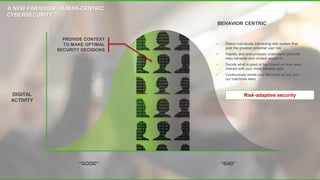
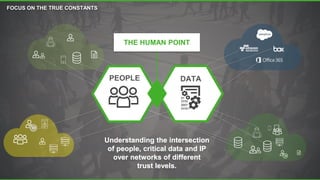
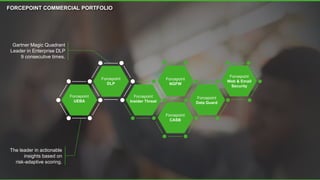
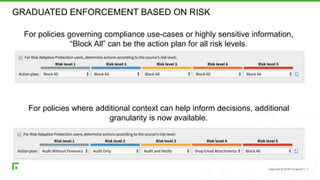
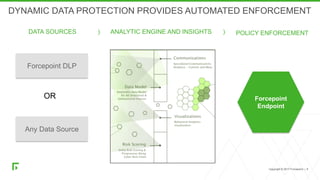
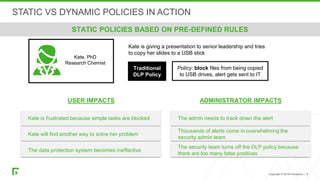
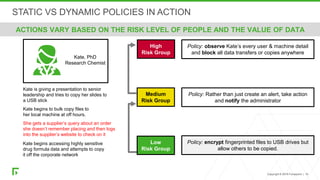
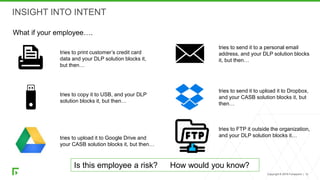
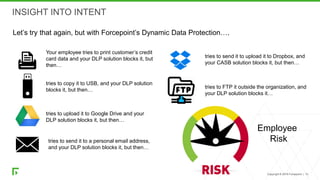
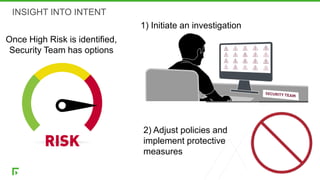
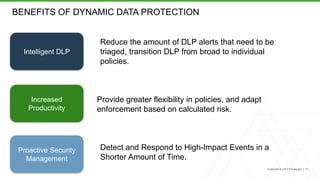
The document discusses a new human-centric approach to cybersecurity that focuses on behavior-centric digital activity and risk-adaptive security, contrasting traditional static policies that struggle to adapt in dynamic environments. It emphasizes the need for continuous evaluation of user interactions with sensitive data to determine potential risks and make informed security decisions. The importance of dynamic data protection is highlighted, showcasing its benefits in reducing alerts and increasing efficiency through more granular controls based on risk levels.