Embed presentation







This document provides an overview of intrusion detection systems (IDS), including their challenges, potential solutions, and future developments. It discusses how IDS aim to detect attacks against computer systems and networks. The challenges of high false alarm rates and dependency on the environment are outlined. Potential solutions explored include data mining, machine learning, and co-simulation mechanisms. Alarm correlation techniques are examined as ways to combine fragmented alert information to better interpret attack flows. Artificial intelligence is seen as important for improving IDS flexibility, adaptability, and pattern recognition.
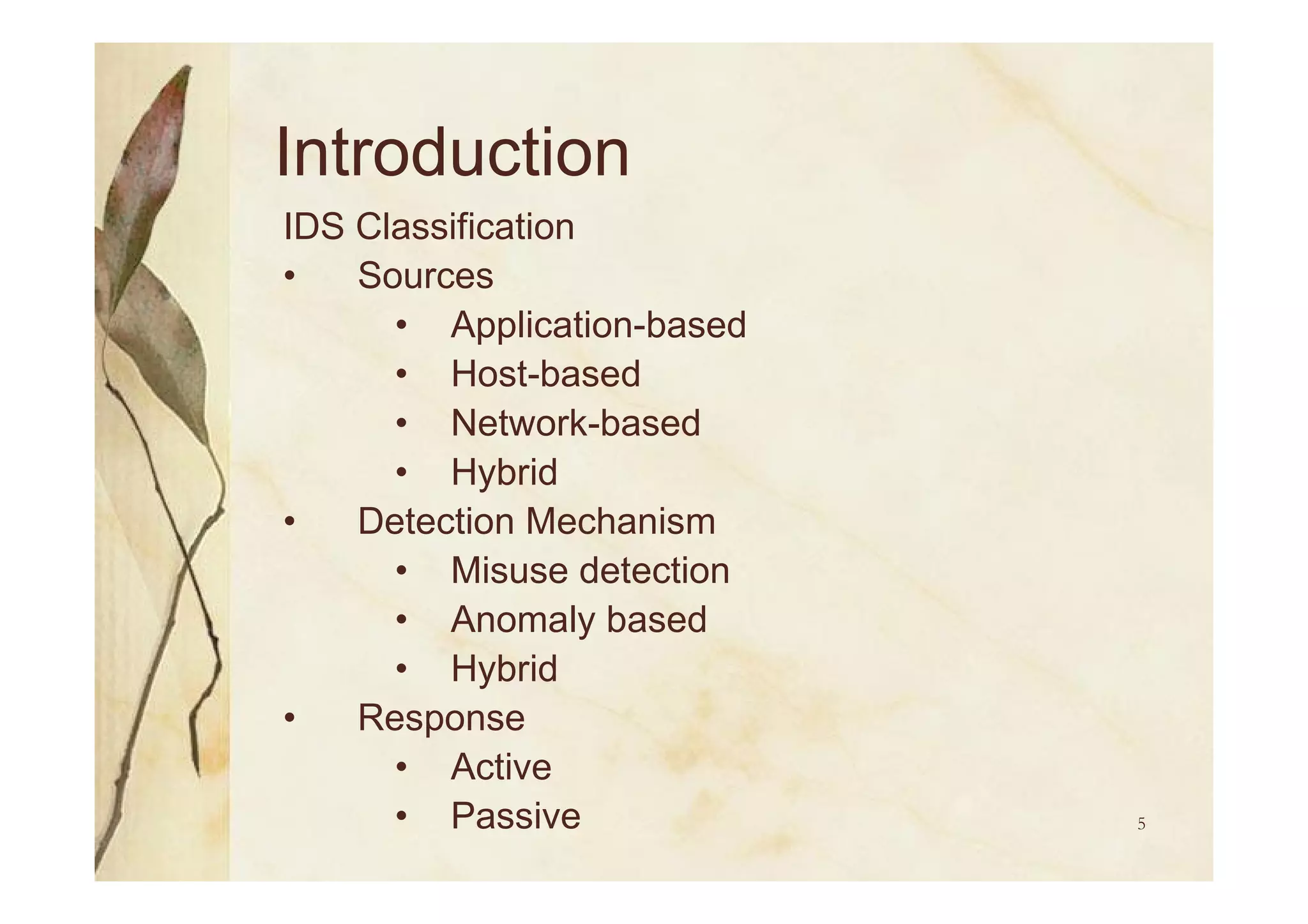
Introduction to IDS, its components, classification, and parameters like accuracy & performance.
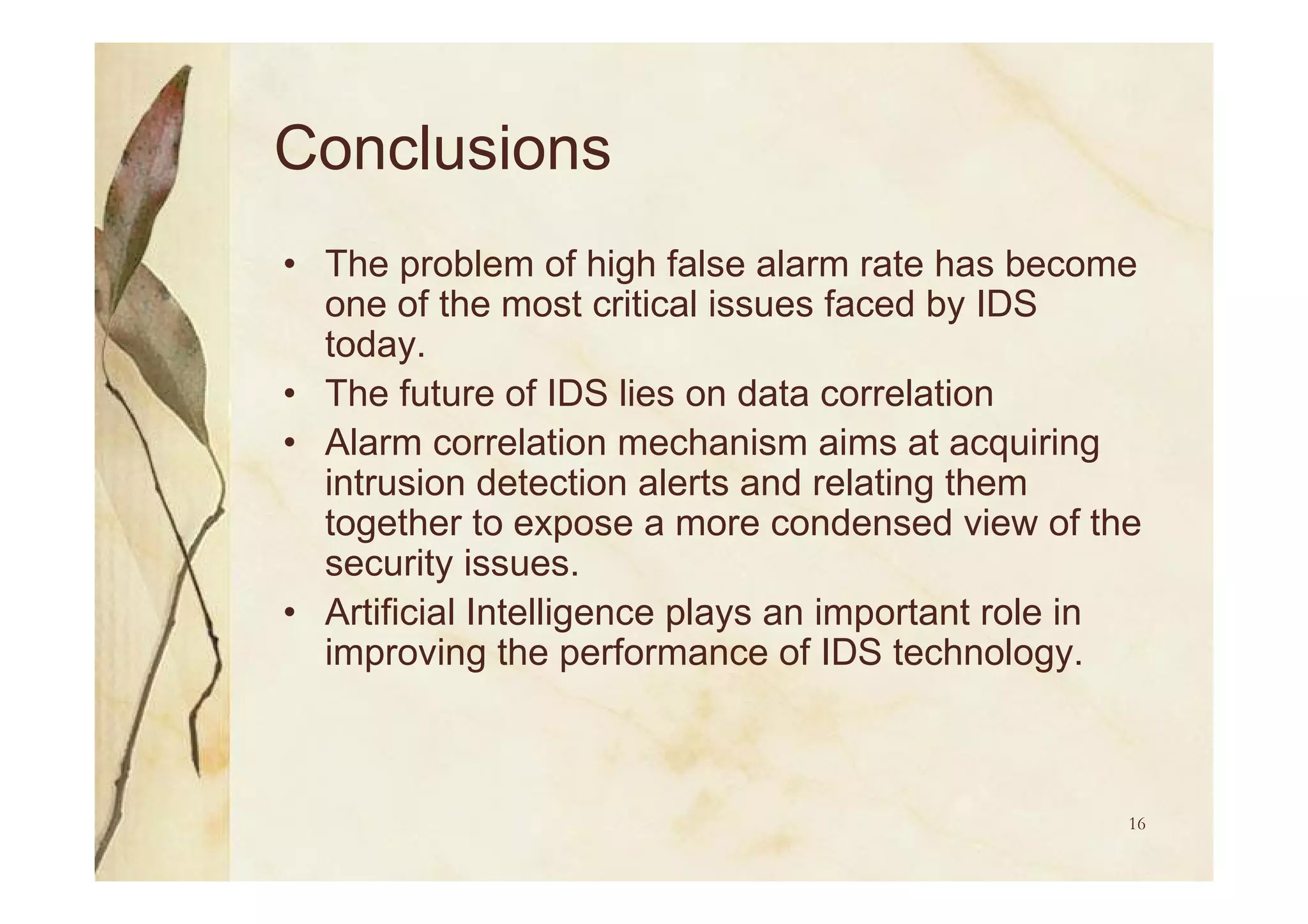
Challenges such as runtime limitations, dependency on environment, and the issue of high false alarm rates.
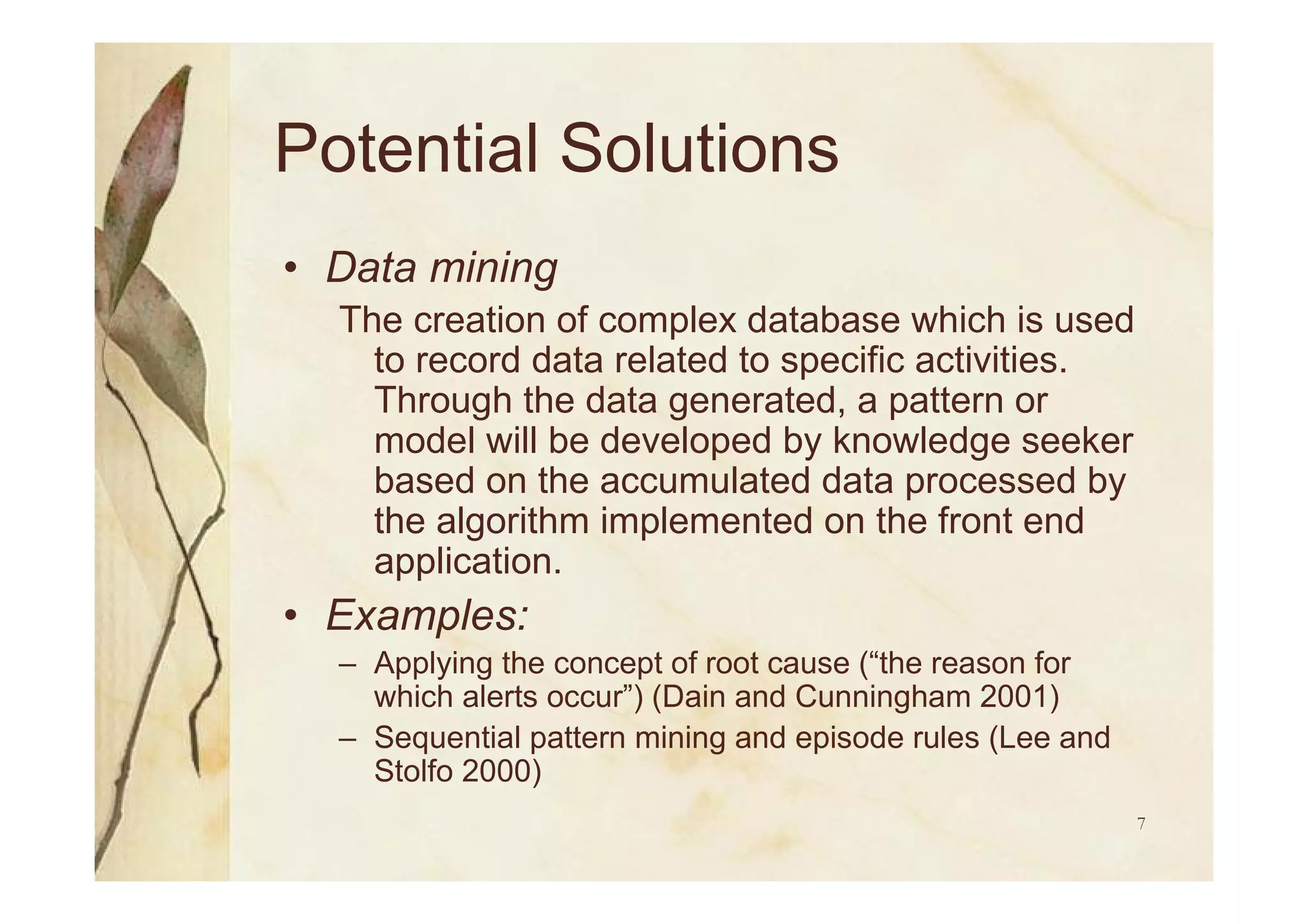
Solutions including data mining, machine learning techniques, and co-simulation mechanisms for improving IDS.
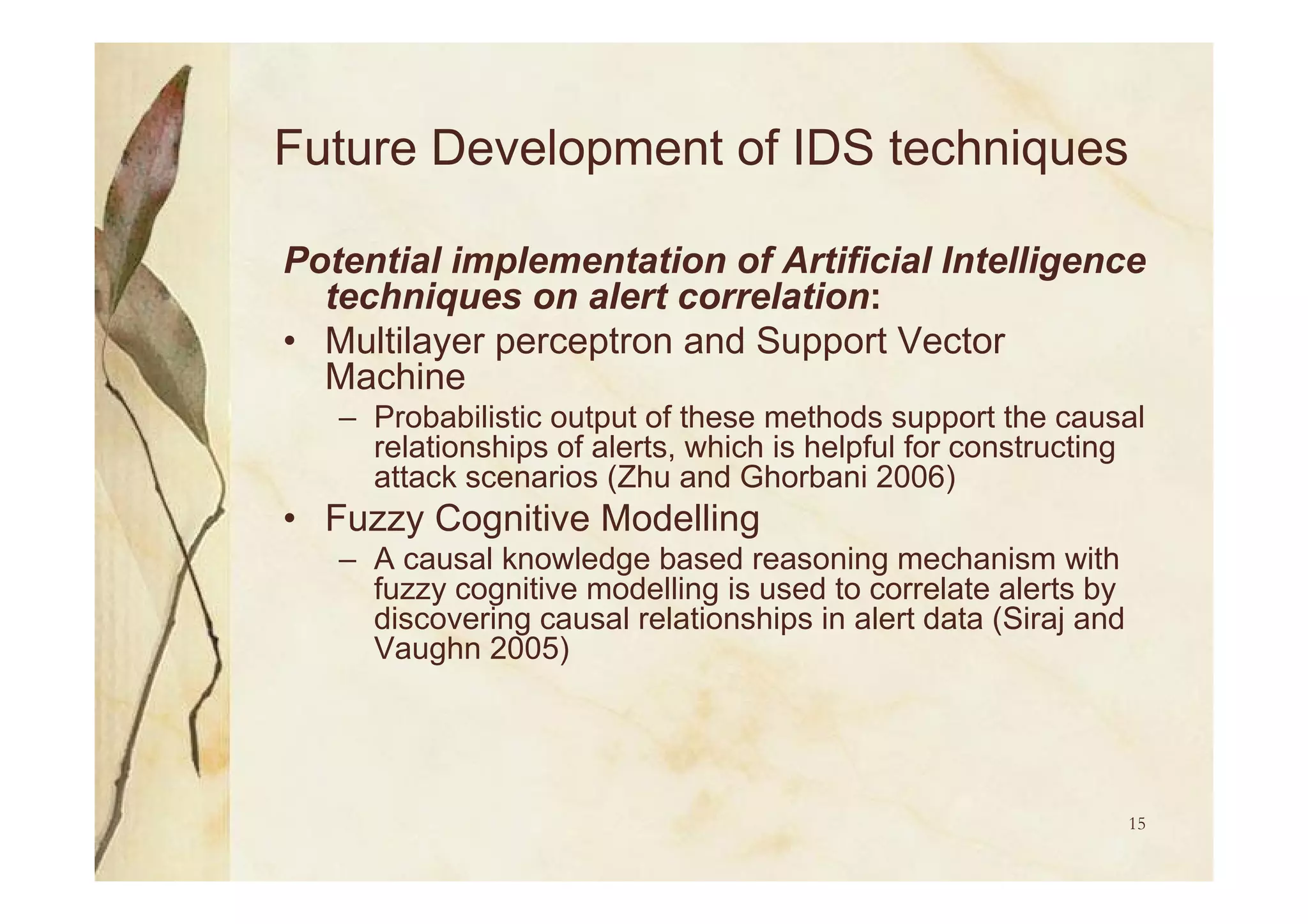
Methods of alarm correlation to enhance intrusion detection through features like modifying, suppressing, and clearing alarms.
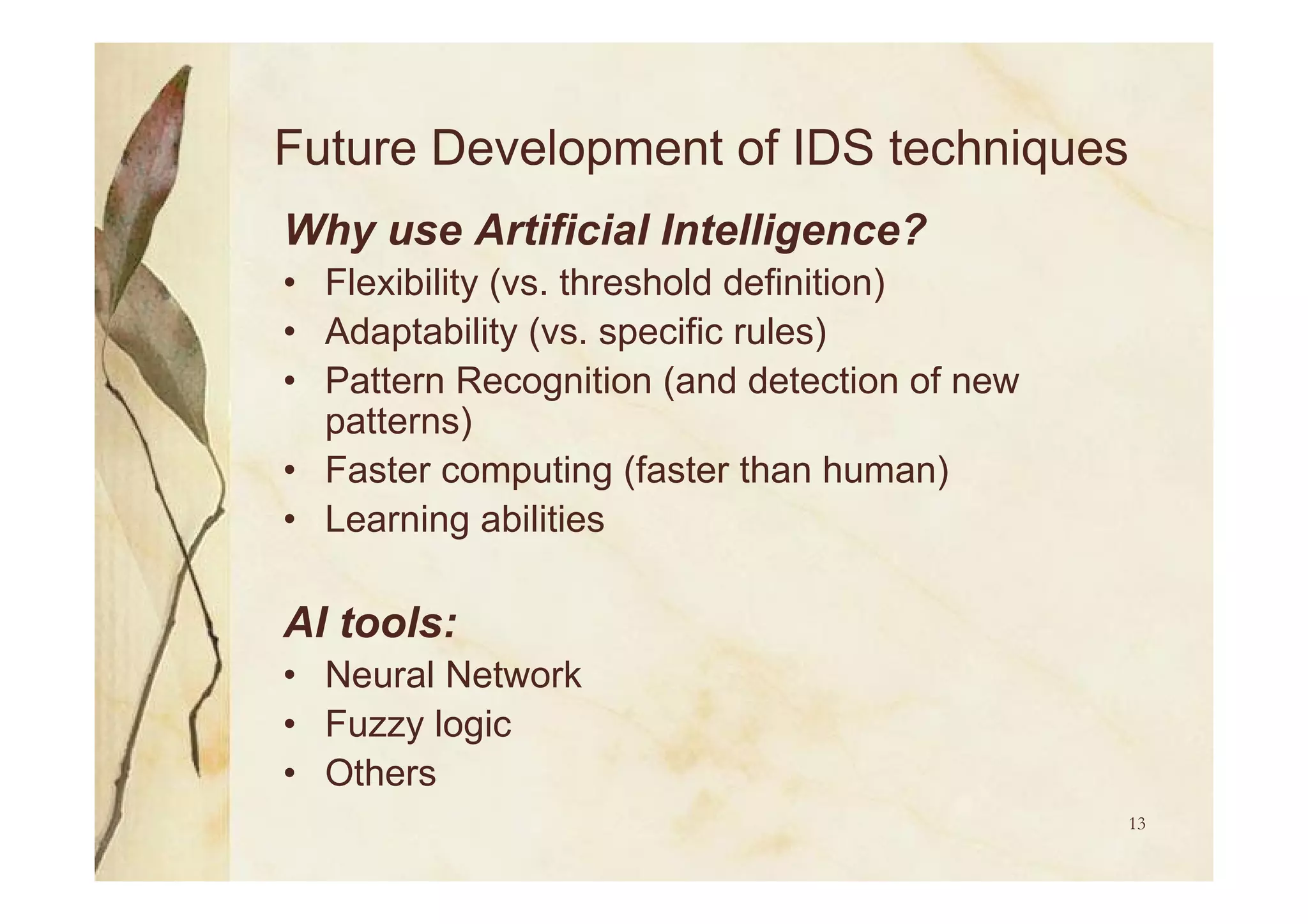
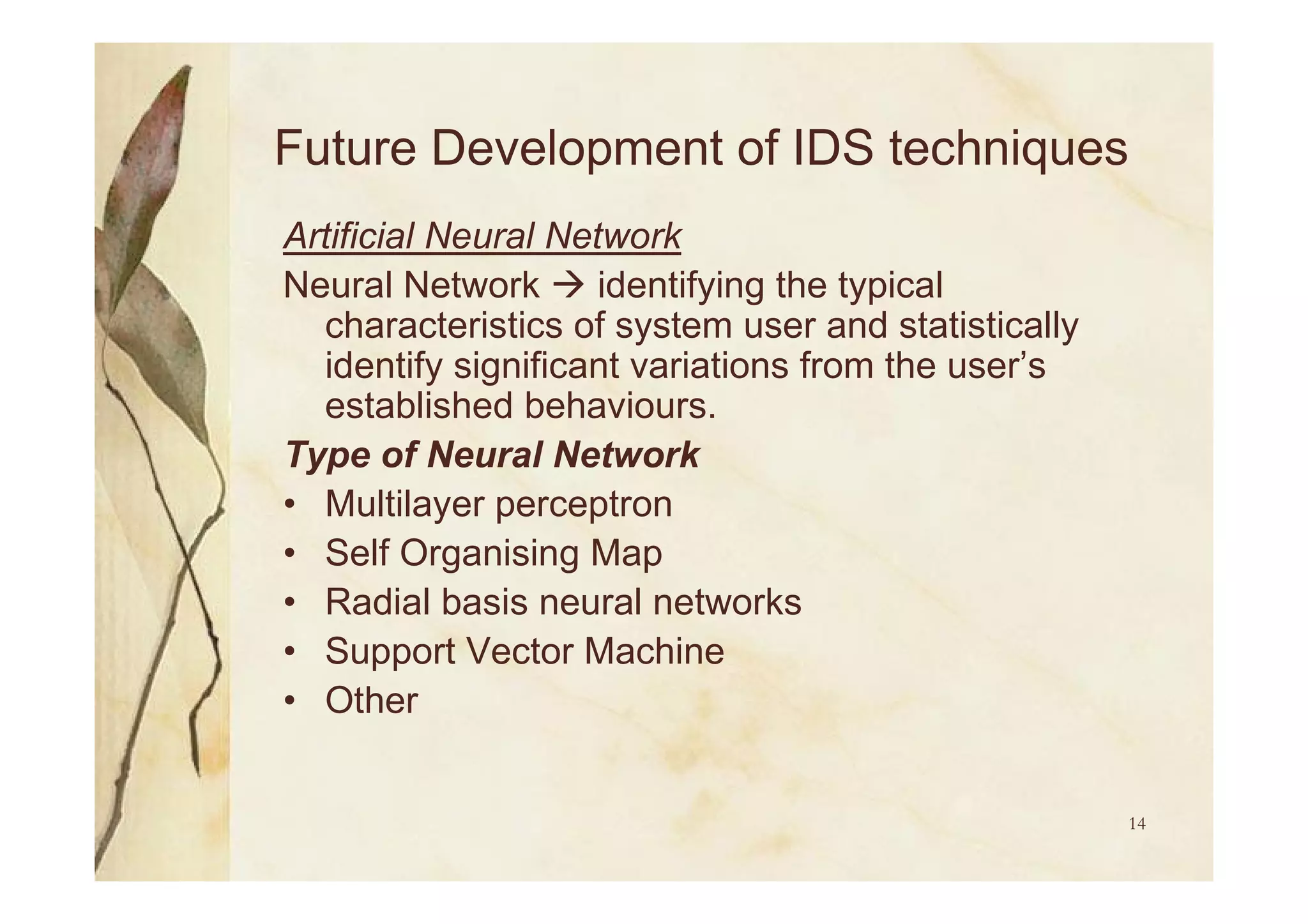
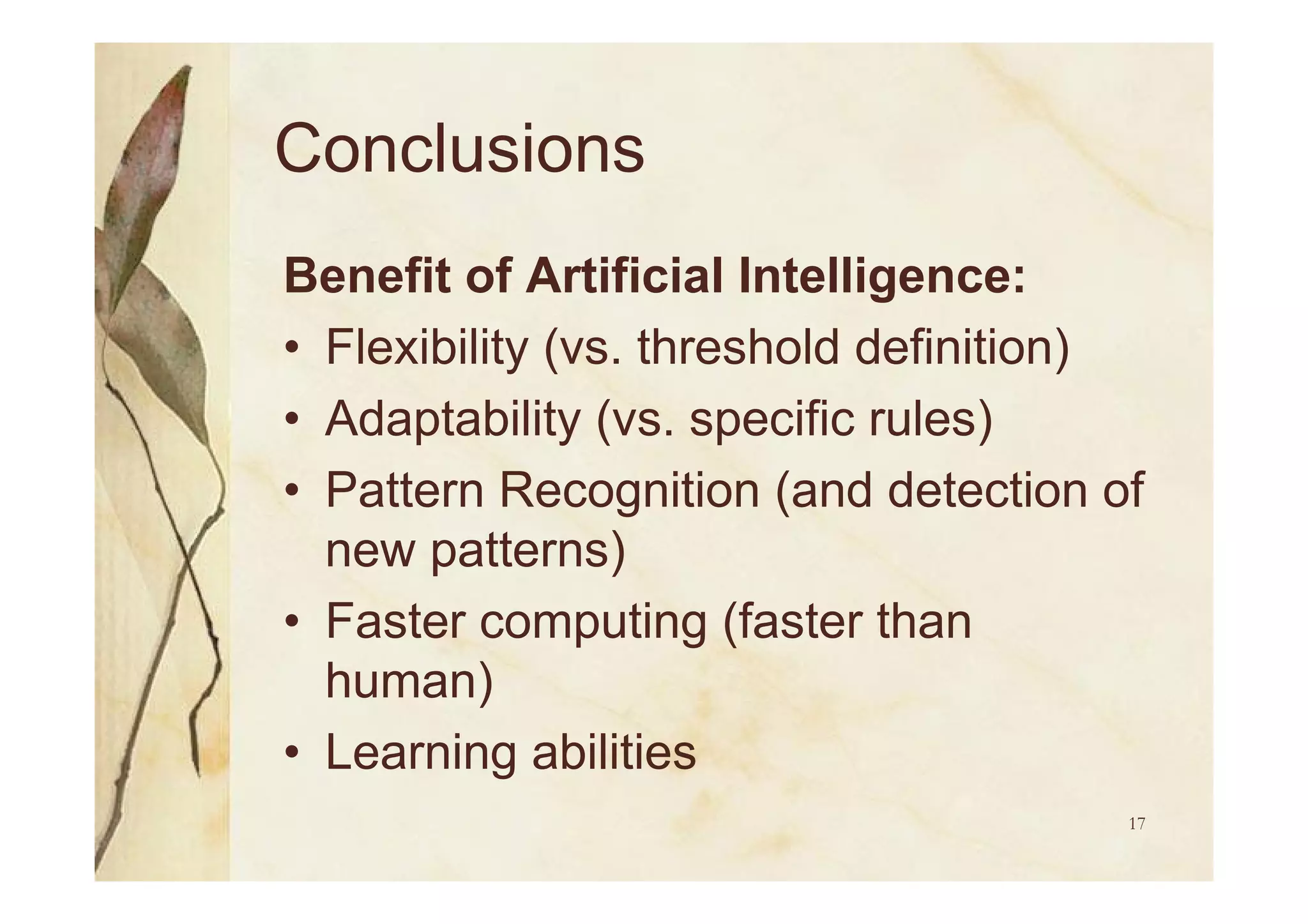
Utilization of AI for future IDS development, focusing on flexibility, adaptability, and employing neural networks for alert correlation.
Summary of IDS challenges, the importance of alarm correlation, and benefits of AI in improving IDS effectiveness.
Citations of sources used in the presentation and an invitation for questions.



















