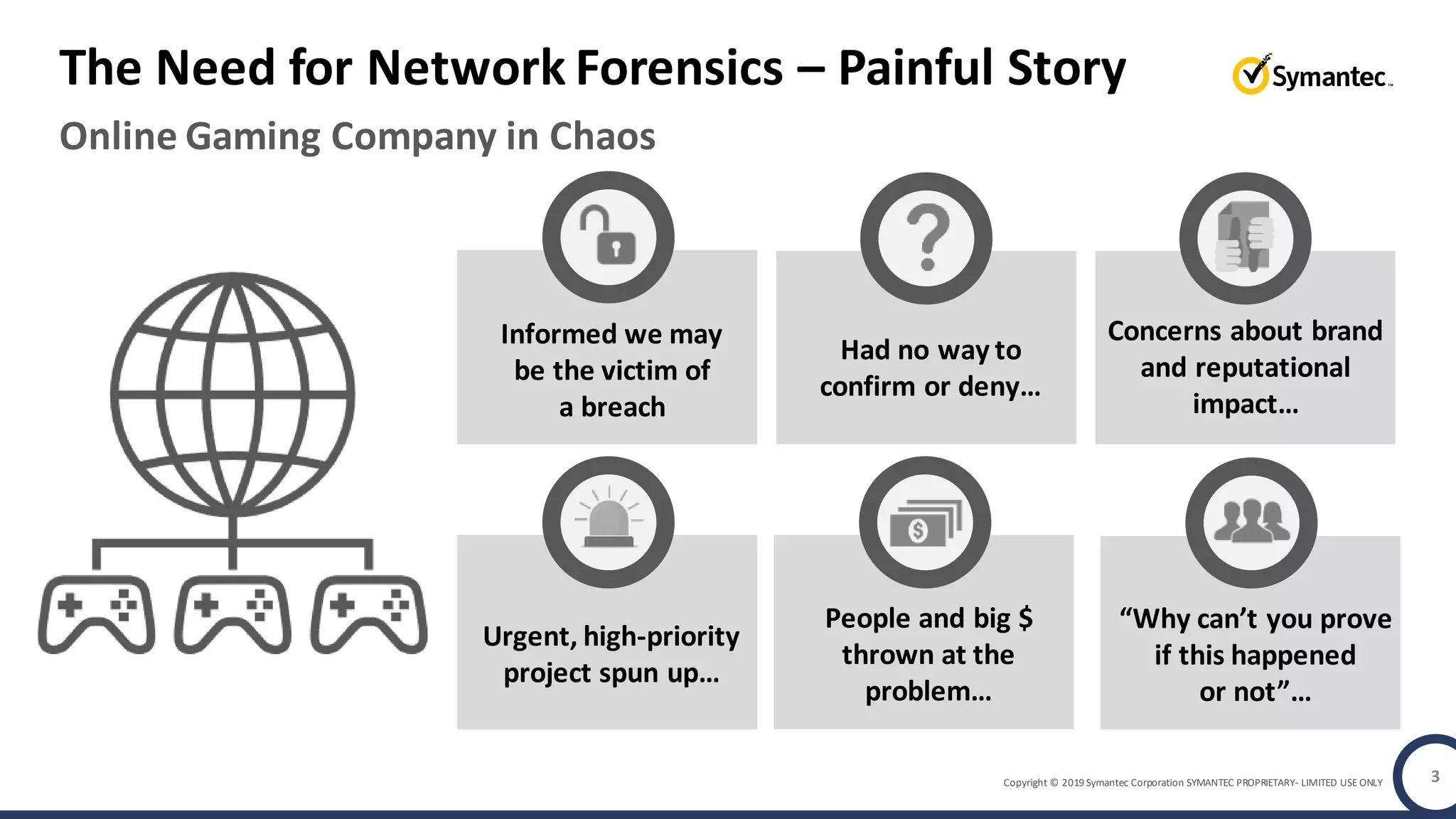
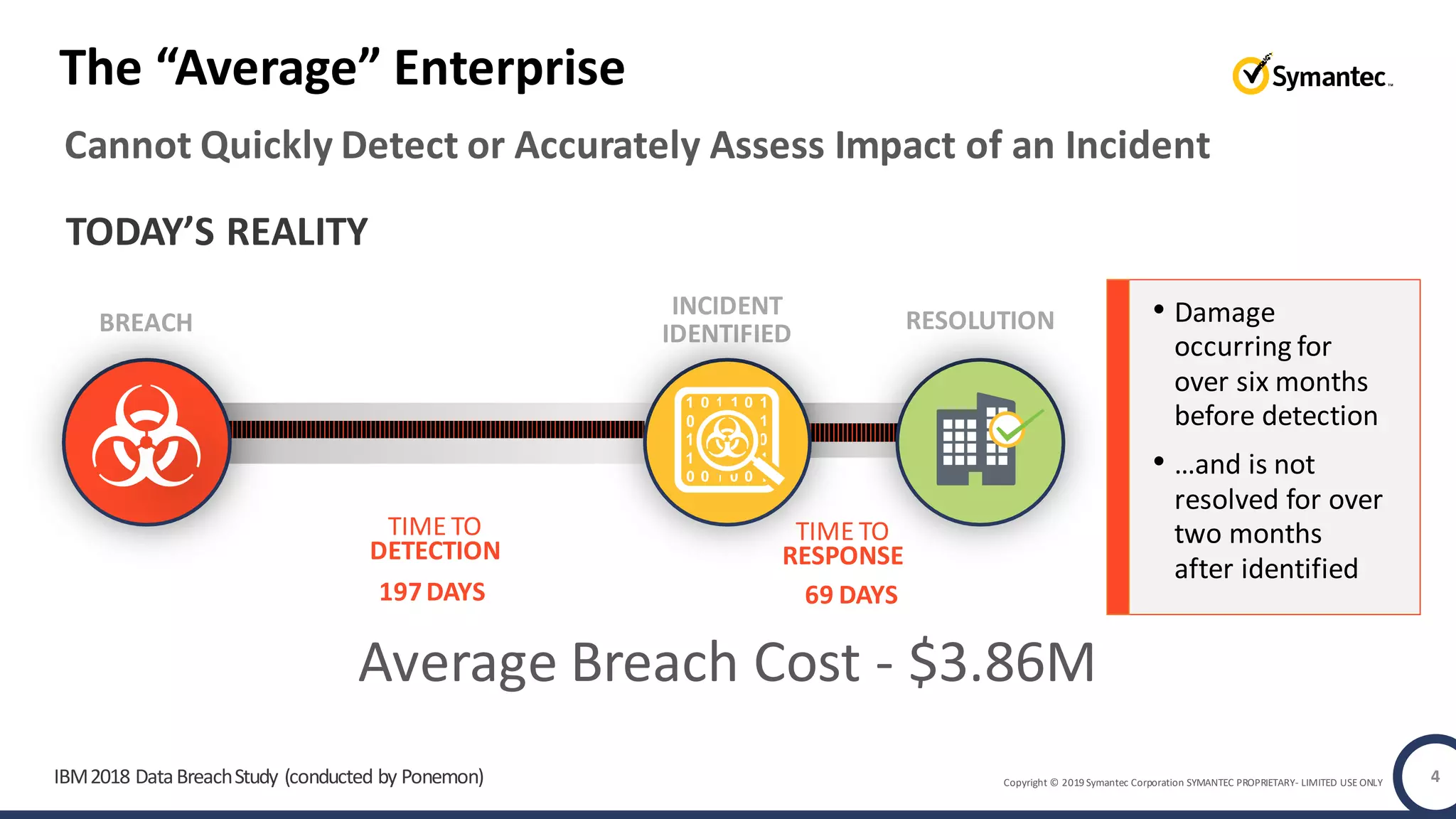
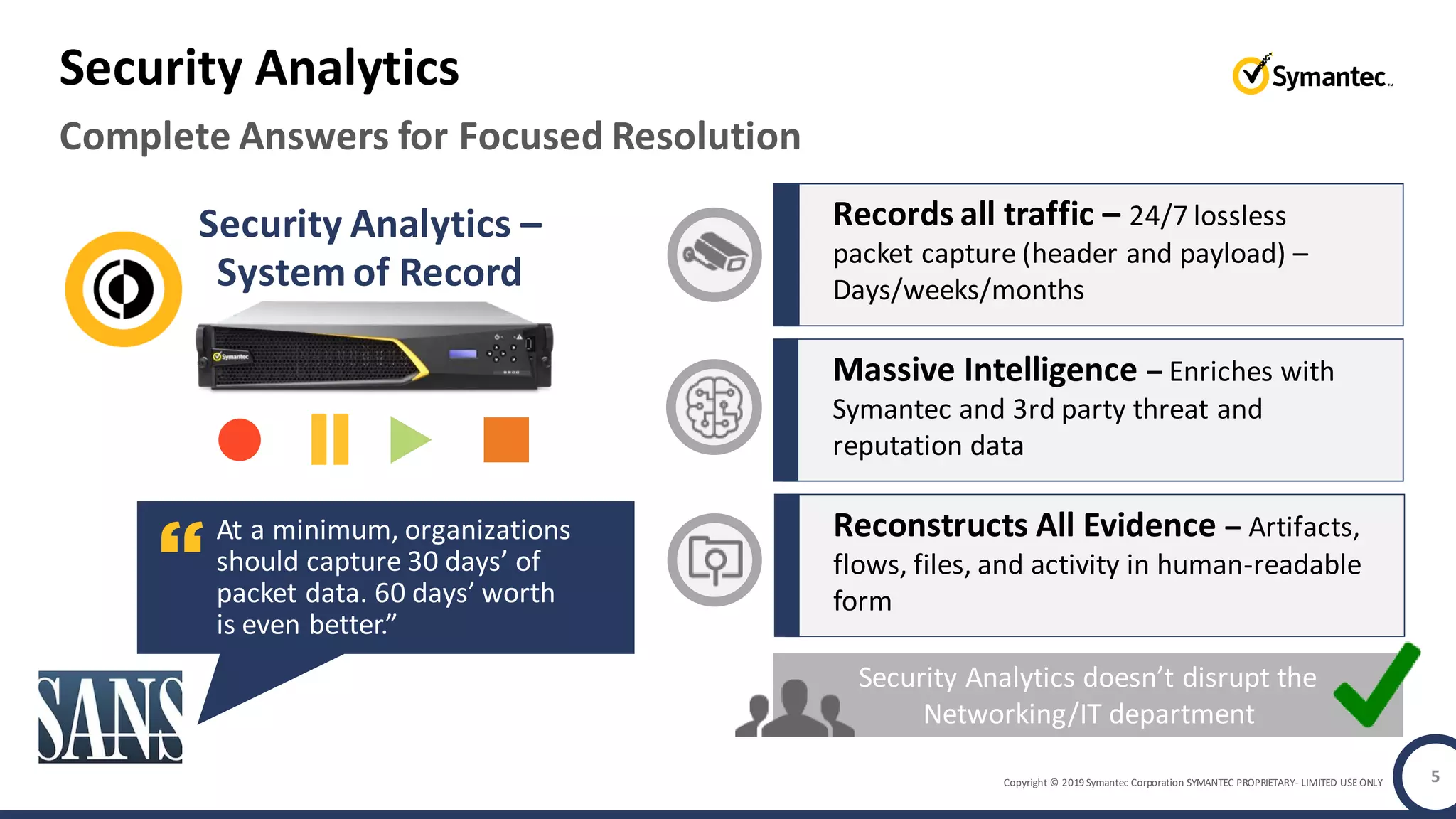
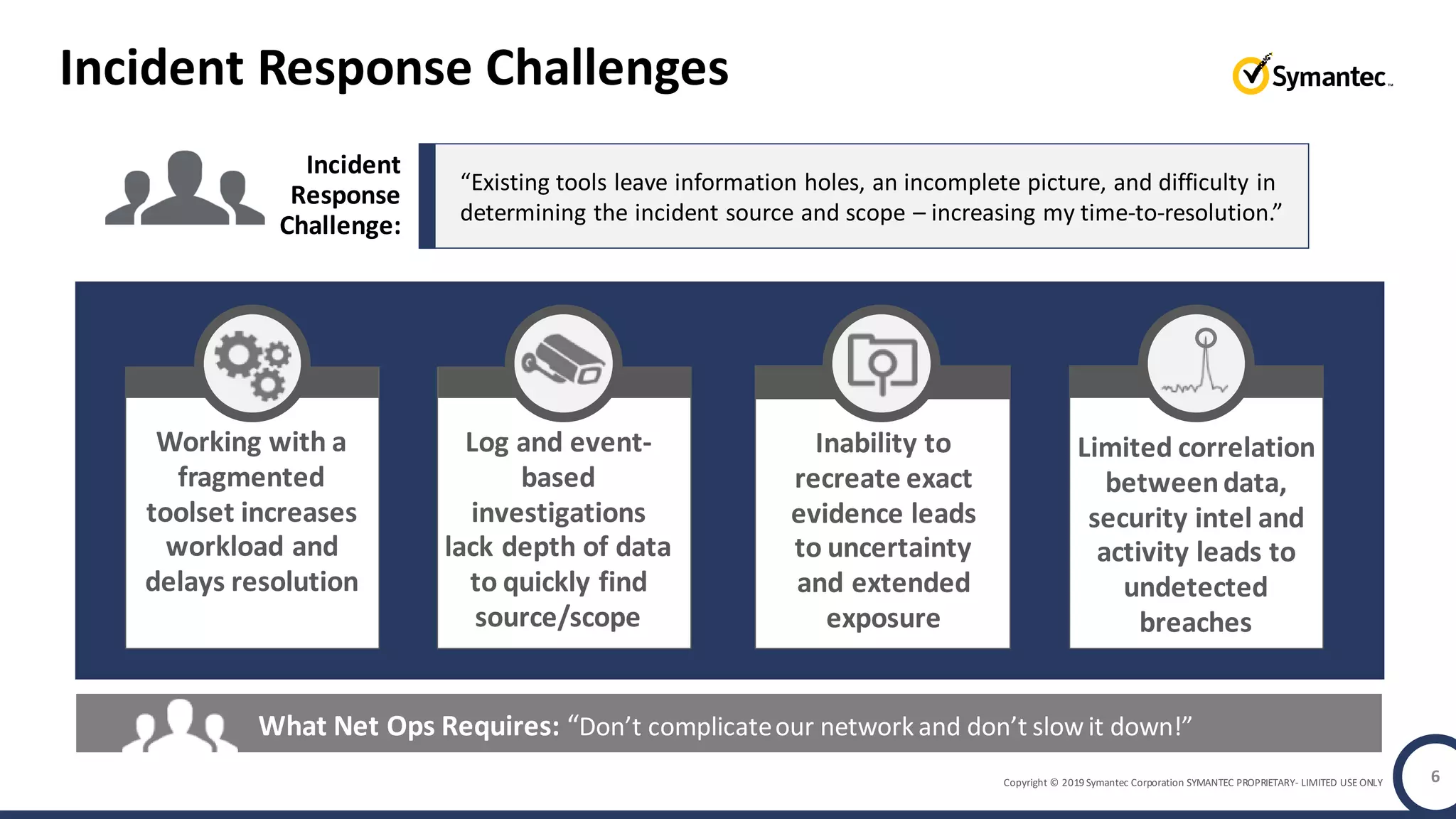
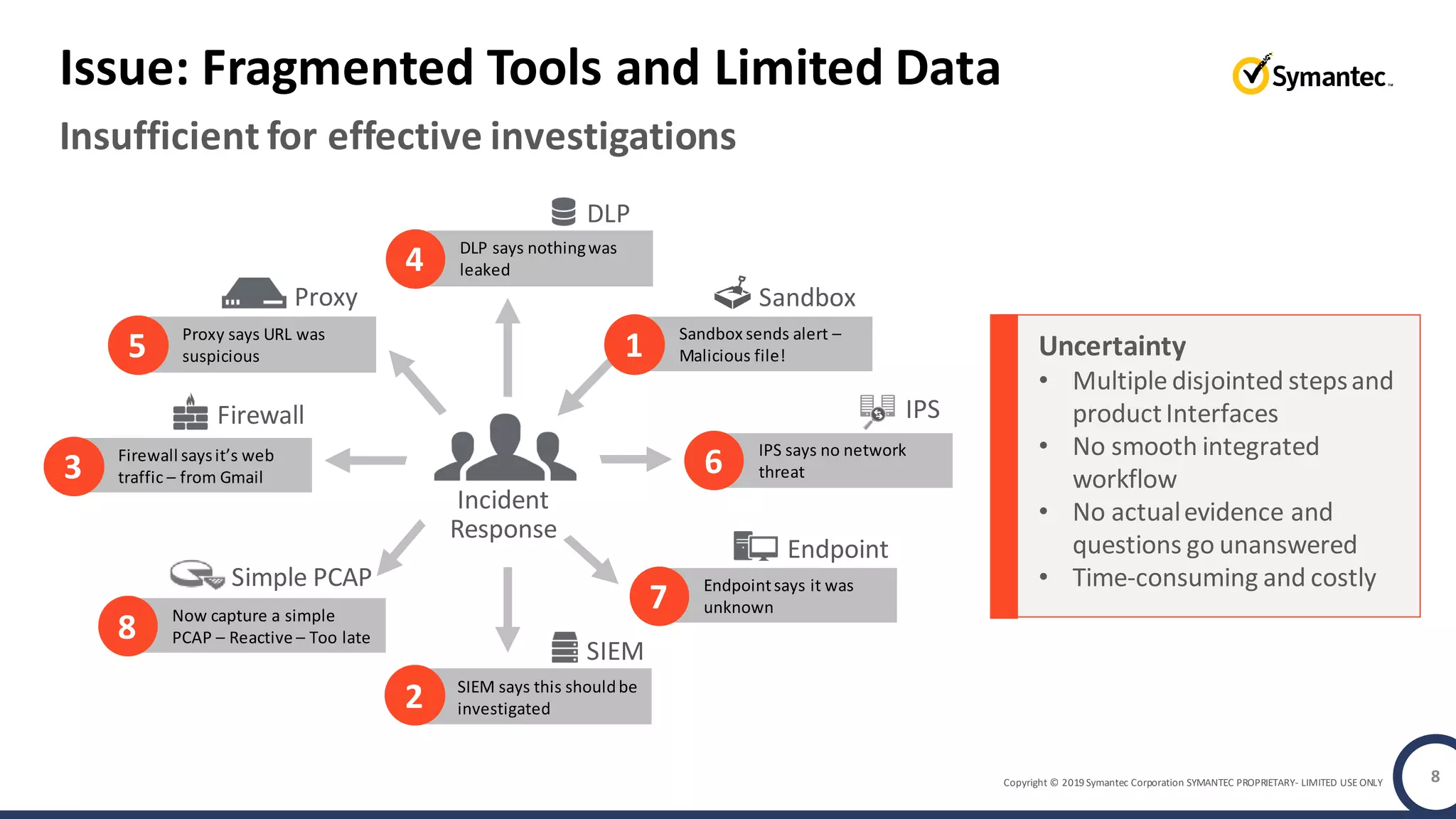
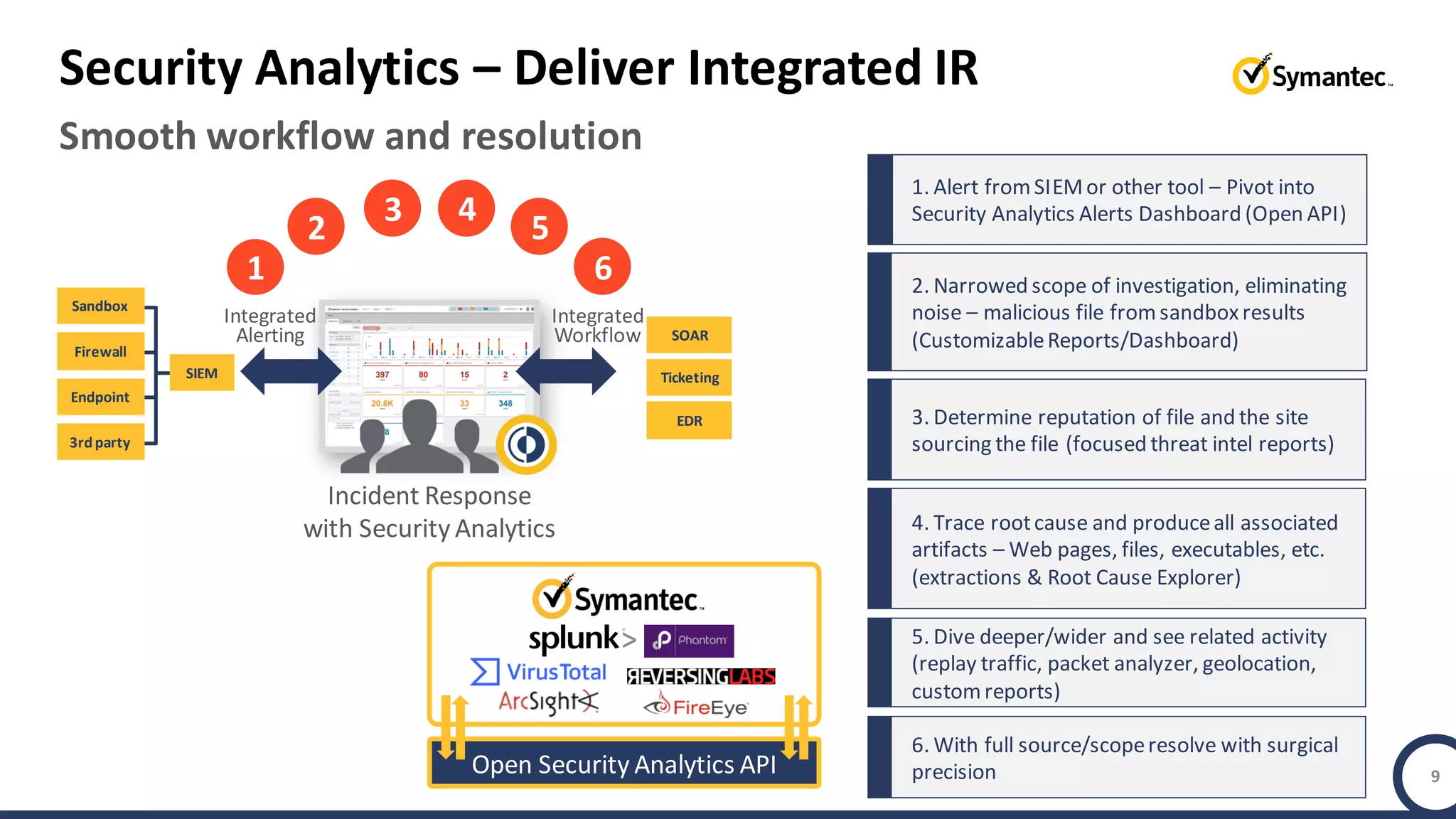
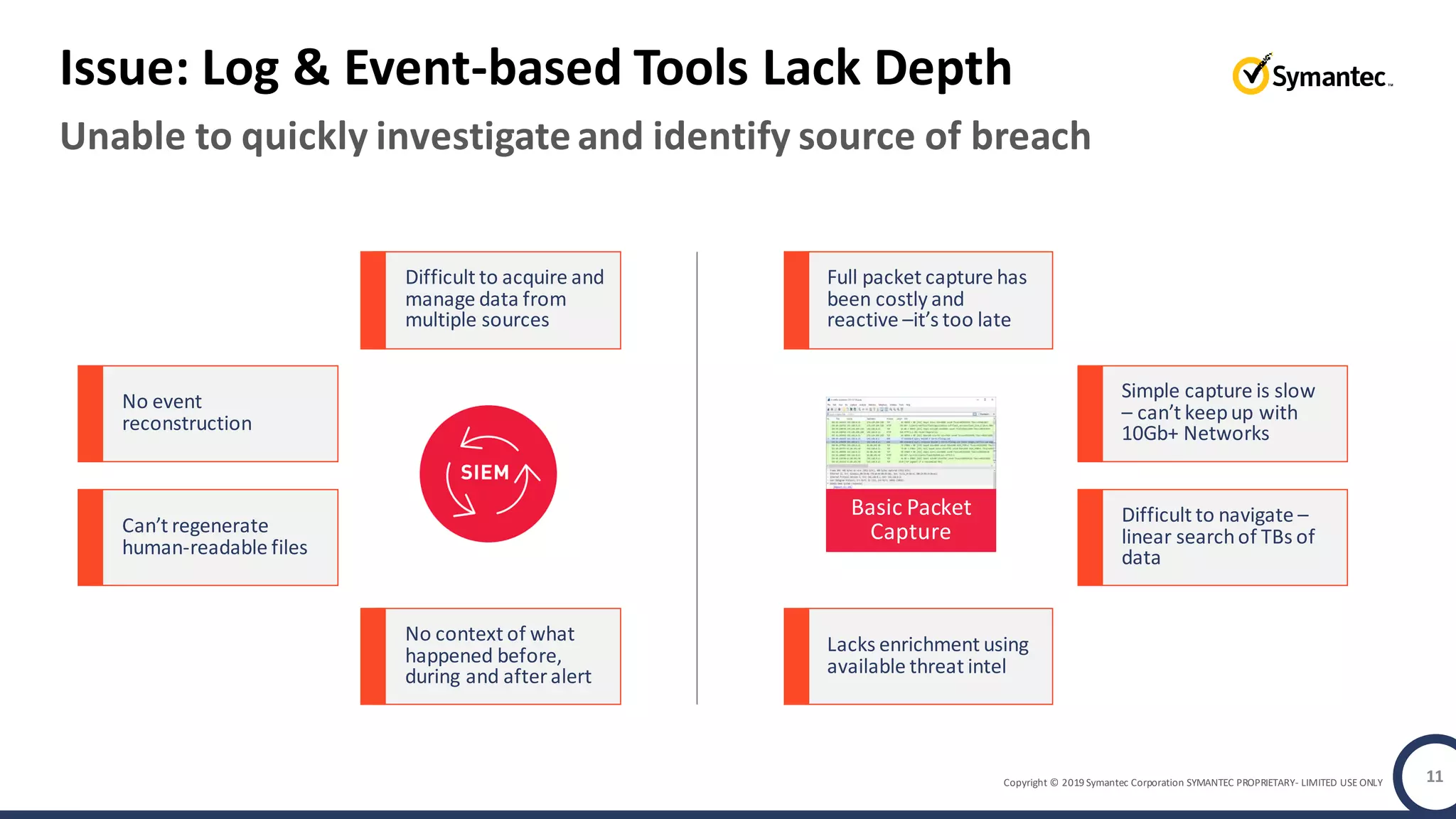
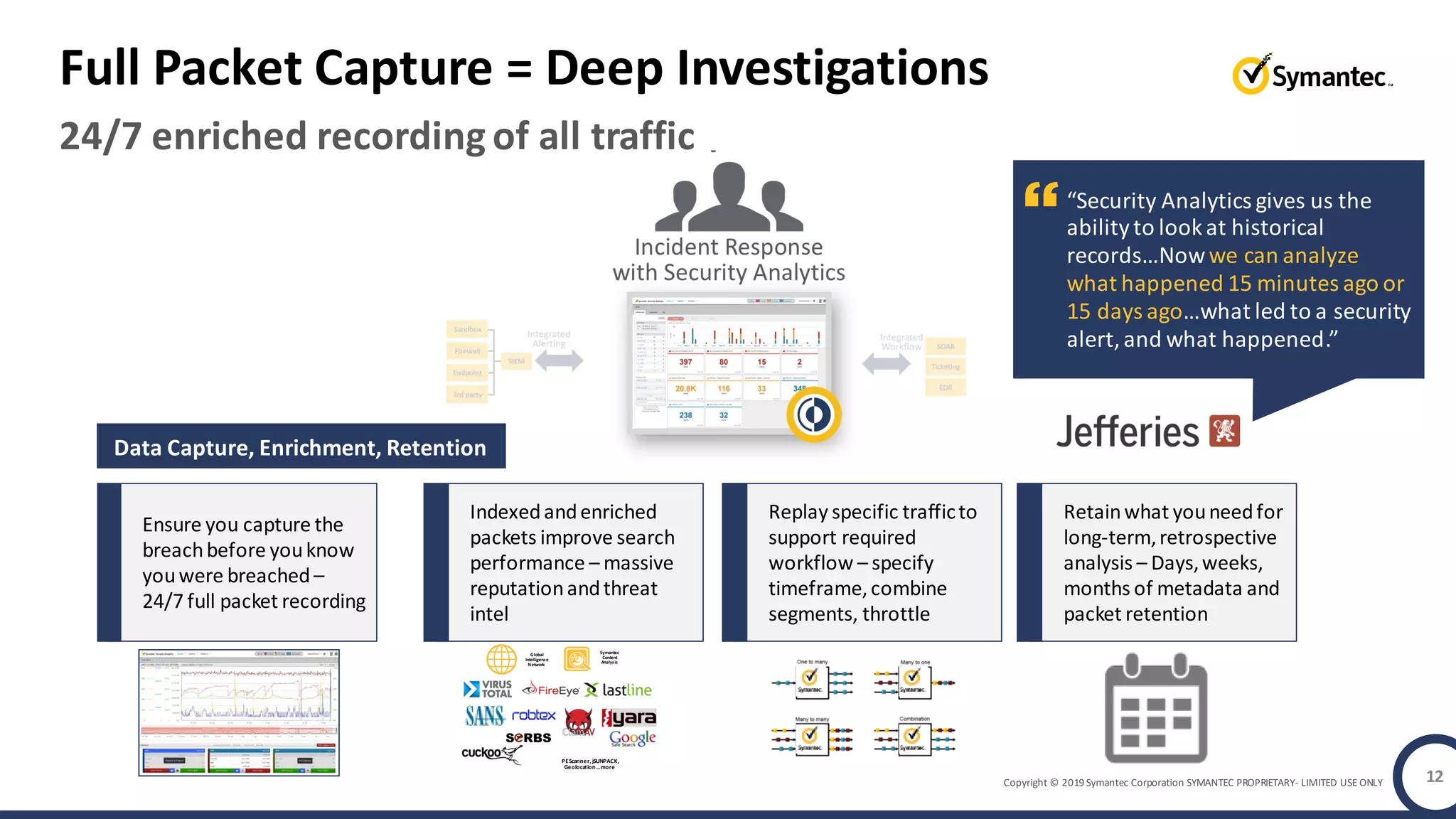
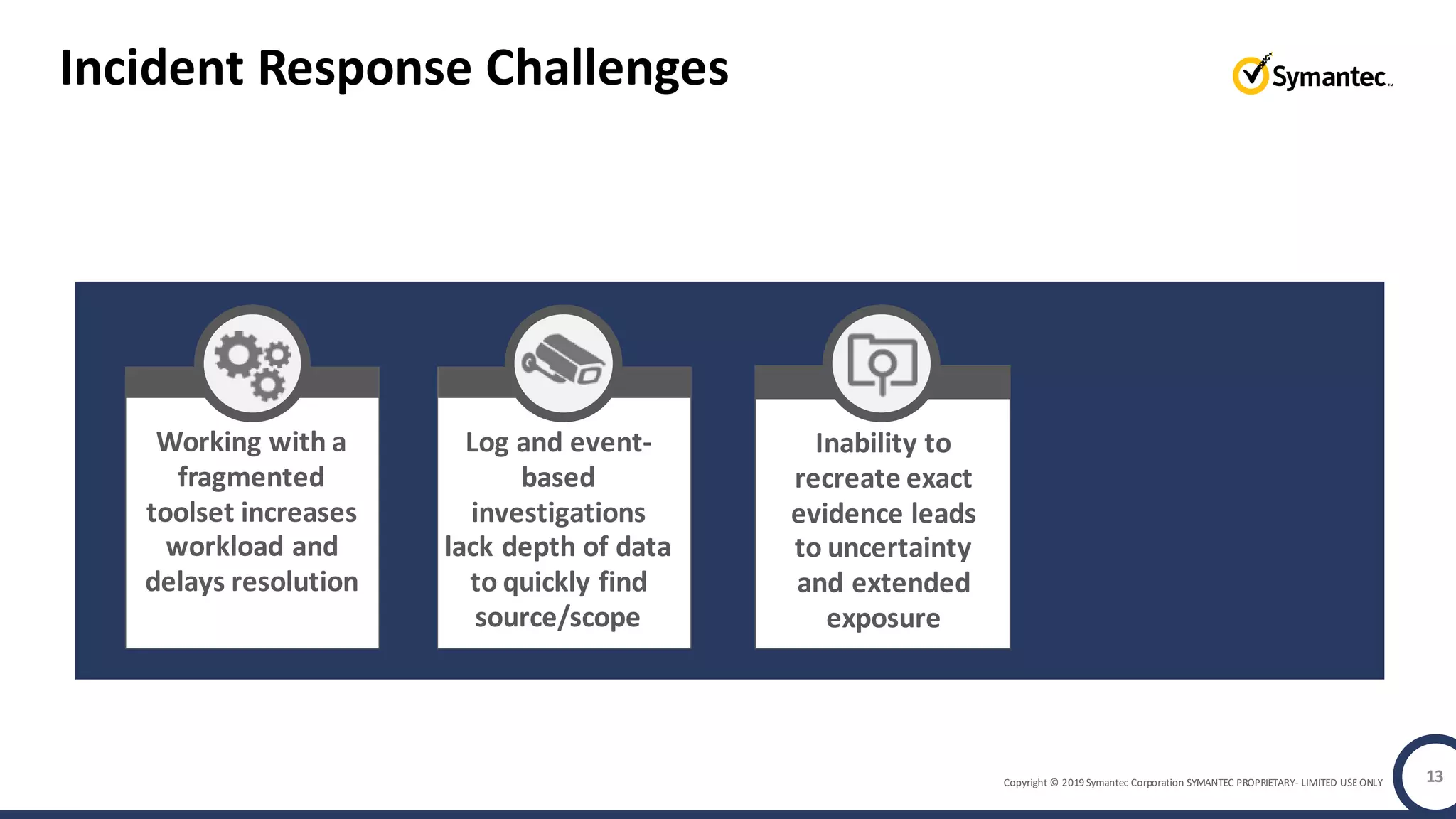
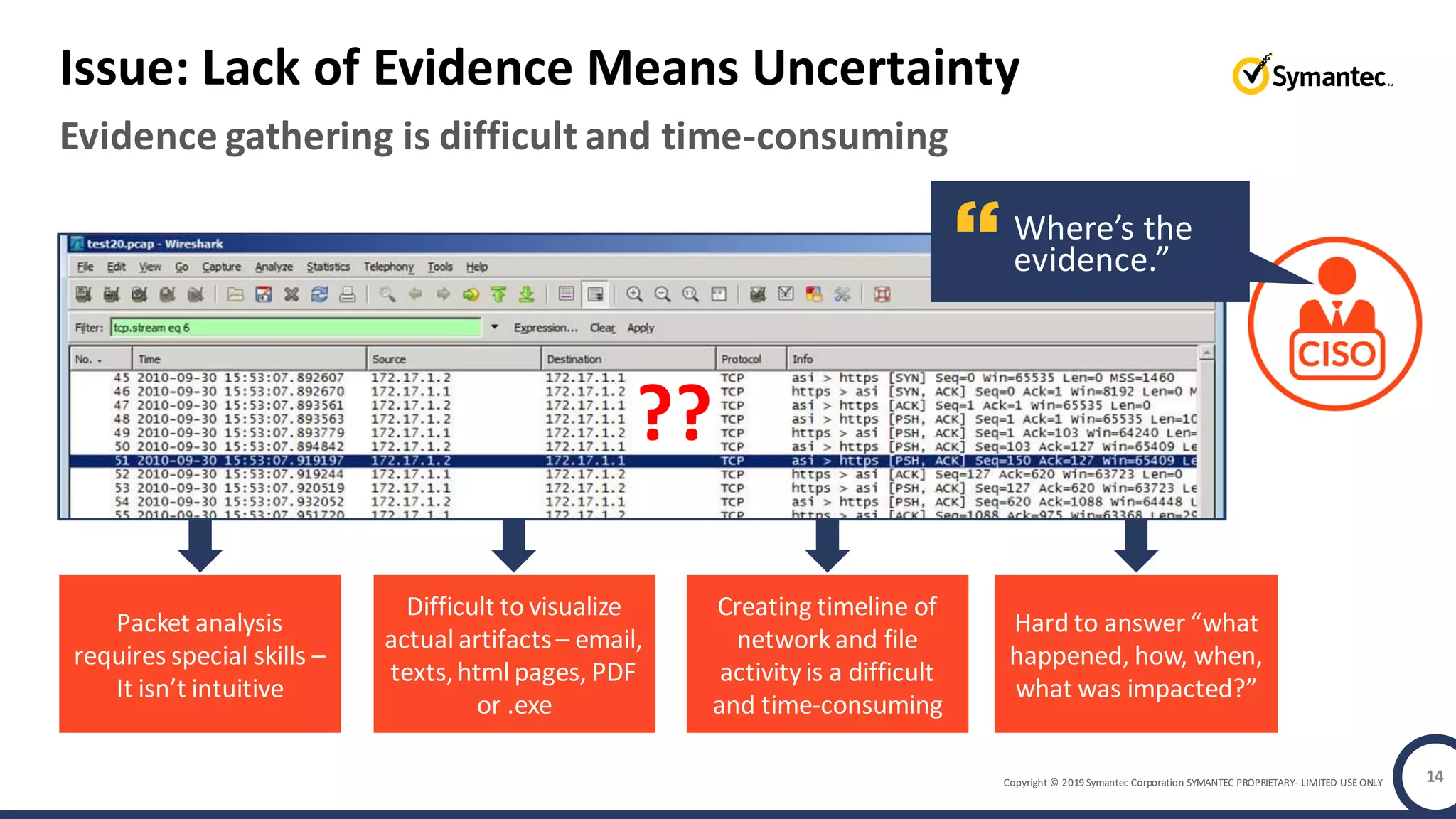
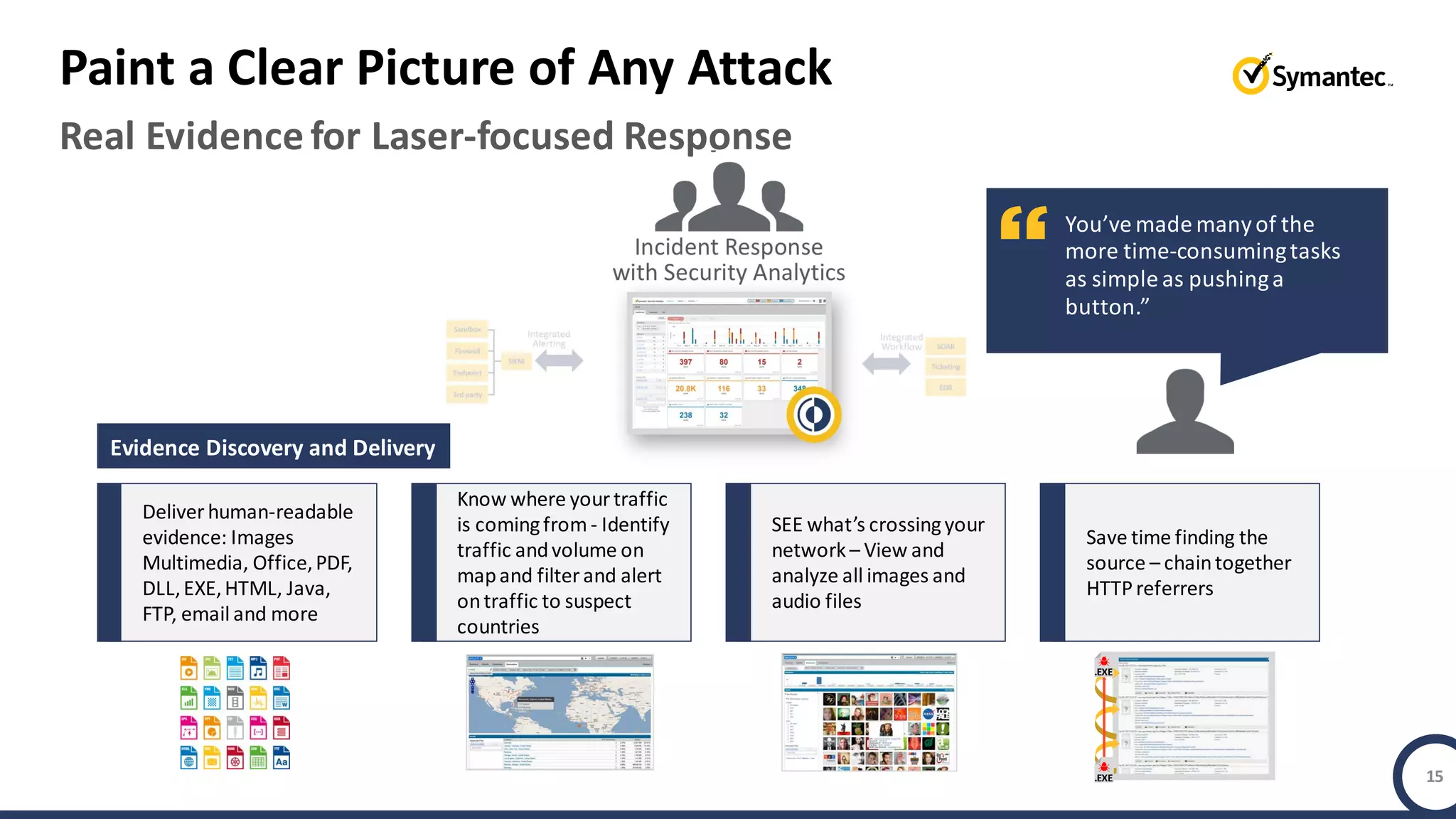
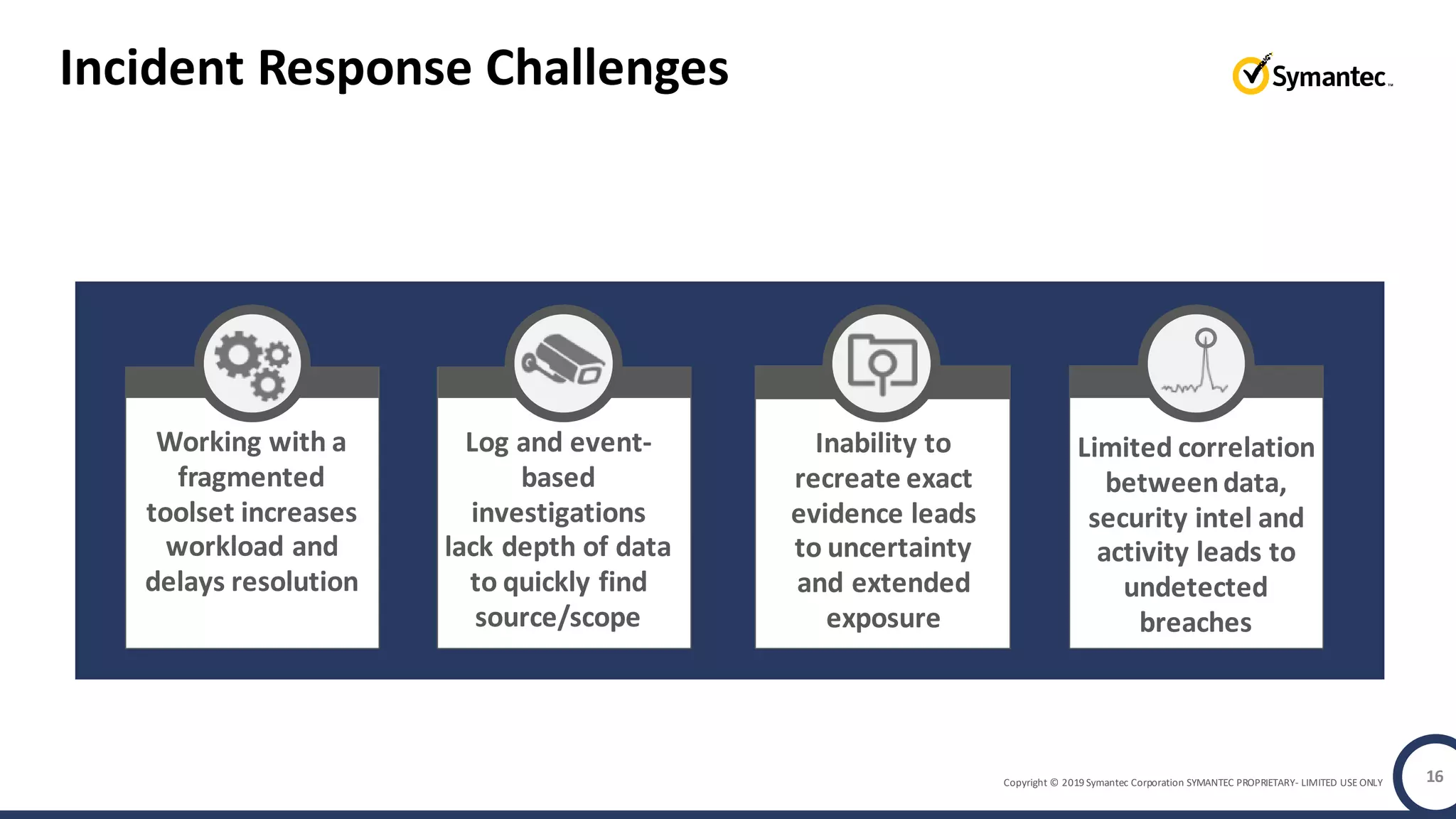
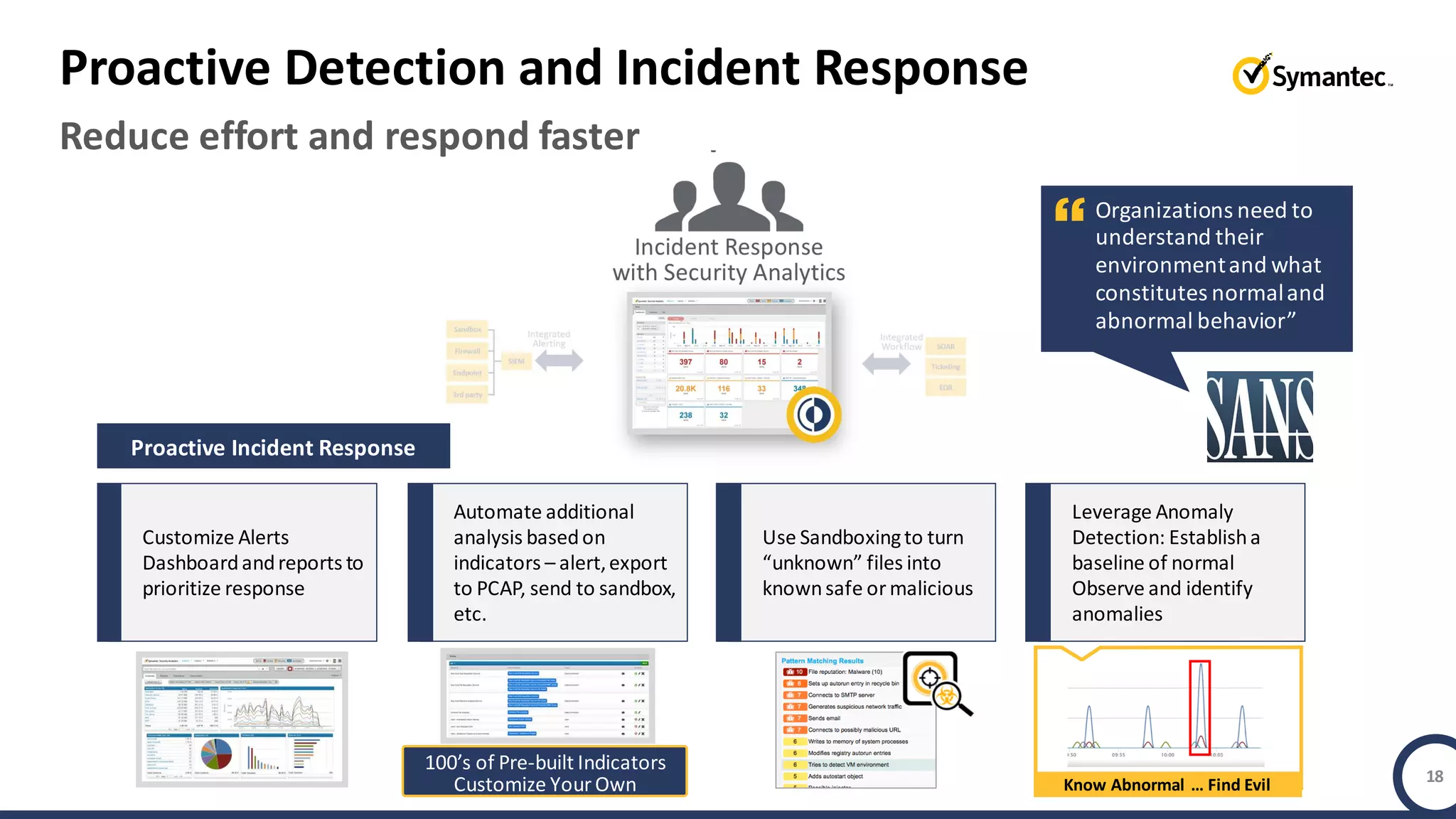
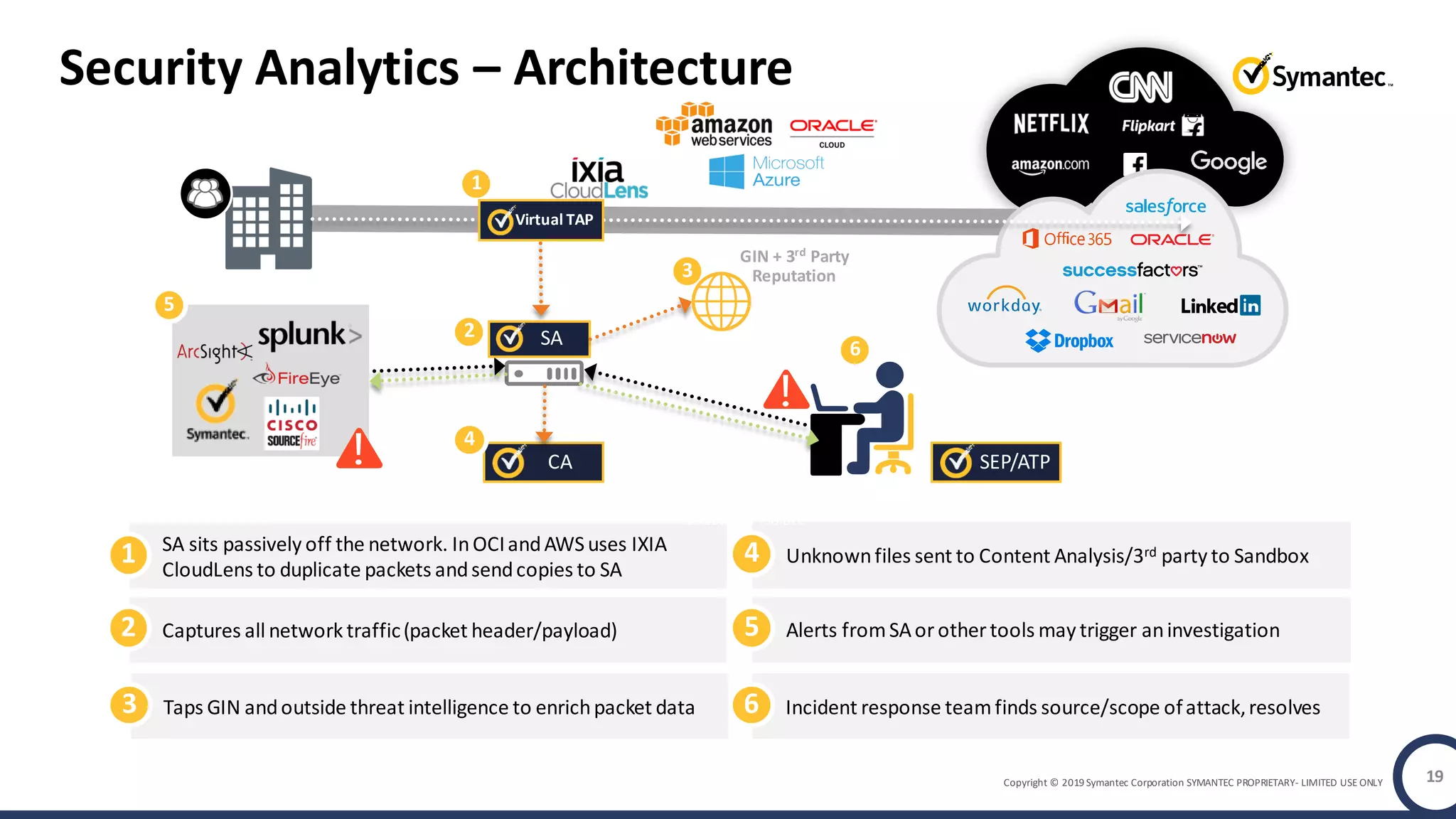
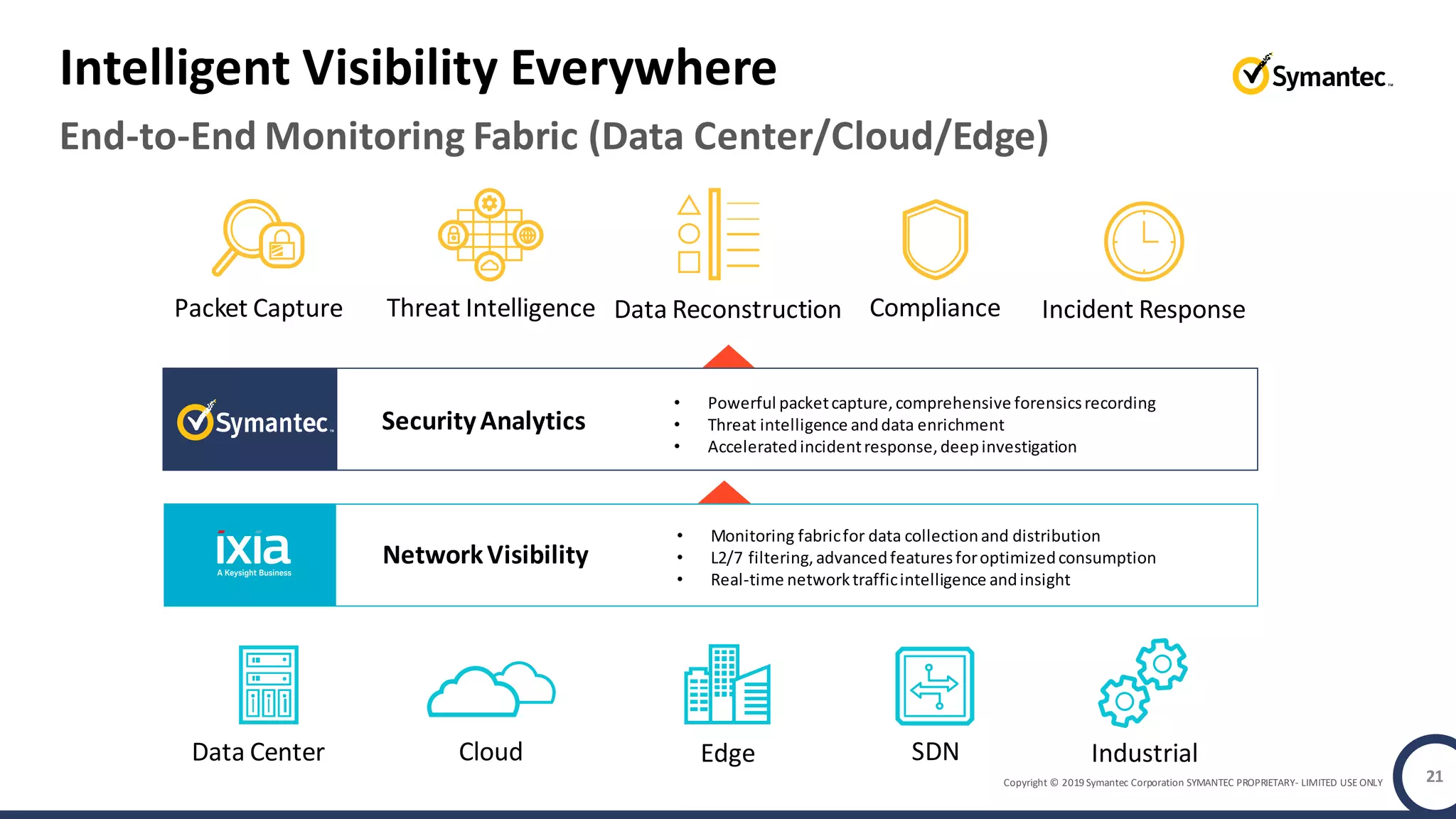
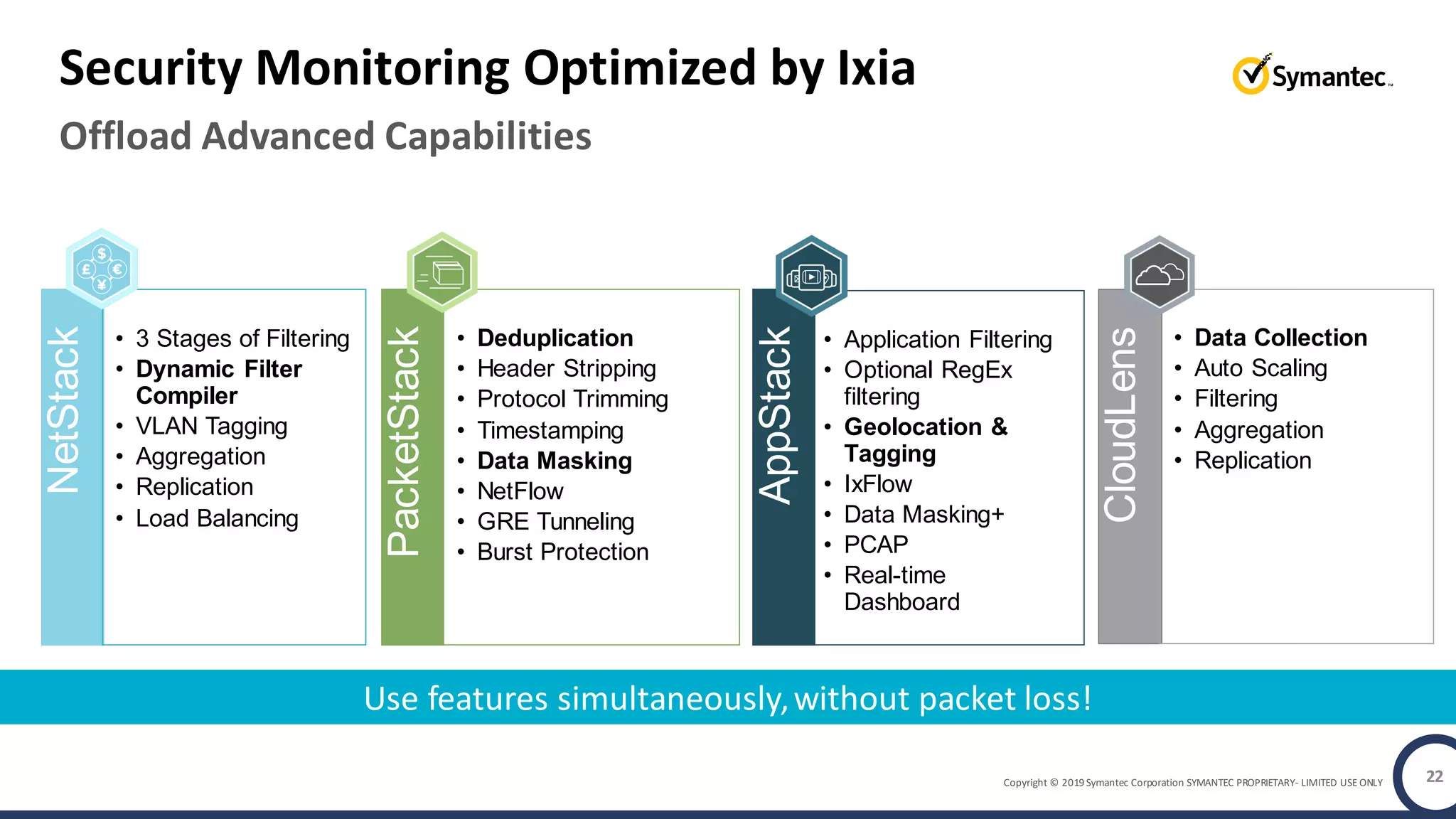
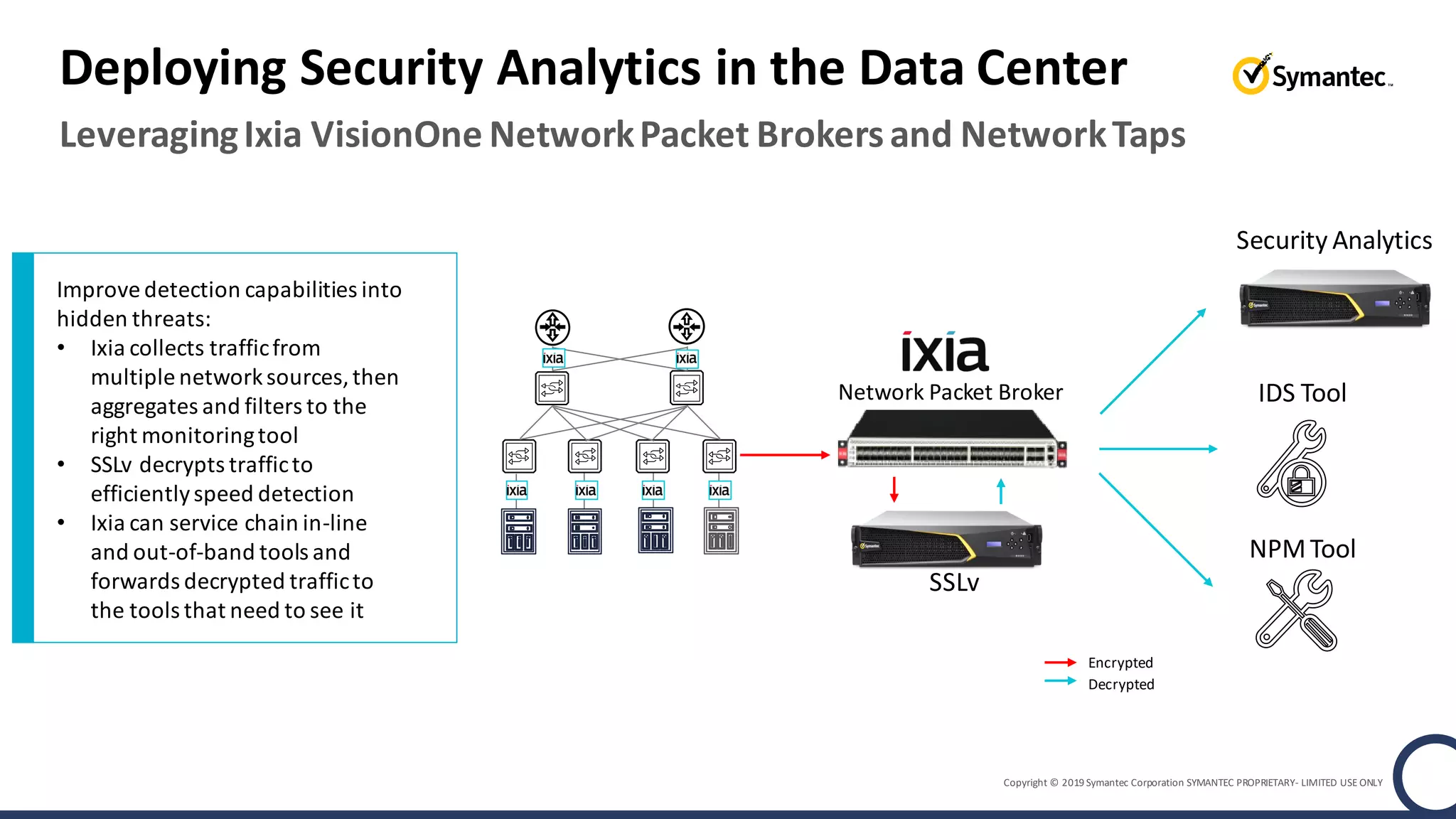
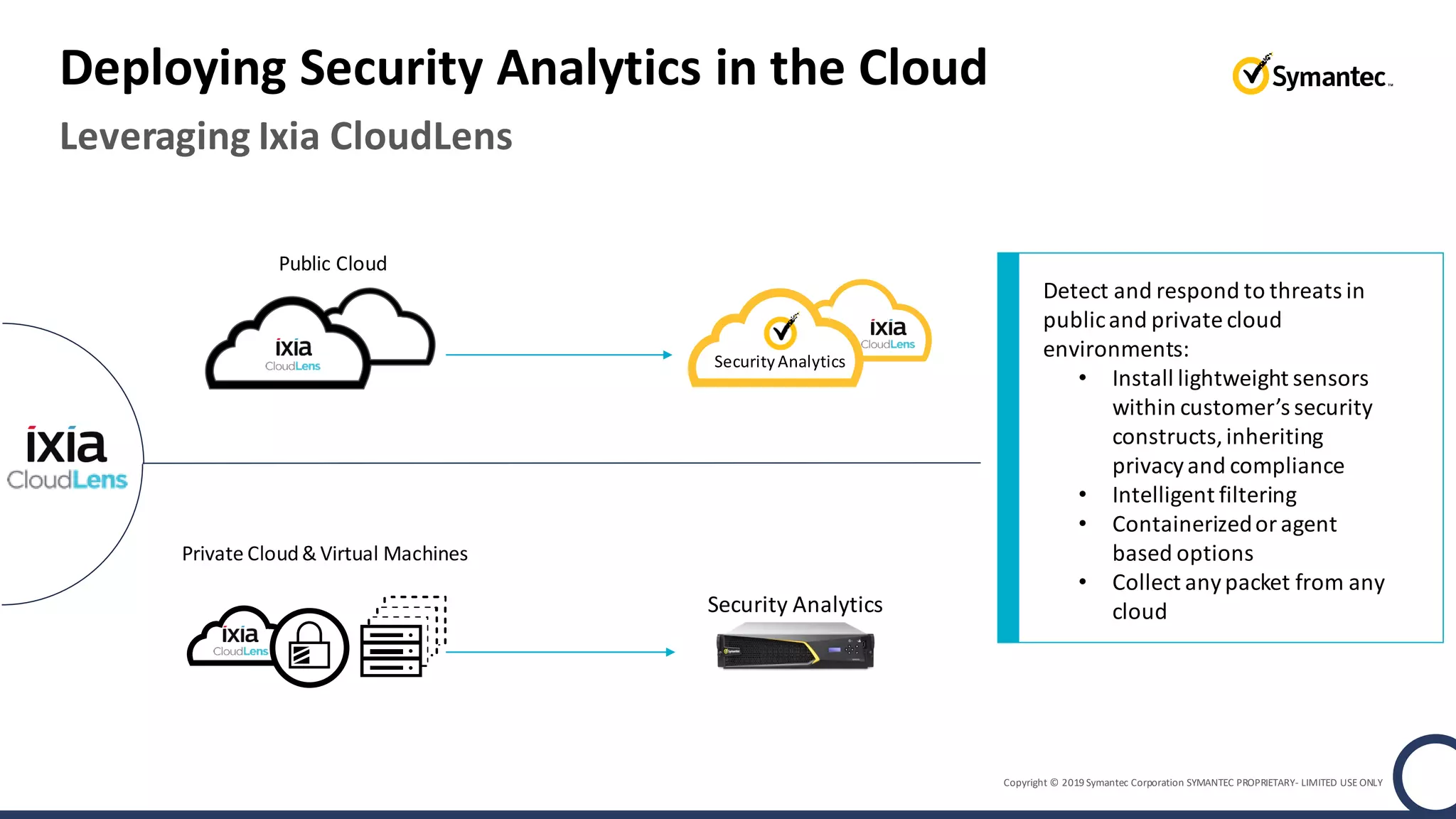
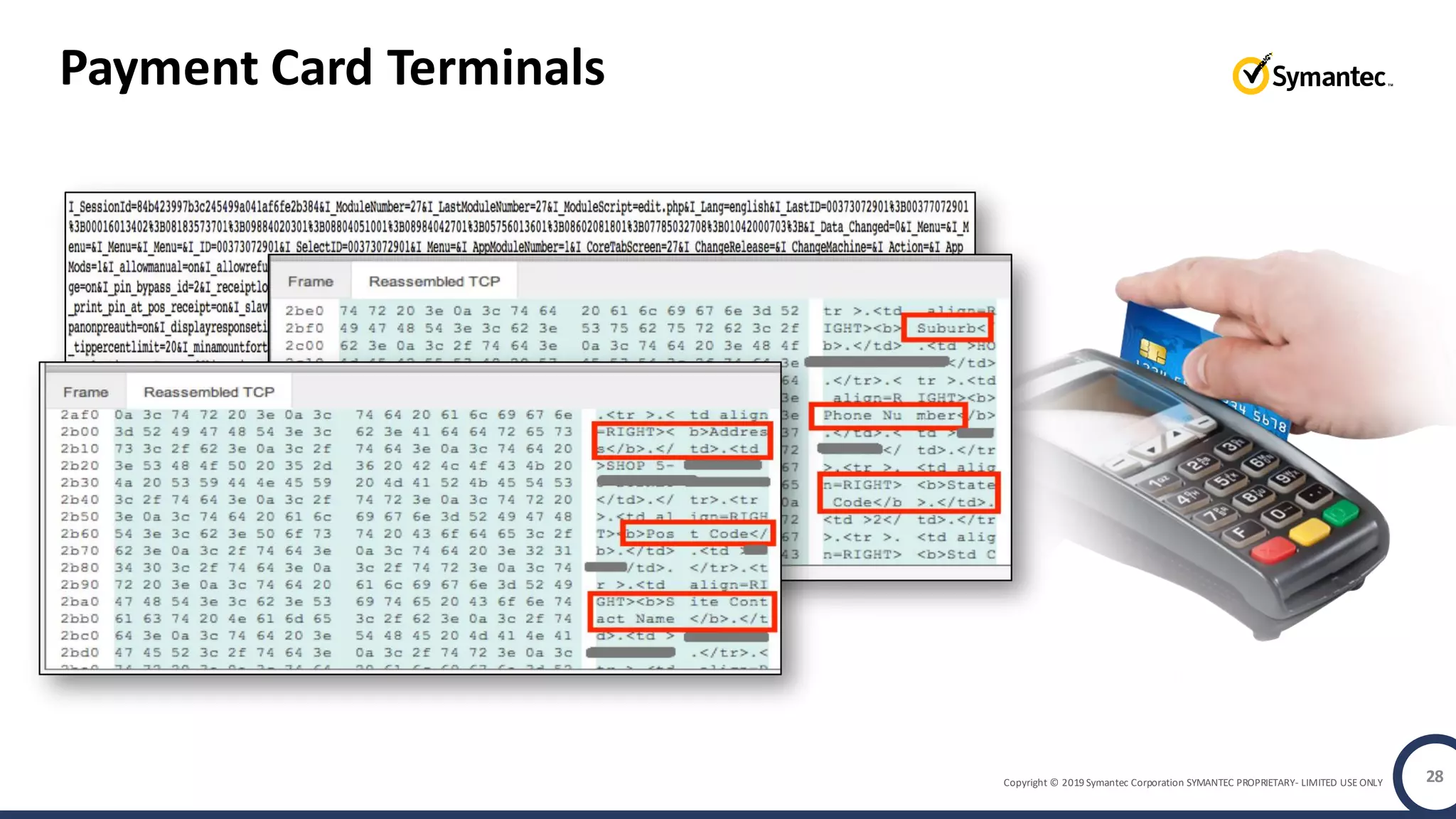
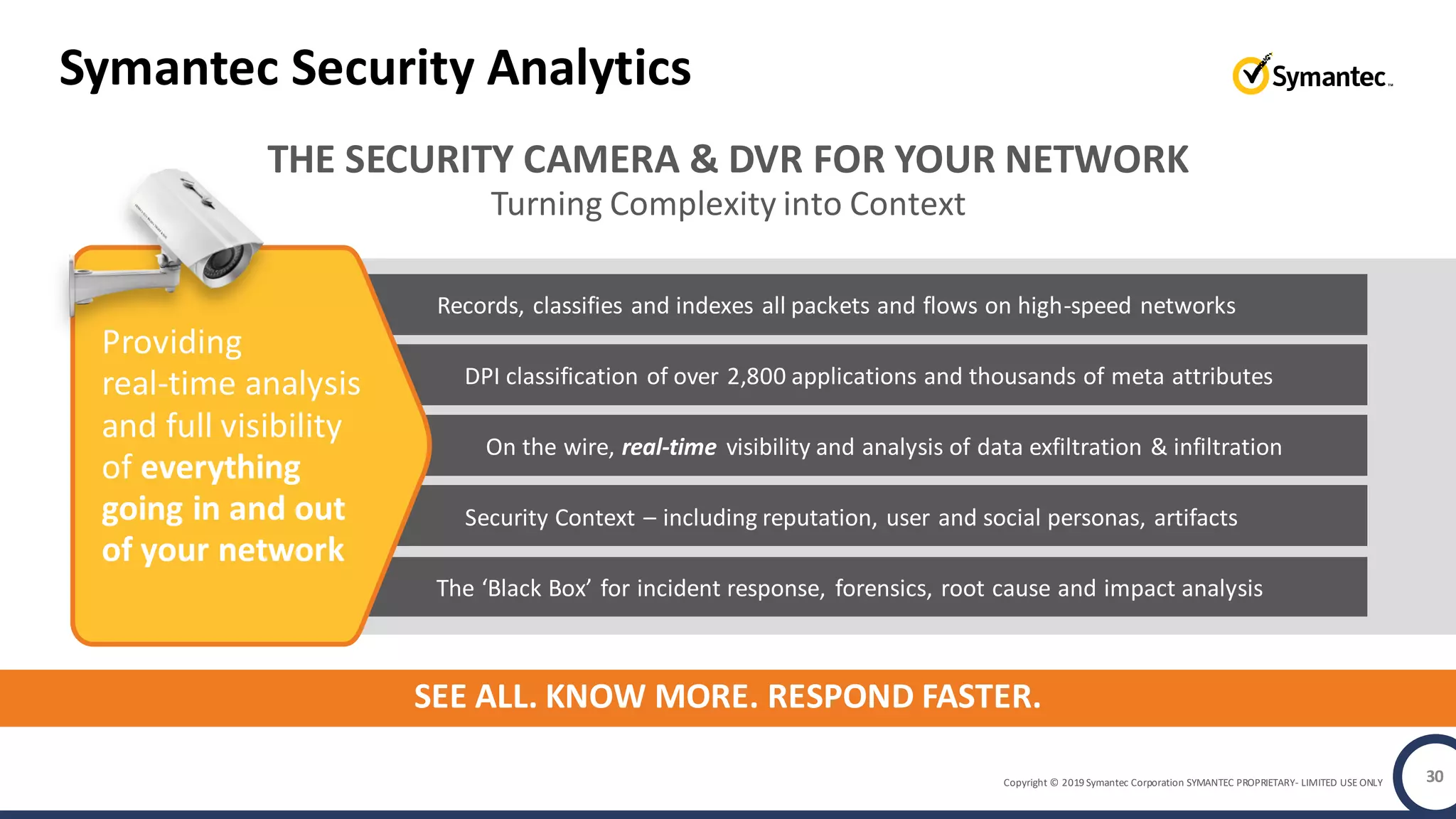
An online gaming company experienced a potential network breach but lacked the tools to investigate what happened. Network forensics tools are needed to quickly detect breaches, determine scope and source, and speed response times. Security analytics provides integrated network monitoring, packet capture, and threat intelligence to give full visibility into network activity and reconstruct evidence for focused incident response. It reduces uncertainty and delays compared to using fragmented, log-based tools lacking rich network data and context.