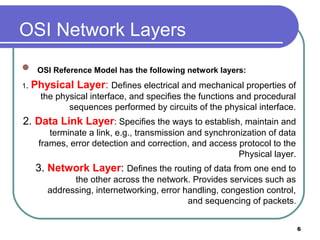
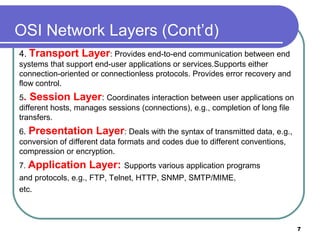
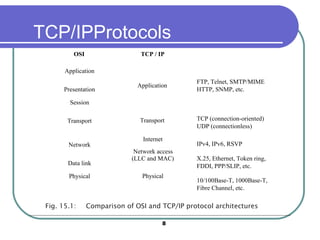
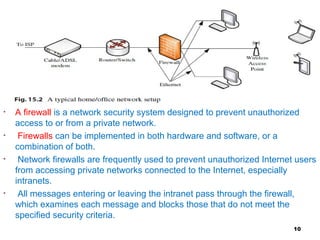
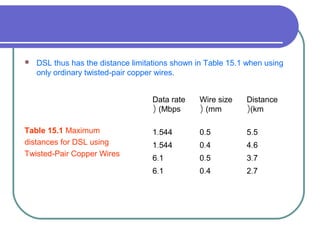
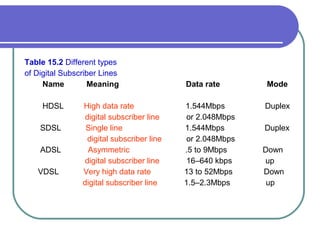
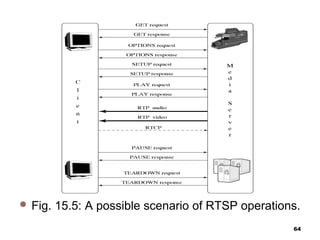
The document discusses various network services and protocols for multimedia communications. It covers protocol layers, local area networks and access network technologies, Internet technologies and protocols, quality of service for multimedia, and protocols for multimedia transmission and interaction. Specifically, it describes the OSI reference model layers, common LAN standards and technologies like Ethernet, Token Ring, FDDI, and digital subscriber line access networks. It also discusses the TCP/IP protocol suite and key protocols like IP, TCP, and UDP.