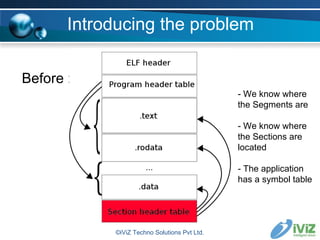
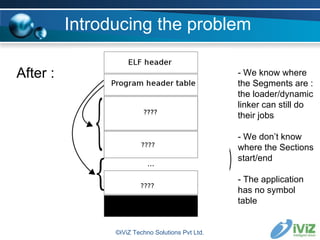
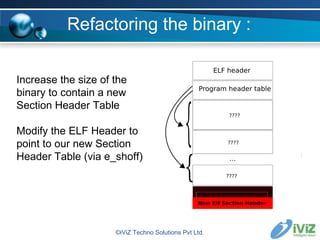
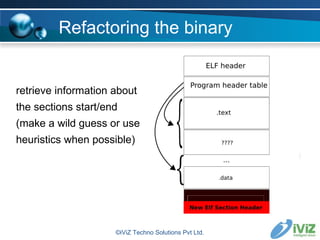
The document discusses reverse engineering binaries to reconstruct missing symbol and section header information. It provides an overview of the ELF file format and issues with stripped binaries. It then describes heuristics and techniques for rebuilding symbol tables and section headers to allow analysis with standard tools like objdump and gdb. Examples are given of finding function labels like main() and global constructors/destructors. The goal is to refactor binaries as little as possible to make them usable again without affecting execution.

![Who Am I ? (and why am I writing this ??) We are recruting ! Send me your CVs at : [email_address]](https://image.slidesharecdn.com/jonathanclubhack08-1230827953258809-1/85/Reverse-Engineering-for-exploit-writers-2-320.jpg)

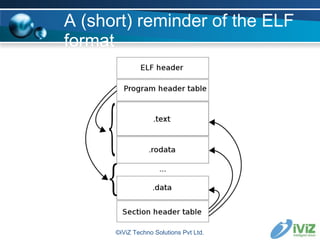
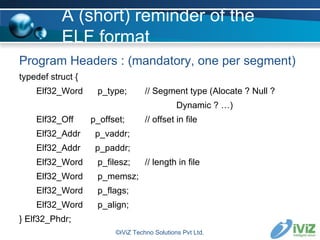
![A (short) reminder of the ELF format The ELF header : (mandatory) typedef struct { unsigned char e_ident[EI_NIDENT]; Elf32_Half e_type; Elf32_Half e_machine; Elf32_Word e_version; Elf32_Addr e_entry; Elf32_Off e_phoff; // offset to Program Header Table Elf32_Off e_shoff; // offset to Section Header Table Elf32_Word e_flags; Elf32_Half e_ehsize; Elf32_Half e_phentsize; Elf32_Half e_phnum; Elf32_Half e_shentsize; // size of a section header Elf32_Half e_shnum; // number of section headers Elf32_Half e_shtrndx; // offset of associated string table } Elf32_Ehdr; ©iViZ Techno Solutions Pvt Ltd.](https://image.slidesharecdn.com/jonathanclubhack08-1230827953258809-1/85/Reverse-Engineering-for-exploit-writers-5-320.jpg)







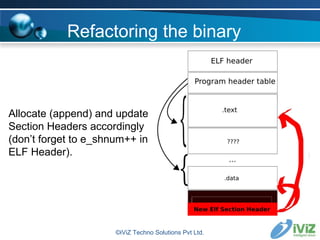
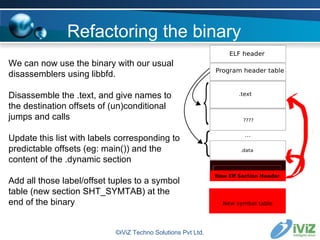
![Refactoring the binary Examples of heuristics : 1) Finding main() objdump -d -j .text ./binary \ 2>/dev/null|tac|grep \ "__libc_start_main@plt" -A 1|grep push|grep \ "0x[0-9a-fA-F]*" -o|awk '{print $0 " main"}' ©iViZ Techno Solutions Pvt Ltd.](https://image.slidesharecdn.com/jonathanclubhack08-1230827953258809-1/85/Reverse-Engineering-for-exploit-writers-22-320.jpg)
![Refactoring the binary Examples of heuristics : 2) Finding constructors objdump -d -j .text ./ binary 2>/dev/null \ |tac|grep \ "bb [0-9a-fA-F][0-9a-fA-F] [0-9a-fA-F][0-9a \ -fA-F] 0[0-9a-fA-F] 08" -A 4|grep -w 55|grep \ "[0-9a-fA-F][0-9a-fA-F]*" -o|head -n 1|sed \ s#"^0"##gi|awk '{print "0x" $0 “ \ __do_global_ctors_aux"}' ©iViZ Techno Solutions Pvt Ltd.](https://image.slidesharecdn.com/jonathanclubhack08-1230827953258809-1/85/Reverse-Engineering-for-exploit-writers-23-320.jpg)
![Refactoring the binary Examples of heuristics : 3) Finding destructors objdump -d -j .text ./binary \ 2>/dev/null|tac|grep "80 3d [0-9a-fA-F][0-9a \ -fA-F] [0-9a-fA-F][0-9a-fA-F] 0[0-9a-fA-F] 08 \ 00" -A 10|grep -w 55|grep "[0-9a-fA-F][0-9a \ -fA-F]*" -o|head -n 1|sed s#"^0"##gi|awk \ '{print "0x" $0 " __do_global_dtors_aux"}' ©iViZ Techno Solutions Pvt Ltd.](https://image.slidesharecdn.com/jonathanclubhack08-1230827953258809-1/85/Reverse-Engineering-for-exploit-writers-24-320.jpg)





