Data classification-policy
•
3 likes•1,419 views
Data classification-policy
Report
Share
Report
Share
Download to read offline
Recommended
18 Tips for Data Classification - Data Sheet by Secure Islands

Making Data Classification Work for You - 18 Things to Consider When Choosing Data Classification Solutions.
For more information, please visit: http://www.secureislands.com/solutions-classification/
Data Loss Prevention (DLP) - Fundamental Concept - Eryk

Presented at APTIKNAS (Indonesia ICT Business Association) DKI Jakarta regular webinar.
Title:Data Loss Prevention: Fundamental Concept in Enabling DLP System
2 July 2020
Technology Overview - Symantec Data Loss Prevention (DLP)

The presentation provides the following:
- Symantec Corporate Overview
- Solution Portfolio of Symantec
- Symantec Data Loss Prevention - Introduction
- Symantec Data Loss Prevention - Components
- Symantec Data Loss Prevention - Features & Use Cases
- Symantec Data Loss Prevention - System Requirements
- Symantec Data Loss Prevention - Appendix (extra information)
This provides a brief overview of Symantec Data Loss Prevention (DLP). Please note all the information is based prior to May 2016 and the full integration of Blue Coat Systems's set of solutions.
Data Loss Prevention

Data loss is considered by security experts to be one of the most serious threats that businesses currently face.
Maintaining the confidentiality of personal information and data is an essential factor in operating a successful business. People must be able to trust that their service provider takes the appropriate measures to implement security controls that will ultimately protect their privacy.
However, some of the largest and most reputable organizations have fallen victim to data loss security breaches resulting in significant legal, financial, and reputation loss, including [1]:
The Bank of America: Losing the personal employee information of over one million employees
The United States Government: Losing data related to the military
Heartland Payment Systems: Transferring credit card information and other personal records of over 130 million customers
In 2013, it was estimated that data breaches had resulted in the exploitation of over 800 million personal records [2]. This number is also expected to rise over the next several years given the advanced tools that cybercriminals use to steal information and data.
Interestingly, it is not just cybercriminals who represent a threat as:
64% of data loss is caused by well-meaning insiders.
50% of employees leave with data.
$3.5 million average cost of a security breach.
Considering these extensive data breaches, it is practical for organizations to understand where their critical data is located and understanding current security controls that can stop data loss.
Data Loss Prevention (DLP) solutions locate critical and personal data for organizations and help prevent data loss. By having a deeper understanding of efficient DLP security controls, you will help protect the reputation of your organization.
For more information contact: rkopaee@riskview.ca
https://www.threatview.ca
http://www.riskview.ca
Personal Data Protection in Indonesia

Personal Data Protection from regulation and technical perspectives.
Presented at Universitas Negeri Makassar Webinar
Recommended
18 Tips for Data Classification - Data Sheet by Secure Islands

Making Data Classification Work for You - 18 Things to Consider When Choosing Data Classification Solutions.
For more information, please visit: http://www.secureislands.com/solutions-classification/
Data Loss Prevention (DLP) - Fundamental Concept - Eryk

Presented at APTIKNAS (Indonesia ICT Business Association) DKI Jakarta regular webinar.
Title:Data Loss Prevention: Fundamental Concept in Enabling DLP System
2 July 2020
Technology Overview - Symantec Data Loss Prevention (DLP)

The presentation provides the following:
- Symantec Corporate Overview
- Solution Portfolio of Symantec
- Symantec Data Loss Prevention - Introduction
- Symantec Data Loss Prevention - Components
- Symantec Data Loss Prevention - Features & Use Cases
- Symantec Data Loss Prevention - System Requirements
- Symantec Data Loss Prevention - Appendix (extra information)
This provides a brief overview of Symantec Data Loss Prevention (DLP). Please note all the information is based prior to May 2016 and the full integration of Blue Coat Systems's set of solutions.
Data Loss Prevention

Data loss is considered by security experts to be one of the most serious threats that businesses currently face.
Maintaining the confidentiality of personal information and data is an essential factor in operating a successful business. People must be able to trust that their service provider takes the appropriate measures to implement security controls that will ultimately protect their privacy.
However, some of the largest and most reputable organizations have fallen victim to data loss security breaches resulting in significant legal, financial, and reputation loss, including [1]:
The Bank of America: Losing the personal employee information of over one million employees
The United States Government: Losing data related to the military
Heartland Payment Systems: Transferring credit card information and other personal records of over 130 million customers
In 2013, it was estimated that data breaches had resulted in the exploitation of over 800 million personal records [2]. This number is also expected to rise over the next several years given the advanced tools that cybercriminals use to steal information and data.
Interestingly, it is not just cybercriminals who represent a threat as:
64% of data loss is caused by well-meaning insiders.
50% of employees leave with data.
$3.5 million average cost of a security breach.
Considering these extensive data breaches, it is practical for organizations to understand where their critical data is located and understanding current security controls that can stop data loss.
Data Loss Prevention (DLP) solutions locate critical and personal data for organizations and help prevent data loss. By having a deeper understanding of efficient DLP security controls, you will help protect the reputation of your organization.
For more information contact: rkopaee@riskview.ca
https://www.threatview.ca
http://www.riskview.ca
Personal Data Protection in Indonesia

Personal Data Protection from regulation and technical perspectives.
Presented at Universitas Negeri Makassar Webinar
Privacy-ready Data Protection Program Implementation

Presented at CDEF 16th Meetup at 18 August 2022.
Title:
Privacy-ready Data Protection Program Implementation
Topics:
- Why data protection is important
- Data Privacy Program Domain
- Operationalize Data Privacy Program
- Privacy-aligned Information Security Framework
- Roadmap to Protect Personal Data
- Privacy Management Technology
Introducing Data Loss Prevention 14

At the highest level, our mission continues to be about keeping our customers (companies and governments) safe from ever-evolving digital threats, so they are confident to move business forward. Our strategy to accomplish this mission centers around four key pillars: Advanced Threat Protection, Information Protection for On Premise and Cloud, Security as a Service -- all anchored by a Unified Security Analytics Platform. Symantec Data Loss Prevention is a foundational product in the Information Protection for On Premise and Cloud pillar.
Everyone knows that storing and accessing data and applications in the cloud and on mobile devices provides makes work much easier and productive by allowing employees to work everywhere they need to.
It allows for great business agility – applications are always up to date, new functionality and processes can be deployed and activated quickly and organizations can adjust things on the fly if they need to.
It also brings the convenience factor – all employees to work in the way that they need to, collaboration and sharing is made vastly easier with cloud applications and storage.
But it brings with it all the challenges of securing devices and applications that your don’t own, and whilst saying NO might be the right thing for security, end users will find a way around it. Right now, close to 30% of employees use their personal devices for work. And that number is on the rise, potentially turning BYOD into Bring Your Own Disaster.
How to Strengthen Enterprise Data Governance with Data Quality

If your organization is in a highly-regulated industry – or relies on data for competitive advantage – data governance is undoubtedly a top priority. Whether you’re focused on “defensive” data governance (supporting regulatory compliance and risk management) or “offensive” data governance (extracting the maximum value from your data assets, and minimizing the cost of bad data), data quality plays a critical role in ensuring success.
Join our webinar to learn how enterprise data quality drives stronger data governance, including:
The overlaps between data governance and data quality
The “data” dependencies of data governance – and how data quality addresses them
Key considerations for deploying data quality for data governance
Activate Data Governance Using the Data Catalog

Data Governance programs depend on the activation of data stewards that are held formally accountable for how they manage data. The data catalog is a critical tool to enable your stewards to contribute and interact with an inventory of metadata about the data definition, production, and usage. This interaction is active Data Governance in the truest sense of the word.
In this RWDG webinar, Bob Seiner will share tips and techniques focused on activating your data stewards through a data catalog. Data Governance programs that involve stewards in daily activities are more likely to demonstrate value from their data-intensive investments.
Bob will address the following in this webinar:
- A comparison of active and passive Data Governance
- What it means to have an active Data Governance program
- How a data catalog tool can be used to activate data stewards
- The role a data catalog plays in Data Governance
- The metadata in the data catalog will not govern itself
Data Governance Program Powerpoint Presentation Slides

"You can download this product from SlideTeam.net"
Showcase data management practices with our content ready Data Governance Program PowerPoint Presentation Slides. Establish processes to ensure effective data management using Information Architecture PPT slides. Data management can enable better planning, minimize rework, optimize staff effectiveness. The information technology governance PowerPoint complete deck contains ready to use slides such as the need for data governance, why companies suffer from data governance, automated data governance, framework, roles and responsibilities, ways to establish data management process, improvement roadmap, etc. The easy to understand data migration program PPT visuals are fully editable. You can modify, color, text, and font size. It has relevant templates to cater to your business needs. Utilize visually appealing information architecture PowerPoint templates to define a set of data management procedures and plans. Data governance is a quality control discipline, assess data accuracy consistency and timeliness. Download this professionally designed information governance program presentation deck to manage, improve, monitor and protect organizational information. Clientele grows with our Data Governance Program Powerpoint Presentation Slides. Give a big boost to your customer base. https://bit.ly/3EViOt3
Data Architecture Best Practices for Advanced Analytics

Many organizations are immature when it comes to data and analytics use. The answer lies in delivering a greater level of insight from data, straight to the point of need.
There are so many Data Architecture best practices today, accumulated from years of practice. In this webinar, William will look at some Data Architecture best practices that he believes have emerged in the past two years and are not worked into many enterprise data programs yet. These are keepers and will be required to move towards, by one means or another, so it’s best to mindfully work them into the environment.
Data Governance Takes a Village (So Why is Everyone Hiding?)

Data governance represents both an obstacle and opportunity for enterprises everywhere. And many individuals may hesitate to embrace the change. Yet if led well, a governance initiative has the potential to launch a data community that drives innovation and data-driven decision-making for the wider business. (And yes, it can even be fun!). So how do you build a roadmap to success?
This session will gather four governance experts, including Mary Williams, Associate Director, Enterprise Data Governance at Exact Sciences, and Bob Seiner, author of Non-Invasive Data Governance, for a roundtable discussion about the challenges and opportunities of leading a governance initiative that people embrace. Join this webinar to learn:
- How to build an internal case for data governance and a data catalog
- Tips for picking a use case that builds confidence in your program
- How to mature your program and build your data community
Data Protection Indonesia: Basic Regulation and Technical Aspects_Eryk

Presented at Orang Siber Indonesia webinar.
11 July 2020
Topic: Data Protection: Basic Regulation and Technical Aspects
This presentation covers:
> Indonesia Data Protection Bill
> Data Masking
> Identity & Access Management
> Data Loss Prevention
Join us (for Indonesian):
t.me/orangsiber
t.me/dataprotectionid
Data Catalog for Better Data Discovery and Governance

Watch full webinar here: https://buff.ly/2Vq9FR0
Data catalogs are en vogue answering critical data governance questions like “Where all does my data reside?” “What other entities are associated with my data?” “What are the definitions of the data fields?” and “Who accesses the data?” Data catalogs maintain the necessary business metadata to answer these questions and many more. But that’s not enough. For it to be useful, data catalogs need to deliver these answers to the business users right within the applications they use.
In this session, you will learn:
*How data catalogs enable enterprise-wide data governance regimes
*What key capability requirements should you expect in data catalogs
*How data virtualization combines dynamic data catalogs with delivery
Introduction to Data Governance

This introduction to data governance presentation covers the inter-related DM foundational disciplines (Data Integration / DWH, Business Intelligence and Data Governance). Some of the pitfalls and success factors for data governance.
• IM Foundational Disciplines
• Cross-functional Workflow Exchange
• Key Objectives of the Data Governance Framework
• Components of a Data Governance Framework
• Key Roles in Data Governance
• Data Governance Committee (DGC)
• 4 Data Governance Policy Areas
• 3 Challenges to Implementing Data Governance
• Data Governance Success Factors
Data Profiling, Data Catalogs and Metadata Harmonisation

These notes discuss the related topics of Data Profiling, Data Catalogs and Metadata Harmonisation. It describes a detailed structure for data profiling activities. It identifies various open source and commercial tools and data profiling algorithms. Data profiling is a necessary pre-requisite activity in order to construct a data catalog. A data catalog makes an organisation’s data more discoverable. The data collected during data profiling forms the metadata contained in the data catalog. This assists with ensuring data quality. It is also a necessary activity for Master Data Management initiatives. These notes describe a metadata structure and provide details on metadata standards and sources.
Data Leakage Prevention (DLP)

Data Leakage is an important concern for the business organizations in this increasingly networked world these days. Unauthorized disclosure may have serious consequences for an organization in both long term and short term. Risks include losing clients and stakeholder confidence, tarnishing of brand image, landing in unwanted lawsuits, and overall losing goodwill and market share in the industry.
Common Practice in Data Privacy Program Management

This material was presented at Orang Siber Indonesia regular webinar.
Content:
> Understanding privacy management
> Global privacy news
> Understanding privacy regulations and frameworks
> Data Privacy Program Management practices
Data Governance

TDWI Presentation explaining how Enterprise Data Governance can be utilized to support Business Strategy.
How to Make a Data Governance Program that Lasts

Traditional data governance initiatives fail by focusing too heavily on policies, compliance, and enforcement, which quickly lose business interest and support. This leaves data management and governance leaders having to continually make the case for data governance to secure business adoption. Join Cameron, VP, Product Management, Precisely, as he shares a lean, business-first data governance approach that connects key initiatives to governance capabilities and quickly delivers business value for the long-term. He will give examples of organizations worldwide who have successfully implemented a data governance program by engaging with key stakeholders using innovative techniques such as gamification and data catalog scavenger hunts.
Data Loss Prevention

DATA LOSS PREVENTION ENSURES CRITICAL INFORMATION ARE KEPT SAFELY AT THE CORPORATE NETWORK AND HELPS ADMINISTRATOR CONTROL THE DATA WHAT
END-USERS WISH TO TRANSFER.
You Need a Data Catalog. Do You Know Why?

The data catalog has become a popular discussion topic within data management and data governance circles. A data catalog is a central repository that contains metadata for describing data sets, how they are defined, and where to find them. TDWI research indicates that implementing a data catalog is a top priority among organizations we survey. The data catalog can also play an important part in the governance process. It provides features that help ensure data quality, compliance, and that trusted data is used for analysis. Without an in-depth knowledge of data and associated metadata, organizations cannot truly safeguard and govern their data.
Join this on-demand webinar to learn more about the data catalog and its role in data governance efforts.
Topics include:
· Data management challenges and priorities
· The modern data catalog – what it is and why it is important
· The role of the modern data catalog in your data quality and governance programs
· The kinds of information that should be in your data catalog and why
Data Protection: We\'re In This Together

All workers in a business are responsible for the protection of their sensitive data.
More Related Content
What's hot
Privacy-ready Data Protection Program Implementation

Presented at CDEF 16th Meetup at 18 August 2022.
Title:
Privacy-ready Data Protection Program Implementation
Topics:
- Why data protection is important
- Data Privacy Program Domain
- Operationalize Data Privacy Program
- Privacy-aligned Information Security Framework
- Roadmap to Protect Personal Data
- Privacy Management Technology
Introducing Data Loss Prevention 14

At the highest level, our mission continues to be about keeping our customers (companies and governments) safe from ever-evolving digital threats, so they are confident to move business forward. Our strategy to accomplish this mission centers around four key pillars: Advanced Threat Protection, Information Protection for On Premise and Cloud, Security as a Service -- all anchored by a Unified Security Analytics Platform. Symantec Data Loss Prevention is a foundational product in the Information Protection for On Premise and Cloud pillar.
Everyone knows that storing and accessing data and applications in the cloud and on mobile devices provides makes work much easier and productive by allowing employees to work everywhere they need to.
It allows for great business agility – applications are always up to date, new functionality and processes can be deployed and activated quickly and organizations can adjust things on the fly if they need to.
It also brings the convenience factor – all employees to work in the way that they need to, collaboration and sharing is made vastly easier with cloud applications and storage.
But it brings with it all the challenges of securing devices and applications that your don’t own, and whilst saying NO might be the right thing for security, end users will find a way around it. Right now, close to 30% of employees use their personal devices for work. And that number is on the rise, potentially turning BYOD into Bring Your Own Disaster.
How to Strengthen Enterprise Data Governance with Data Quality

If your organization is in a highly-regulated industry – or relies on data for competitive advantage – data governance is undoubtedly a top priority. Whether you’re focused on “defensive” data governance (supporting regulatory compliance and risk management) or “offensive” data governance (extracting the maximum value from your data assets, and minimizing the cost of bad data), data quality plays a critical role in ensuring success.
Join our webinar to learn how enterprise data quality drives stronger data governance, including:
The overlaps between data governance and data quality
The “data” dependencies of data governance – and how data quality addresses them
Key considerations for deploying data quality for data governance
Activate Data Governance Using the Data Catalog

Data Governance programs depend on the activation of data stewards that are held formally accountable for how they manage data. The data catalog is a critical tool to enable your stewards to contribute and interact with an inventory of metadata about the data definition, production, and usage. This interaction is active Data Governance in the truest sense of the word.
In this RWDG webinar, Bob Seiner will share tips and techniques focused on activating your data stewards through a data catalog. Data Governance programs that involve stewards in daily activities are more likely to demonstrate value from their data-intensive investments.
Bob will address the following in this webinar:
- A comparison of active and passive Data Governance
- What it means to have an active Data Governance program
- How a data catalog tool can be used to activate data stewards
- The role a data catalog plays in Data Governance
- The metadata in the data catalog will not govern itself
Data Governance Program Powerpoint Presentation Slides

"You can download this product from SlideTeam.net"
Showcase data management practices with our content ready Data Governance Program PowerPoint Presentation Slides. Establish processes to ensure effective data management using Information Architecture PPT slides. Data management can enable better planning, minimize rework, optimize staff effectiveness. The information technology governance PowerPoint complete deck contains ready to use slides such as the need for data governance, why companies suffer from data governance, automated data governance, framework, roles and responsibilities, ways to establish data management process, improvement roadmap, etc. The easy to understand data migration program PPT visuals are fully editable. You can modify, color, text, and font size. It has relevant templates to cater to your business needs. Utilize visually appealing information architecture PowerPoint templates to define a set of data management procedures and plans. Data governance is a quality control discipline, assess data accuracy consistency and timeliness. Download this professionally designed information governance program presentation deck to manage, improve, monitor and protect organizational information. Clientele grows with our Data Governance Program Powerpoint Presentation Slides. Give a big boost to your customer base. https://bit.ly/3EViOt3
Data Architecture Best Practices for Advanced Analytics

Many organizations are immature when it comes to data and analytics use. The answer lies in delivering a greater level of insight from data, straight to the point of need.
There are so many Data Architecture best practices today, accumulated from years of practice. In this webinar, William will look at some Data Architecture best practices that he believes have emerged in the past two years and are not worked into many enterprise data programs yet. These are keepers and will be required to move towards, by one means or another, so it’s best to mindfully work them into the environment.
Data Governance Takes a Village (So Why is Everyone Hiding?)

Data governance represents both an obstacle and opportunity for enterprises everywhere. And many individuals may hesitate to embrace the change. Yet if led well, a governance initiative has the potential to launch a data community that drives innovation and data-driven decision-making for the wider business. (And yes, it can even be fun!). So how do you build a roadmap to success?
This session will gather four governance experts, including Mary Williams, Associate Director, Enterprise Data Governance at Exact Sciences, and Bob Seiner, author of Non-Invasive Data Governance, for a roundtable discussion about the challenges and opportunities of leading a governance initiative that people embrace. Join this webinar to learn:
- How to build an internal case for data governance and a data catalog
- Tips for picking a use case that builds confidence in your program
- How to mature your program and build your data community
Data Protection Indonesia: Basic Regulation and Technical Aspects_Eryk

Presented at Orang Siber Indonesia webinar.
11 July 2020
Topic: Data Protection: Basic Regulation and Technical Aspects
This presentation covers:
> Indonesia Data Protection Bill
> Data Masking
> Identity & Access Management
> Data Loss Prevention
Join us (for Indonesian):
t.me/orangsiber
t.me/dataprotectionid
Data Catalog for Better Data Discovery and Governance

Watch full webinar here: https://buff.ly/2Vq9FR0
Data catalogs are en vogue answering critical data governance questions like “Where all does my data reside?” “What other entities are associated with my data?” “What are the definitions of the data fields?” and “Who accesses the data?” Data catalogs maintain the necessary business metadata to answer these questions and many more. But that’s not enough. For it to be useful, data catalogs need to deliver these answers to the business users right within the applications they use.
In this session, you will learn:
*How data catalogs enable enterprise-wide data governance regimes
*What key capability requirements should you expect in data catalogs
*How data virtualization combines dynamic data catalogs with delivery
Introduction to Data Governance

This introduction to data governance presentation covers the inter-related DM foundational disciplines (Data Integration / DWH, Business Intelligence and Data Governance). Some of the pitfalls and success factors for data governance.
• IM Foundational Disciplines
• Cross-functional Workflow Exchange
• Key Objectives of the Data Governance Framework
• Components of a Data Governance Framework
• Key Roles in Data Governance
• Data Governance Committee (DGC)
• 4 Data Governance Policy Areas
• 3 Challenges to Implementing Data Governance
• Data Governance Success Factors
Data Profiling, Data Catalogs and Metadata Harmonisation

These notes discuss the related topics of Data Profiling, Data Catalogs and Metadata Harmonisation. It describes a detailed structure for data profiling activities. It identifies various open source and commercial tools and data profiling algorithms. Data profiling is a necessary pre-requisite activity in order to construct a data catalog. A data catalog makes an organisation’s data more discoverable. The data collected during data profiling forms the metadata contained in the data catalog. This assists with ensuring data quality. It is also a necessary activity for Master Data Management initiatives. These notes describe a metadata structure and provide details on metadata standards and sources.
Data Leakage Prevention (DLP)

Data Leakage is an important concern for the business organizations in this increasingly networked world these days. Unauthorized disclosure may have serious consequences for an organization in both long term and short term. Risks include losing clients and stakeholder confidence, tarnishing of brand image, landing in unwanted lawsuits, and overall losing goodwill and market share in the industry.
Common Practice in Data Privacy Program Management

This material was presented at Orang Siber Indonesia regular webinar.
Content:
> Understanding privacy management
> Global privacy news
> Understanding privacy regulations and frameworks
> Data Privacy Program Management practices
Data Governance

TDWI Presentation explaining how Enterprise Data Governance can be utilized to support Business Strategy.
How to Make a Data Governance Program that Lasts

Traditional data governance initiatives fail by focusing too heavily on policies, compliance, and enforcement, which quickly lose business interest and support. This leaves data management and governance leaders having to continually make the case for data governance to secure business adoption. Join Cameron, VP, Product Management, Precisely, as he shares a lean, business-first data governance approach that connects key initiatives to governance capabilities and quickly delivers business value for the long-term. He will give examples of organizations worldwide who have successfully implemented a data governance program by engaging with key stakeholders using innovative techniques such as gamification and data catalog scavenger hunts.
Data Loss Prevention

DATA LOSS PREVENTION ENSURES CRITICAL INFORMATION ARE KEPT SAFELY AT THE CORPORATE NETWORK AND HELPS ADMINISTRATOR CONTROL THE DATA WHAT
END-USERS WISH TO TRANSFER.
You Need a Data Catalog. Do You Know Why?

The data catalog has become a popular discussion topic within data management and data governance circles. A data catalog is a central repository that contains metadata for describing data sets, how they are defined, and where to find them. TDWI research indicates that implementing a data catalog is a top priority among organizations we survey. The data catalog can also play an important part in the governance process. It provides features that help ensure data quality, compliance, and that trusted data is used for analysis. Without an in-depth knowledge of data and associated metadata, organizations cannot truly safeguard and govern their data.
Join this on-demand webinar to learn more about the data catalog and its role in data governance efforts.
Topics include:
· Data management challenges and priorities
· The modern data catalog – what it is and why it is important
· The role of the modern data catalog in your data quality and governance programs
· The kinds of information that should be in your data catalog and why
What's hot (20)
Privacy-ready Data Protection Program Implementation

Privacy-ready Data Protection Program Implementation
How to Strengthen Enterprise Data Governance with Data Quality

How to Strengthen Enterprise Data Governance with Data Quality
Data Governance Program Powerpoint Presentation Slides

Data Governance Program Powerpoint Presentation Slides
Data Architecture Best Practices for Advanced Analytics

Data Architecture Best Practices for Advanced Analytics
Data Governance Takes a Village (So Why is Everyone Hiding?)

Data Governance Takes a Village (So Why is Everyone Hiding?)
Data Protection Indonesia: Basic Regulation and Technical Aspects_Eryk

Data Protection Indonesia: Basic Regulation and Technical Aspects_Eryk
Data Catalog for Better Data Discovery and Governance

Data Catalog for Better Data Discovery and Governance
Data Profiling, Data Catalogs and Metadata Harmonisation

Data Profiling, Data Catalogs and Metadata Harmonisation
Common Practice in Data Privacy Program Management

Common Practice in Data Privacy Program Management
Similar to Data classification-policy
Data Protection: We\'re In This Together

All workers in a business are responsible for the protection of their sensitive data.
DAMA Webinar: The Data Governance of Personal (PII) Data

To do effective data governance, analysts should preview the amount of data their organization is collecting and consider if it is all necessary information to run the business or just “nice to have” data. Today companies are collecting a variety of Personally identifiable information (PII), combining it with location information, and using it to both personalize their own services and to sell to advertisers for behavioral marketing. Data brokers are tracking cell phone applications and insurance companies are installing devices to monitor driving habits. At the same time, however, hackers are embedding malicious software in company computers, opening a virtual door for criminals to rifle through an organization’s valuable personal and financial information.
This presentation explores:
•What company data should be tagged as “sensitive” data?
•Who within the company has access to personal data?
•Is the company breaking any privacy laws by storing PII data?
•Is the data secure from both internal and external hackers?
•What happens if there is an external data breech?
Privacy - Useful resources for department staff

A resource for department staff on understanding privacy obligations.
FTC Safeguard

The goal of VCU is to eliminate unacceptable risks in order to safeguard customer information and protect the confidentiality and privacy rights of its customers.
Safeguarding Personal Health Information: HIPAA Rules on De-Identification

In this session, we will delve into the concepts and methodologies of de-identification of Protected Health Information (PHI) as mandated by HIPAA regulations. Attendees will gain a comprehensive understanding of the typical questions that arise during de-identification processes and will be able to proceed with greater confidence. We will also discuss the various scenarios where de-identified information is required, and how it facilitates better sharing of information while maintaining patient privacy. The guidance provided will offer a sound and defensible basis for organizations to make informed decisions and establish robust processes surrounding the de-identification of PHI. By the end of this session, attendees will have the knowledge and skills necessary to effectively implement de-identification practices in compliance with HIPAA regulations.
Register,
https://conferencepanel.com/conference/hipaa-and-de-identification-of-phi-sometimes-required-never-easy
Protecting PII

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Enabling Data Governance - Data Trust, Data Ethics, Data Quality

Presented on PHPID Online Learning 35.
Komunitas PHP Indonesia
Title: Enabling Data Governance - The Journey through Data Trust, Ethics, and Quality
Eryk B. Pratama
Global IT & Cybersecurity Advisor
GDPR Demystified 

GDPR (General Data Protection Rules) were implemented in May 2018 across Europe, and they have confused ordinary people and business gurus alike,
This simple PowerPoint presentation destroys and dismantles some of the myths of GDPR, making it more accessible & easily understandable.
Produced by Terence O'Sullivan (TheEmploymentLawyer/TJOS.ie) in October 2018
Similar to Data classification-policy (20)
DAMA Webinar: The Data Governance of Personal (PII) Data

DAMA Webinar: The Data Governance of Personal (PII) Data
Privacy and Data Security: Risk Management and Avoidance

Privacy and Data Security: Risk Management and Avoidance
Safeguarding Personal Health Information: HIPAA Rules on De-Identification

Safeguarding Personal Health Information: HIPAA Rules on De-Identification
Privacy_Engineering_Privacy Assurance_Lecture-Ecole_Polytechnic_Nice_SA-20150127

Privacy_Engineering_Privacy Assurance_Lecture-Ecole_Polytechnic_Nice_SA-20150127
Enabling Data Governance - Data Trust, Data Ethics, Data Quality

Enabling Data Governance - Data Trust, Data Ethics, Data Quality
Recently uploaded
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Recently uploaded (20)
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Data classification-policy
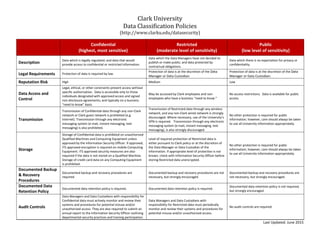
- 1. Clark University Data Classification Policies (http://www.clarku.edu/datasecurity) Confidential (highest, most sensitive) Restricted (moderate level of sensitivity) Public (low level of sensitivity) Description Data which is legally regulated; and data that would provide access to confidential or restricted information. Data which the Data Managers have not decided to publish or make public; and data protected by contractual obligations. Data which there is no expectation for privacy or confidentiality. Legal Requirements Protection of data is required by law. Protection of data is at the discretion of the Data Manager or Data Custodian. Protection of data is at the discretion of the Data Manager or Data Custodian. Reputation Risk High Medium Low Data Access and Control Legal, ethical, or other constraints prevent access without specific authorization. Data is accessible only to those individuals designated with approved access and signed non-disclosure agreements; and typically on a business “need to know” basis. May be accessed by Clark employees and non- employees who have a business “need to know.” No access restrictions. Data is available for public access. Transmission Transmission of Confidential data through any non-Clark network or Clark guest network is prohibited (e.g. Internet). Transmission through any electronic messaging system (e-mail, instant messaging, text messaging) is also prohibited. Transmission of Restricted data through any wireless network, and any non-Clark wired network is strongly discouraged. Where necessary, use of the University’s VPN is required. Transmission through any electronic messaging system (e-mail, instant messaging, text messaging), is also strongly discouraged. No other protection is required for public information; however, care should always be taken to use all University information appropriately. Storage Storage of Confidential data is prohibited on unauthorized Qualified Machines and Computing Equipment unless approved by the Information Security Officer. If approved, ITS approved encryption is required on mobile Computing Equipment. ITS approved security measures are also required if the data is not stored on a Qualified Machine. Storage of credit card data on any Computing Equipment is prohibited. Level of required protection of Restricted data is either pursuant to Clark policy or at the discretion of the Data Manager or Data Custodian of the information. If appropriate level of protection is not known, check with Information Security Officer before storing Restricted data unencrypted. No other protection is required for public information; however, care should always be taken to use all University information appropriately. Documented Backup & Recovery Procedures Documented backup and recovery procedures are required. Documented backup and recovery procedures are not necessary, but strongly encouraged. Documented backup and recovery procedures are not necessary, but strongly encouraged. Documented Data Retention Policy Documented data retention policy is required. Documented data retention policy is required. Documented data retention policy is not required, but strongly encouraged. Audit Controls Data Managers and Data Custodians with responsibility for Confidential data must actively monitor and review their systems and procedures for potential misuse and/or unauthorized access. They are also required to submit an annual report to the Information Security Officer outlining departmental security practices and training participation. Data Managers and Data Custodians with responsibility for Restricted data must periodically monitor and review their systems and procedures for potential misuse and/or unauthorized access. No audit controls are required. Last Updated: June 2015
- 2. Confidential (highest, most sensitive) Restricted (moderate level of sensitivity) Public (low level of sensitivity) Data Examples (not all-inclusive) * exceptions apply Information resources with access to confidential or restricted data (username and password). Personally Identifiable Information (PII): Last name, first name or initial with any one of following: - Social Security Number (SSN) - Driver’s license - State ID card - Passport number - Financial account (checking, savings, brokerage, CD, etc .), credit card, or debit card numbers Protected Health Information (PHI) * - Health status - Healthcare treatment - Healthcare payment Personal/Employee Data - Worker's compensation or disability claims Student Data not included in directory information. This includes:** - Loan or scholarship information - Payment history - Student tuition bills - Student financial services information - Class lists or enrollment information - Transcripts; grade reports - Notes on class work - Disciplinary action - Athletics or department recruiting information Business/Financial Data - Credit card numbers with/without expiration dates * Exceptions apply ** Recent case law related to FERPA suggests that email containing information about a student’s academic performance is not considered part of a student’s “education record” unless the email is centrally maintained by the University (e.g., printed off and placed in the student’s file). Clark suggests that faculty and staff be very mindful and attentive to the seriousness of the information being communicated about students as email is not a secure means of transmission. When electronic communication about a student is deemed necessary, faculty and staff should make use of Clark’s email system and not other third party email systems (e.g. Gmail). Personal/Employee Data - Clark ID number - Income information and payroll information * - Personnel records, performance reviews, benefit information - Race, ethnicity, nationality, gender - Date and place of birth - Directory/contact information designated by the owner as private Business/Financial Data - Financial transactions which do not include confidential data - Information covered by non-disclosure agreements - Contracts that don’t contain PII - Credit reports - Records on spending, borrowing, net worth Academic / Research Information - Library transactions (e.g., circulation, acquisitions) - Unpublished research or research detail / results that are not confidential data - Private funding information - Human subject information - Course evaluations Anonymous Donor Information Last name, first name or initial (and/or name of organization if applicable) with any type of gift information (e.g., amount and purpose of commitment). Other Donor Information Last name, first name or initial (and/or name of organization if applicable) with any of the following: - Telephone/fax numbers, e-mail & employment information - Family information (spouse(s), partner, guardian, children, grandchildren, etc.) - Medical information Management Data - Detailed annual budget information - Conflict of Interest Disclosures - University's investment information Systems/Log Data - Server event logs Certain directory/contact information not designated by the owner as private. - Name - Addresses (campus and home) - Email address - Listed telephone number(s) - Degrees, honors and awards - Most recent previous educational institution attended - Major field of study - Dates of current employment, position(s) - ID card photographs for University use Specific for students: - Class year - Participation in campus activities and sports - Weight and height (athletics) - Dates of attendance - Status Business Data - Campus maps - Job postings - List of publications (published research)
