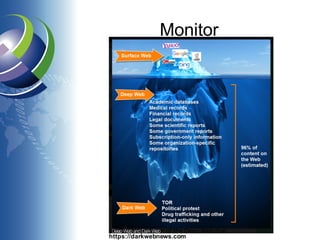
The document discusses Data Loss Prevention (DLP), outlining its definition, importance, and strategies for managing data loss risks. It emphasizes the need for awareness, classification, control, and response to data threats while highlighting the evolving landscape of data breaches and the necessity for proactive measures. The text also touches on the future of DLP, including the use of artificial intelligence and the importance of training users and utilizing existing tools.