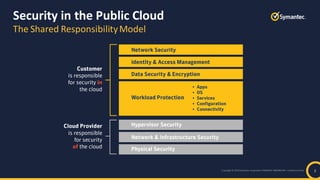
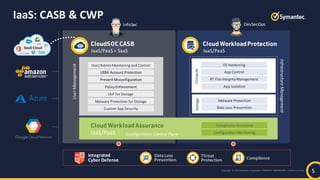
The document outlines best practices for cloud security in 2019, emphasizing the importance of shared responsibility between security and development teams. It highlights challenges such as immature security practices and the inadequacy of traditional security tools for modern cloud environments. Recommendations include deploying DevSecOps, automating compliance, and ensuring proper configuration to protect data across various cloud services.