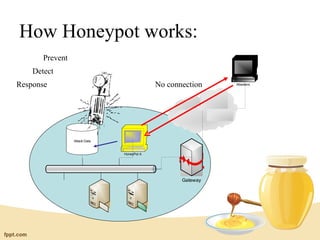
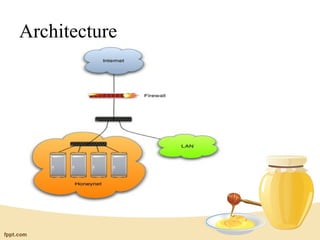
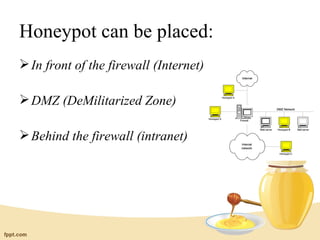
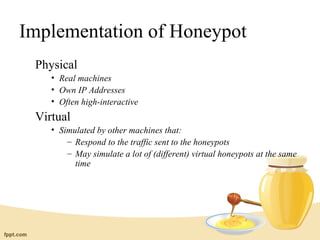
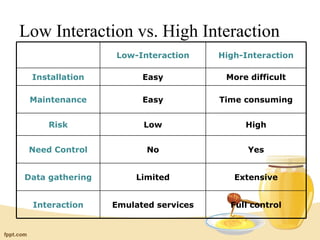
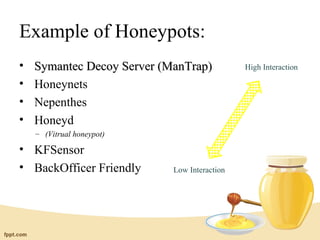
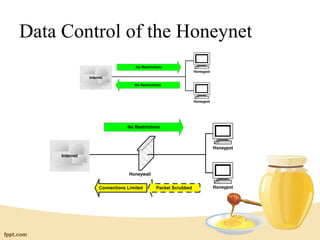
Honeypots are information systems designed to detect attacks by capturing unauthorized access. A honeypot mimics real systems to attract hackers while logging their activities without exposing real systems to harm. Honeynets are networks of high-interaction honeypots that provide whole systems for hackers to interact with and reveal their tactics. While helpful for research, honeypots require careful control and monitoring to prevent real damage while gathering forensic data on intrusions and attacks.