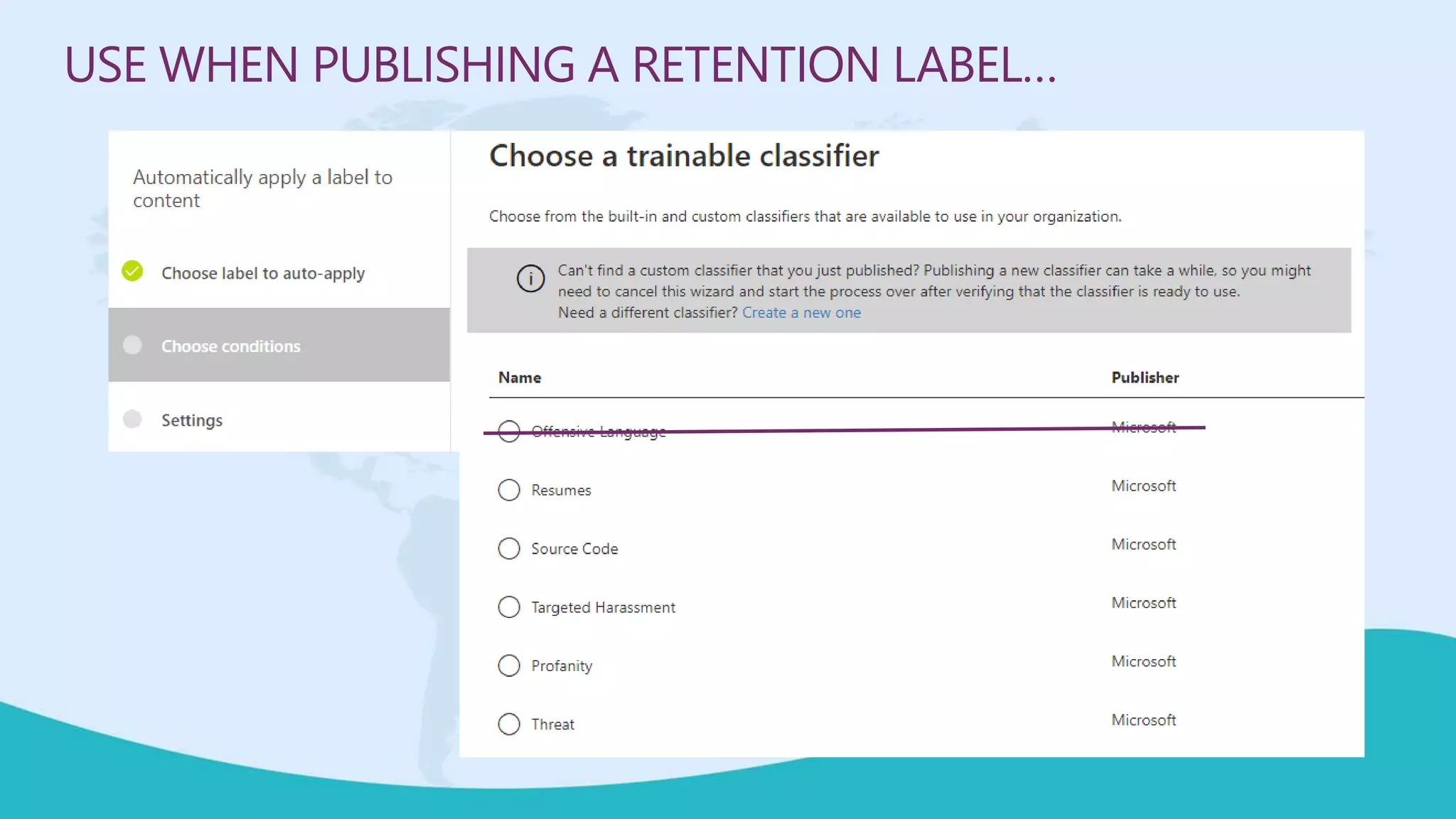
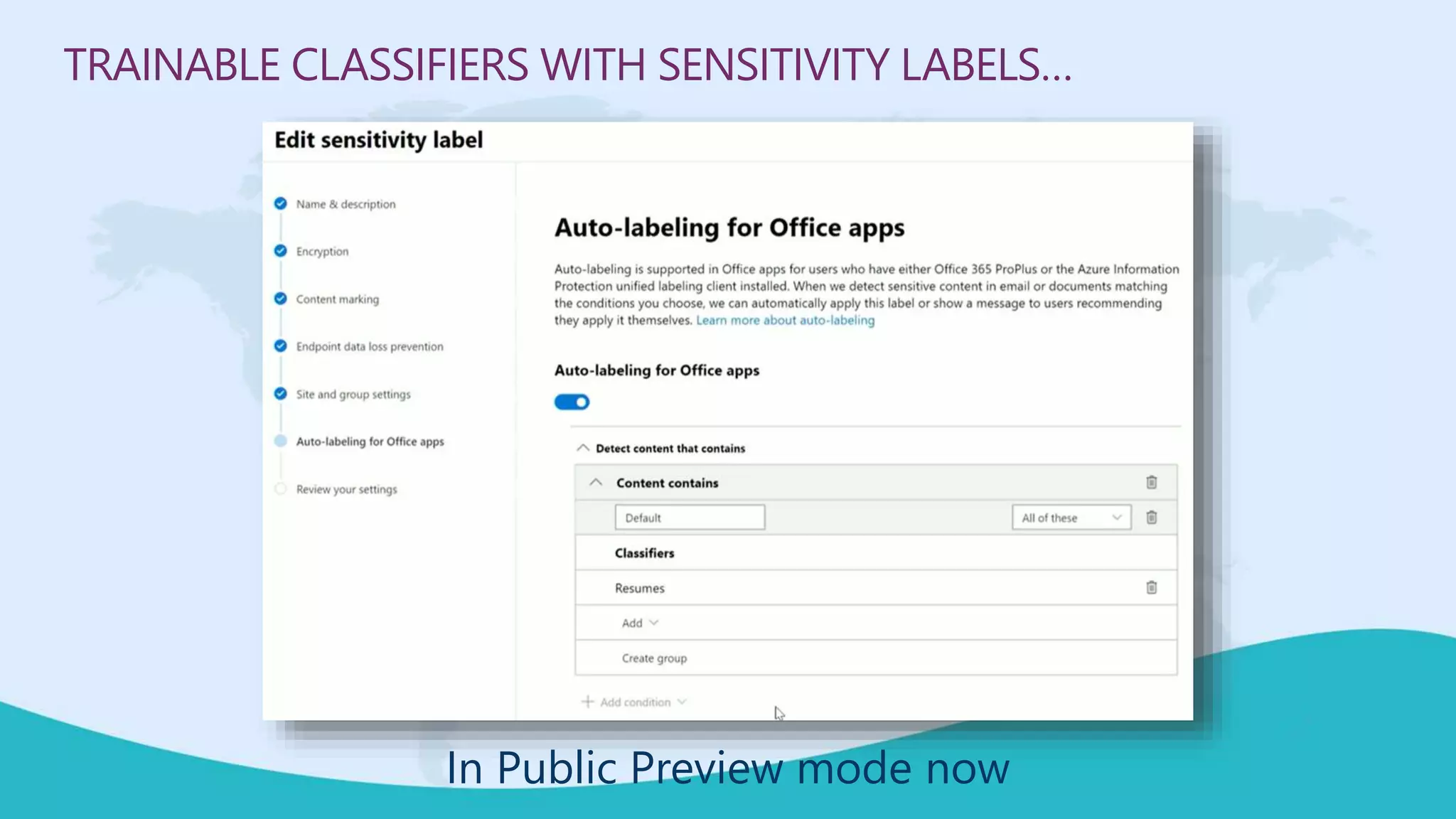
This document summarizes a virtual marathon event on May 27-28, 2020 about protecting teamwork across Microsoft 365. The event will include sessions on discovering and managing sensitive data, applying information governance policies across collaboration tools, collaborating securely with external parties, and other topics. Joanne Klein will be the main presenter. She is an independent Microsoft 365 consultant and Microsoft MVP who focuses on data protection, retention, governance, and eDiscovery.